The cloud-native architecture enables organizations to build and run scalable applications in a dynamic environment. However, it does come with several challenges — security, cost, governance, observability, and more. Let us look at some of the best practices every development team working in the cloud-native space needs to embrace to secure their applications.
Zero-Trust Architecture
Zero trust is a strategic approach to rebuild and modernize security by enforcing strict access controls to protect data, applications, and networks. By inspecting and monitoring network traffic to catch any malicious activity, the zero-trust architecture helps reduce the blast radius in case of a compromise. In a cloud-native architecture that uses a combination of microservices and containers, service mesh helps reduce the surface area of attack and implement the zero-trust security model.
Pattern |
Every entity must authenticate itself, and implicit trust in data and applications is denied even within a network perimeter. |
Anti-Patterns |
Workloads are not monitored for misconfigurations and vulnerabilities. A least-privilege access strategy between components is not implemented. |
Identity and Access Management
IAM is a core component of the security management posture within an organization that enables the proper entities to access the right resources. IAM protects against compromised access, safeguards resources within the network, and provides comprehensive security against phishing and ransomware attacks.
Pattern |
Following the zero-trust model, each entity is authenticated and authorized when logging in or accessing resources. |
Anti-Patterns |
Not visualizing IAM as a framework of policies and processes — like single sign-on, multi-factor authentication — to help mitigate risk. |
Principle of Least Privilege
The least-privilege policy grants permissions to only the resources required to perform the task; no other access gets assigned. Having overprivileged users and roles in an organization increases the risk factor. With an increasing number of security breaches caused by privileged credentials, it is best to always validate policies and adopt the least-privilege principle by default.
Pattern |
As a security best practice, when you create your IAM policies, start with a minimum set of permissions and grant additional permissions as needed. |
Anti-Pattern |
Providing broad permissions increases the blast radius and risk factor. |
Secrets Management
Cloud secrets management refers to tools and methods to securely manage secrets — passwords, certificates, SSH keys, encryption keys, and API tokens. You should have a strategy to rotate your passwords periodically. Public cloud providers offer managed services to handle secrets and their management.
Pattern |
Policies and procedures for secrets management are established, documented, and communicated across the development teams in your organization. |
Anti-Pattern |
Storing sensitive credentials in code repositories. |
Incident Response
Building incident response and triaging strategies are challenging when you have microservices running in a Kubernetes cluster in a cloud-native landscape. When you treat your workloads running in containers as cattle and not pets, performing post-mortem analysis and gathering audit trail events become difficult.
Containers spin up and down frequently, and so, responding to security threats in a transient environment requires a different strategy. Incident response is critical to resolving security issues efficiently and spreading awareness within your organization about operational duties.
Pattern |
As you start creating an incident response playbook, it is crucial to have access to proper observability tools, including logs, metrics, and traces. |
Anti-Pattern |
There is no proper audit trail or monitoring to support troubleshooting activities. |
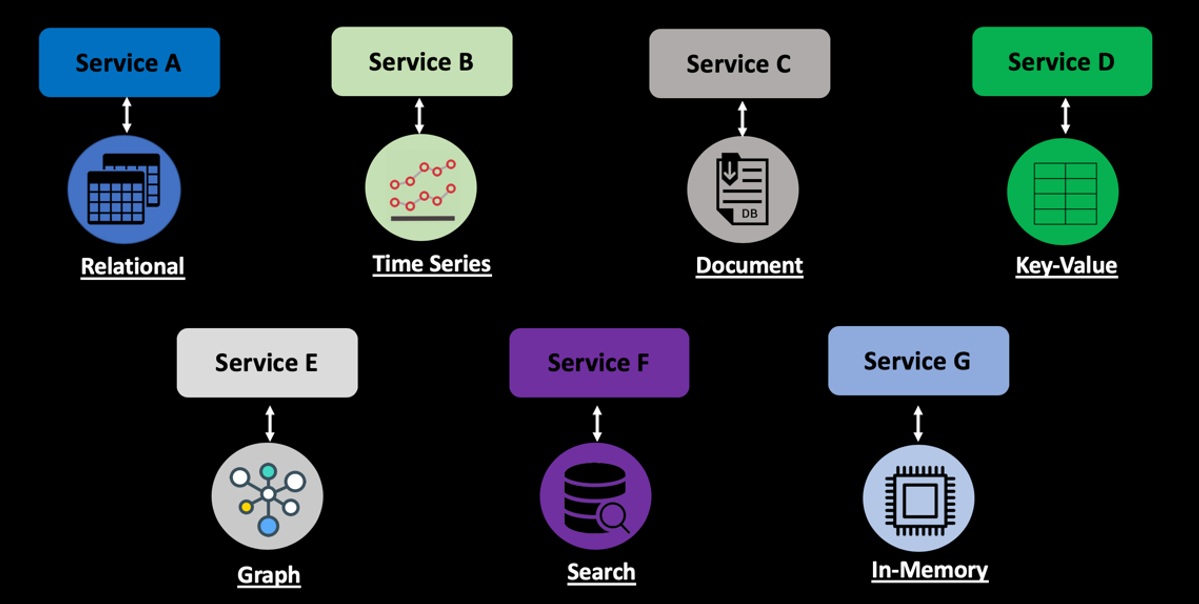
Data Protection
Cloud-native microservices support polyglot persistence, and therefore, development teams have flexibility in choosing the appropriate database technology, as seen in Figure 3, for developing their services. These datastores can store both structured and unstructured data to support a variety of functions like search, reporting, time-series, caching, transactional, etc.
Pattern |
Support critical data management functions like backup and recovery, archival, data replication, data encryption at rest, and motion. When it comes to data auditing, be aware of regulatory compliance laws set by the government like HIPAA, GDPR, and FedRAMP to protect consumer rights. |
Anti-Pattern |
Excluding data from your automated CI/CD pipeline. |
Figure 3: Polyglot persistence in cloud-native applications
Container Image Security
Many organizations are running containerized workloads in production. Containers make it easy to package, deploy and run your code, thereby increasing the speed and portability of your application. It is necessary to secure the container image to secure your environment.
Organizations can leverage open-source tools to detect anomalous behavior of applications running inside containers and send timely alerts. A continuous and automated monitoring strategy is necessary to address the increasing security risks associated with container environments. As a best practice, ensure that the images don’t contain any known vulnerabilities, do not have passwords and sensitive data included, do not contain misconfigurations, and are downloaded from trusted providers. Regularly scanning container registries in your organization is recommended to boost the quality of containerized deployments.
Pattern |
Images in popular container registries are not guaranteed to be free from vulnerabilities; hence, you should have a process for vulnerability scanning of your container images before deploying them to production. |
Anti-Pattern |
No automated strategy to periodically scan container images. |
Threat Modeling
Developing services in the public cloud can trigger new security threats like malware and ransomware. You can leverage managed services provided by cloud providers or third-party vendors that use machine learning and artificial intelligence to identify security threats and vulnerabilities across your organization.
Patterns |
Continuously monitor your cloud resources, have unified visibility into security incidents, and develop a strategy to detect unauthorized activities. |
Anti-Patterns |
No policies have been created to detect malicious activities like suspicious user actions, unsuccessful login attempts, network anomalies, and unusual activities that indicate credential compromise. |
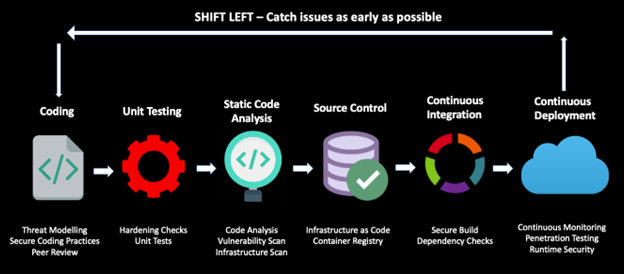
Using Infrastructure as Code
Cloud-native architectures leverage the principle of immutability to manage infrastructure resources. If you need to make any configuration changes, you don’t modify the server; instead, build a new server with the updated configuration. IaC ensures consistency between environments and enables better DevOps practices by deploying infrastructure code in an automated and repeatable manner.
Patterns |
Development and security teams can use IaC tools like Terraform, Chef, Puppet, and Ansible to create guardrails, implement policies, patch vulnerabilities, and fix configuration issues seamlessly across environments without worrying about drifts. With IaC, all your infrastructure changes are peer-reviewed and stored via source control for increased visibility. |
Anti-Pattern |
Making infrastructure changes manually, which creates configuration drifts across environments. |
Runtime Visibility
With enterprises growing their workloads rapidly and adapting multi-cluster/multi-cloud environments, it becomes crucial to have a centralized view of your systems. Furthermore, to have a sound observability strategy, you need to continuously profile your applications and collect a considerable volume of data round the clock.
Pattern |
Provide observability to the teams as a platform offering — and not something they have to build and maintain for individual services. |
Anti-Pattern |
Lack of robust security tooling to make sense of the high volume of logs, metrics, and trace data produced by your applications. |



{{ parent.title || parent.header.title}}
{{ parent.tldr }}
{{ parent.linkDescription }}
{{ parent.urlSource.name }}