Detect Log4j Vulnerability Using ACS
Here, learn how to detect Log4j vulnerability using Red Hat Advanced Cluster Security, or ACS, which will help protect and defend your Kubernetes cluster.
Join the DZone community and get the full member experience.
Join For FreeIn this article, I will discuss how to detect Log4j vulnerability using Red Hat Advanced Cluster Security or ACS, which will help you to protect and defend your Kubernetes cluster.
ACS protects your application across build, deploy, and runtime. It performs risk profiling of your entire environment and ranks your running deployments according to their security risk. It also detects the suspicious process execution within the container.
Let's explore how to detect applications using the older Log4j jar running in the Kubernetes cluster (here I am using Red Hat OpenShift Container Platform 4.9).
Prerequisites
Install the following technologies before beginning this exercise:
Red Hat OpenShift Container Platform 4.9 (or any Kubernetes cluster)
Deploy Red Hat Advanced Cluster Security for Kubernetes 3.67(ACS)
Note: I have purposely deployed a SpringBoot application using log4j-core version 2.14.1 [quay.io/shailendra14k/log4jissue]
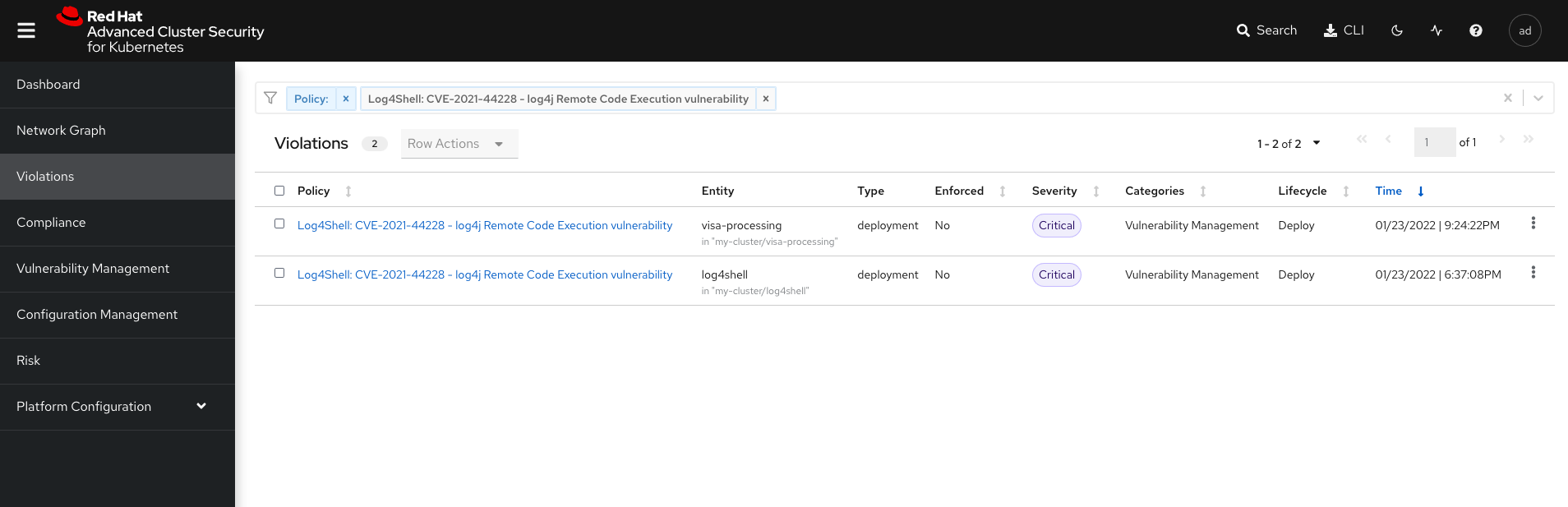
Search for the Log4j Violation
ACS comes with 75+ default policies out of the box. You can also create the custom policy as per the requirement. Log4j security policy by default comes with the latest ACS 3.67 version.
For the older versions, policies are available on StackRox.
Open ACS Management console —> Navigate to Violation tab —> Search for policy:Log4Shell —> This will display the list of all the deployments having the vulnerable log4j jars.
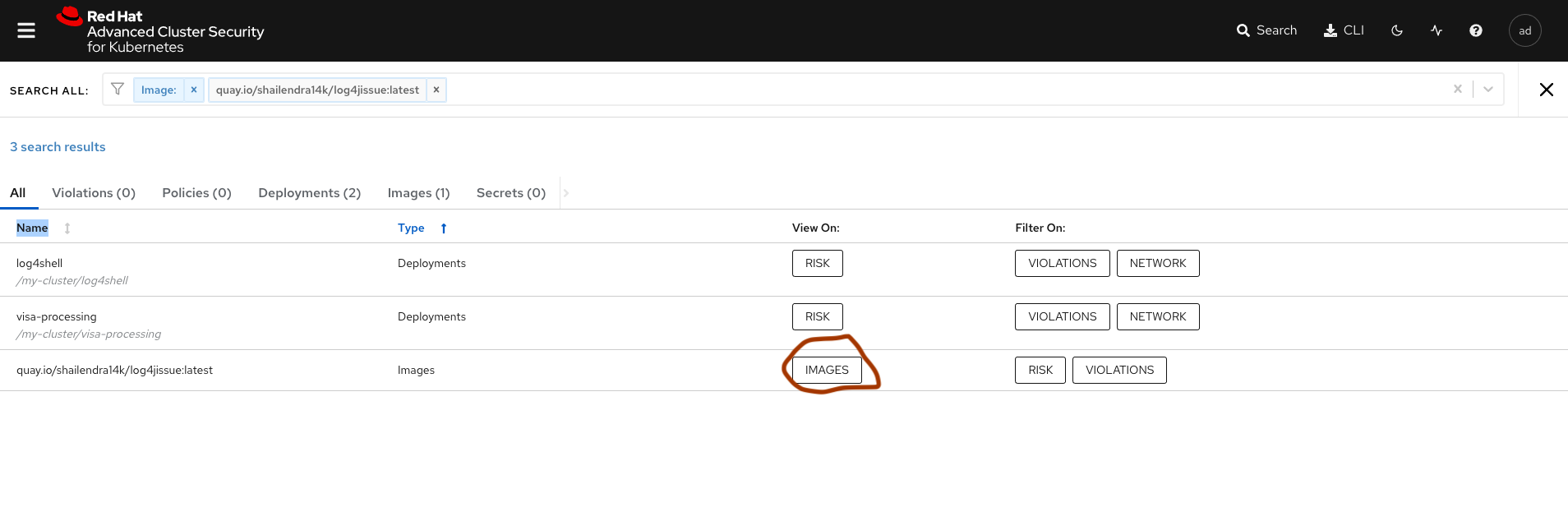
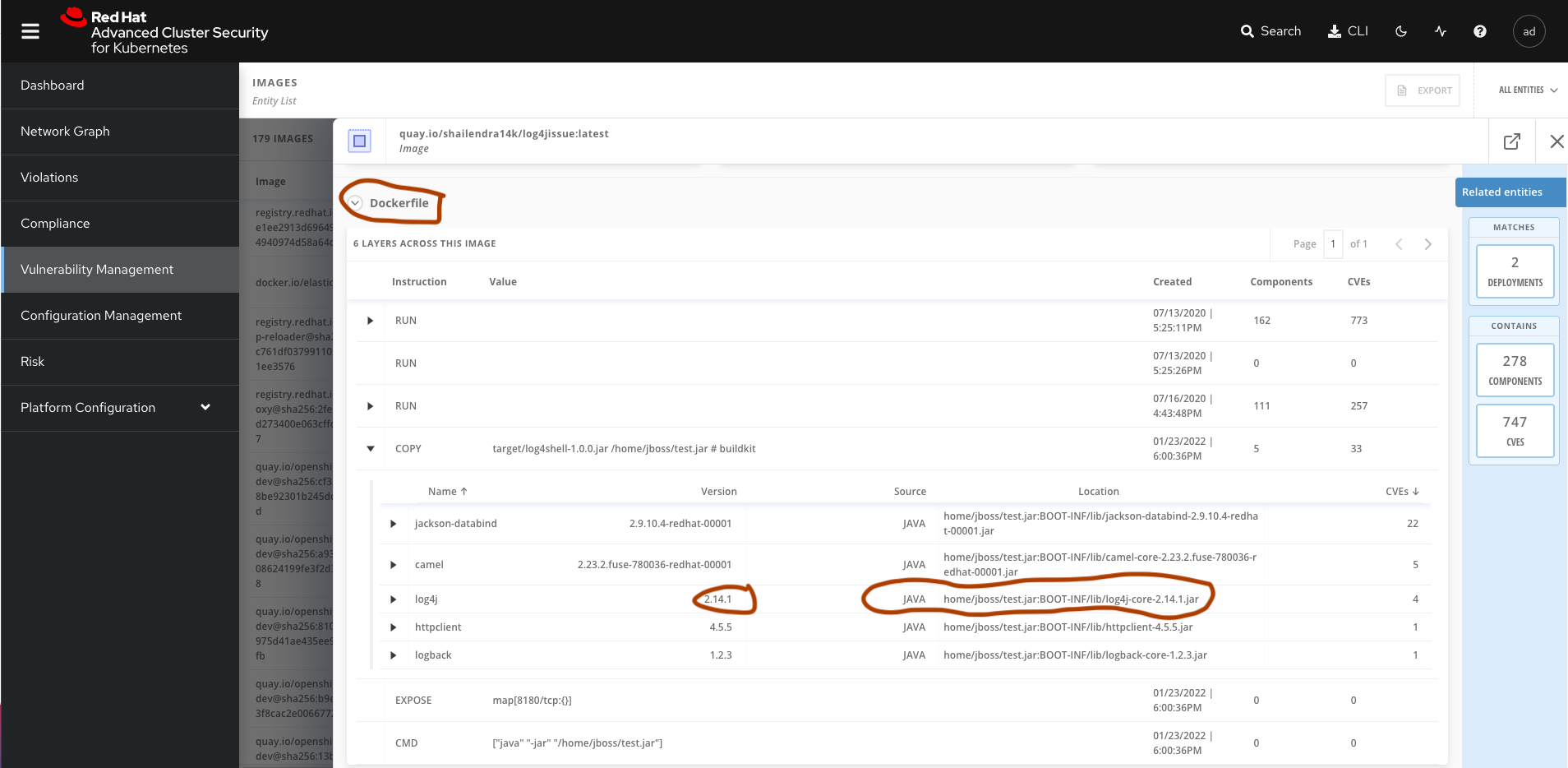
Which Layer Has the Vulnerable Log4j Jars?
ACS will help you to identify the exact layer in the image which has included the Log4j jars.
Click on the Search → filter Image:<name of the image>. In my case, it is quay.io/shailendra14k/log4jissue:latest.
Once you find the image, click on the IMAGES button under view on the column.
 Click on the Dockerfile and verify each layer.
Click on the Dockerfile and verify each layer.
![ACS Dockerfile verification]() Notification?
Notification?
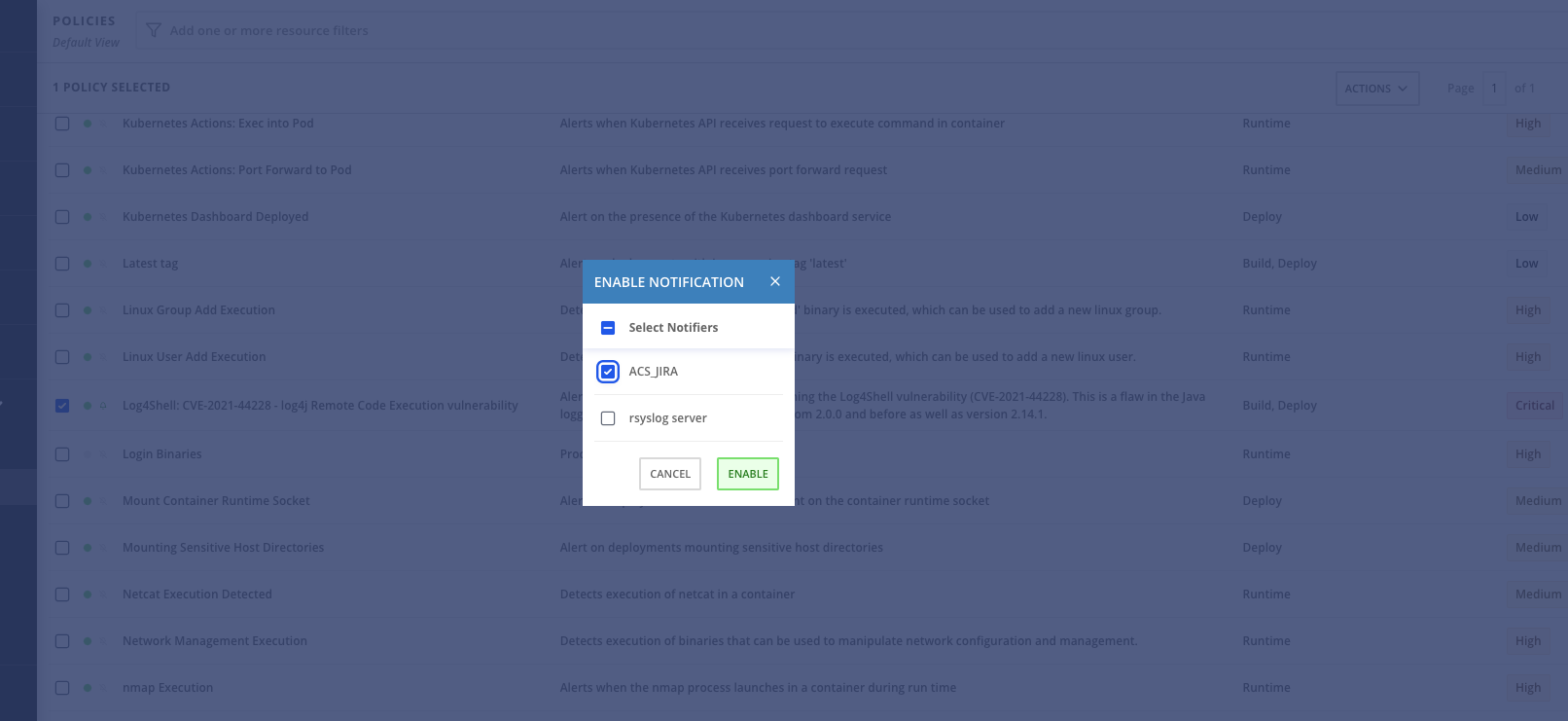
Yes, you can integrate ACS with various notifiers such as Slack, Jira, Splunk, and Syslog. I have integrated with Jira and Syslog server.
To get the notification, you will first have to enable it by going to the System policies → Select the policies against which you want to enable the notification→ click on Action → Enable notification.
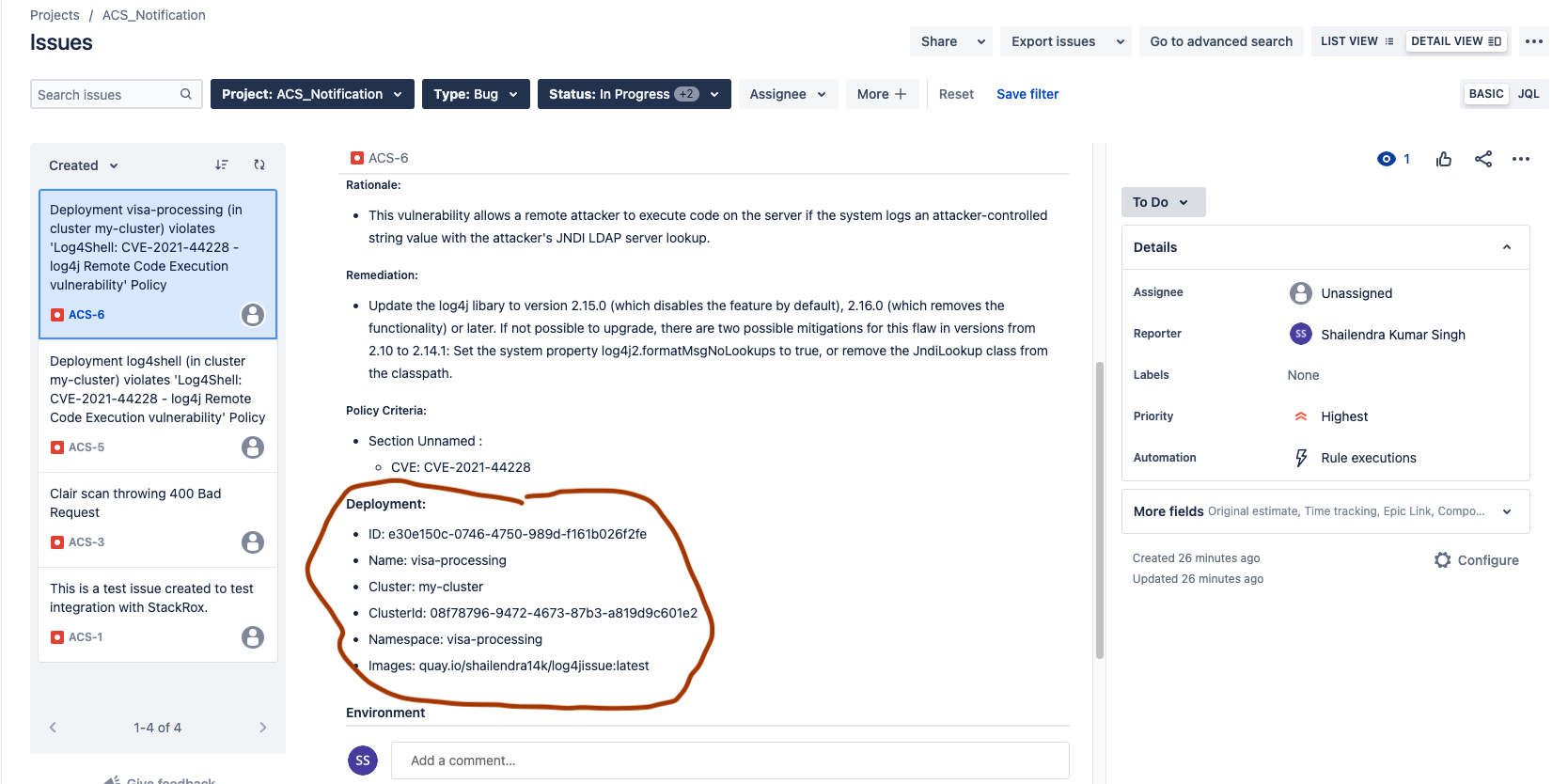
Once the notification is enabled, you will be notified of every violation. As I have integrated with JIRA, for every violation, a bug is created with all the details of the deployment as below.
Conclusion
We saw how to identify the Log4j venerable deployment across the Kubernetes cluster. In the next tutorial, I will walk through how to enforce the policy behavior at build, deploy, or runtime, which will block any deployment violating the policies.
Thank you for reading!
Opinions expressed by DZone contributors are their own.

 Notification?
Notification?
Comments