The Art of Securing Cloud-Native Mobile Applications, Strategic Defenses: Safeguarding Mobile Apps in the Cloud-Native Realm
Explore the intersection of cloud-native architecture and mobile application security. Delve into strategies and best practices to safeguard sensitive data.
Join the DZone community and get the full member experience.
Join For FreeThis is an article from DZone's 2023 Enterprise Security Trend Report.
For more:
Read the Report
In the ever-evolving landscape of mobile applications, the seamless integration of cloud-native technologies has become a cornerstone for innovation, speed, and efficiency. As organizations harness the power of the cloud to enhance their mobile applications, the critical need to master the art of securing these cloud-native solutions has never been more paramount. We will explore the dynamic intersection of cloud-native architecture and mobile application security, delving into the strategies and best practices essential for safeguarding sensitive data, ensuring user privacy, and fortifying against emerging threats in this dynamic digital ecosystem.
An Overview of Mobile Application Development and Security
Technological innovations are manifesting in the form of mobile applications. Advancements in technology have facilitated the evolution of mobile apps. Unfortunately, there is no universal app type that fits all platforms or purposes. Diversity in mobile apps — such as gaming, shopping, education, and productivity — means that each type has its own unique requirements, like access to low-level APIs, the nature of app store distribution, offline or partial offline functionality, cross-browser compatibility, etc. This has led to various underlying technologies.
There are three main types of apps, each with distinct security challenges:
- Web apps – Simple and browser-based. Key security challenges for web apps are protecting against data in transit, cross-site scripting (XSS) and cross-site request forgery (CSRF), secure session handling, securing third-party integrations, preventing security misconfigurations, etc.
- Native apps – Platform-specific, accessing low-level APIs. Challenges for native mobile apps are safeguarding against code vulnerabilities, securing data storage on devices, protecting against reverse engineering and tampering, addressing potential flaws in third-party libraries, and staying vigilant against platform-specific risks (e.g., jailbreaking on iOS, rooting on Android).
- Hybrid apps – A blend of web and native features. A security checklist for hybrid mobile apps includes addressing vulnerabilities in both web and native components, ensuring secure data transmission, managing potential weaknesses in third-party plugins, safeguarding against cross-platform scripting issues, and mitigating risks associated with the reliance on web views and native wrappers.
Shared security challenges across all types of mobile apps involve protecting against data breaches, ensuring secure communication between the app and back-end servers, implementing robust authentication and authorization mechanisms, addressing vulnerabilities in third-party libraries, and regularly updating and patching the app to address emerging security issues.
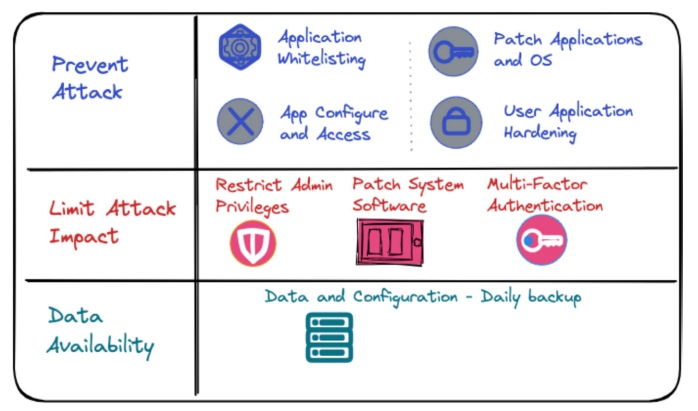
Figure 1: Essential Eight cybersecurity framework
The Essential Eight (E8) is an Australian Cyber Security Centre (ACSC) framework designed to help organizations enhance their cybersecurity posture by assessing and addressing security risks in mobile and other enterprise apps.
The framework consists of eight strategies — depicted on the right-hand side of Figure 1 — aimed at mitigating cyber threats. In addition, it assigns a maturity level (zero to three based on mitigation factors) and helps cyber consultants in risk modeling.
Emerging Security Threats, Patterns, and Vulnerabilities for Mobile Applications
Emerging security threats for mobile applications in the cloud include data breaches due to inadequate cloud security measures, API vulnerabilities leading to unauthorized access, insecure data storage, and the risk of cloud misconfigurations. These patterns involve the growing use of serverless architectures and microservices, which present new attack surfaces.
As per the 2023 OWASP Mobile Top 10 report, the evolving threat landscape of mobile application security is depicted in the table below:
| EMERGING THREATS FOR MOBILE APPLICATION SECURITY | |
|---|---|
| Security Concern | Description |
| API security | Issues related to insecure API usage, including insufficient authentication, improper authorization, and lack of encryption in API communications. |
| Mobile app authentication | Weak authentication mechanisms, such as insecure password handling and insufficient multi-factor authentication, leading to unauthorized access. |
| Data storage and transmission | Insecure data storage and transmission practices, risking data breaches. Encryption should be applied at rest and in transit to protect sensitive information. |
| Insecure direct object references (IDOR) | Inadequate access controls and improper validation of user inputs, leading to IDOR vulnerabilities where attackers can gain unauthorized access to data or functionalities. |
| Mobile app reverse engineering | Vulnerable to reverse engineering where attackers decompile and analyze the application's code, potentially revealing sensitive information. |
Table 1
Addressing the challenges posed by emerging and sophisticated cyber threats requires a proactive approach. By diligently adhering to the guidance provided by the E8 framework, organizations can fortify their defenses.
Developing and Securing Mobile Application Components on Cloud
In the realm of mobile application development, adopting a cloud-native approach introduces both innovative possibilities and security considerations. Let's explore the crucial intersection of developing and securing mobile application components in a cloud-native environment.
Securing Mobile Applications on the Front End
Developing and securing the front end of native and hybrid mobile applications on cloud platforms involves a technical strategy focused on robust authentication, secure communication using HTTPS, and mitigation of client-side vulnerabilities like XSS and CSRF. Collaboration with cloud and mobile platform providers, like iOS and Android, allows for the use of platform-specific security features, and adherence to industry standards, such as the OWASP Mobile Security Guidelines, is crucial.
Threat-proofing biometrics and low-level platform vulnerabilities involves a specialized approach. Addressing low-level platform vulnerabilities requires a thorough understanding of the specific platform's architecture. Mitigation measures involve implementing secure coding practices, completing regular security assessments, and staying informed about platform-specific security updates.
Additionally, leveraging platform-specific security features, such as secure enclaves or trusted execution environments, enhances protection against low-level threats. User education completes the approach for a resilient and secure mobile app front end.
Securing Mobile Applications on the Back End
Securing the back end of a mobile application in the cloud, with a focus on data and APIs, demands a robust strategy. Key steps include:
- Selecting a cloud provider (e.g., AWS, Azure, Google Cloud)
- Setting up secure data storage (e.g., DynamoDB, Cosmos DB)
- Implementing authentication with tools (e.g., Cognito, Entra ID, Firebase)
- Using serverless computing for efficient scalability
This evolves into implementing rigorous access controls to manage user permissions effectively, employing robust data transmission protocols such as TLS/SSL, and ensuring encryption for both data in transit and at rest. Regular security audits and continuous monitoring play a pivotal role in promptly identifying and addressing vulnerabilities. Augmenting the security posture for publicly exposed back ends involves integrating threat intelligence feeds and utilizing web application firewalls. Collaborating closely with cloud service providers along with continuous education enhances overall security, and adhering to cross-industry best practices establishes a resilient defense against evolving threats.
This comprehensive, layered approach — encompassing access controls, encryption, monitoring, collaboration, and continuous education — fortifies the defense against the intricate security challenges inherent in cloud-based mobile applications.
Back End for Front End Design Pattern
The Back End for Front End (BFF) design pattern involves creating dedicated back-end services tailored to specific frontend applications, such as iOS or Android, ensuring optimized data flow and API interactions. This architecture promotes a responsive and tailored user experience, allowing each mobile app to communicate directly with its designated BFF.
To enhance security, measures such as OAuth, JWT, and HTTPS are implemented within each BFF, which ensures secure communication. The BFF, in turn, can aggregate data from microservices or APIs, creating a modular and scalable system that prioritizes both user experience and data security.
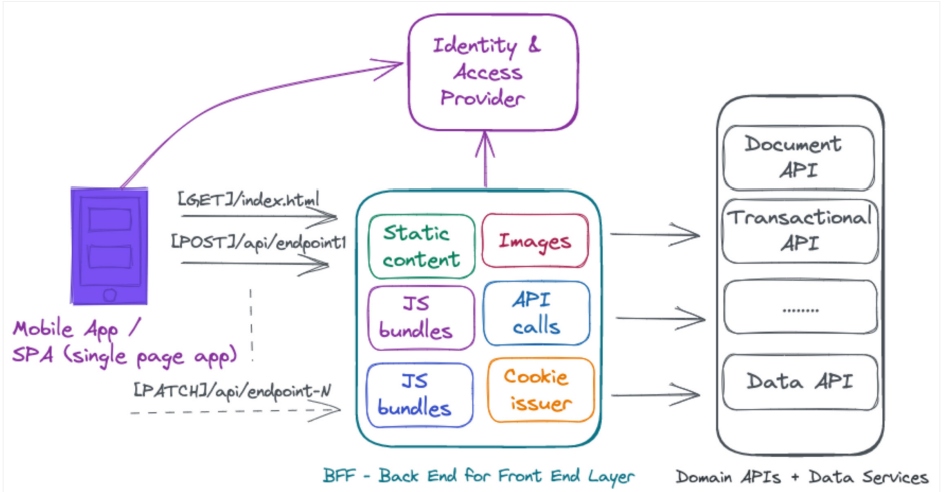
Figure 2: BFF architecture
The BFF pattern enhances security by isolating concerns for specific front ends, minimizing the impact of potential breaches to a localized area to limit the depth of threat penetration. Modular updates and isolated components contribute to a resilient security posture, efficiently containing and addressing security issues.
Mobile Application Security Testing and Automation
Ensure robust mobile app security by integrating continuous security checks throughout development and emphasizing early security practices. Leverage cloud-native testing infrastructure for scalable and efficient automated testing. Perform dynamic threat analyses and API security testing, addressing serverless architecture considerations. Containerized testing ensures consistency, while enhancing DevOps to DevSecOps seamlessly integrates security into the delivery pipeline. Employ cloud identity services, automated compliance checks, and scalable test orchestration for comprehensive and efficient security testing in cloud-native environments.
Threat Modeling
Application security assessment using threat modeling is a proactive approach that helps enterprises identify and mitigate security threats early in the software development lifecycle. Threat modeling involves systematically evaluating potential security risks and vulnerabilities in an application (see Figure 3).
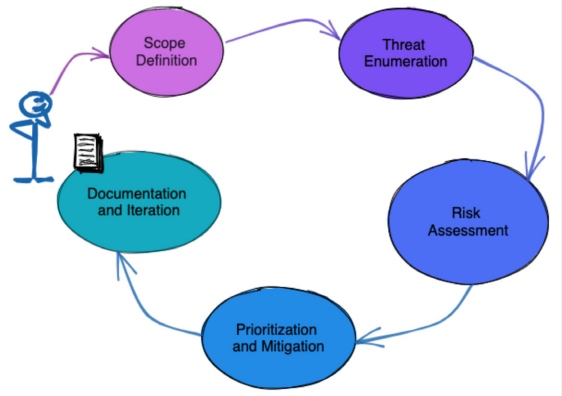
Figure 3: Threat modeling in a nutshell
Here's how threat modeling assists enterprises in mitigating security threats:
- Early identification – pinpoints security threats in the application during the design phase
- Comprehensive risk assessment – evaluates various attack vectors and potential vulnerabilities comprehensively
- Risk prioritization – helps prioritize risks based on impact, likelihood, and criticality for focused mitigation efforts
- Informed decision-making – empowers teams to make informed decisions on security controls and countermeasures
- Secure design principles – promotes the integration of secure design principles into the application architecture
- Collaborative communication – facilitates collaboration for a shared understanding of security risks
- Adaptability – flexible, iterative process that is adaptable to changes in app functionality and the evolving threat landscape
- Cost-effective measures – enables cost-effective security measures by addressing vulnerabilities early on
Fully Managed Mobile App Threat Detection and Alerting
Achieving fully managed mobile app threat detection and alerting in the cloud-native landscape involves leveraging cloud-native security services, API security gateways, mobile app analytics, and endpoint protection. Implementing cloud-based threat intelligence feeds enhances real-time threat detection. Continuous monitoring, automated alerting, and the integration of machine learning (ML) and artificial intelligence algorithms contribute to advanced threat detection capabilities, reducing mean time to detect.
Emphasizing observability through log analysis, metrics, and tracing further enhances the ability to detect and respond to security incidents swiftly. Collaboration with mobile app platforms, regular security audits, incident response planning, employee training, and compliance monitoring are crucial elements in ensuring a proactive and adaptive approach to evolving security threats in mobile app environments.
Intelligent Security Patching Mechanism
Securing cloud-based mobile apps through intelligent patching involves automated tools for real-time threat detection and prioritization. Dynamic risk assessment guides the application of patches, supported by automated deployment pipelines and rollback mechanisms. Centralized patch management through cloud-based security services, coupled with user notifications and integration into incident response plans, ensures a unified security strategy for the mobile app in a cloud context.
ML algorithms proactively address vulnerabilities, and regular compliance checks guarantee adherence to industry standards. This streamlined approach optimizes security while efficiently managing word count.
Security Challenges of Device Fragmentation
Navigating the security challenges of device fragmentation is crucial in the context of mobile apps on the cloud. Device fragmentation, arising from the diversity of devices and operating systems, poses challenges in ensuring consistent security measures. Tailoring mobile apps to function seamlessly across various devices requires addressing potential vulnerabilities specific to each platform. Security testing becomes complex due to diverse hardware capabilities and OS versions.
Additionally, managing updates and patches across fragmented devices demands an agile approach to promptly address security concerns. Cloud-based solutions can mitigate some challenges by centralizing certain security measures, but a comprehensive strategy is essential to safeguard mobile apps across the diverse landscape of fragmented devices.
Address device fragmentation security challenges by adopting cross-platform testing, centralized cloud-based measures, and agile patching. Implement device-agnostic security protocols, educate users, and collaborate with manufacturers. Utilize dynamic access controls, secure communication, and adhere to industry standards for a comprehensive strategy in managing diverse devices.
Conclusion
With an evolving landscape and trajectory of mobile and web app security within cloud-native realms, a proactive stance is paramount. Embracing dynamic threat analysis, robust API security, and nuanced considerations for serverless architectures will be imperative. Collaborative integration with DevOps teams to become DevSecOps, accompanied by automated compliance checks, will become indispensable practices to fortify digital landscapes. The recommendation is clear: As we navigate the future of app security, aligning with cloud-native principles and adopting these evolving strategies will not only safeguard against emerging threats but also pave the way for a more resilient and secure digital future.
The synergy between cloud-native principles and app security is not merely a trajectory but a dynamic evolution, fortifying digital ecosystems against emerging threats and embodying the next chapter in secure, connected experiences.
This is an article from DZone's 2023 Enterprise Security Trend Report.
For more:
Read the Report
Opinions expressed by DZone contributors are their own.

Comments