The Top Security Strategies in Custom Software Development
Data security is paramount in custom software development. Here are 6 key security strategies to ensure customs software remains secure and data is protected.
Join the DZone community and get the full member experience.
Join For FreeThe global spending on enterprise software is $605 billion.
An increasing number of companies explore custom software development to digitize their operations.
Software solutions simplify the business processes and streamline the workflow. Both B2B and B2C software development solutions enable companies to achieve operational efficiency.
A major element of creating custom enterprise software solutions is data security. The confidential data of users is an aspect that companies cannot ignore. Therefore, security plays a significant role in custom development.
Secure software development is proliferating. Companies are widely adopting the DevSecOps (Development + Security + Operations) methodology. With government restrictions coming into the picture, security and governance are now paramount.
Why Is Data Security Important?
The worldwide average cost of a data breach is $3.8 million, while 51% of organizations pay ransom to eliminate ransomware from their system.
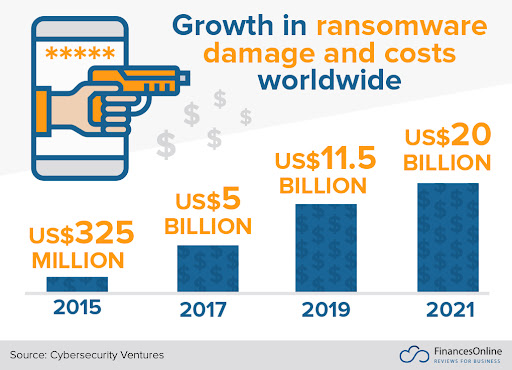
Data is a key element for every business. It enables them to derive valuable business insights and make better decisions. Unfortunately, today, data has become vulnerable due to the number of cyberattacks happening across the globe.
Security has become paramount because:
It Improves Application Quality
The quicker a team can fix bugs and repair the loopholes, the better the application will become impenetrable.
It Reduces Long-Term Costs
The cost of fixing a security vulnerability is six times more after the attack than during the development process. Therefore, better security reduces the long-term costs.
It Is Necessary for Compliance
Today, GDPR and several other regulations require companies to comply with data security policies. Not following such guidelines can result in massive fines and penalties.
So how can enterprises and companies improve their data security? What are the ways through which they can reduce cyberattacks and eliminate vulnerabilities in their systems?
Top Security Strategies for Custom Software Development
Security should be a key element in software development services. Companies that build software need to take proper precautions to ensure no vulnerabilities and threats can enter the system.
Here are the top security strategies that enterprises can follow for custom software development:
1. Secure Software Development Policy
The first thing every enterprise needs while availing of custom software development services is a secure software development policy.
Such a policy comprises the guidelines and best practices to follow during the software building process. In addition, the policy should have detailed instructions on viewing, assessing, and monitoring the application to reduce the risk of security vulnerabilities.
The policy must also disclose the responsibility of each team member in the development process. Proper training is necessary to ensure teams understand the policy and follow the standards set in the industry. It should be a mandatory document for custom software development to ensure everyone follows the guidelines.
2. Security Awareness Training
When the document for secure software development services is ready, training becomes necessary. However, it doesn't include only the policy measures and how to follow them.
Security awareness training is a comprehensive approach where developers learn about common security vulnerabilities. They also work on practical projects that help them understand the rise and fall of cyber threats in the application.
An important thing to teach in the awareness training is to help developers understand the areas where they are most likely to make mistakes. Then, when they identify the bug easily, they will eliminate it quickly.
3. Update Your Software & Systems
Today, most security vulnerabilities arise from outdated software and traditional systems. Therefore, it becomes essential to update the software and switch to modern enterprise systems.
Hackers and cyber attackers know the security threats in older software and can easily penetrate through the layer of protection. In addition, since many software tools developers use are open-source, they need a software bill of materials to keep an inventory of all the components.
Regularly patching will enable developers to stay on top of their game and secure data much better. New software patches also ensure that cyber attackers don't easily attack the system with old methodologies.
4. Conduct Regular Code Reviews
Code reviews are an important activity for enterprise software development companies. Identifying and fixing bugs in the code early in the process helps in avoiding common security pitfalls.
It is a common step to test the code and fix the bugs. However, when the application gets a little older, hackers can easily penetrate the applications. They know what the irregularities are and how to take advantage of them.
Another aspect of checking in new code is reviewing any security vulnerabilities that may arise due to code changes. Regular code reviews come in handy as they ensure that nothing is left unnoticed.
5. Data Encryption and Access Controls
Encrypting data has become a priority for custom software development. Today, no company operates without data encryption policies. In addition, there must be a secure password recovery method, strong password enforcement, and multi-factor authentication.
If there are proper access controls and people know what they can access, everyone achieves transparency. In addition, there are fewer chances of hackers entering the system when data is encrypted, and access controls are modified regularly.
Encrypting sensitive information will enable only authorized users to access it. It becomes a simple firewall that cyberattackers have trouble penetrating. Therefore, data encryption is crucial for cybersecurity in custom software development.
6. Penetration Testing
And last but not least, penetration testing is a great security strategy for software development services. Enterprises can hire a penetration testing team that provides the best solutions without the hassle.
The team will conduct security vulnerability tests and use the same tools that hackers use to evaluate the system's security. Then, when they identify the security issues, developers can easily fix them and be free from any tension.
Generally, penetration testing should be done every month or quarter to ensure the application consistently remains safe. It will also mitigate any concerns revolving around the usage of third-party software.
Conclusion
Custom software development is increasing in demand, which is why security is becoming a major concern. Data security is essential to win users' trust and ensure that confidential information will never be shared. The above 6 security strategies can help companies achieve better data protection and secure their applications.
Opinions expressed by DZone contributors are their own.

Comments