8 Penetration Testing Trends You Should Know in 2022
As 2022 begins, it is the perfect time to evaluate the tech trends currently shaping the future of pen testing, and how it will continue to do so going forward.
Join the DZone community and get the full member experience.
Join For Free
As a result of the pandemic’s transition to remote work, the year 2022 is also considered a year of fresh challenges and transformation. The rising demand for the safety of software-based properties like web and mobile applications is projected to enhance the growth of the global pen tests market. Moreover, the growing usage of cloud-based security services is anticipated to fuel the demand for penetration testing. Additionally, the ever-increasing digitization in developing countries is projected to boost the trend of the Internet of Things-based connected devices. This, in turn, boosts the need for pen-testing. Companies have become more prone to malicious assaults and attacks. The rising number of cyber-attacks, coupled with the increasing necessity to meet the compliance measures, is estimated to be a driver for the global pen-testing market during the estimated period. To combat such malicious attacks, penetration testing company must have to keep a close eye on growing cybersecurity trends.
In the year 2022, we will undeniably continue to see attacks on the Internet of Things devices. Edge computing gadgets – where data and information are operated on as close as possible to the point it is gathered – besides centralized cloud infrastructure is all vulnerable. Once again, awareness and instruction are two of the most valuable tools when it comes to protecting against these vulnerabilities. Any cybersecurity approach should always take account of a thorough audit of each and every device that is given access to a network or is connected and a full understanding of any vulnerability it may create. As 2022 gets underway, it is the perfect time to evaluate the tech trends presently shaping the future of pen-testing, and how it will persistently go forward.
What Exactly Is Pen Testing All About?
Pen-test is a way for enterprises for testing the security of their network with an exterior perspective. Companies appoint pen testers often called pen testers, who are capable enough of compromising systems and accessing data that is not supposed to be available. Of course, this is simply performed under supervision and with complete legal consent. It provides a very eye-opening insight into how well the cyber security measures truly stand up against cyber-attacks. Such type of testing can assist companies to discover where they have security glitches so that they do not become major concerns down the road.
The Three Kinds of Penetration Testing:
- White-box Testing: This type of penetration test is performed with all the documentation and details accessible about a network system as it was provided by the organization itself. Penetration testers have extra information to work with; however, they are still trying to discover vulnerabilities in the system.
- Black-box Testing: Unlike white-box testing, black-box testing is performed without the consent or knowledge of the target organization that is being tested, so penetration testers have to understand and figure out what data they can get access to by themselves.
- Grey-box Testing: This kind of pen testing is a blend of white and black box testing techniques where penetration testers have restricted knowledge about the target company’s systems but extra data than what would be accessible in a black box test.
Market Snapshot
- The international pen-testing market is projected to hit a CAGR of around 14.2% during 2018-2027. It is estimated to reach around $ 2.6 billion by the year 2027. As per region, the universal pen tests market is segmented into Latin America, Asia-Pacific, North America, Europe, Africa, and the Middle East. North America is estimated to hold a huge market share for the global pen test market during the estimated period.
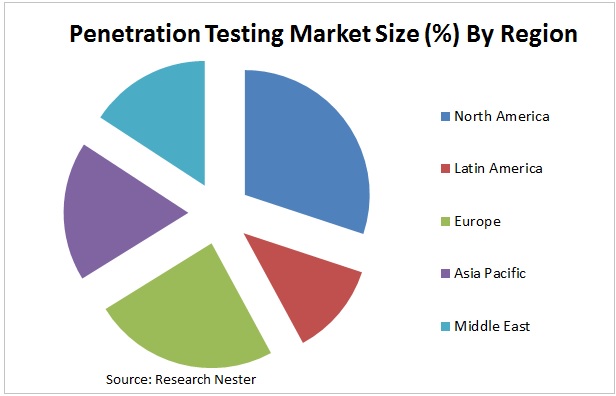
- According to the newest study Penetration Testing Market is anticipated to mature at a CAGR of 24.9% from 2017 to 2025. The pen tests market size was projected to be USD 4,426 million in 2016 and is estimated to reach USD 6,887 million by 2025, registering a CAGR (compound annual growth rate) of 24.9 percent. The pen tests industry is primarily driven by continuous cyber-attacks and mounting cybersecurity threats.
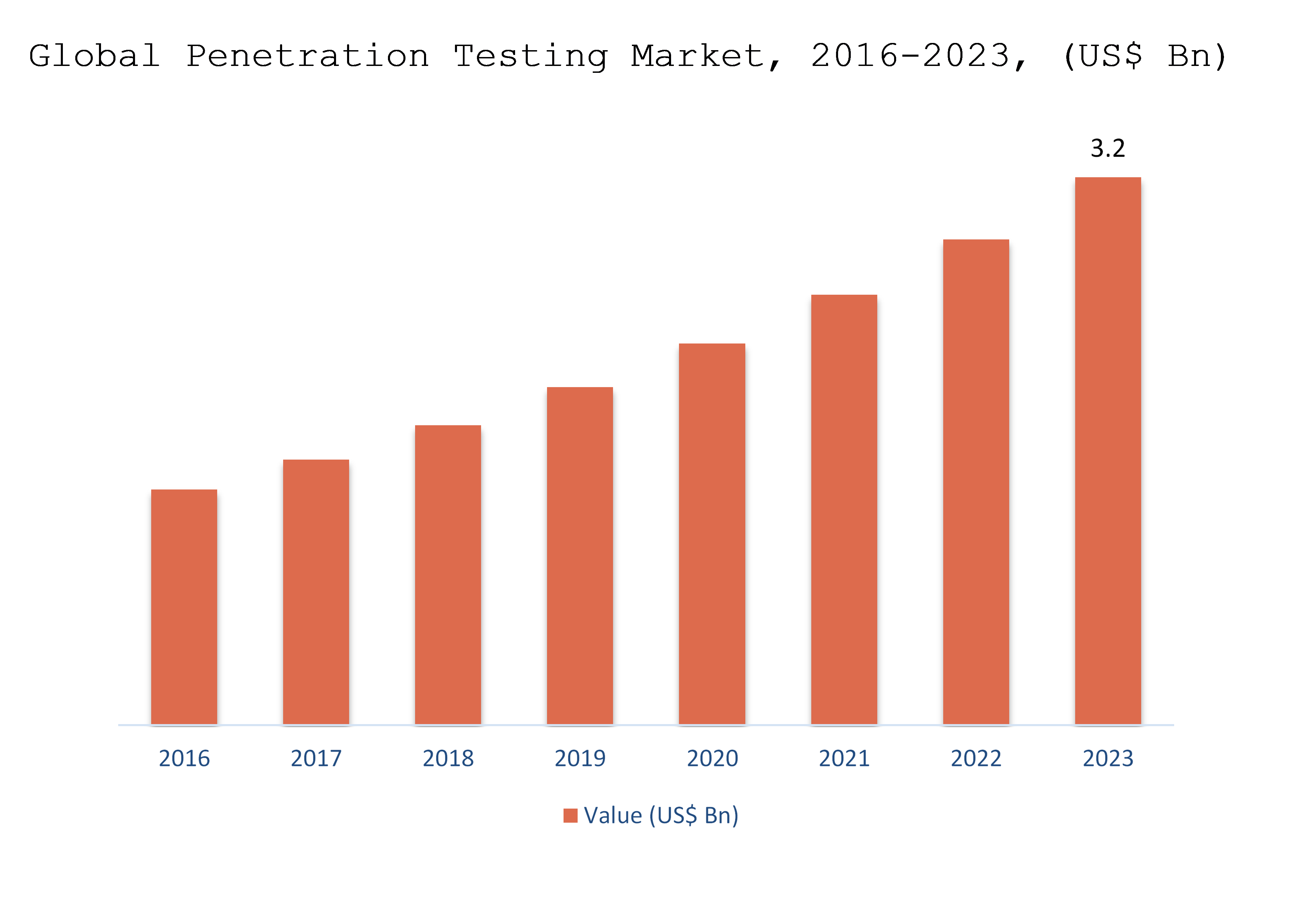
- The Pen testing market is also estimated to hit 3.2 billion and rise with a 27 percent CAGR (compound annual growth rate) during the prediction period 2016-2023
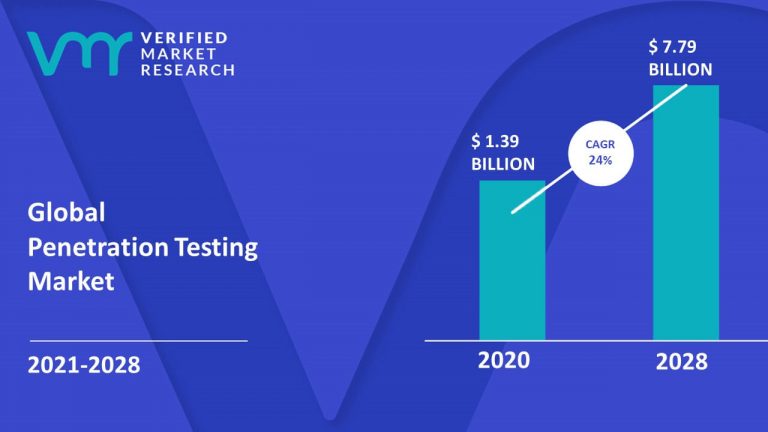
- As per Verified Market Research the Pen Testing Market size was valued at $ 1.39 Billion in 2020 and is estimated to hit USD 7.79 Billion by 2028, growing at a Compound annual growth rate (CAGR) of 24 percent from 2021 to 2028.
Competitive Landscape
The penetration testing services market is extremely competitive and comprises various major players. In terms of market share, some of the key players presently dominate the market. Such major players with an important share in the market are concentrating on enlarging their consumer base across foreign nations. These enterprises are leveraging on collaborative initiatives and strategic innovations to boost their market shares & raise their profitability. Security giants such as FireEye and Symantec have offered penetration tests for years, and other bug bounty players like Synack and Bugcrowd also carry out crowd-sourced penetration tests.
What We Can Expect To Observe in Terms of Cyber-Attacks This Year?
- Targeted attacks are presenting no signs of declining as cyber attackers or hackers become highly sophisticated and best at infiltrating networks. Due to the fact, there will also be a better need to instruct both the folks working in cybersecurity as well as those who are just trying to maintain their information secure from falling into the wrong hands.
- Additionally, we can be expecting additional attacks against mobile gadgets as more and more persons switch from their old-version computers to using tablets and smartphones. Cybersecurity will have to sustain with the ever-changing era and build up new strategies for protecting our technology against breaches.
- We can also look ahead to see more malware and ransomware attacks shortly as these shapes of attack become lucrative and highly popular for cybercriminals. Therefore, companies and individuals will need to be increasingly vigilant in safeguarding their crucial information and networks from such kind of threats.
Top 8 Penetration Testing Trends To Adapt in 2022
1. DevSecOps
DevScope is a significant factor to create safety into the DevOps model. It develops a “SaC“(security as a code) culture. While accepting this approach, one must automate security workflows. It is tremendously beneficial for the QA testers as it adopts the power of agile techniques to incorporate security tests into the development process flawlessly. In case if your company is reluctant to adopt DevOps, it offers you a reason to change and renovate. Devscopes assimilates pen tests activities by being flexible and providing rapid vulnerabilities recognition at the code level.
2. Blockchain-Centric Tech Will Increase the Stakes for Security
Crypto is on a route towards the mainstream, and it is not going to end anytime soon. Even though the blockchain tech that shapes the foundation of Bitcoin and its ilk is built with the principles of decentralization and security—and although there are several apps for blockchain in cybersecurity—it is significant to remember that this does not mean it is resistant to being hacked. Neither does it mean that security and cryptocurrency go hand-in-hand.
Take the rise of NFTs (non-fungible tokens) for instance. They are all set to be adopted by a raft of large corporations this year and beyond, however, they are also vulnerable to theft and could become the next most important focus of cybercriminals. For penetration tests, an understanding of the core technology will turn exponentially significant in the upcoming years. This is true whether your enterprise adopts crypto for consumers or leverages blockchain to safeguard data and assets.
3. Cloud-Services Attacks
Both remote and on-site workplaces now lean heavily on every kind of cloud service. Remote work has enhanced cloud security concerns, yet the threats transcend beyond the move to distributed employees. Threats count API vulnerabilities as well as traditional software issues. Flaws in the configuration as well as integration, counting authorization, and authentication, of one cloud service, can bring about broader issues. For instance, cyber attackers are leveraging vulnerable PaaS (Platform as a Service) products to extend the reach of their ransomware or malware. The rewards of the cloud are sometimes enough to outweigh the threats. Using a programmatic approach, a company can reduce the threats of increasing cloud operations and build a foundation for a safe and sound future.
4. Integrations With GRC, SIEM, and Helpdesk Systems
As constant pen tests become more integrated with patching systems and procedures, it will also be tied into overall GRC, SIEM, as well as helpdesk operations and serve to strengthen separate teams into a big cybersecurity unit. By incorporating these systems, the jobs of requesting other teams’ support to remediate vulnerabilities will be updated, automated, and organized streamlined.
When vulnerability is exposed, whether it is with a traditional piece of software or particular workflows, system, and notifications will automatically activate to inform the liable teams and suggest remedial actions. When the issue is mitigated, the continuous pen tests platform's ties into remediation tracking will notify the security team that they can obtain that fix off the to-do listing and move on to other jobs and responsibilities.
5. Artificial Intelligence(AI)-Centric Cybersecurity
Artificial intelligence (AI) can counteract attacks or cybercrime by determining patterns of behavior that denote something extraordinary or unusual may be taking place. Significantly, AI means this can be done in systems that require coping with hundreds of events taking place each second, which is usually where cybercriminals will try to strike. It is the predictive powers of Artificial intelligence that make it so constructive here, which is why more and more enterprises will be investing in these solutions as we move into 2022.
Sadly, cybercriminals or attackers are also aware of the rewards of Artificial Intelligence, and new risks are emerging that use technologies like ML (machine learning) to elude the protective ways of cyber-security. This makes Artificial Intelligence even more essential – as it’s the only hope of counteracting AI-powered cyber-attacks. The current research recently revealed that companies now believe Artificial Intelligence is important to determining and countering critical cybersecurity risks, and nearly 3 quarters of companies are using or testing Artificial Intelligence for this purpose.
6. Machine Learning (ML)
Machine learning is playing a more proactive and larger role in cybersecurity. Cybersecurity becomes simpler, less expensive, and more effective with ML. Machine learning creates patterns and manipulates them with algorithms utilizing a huge dataset. It can forecast and react to active attacks in real-time in this way. To generate effectual algorithms, this technology principally relies on complex and extensive data. The data should come from a range of sources and represent as many diverse scenarios as possible. As a result of Machine learning implementation, cybersecurity systems can calculate attack patterns and learn the cybercriminal’s behaviors. These help in the prevention of future threats and reduce the time needed for cybersecurity experts to perform basic operations.
7. The Rising Threat of Ransomware
The new research by PwC revealed that technology executives anticipate ransomware attacks to increase in the year 2022. We can blame this on the deadly disease, and the development in the amount of action performed online and in digital environments. Ransomware usually includes infecting gadgets with a virus that locks files away behind firm cryptography and threatens to demolish them unless a ransom is paid, generally in the shape of untraceable cryptocurrency. On the flip hand, the software virus may terrorize publishing the data publicly, leaving the company liable to massive fines.
Ransomware is naturally deployed via. phishing attacks – where workers of an organization are tricked into offering details or clicking a link that downloads the malware or ransomware software onto a system. But, currently, a direct infection via USB devices by folks who have physical access to gadgets is becoming ever more common. Education is the highly effective means of tackling this risk, with research revealing that employees who are aware of the threats of this kind of attack are nine times less likely to fall prey.
8. Environment-Friendly 5G Networks
For data exchange & self-control, the current digital revolution is greatly reliant on gadget connectivity. To perform so powerfully, a top-performance network is essential, and 5G technology is suitable for the job. Given an intelligent city’s dependency on telecommunications that links and connects every single thing, several nations have declared 5G networks to be nationwide infrastructure. Their safety has to turn out to be a concern of national security. In a term, “security by design” is crucial for a secure 5G network, as it tackles security threats from the start. Following the COVID-19 outburst, an increasing number of nations appear to be following the US government’s lead in labeling the handful of companies as untrustworthy suppliers. Whilst such incidents may be enthused by political concerns, one thing is sure: they aren’t going away anytime soon.
Nobody knows what the future holds for cybersecurity, and several verticals are still working out how to safeguard their networks amid the pandemic’s uncertainty and confusion. But, these recent trends give us a sight of what we might be expecting in the upcoming years. IT security administrators and software developers will be in heavy demand for decades to come.
5 Best Security Test Tools of 2022
There are several tools used for security tests, however, here we are going to talk about the topmost vulnerability evaluation and pen test tools that are commonly used while executing security tests.
1. Burp Suite
Burp Suite by Portswigger Web Security is the world’s commonly used web application security test software. It comes in two versions – Burp Suite experts for hands-on testers, & Burp Suite Enterprise Edition with Continuous integration and scalable automation. It is found in most pen test toolkits, even though its power is more on the scanning part than on penetration. Though there is a free version accessible, it is restricted in functionality, with no automation capacities. Those interested in the total package for enterprise-wide automation and scalability should be equipped to pay well.
2. AppScan
Earlier called IBM AppScan is now referred HCL Appscan standard is the best web app security testing tool. AppScan is a robust analysis test tool designed for penetration testing experts and security experts to use when performing security testing on web apps. The item scans the behavior of every app, whether an internally developed app or an off-the-shelf app and develops a program intended for testing all of its functions for both common & app-precise vulnerabilities. This family of product is capable to execute IAST, DAST, SAST, and Mobile Analysis against the source code of the users and verify for vulnerabilities.
3. Nmap
The Nmap is an open-source and free tool for security auditing and network discovery. Network Mapper is used for identifying the live host on the network (host discovery), also discovering the host’s open ports. It is a port scanner more than a pen test tool. However, it assists penetration tests by flagging the better zones to target in an attack. That is helpful for ethical hackers to determine network flaws. It is handy and familiar with the open-source arena, yet it may be a challenge for a few newer to such apps. Even though it runs on all major Operating Systems, Linux users will find it highly familiar.
4. Nessus
It is a remote security scanning tool used at some stage in a pen test and vulnerability assessment. Nessus is an open-source and free tool for non-enterprises usage. It scans for vulnerabilities on UNIX and Windows systems, these traits make this tool all-rounder. Nessus tool is best for penetration experts and security test teams. This tool is probably better for skilled security teams, as its interface can be slight tricky to master in the beginning. It should be used in combination with penetration test tools, offering them areas to target & potential threats to exploit.
5. Metasploit
It is a famous hacking and pen-testing tool. This framework makes finding vulnerabilities very easy and is often used to test for computer system vulnerability. Metasploit finds security issues, manages security assessments & verifies vulnerability mitigations. It counts the scanning as well as testing of threats and vulnerabilities. Backed by a large open-source database of known exploits, it offers IT security experts an analysis of penetration test outcomes so remediation steps can be done effectively. But, it does not scale up to enterprise-level & few users say it is hard to use at first.
Key Players
According “Global Penetration Testing Market” study report a valuable insight with an emphasis on the international market counting some of the key players like Checkmarx, IBM Corporation, Veracode, Qualys, Inc., Trustwave Holdings, Inc., Cigital, Inc., Whitehat Security, Acunitix, Rapid7, Inc., Hewlett Packard Enterprise, etc.
Future Scope
Because of the low capacity and cost to scale down or scale up the business with no investment, cloud-based storage is now selected by industries over old-version physical servers. Each year, Apple expenses more than USD 306 million on AWS cloud. Likewise, Amazon made around USD 25 billion in returns from its AWS cloud computing services in the year 2018. Such cloud-centric systems are subject to threat and then hacking and should be protected from damaging and malicious malware. The well-known financial firm, Capital One, was hit with a cloud computing susceptibility in the year 2019, exposing the information of 106 million credit card users. Therefore, penetration testing services is becoming a crucial aspect of cloud computing platforms to ensure extra security, and it is estimated to grow at a rapid rate with the cloud computing business.
Opinions expressed by DZone contributors are their own.

Comments