The pdfChain add-on is blockchain-technology agnostic. You need to implement the IBlockChain interface, or pick an existing implementation to match with the blockchain technology of your choice. You also have to extend the abstract class named AbstractExternalSignature.
The IBlockChain Interface
We have defined an interface that consists of only three methods:
public boolean put(String key, Record data);
A method to put a record on the blockchain.public List get(String key);
A method to get a record from the blockchain based on its key.public List all();
A method to list all records registered on the blockchain.
The Record class simply extends Map<String, Object> and is used as a collection of key-value pairs.
The AbstractExternalSignature Class
We have created an AbstractExternalSignature class implementing a hash() and an encryptHash() method, but four methods are abstract:
public abstract String getHashAlgorithm();
A method in which you provide the hash algorithm to be used.public abstract String getEncryptionAlgorithm()
A method in which you provide the encryption algorithm to be used.public abstract Key getPublicKey();
A method in which you provide the public key object.public abstract Key getPrivateKey();
A method in which you provide the private key object.
The DefaultExternalSignature class currently uses SHA-256 as hashing algorithm and RSA as encryption algorithm.
The PdfChain class
Using an IBlockChain implementation and an external signature class, we can create a PdfChain object that can be used to add and retrieve records from the blockchain.
This is how we add a record to a blockchain for which we used MultiChain technology:
IBlockChain mc = new MultiChain(
"http://127.0.0.1", 4352, "chain1", "stream1", "multichainrpc",
"BHcXLKwR218R883P6pjiWdBffdMx398im4R8BEwfAxMm");
sign.AbstractExternalSignature sgn =
new sign.DefaultExternalSignature(new File("path_to_keystore"), "demo", "password");
pdfchain.PdfChain blockchain = new pdfchain.PdfChain(mc, sgn);
File inputFile = new File("input.pdf");
blockchain.put(inputFile);
This is how we retrieve records from the blockchain:
IBlockChain mc = new MultiChain(
"http://127.0.0.1", 4352, "chain1", "stream1", "multichainrpc",
"BHcXLKwR218R883P6pjiWdBffdMx398im4R8BEwfAxMm");
sign.AbstractExternalSignature sgn =
new sign.DefaultExternalSignature(new File("path_to_keystore"), "demo", "password");
pdfchain.PdfChain blockchain = new pdfchain.PdfChain(mc, sgn);
File inputFile = new File("input.pdf");
for (Map<String, Object> docEntry : blockchain.get(inputFile)) {
for (Map.Entry<String, Object> entry : docEntry.entrySet())
System.out.println(padRight(entry.getKey(), 32) + " : " + entry.getValue());
System.out.println("");
}
The get() method returns a List of Record objects, because the same document can be stored more than once, with different properties.
A possible output could be:
blocktime : 1499691151
id2 : �Ʊ��B�}ә`�-o�R
id1 : z�L{�Wd=����G�
publishers : [14pwDpkcfRvSiw6DJWpP7RdcYgv5NfRRn6Dudr]
txid : b0092d7eb967ac2e45671742ddf1a0a96bc049a4bbfe3528888b6d9ff396b7a2
hsh : ��B�����șo�$'�A�d��L���xR�U
confirmations : 22
key : ��Bï¿½ï¿½ï¿½ï¿½ï¿½È o�$'�A�d��L���xR�U
shsh : <garbled>
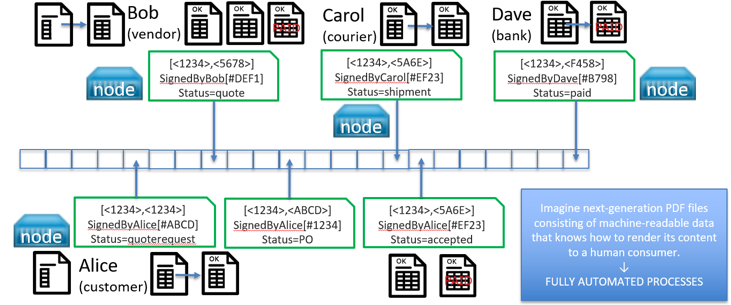
As you can see, the PdfChain class stored an entry with a key named confirmations. That's extra metadata that we stored in the blockchain using the PdfChain method. We can use the BQL functionality of the pdfChain add-on to create a query. For instance, we can use the BQLCompiler to get the ID-pair, the number of confirmations, and the hash value of all the records of which the number of confirmations is greater than 10, but lower than 50.
IBlockChain mc = new MultiChain(
"<http://127.0.0.1>", 4352, "chain1", "stream1", "multichainrpc", "BHcXLKwR218R883P6pjiWdBffdMx398im4R8BEwfAxMm");
AbstractBQLOperator op = BQLCompiler.compile("SELECT [id1, id2, confirmations,hsh]( confirmations > 10 AND confirmations < 50 ) SORT confirmations");
Executor exe = new Executor(mc);
Collection<Record> resultSet = exe.execute(op);
For more examples and more info about the classes used in these examples, see https://itextpdf.com/Blockchain.


{{ parent.title || parent.header.title}}
{{ parent.tldr }}
{{ parent.linkDescription }}
{{ parent.urlSource.name }}