Safeguarding Sensitive Data: Content Detection Technologies in DLP
Data breaches cost $4.88M on average — learn in this article how DLP content detection protects sensitive data with the help of AI, RegEx, OCR, and more.
Join the DZone community and get the full member experience.
Join For Free
The 2024 IBM Cost of a Data Breach Report found that data breaches cost organizations an average of $4.88 million per incident globally. Many of these breaches were caused by accidental or intentional mishandling of sensitive information. As businesses rely more on cloud collaboration tools, SaaS applications, and global data sharing, Data Loss Prevention (DLP) solutions have become essential to cybersecurity.
Content detection technologies are the core of DLP tools. They identify and protect confidential data at rest, in motion, and in use. This article explores the key content detection technologies, their applications in various industries, and the best practices for effective deployment.
Data at Rest, in Motion, and in Use: What Is the Difference?
Data Loss Prevention (DLP) solutions are frequently classified based on the state of the data they protect:
- Data at Rest. This refers to information that is stored in locations like databases, file servers, and endpoints.
- Data in Motion. This refers to information that is transmitted across networks, such as emails, file transfers, and instant messages.
- Data in Use. This refers to information that is actively being accessed, edited, or shared by users.
While most organizations are accustomed to protecting data at rest and data in motion, data in use presents new challenges, particularly in the context of cloud collaboration platforms, real-time file sharing, and remote work. DLP solutions utilize advanced content detection to address the complexities of safeguarding data in all three states.
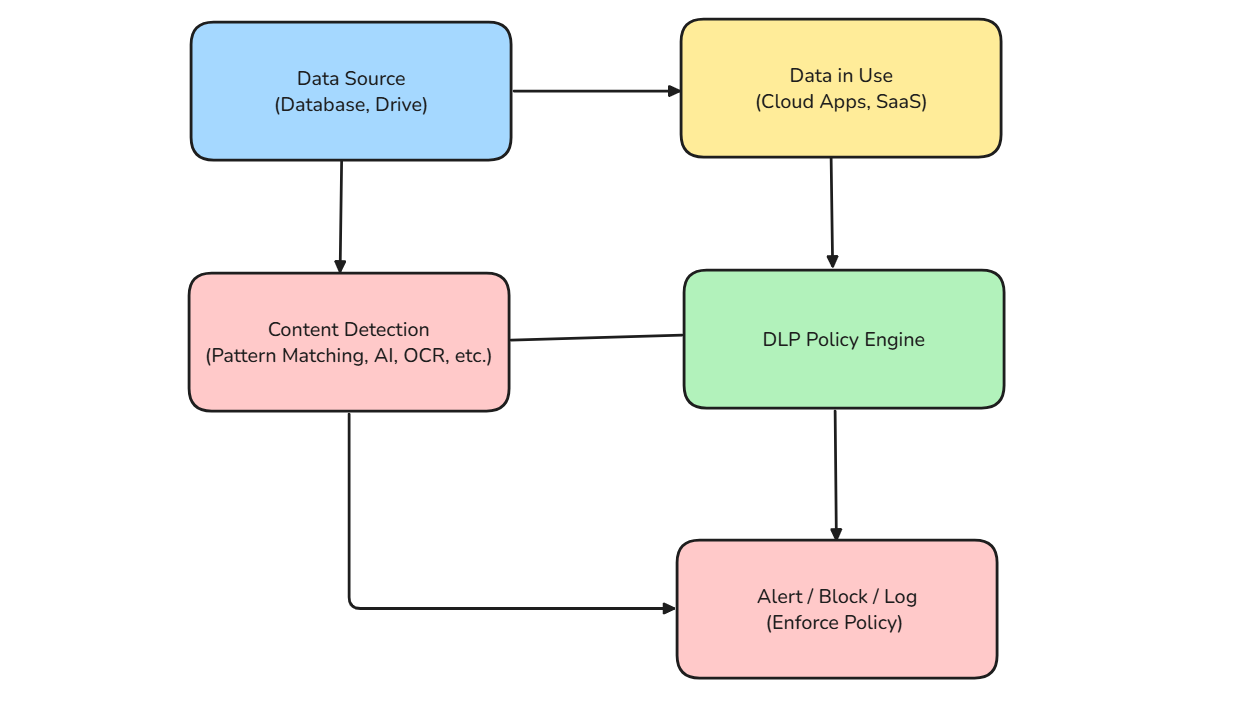
Content Detection Methods: A Layered Approach
Below is a high-level flowchart illustrating how different content detection methods fit into the larger DLP process:
Regular Expressions (RegEx) and Pattern Matching
RegEx is a fundamental technique in DLP systems, used to search for known patterns like 16-digit credit card numbers or 9-digit Social Security numbers. It is fast, transparent, and easy to implement for straightforward use cases.
However, maintaining complex RegEx rules can be challenging, often requiring specialized expertise. It is also prone to false positives when context is not considered. For instance, in financial services, RegEx is commonly used to identify potential credit card leaks by detecting specific numeric sequences.
Rule-Based Policies and Dictionaries
This method relies on customizable dictionaries containing sensitive terms relevant to specific industries, such as medical codes or legal terminology, combined with policy rules. It offers a nuanced approach tailored to organizational needs, making it more effective than plain RegEx.
However, maintaining the accuracy of dictionaries requires regular updates, and overly broad policies can lead to false positives. In healthcare, for example, dictionaries of HIPAA-related terms like ICD-10 codes are used to trigger alerts when sensitive information is identified.
Exact Data Matching (EDM) and Fingerprinting
EDM involves creating a unique "fingerprint" of sensitive data from authoritative sources like a CRM database. The system flags outbound files that match these digital signatures, ensuring high accuracy with minimal false positives.
However, it requires significant setup and maintenance and can be resource-intensive for large datasets. In the banking industry, this method is critical for protecting customer records, such as account details and Social Security numbers, stored in core banking systems.
Partial Document Matching
Unlike EDM, which detects exact matches, partial document matching identifies segments of sensitive documents. This capability is essential for catching partial leaks, such as a few pages of a legal contract or product blueprint shared outside the organization. While resource-intensive and complex to implement across various file types, it is particularly valuable in the legal sector, where it can detect unauthorized sharing of portions of sensitive briefs.
Machine Learning (ML) and Artificial Intelligence (AI)
Modern DLP solutions leverage machine learning and AI to classify content based on learned examples rather than explicit rules. These models often use natural language processing (NLP) and deep learning to adapt to evolving patterns, reducing the need for manual rule creation.
However, they require high-quality labeled data, ongoing retraining, and significant computational resources. AI can also act as a "black box," making decisions harder to interpret. For tech startups, AI models are particularly useful in identifying proprietary source code in emails or Git commits by training on large sets of engineering documents.
Optical Character Recognition (OCR)
OCR converts text from images or scanned documents into machine-readable formats for analysis. This is critical for detecting sensitive information in screenshots, scanned PDFs, or images of IDs and passports.
However, OCR accuracy depends heavily on image quality and font clarity, and handling multiple languages or stylized text can add complexity. In the legal industry, OCR is frequently used to process scanned case files, ensuring sensitive client data is identified and protected before sharing.
Heuristics and Contextual Analysis
Heuristic analysis goes beyond raw content by evaluating user behavior, metadata, and environmental factors like location, time of day, or user roles. For example, it can identify anomalies such as large file transfers to personal emails late at night, sudden spikes in printing activity, or frequent access to confidential folders by unusual users.
While this approach provides greater context and helps mitigate insider threats, it requires continuous tuning and updates to remain effective. Privacy concerns can also arise if monitoring is perceived as intrusive. In multinational corporations, heuristics are invaluable for detecting suspicious behavior, such as employees exporting large amounts of data to personal storage just before leaving the company.
Focus on Data in Use: Real-Time Protection
As cloud-based collaboration and SaaS applications proliferate, monitoring data in use becomes increasingly critical. Traditional DLP solutions that excel at scanning stored files or emailed attachments may fall short in this dynamic environment.
Real-Time Content Analysis
- Integrates with productivity suites (Microsoft 365, Google Workspace) to scan documents as they are being edited.
- Identifies sensitive text or patterns in real time, prompting immediate alerts or encryption.
Watermarking and Labeling
- Embeds metadata or visible watermarks in documents that identify classification levels or ownership.
- Helps track the flow of data and ensures that sensitive files remain traceable.
Access Control Lists (ACLs)
- Restricts who can open, edit, or share a document within the application.
- Offers granular control, preventing unauthorized viewing or distribution.
Example: A marketing team collaborates on new product specs in Google Docs. The DLP system flags potential intellectual property terms in real time and prompts the user to classify the document as “Confidential.”
Industry-Focused Examples: Bringing Content Detection to Life
Healthcare
- Optical character recognition (OCR) for patient records. Scanning patient forms with OCR allows for the identification and protection of any embedded Personal Health Information (PHI).
- Dictionary and rule-based policies. Create alerts for files containing specific health codes or procedural details.
Financial Services
- RegEx for credit card numbers. Rapidly detect and mask or block credit card information found in emails.
- Exact data matching (EDM) for bank account data. Utilize fingerprinting on core banking records to prevent their unencrypted transmission outside of the organization.
Legal Industry
- Partial document matching. Compare sections of legal contracts to detect unauthorized sharing with external parties.
- Heuristic analysis. Flag large quantities of scanned case files that have been uploaded to personal cloud drives.
Manufacturing and Engineering
- AI-based classification. Employ machine learning to identify proprietary CAD drawings or design documents.
- Watermarking. Embed logos and classification tags within sensitive blueprints to track their distribution.
Addressing Zero-Day Threats and Evolving Risks
DLP solutions must also adapt to emerging attack vectors, often referred to as zero-day threats, vulnerabilities, or exploit methods that are not yet widely known or patchable. Some approaches include:
- Anomaly detection. Use AI to baseline “normal” data flows and user behavior, triggering alerts when there is a deviation.
- Sandboxing. Isolate and analyze suspicious files or email attachments in a secure environment before allowing them to pass through.
- Continuous updates. Regularly patch the DLP software and refresh detection signatures to keep pace with new threats.
Balancing Security, Usability, and Privacy
One of the biggest challenges is preventing data loss without disrupting legitimate workflows or infringing on user privacy. Overly stringent rules can hamper productivity; overly lax rules can open the door to data exfiltration.
Tips for Balancing
- Phased rollouts. Start with “monitor-only” mode, gather metrics on triggers, and refine policies.
- Role-based policies. Align detection rules with job responsibilities. For instance, an HR team may need access to Social Security numbers, but marketing should not.
- Transparent communication. Educate employees about what DLP is scanning and why.
Key Takeaways and Conclusion
- Content detection is the engine of a robust DLP strategy; it identifies sensitive information across multiple formats and channels.
- Modern DLP must address data at rest, in motion, and in use, especially as cloud collaboration becomes the norm.
- A layered approach with RegEx, dictionaries, AI, OCR, and heuristics ensures comprehensive coverage.
- Contextual and behavioral analysis can help reduce false positives and detect insider threats.
- As zero-day threats continue to evolve, DLP solutions must incorporate anomaly detection, sandboxing, and continuous updates.
- A successful DLP program strikes the right balance between security, usability, and privacy and this depends on ongoing fine-tuning, user training, and a deep understanding of your organizations risk profile.
Opinions expressed by DZone contributors are their own.

Comments