A Complete Guide to the Stages of Penetration Testing
This article emphasizes the importance of penetration testing in business and discusses the various phases that a penetration tester should adopt.
Join the DZone community and get the full member experience.
Join For Free
As per the new study, 95 percent of all successful hacks in the companies worldwide are the result of spearfishing. This is a kind of an email spoofing that targets a particular company or individual for stealing steal sensitive information or gain a grip on the network.
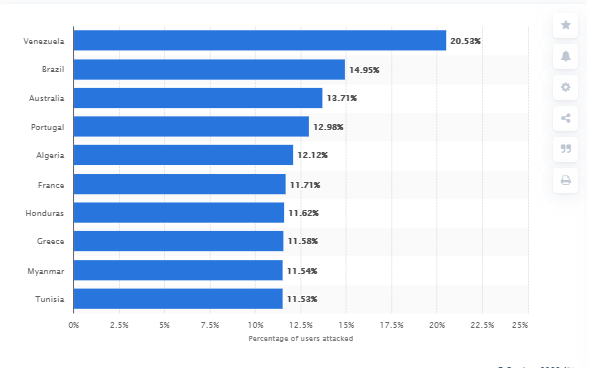
As per the Statista, fig shows the nations majorly targeted by phishing attacks globally during 1st quarter 2020
This statistic gives entire information on the nations with the most repeated occurrence of phishing attacks across the globe in the first quarter of 2020. During this period, Venezuela was ranked 1st with a rate of 20.53 % phishing attacks among online users.
With such increasing cyber attacks such as spear phishing attacks, in current years, enterprises have started concentrating on the safety features of software apps and products. In spite, applying attentive and sincere efforts towards the development of secure and safe software apps, such software products get a lack of 1 or more than 1 safety facet or feature, because of several intangible and tangible errors. Therefore, it has turned crucial to explore each vulnerable part present in the app which might invite and give the opportunity to crackers and hackers to exploit the system.
Conducting frequent penetration testing is a beneficial way to discover serious security vulnerabilities within your IT environment. The trusted testing company performs the penetration test using a thorough and methodical approach.
What Is Penetration Testing All About?
Penetration or Pen testing is the art or step to finding risks and vulnerabilities and digging deep to detect how much a target can be compromised in any sort of a legitimate attack. It also seeks to discover added security risks that often do not show on a vulnerability scan. The pen testing will involve exploiting the servers, network, firewalls, computers, etc., to discover vulnerabilities and draw attention to the practical threats involved with the recognized vulnerabilities.
Besides defined objectives, the pen testing approach may also be used for evaluating and assessing the suspicious power mechanism of the system; how capable or strong is the system to protect distinct kinds of unanticipated malicious attacks.
Companies should conduct penetration tests for the following particular reasons:
- To observe the effects of numerous vulnerabilities and how they can be grouped together
- To make certain the effectiveness of recent controls and how they are executed and configured
- To develop controls to deal with weaknesses discovered in the app, infrastructure, or process. (Software, People, and Hardware)
- To measure the effectiveness of an app’s input validation controls. Where user input is entered, a thorough fuzz test is carried out to ensure that it merely sanitized input is accepted.
- To improvise security response time. Pen testing can be used to spot how varied teams react to an intrusion and improve inner incident response procedures and processes.
How Frequently Should Pen Tests Be Done?
The regularity of penetration tests replies on numerous factors, from the kind of sector to network technology and compliance regulations. If in case there is some sort of industry compliance regulations in place, pen-testing must also be executed as essential to fulfill those necessities.
It is often suggested that a penetration test be scheduled if any of the following take place:
- Significant alterations are made to the network or infrastructure
- The security patch is functional
- New apps or infrastructure are added
- An office is added or the office location changes to the network
- Newest industry regulations necessitate additional compliance
- The increase in media awareness and attention that could augment the likelihood of an attack
How to Execute Pen Tests?
Penetration tests of a system may be performed by using any of the following approaches:
- Automated Penetration Testing
- Manual Penetration Testing
- Automated + Manual Penetration Testing
Different Stages of Penetration Tests
The typical penetration testing is broken out in various phases, alike the cyberattack lifecycle. Every single phase has a goal that they require to achieve to further the attack.
1. Gathering of Crucial Information
This is the research and study phase, where the software tester learns all they can about your employees and company externally. The software testing team will use similar resources a hacker or attacker would use to target your network, counting your company programs, website, staffs’ social media, online presence, and more.
2. Enumeration & Identification
At this phase, the software testers research your network particularly, searching for services, open ports, and apps that might be susceptible. Depending on which kind of pen testing you agree upon, the tester may collect varying degrees of information about your enterprise or identify critical information to discover entry points and vulnerabilities in your environment.
3. Vulnerability Scanning
This is the next significant phase of research and preparation where the performance tester team test manually and scan automatically for risks and vulnerabilities on the network.
The commonest parts a tester will plan and spot include:
- Business vital assets – Discover and sort out high-value assets
- Technical data
- Customer data
- Employee data
- Threats & Vulnerability – Discover and categorize external as well as internal risks
- External threats – Network Protocols, Ports, Network Traffic, Web Apps, etc.
- Internal threats – Vendors, employees, management, etc.
A QA engineer will often use a vulnerability scanner for completing a detection and record on the security threats posed by detected vulnerabilities. After that, the QA tester will authenticate if the vulnerability is exploitable. The vulnerabilities list is reported and shared at the closing stages of the pen test exercise in the reporting phase.
4. Determines the best method of attack
At this phase, all of the preparation is assembled and the QA specialists decide the best way of attack surface Analysis, counting possibilities to capitalize on network risks or vulnerabilities—eventually leading them for developing an attack preparation.
5. Penetration as well as Exploitation
Then the developed plan is putting mainly into action as those risks and vulnerabilities are exploited and the network is compromised. This is the stage where the main damage is completed. The attacker will try to grab the information, launch DoS attacks, compromise the system, etc (a resource that will steer you through cyber-security attacks). Generally, this stage is controlled in a pen test to make certain that the mayhem on the network is restricted
Some of the most common exploit tactics count:
- Physical Attacks
- Network Attacks
- Web Application Attacks
- Wi-Fi attacks
- Social engineering
- Zero-Day Angle
- Memory-based attacks
The ethical hacker or attacker will also reassess and document how threats or vulnerabilities are exploited and describe the tactics and methods used to gain access to top-value targets. Last of all, during the exploitation stage, the ethical hacker ought to explain with clearness what the outcomes were from the exploit on top-value targets.
6. Risk Analysis as well as Recommendations
After the fifth stage is complete, the objective is to get details and document the techniques used to gain access to your company’s precious information. The pen tester must be able to find out the worth of the compromised systems and any value linked with the confidential data captured.
Some QA testers are not able to quantify the influence to access data or are not capable to give recommendations on how to mitigate the vulnerabilities or any sort of threat within the environment. Make certain you ask to see a sanitized pen tests report that reveals recommendations to fix security vulnerabilities and holes.
Once the pen test recommendations are ended, the QA specialists should clean up the environment, reconfigure any access she/ he acquired to penetrate the environment, and stop future unauthorized access into the system all the way through whatever means essential.
7. Report Preparation (Goals)
Report preparation should begin with overall performance test procedures, followed by an analysis of risks and vulnerabilities. The greater crucial vulnerabilities and risks should have priorities set and then tracked by the lower order.
But, when documenting the final report, these below-mentioned points need to be considered −
- Overall synopsis of pen tests
- Descriptions of every phase and the data gathered during the pen tests
- Complete descriptions of all the risks and vulnerabilities identified
- Full description of managing and fixing the systems
- Proposal for future safety and security
Penetration Testing Limitations:
Amidst its several positives, the pen test is affected by some drawbacks as stated below:
- Pen testing aka penetration testing may put the system into a failure state or break-down the system
- Restricted time and high testing expense
- Data is vulnerable to failure, damage, or corruption
- Restricted possibility of testing based on the necessities in the specified period that might result into overlooking of other significant and vital areas.
Penetration Tests Open-source (Free) Tools:
Final Thoughts
Development in technologies has armed hackers or attackers with an extensive variety of tools and resources to effortlessly break into system and network with the intent to cause loss to your organization or you or your business reputation, assets, and name. More than simply the test process, pen-testing may be seen as a precautionary or preventive approach to spot and detect different symptoms of security deficiencies to nullify or abolish the potential security risks to the system.
Opinions expressed by DZone contributors are their own.

Comments