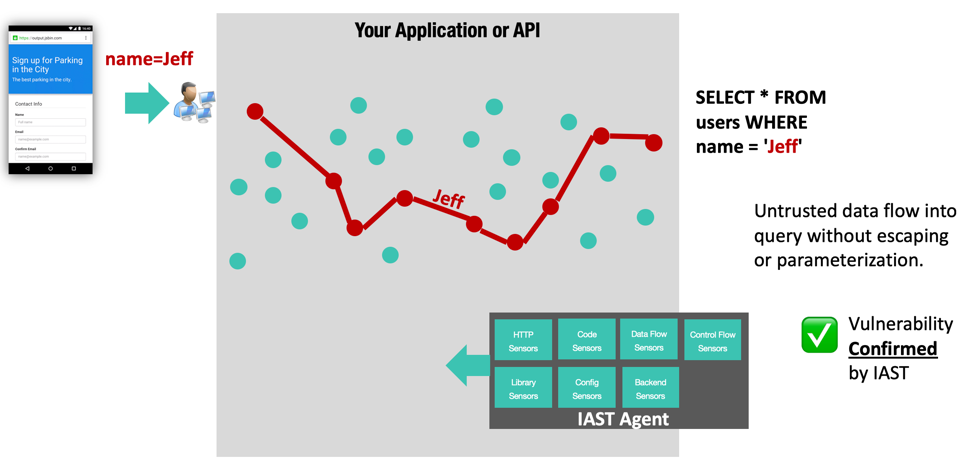
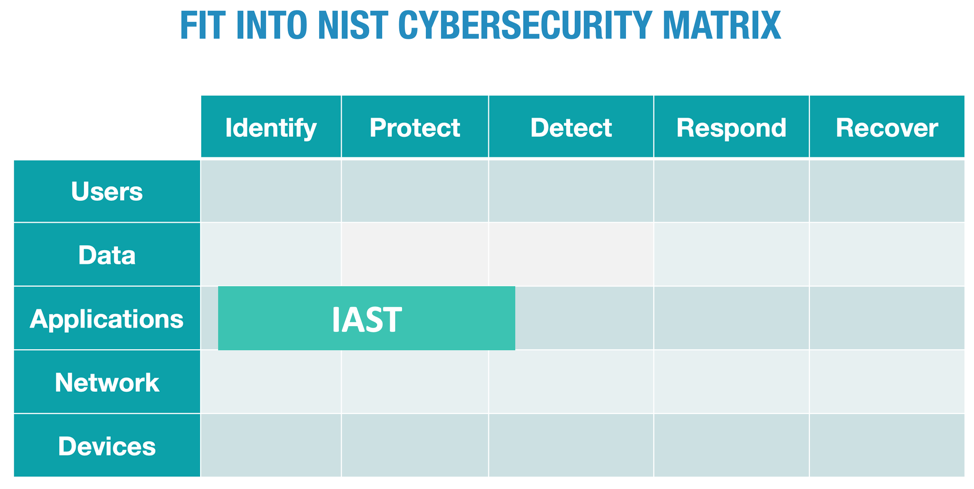
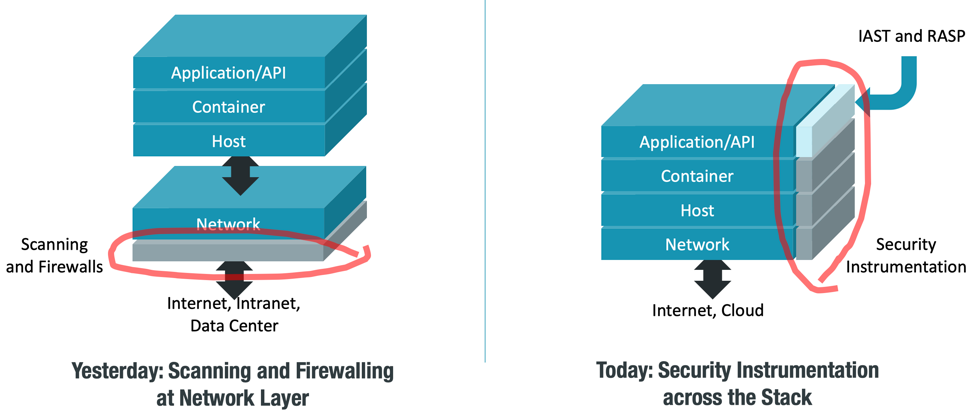
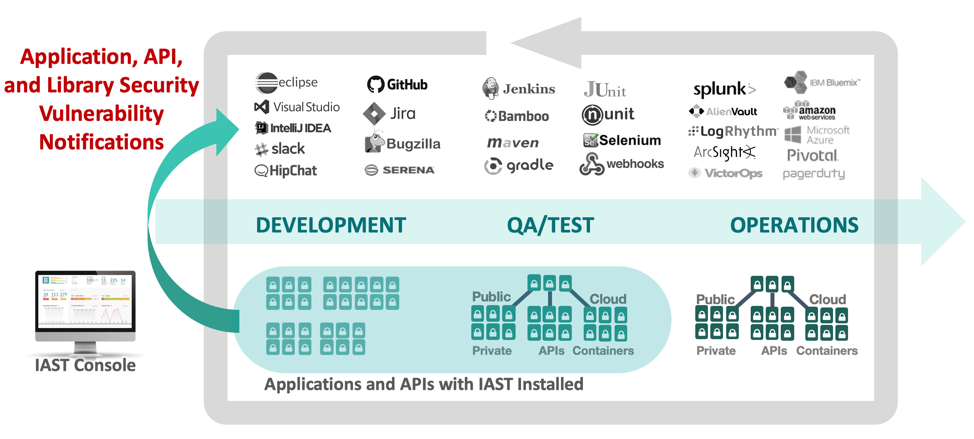
For enterprise organizations, IAST is a powerful way to establish continuous security testing across the entire application and API portfolio. With IAST, organizations can perform continuous application security testing in parallel across their entire application portfolio.
Securing the Enterprise Application Portfolio
Many organizations only test a small subset of their application portfolio for security. Some organizations only test the “critical” applications. Others have policies to test all “external facing” applications. More than likely, it won’t be your primary website that gets compromised. Instead, it’s more likely to be a partner website, an obscure mobile API, or a business app on your intranet. This is why protecting all your applications and APIs, even non-web APIs, is so critical.
Many organizations reserve security testing for what they think of as “external” or “public-facing” applications. Actually, the concept of “internal” and “external” applications is dependent on a working security perimeter. Unfortunately, the perimeter established by firewalls and other network security devices has become so porous that it is now essentially meaningless. For example, a single employee workstation that is compromised by an attacker becomes an internal attack portal that makes the perimeter irrelevant. Consider testing your entire application portfolio, including internal applications.
IAST in the Pipeline
Remember, IAST is nothing like a scanner. IAST effectively becomes part of your application. It can run anywhere that your application runs, including your developer IDE, on a local testing server, on a QA machine, as part of a CI/CD build, in a container, in the cloud, or anywhere else your code runs. You can use IAST anywhere that your software runs throughout the entire software development lifecycle. There are good reasons to use IAST extremely early in development, in integration and test environments, and also in production.
The image below depicts a simple development pipeline, using IAST throughout to identify vulnerabilities continuously.
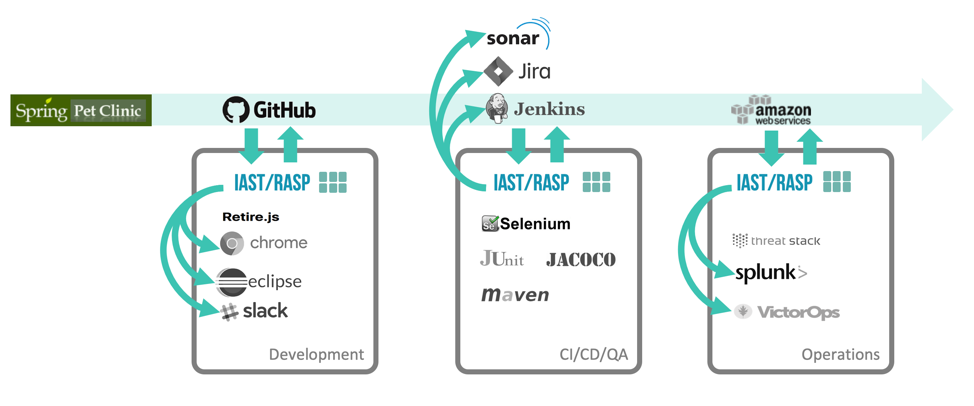
You can choose exactly which locations in your software lifecycle to use IAST. Because IAST doesn’t require any extra steps, IAST is compatible with all different approaches to software development. IAST is particularly well suited to DevOps, which is allergic to tools that require expert babysitting and take a long time to run.
Installation and Configuration
The process of installation is very simple. There are typically two parts to an IAST solution: an IAST agent and an IAST console. You create an account on the IAST console and then download the IAST agent, which performs the analysis and sends results back to the console.
The first step is to add the IAST agent to your application environment in some way. It might be as simple as adding a library, running an installer, setting an environment variable, etc… Then when you use your application, the IAST agent will automatically do the security testing in the background. Important: you don’t need to attack the application to get great security results. IAST can be used by anyone, even novice developers.
The IAST console enables you to manage security across an entire portfolio of applications in parallel. You can administer security policy, configure security controls, and set up integrations with common development tools for vulnerability notification.
Deploying IAST in Development – Process and Integrations
In development, our goal is to empower developers to find and fix their own vulnerabilities and commit clean code. But we must avoid slowing them down or giving them false positive results that waste their time.
IAST is a good match for these goals, because it provides instant feedback on exactly the code that the developer is building and testing in their local environment. IAST alerts might come through the IDE, a chat program, bugtracker, or other integration. Because IAST provides the exact line of code, the full HTTP request, and the full data and control flow, the developer’s work is made easy. They can fix the code and retest with the HTTP request to verify that the problem is resolved correctly, and check in clean code.
Deploying IAST in CI/CD and QA Environments – Process and Integrations
In the QA environment, we are looking to ensure that the developers have done the right thing and eliminated any vulnerabilities. We want confidence that the application or API is free from vulnerabilities before we push into production. We want the ability to “fail the build” in the case of serious security vulnerabilities. But we must not slow down the build or require the involvement of security experts.
IAST is a great match for security testing in QA environments, because it runs alongside your normal automated and manual tests and provides security testing automatically in the background. In these environments, the IAST notifications are typically provided through CI/CD tools and bugtrackers. Formal reports can also be generated for audit and compliance purposes.
Deploying IAST in Production
Doing security testing in production is generally not a great idea. Ideally, you would have found and fixed any security issues long before they reach production. However, there are many “legacy” applications that are no longer being actively developed. There are also third-party products that only exist in production. Yet we still need ongoing, continuous assurance that these applications are free from vulnerabilities. And we want to know if any new vulnerabilities emerge that might affect these applications.
While it is not as common as using in development or testing, IAST can also be used effectively in production. Because IAST does not require the source code, it can be used on almost any application provided it is possible to install the IAST agent. It’s important to consider the performance impact of IAST on these applications. While IAST is generally fast enough not to be noticed in development and test environments, in production even a few extra milliseconds might not be acceptable. Note that IAST often has configurations, such as “sampling mode” that can significantly improve performance in production environments, while still providing great security coverage over time.