Encryption and Signing
Learn more about encryption, signing, and the Public Key Infrastructure (PKI).
Join the DZone community and get the full member experience.
Join For FreeSymmetric Encryption
Symmetric encryption means that the same key is used to encrypt and decrypt:

Public Key Infrastructure (PKI)
Asymmetric Encryption
To solve the problem of negotiating 100 keys, if you want to send something privately to 100 individuals/system, a public/private key is used. If a message is encrypted using public key then it can be decrypted only with private key, and on the same line, if a message is encrypted using a private key, then it can decrypted using only a public key (not even with a private key)
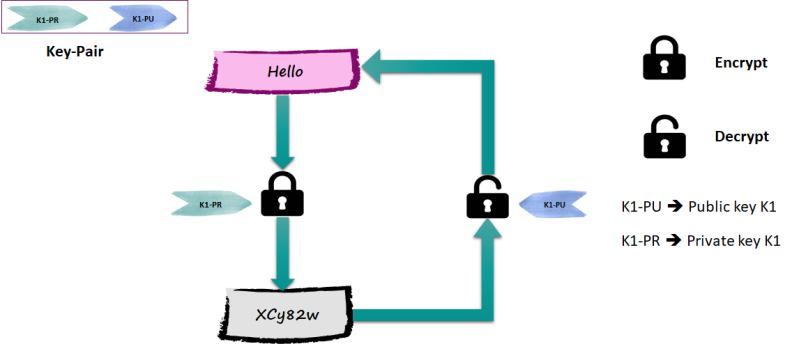

- Key-pair (private/public) is generated by owner.
- Private key is kept confidential, while public key is shared with every one.
- It is difficult (next to impossible) to derive private key from public key.
Suppose you are planning to send a message to James privately;, you would use his public key to encrypt the message. Even though other people know the public, they can't decrypt it — only James knows the private key, so he can decrypt it.

Digital Signature
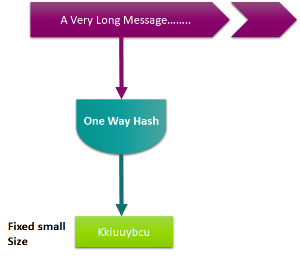
Let's assume that the message you send to James is not confidential; however, James should know the message is really from you. You can use your private key to encrypt the message, and then, James can use your public key to decrypt the message. However, this is not feasible if the message is too long, since the encrypted message would get doubled and it is a time-consuming operation. To solve this, you can feed the message to a one way hash function to produce a result (message digest) of same size always (depending upon the algorithm)
Features of one way hash function:
- Extremely fast
- Impossible to create message from a digest
Now to prove to James that you are who you are claiming to be, you can use your private key to encrypt the message digest and then send both the message and the digest to James.
James can decrypt the digest using your public key, calculate the digest from the original message, and finally compare the message digests.
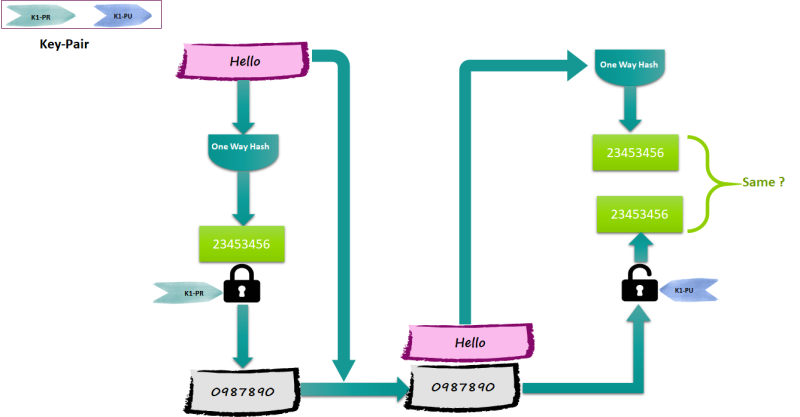
The encrypted digest is called the “Digital Signature,” and the whole process of calculating the digest and then encrypting it is called “signing the message."
Signing and Encrypting
What if you would like to prove to James that you are who you are claiming to be, and at the same time, you want to make sure message is received only by James?
Follow the diagram.

Certificate and CA
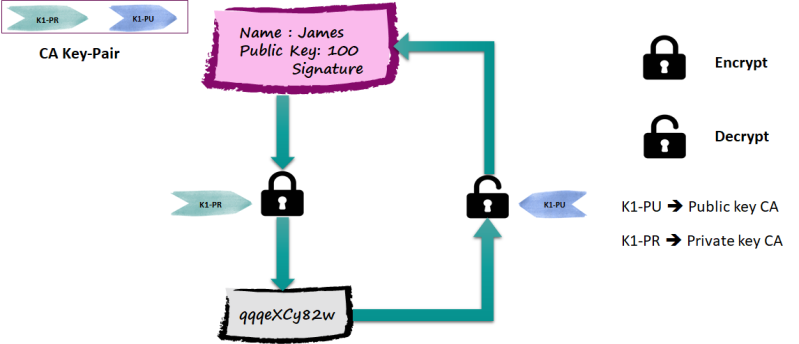
The problem of how we get one's certificate (without being trapped) and, most importantly, how do we distribute to many individuals is solved by Certificate and CA.
You go to an authority, and by stating your public key with proof of ID, the authority generates an electronic message with your public key that is signed with his (authority) private key.
Such a signed message is called a certificate, and such an authority is called the Certificate Authority (CA)
Conclusion
In order to use asymmetric encryption and digital signature, the following are required:
- Private Keys
- Public Keys
- Certificates
- CA
All of the above, when combined, are called a Public Key Infrastructure (PKI)
References
- Developing Webservices with Apache Axis
- OWASP Using_the_Java_Cryptographic_Extensions
- JCE Book
Published at DZone with permission of Mohammad Nadeem, DZone MVB. See the original article here.
Opinions expressed by DZone contributors are their own.

Comments