Limitations
This memcached Refcard provides you with basic configuration information for servers and client-side commands to use memcached as a caching solution for your applications.
memcached is defined as “a high performance, distributed memory object caching system, generic in nature, but originally intended for use in speeding up dynamic web applications by alleviating database load” by memcached.org.
memcached works by caching data in RAM so that the number of times an application has to read an external data source is reduced. The in-memory key-value store can be used for data that would be returned from database or API calls. On top of all of this, memcached allows the cache load to be distributed across servers. However, as the data is stored in memory by default, when the server is restarted, memcached will re-initialize with an empty dataset.
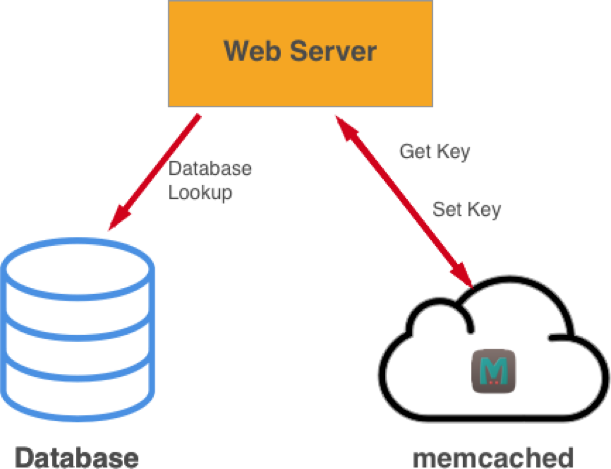
Diagram 1: Illustration of how a web server interacts with memcached and a database
There are four key limitations in memcached to keep in mind:
- The key used is a string with a maximum length of 250 bytes
- The value has a 1 megabyte size limit, which can be increased with the –I parameter
- No persistence
- It is not highly available
To install memcached on your Linux-based system, use either of the following commands, depending on the OS that it is being installed to:
apt-get install memcached(Debian / Ubuntu)yum install memcached(Red Hat / Fedora)
Once installed you can run memcached using the following command, where –d causes memcached to run as a daemon process:
memcached –p <TCP port> -U <UDP port> -u <username> -d Tip: Use memcached –h for up-to-date documentation on the memcached version you have installed on your server

