STRIDE: A Guide to Threat Modeling and Secure Implementation
Cloud monitoring is a gold mine for attackers. This guide breaks down STRIDE threat modeling for cloud data ingestion, processing, and storage.
Join the DZone community and get the full member experience.
Join For FreeThreat modeling is often perceived as an intimidating exercise reserved for security experts. However, this perception is misleading. Threat modeling is designed to help envision a system or application from an attacker's perspective. Developers can also adopt this approach to design secure systems from the ground up. This article uses real-world implementation patterns to explore a practical threat model for a cloud monitoring system.

What Is Threat Modeling?
Shostack (2014) states that threat modeling is "a structured approach to identifying, evaluating, and mitigating risks to system security." Simply put, it requires developers and architects to visualize a system from an attacker’s perspective. Entry points, exit points, and system boundaries are evaluated to understand how they could be compromised. An effective threat model blends architectural precision with detective-like analysis. Threat modeling is not a one-time task but an ongoing process that evolves as systems change and new threats emerge.
Let’s apply this methodology to a cloud monitoring system.
Applying Threat Modeling to Cloud Monitoring Systems
Threat modeling in cloud monitoring systems helps identify potential vulnerabilities in data collection, processing, and storage components. Since these systems handle sensitive logs and operational data, ensuring their security is paramount. Cloud environments, due to their dynamic and distributed nature, present unique challenges and opportunities for threat modeling.
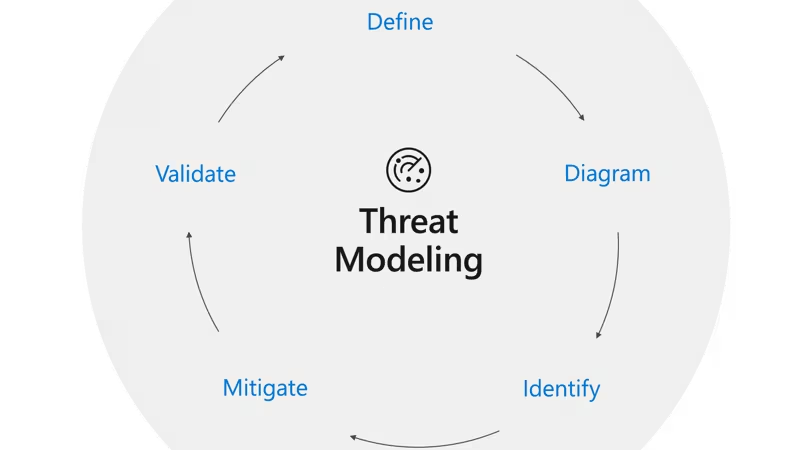
Key Steps
- Define the system scope. Identify all components involved, including data sources (log producers), flow paths, and endpoints.
- Identify security objectives. Protect data confidentiality, integrity, and availability throughout its lifecycle.
- Map data flows. Understand how data moves through the system — from ingestion to processing to storage. Data flow diagrams (DFDs) are beneficial for visualizing these pathways.
- Identify threats. Use a methodology like STRIDE to categorize potential threats for each component.
- Develop mitigation strategies. Implement controls to reduce risks identified in the threat model.
System Design: The Foundation
Consider a standard cloud monitoring setup that handles log ingestion and processing. Here’s how the architecture typically flows:
Architecture Flow
Log Producer → Load Balancer → Ingestion Service → Processing Pipeline → Storage Layer
Security Measures
- Authentication
- Rate limiting
- Data validation
- Encryption
This structure ensures efficient data flow while maintaining strong security at every stage. Each layer is designed to minimize potential vulnerabilities and limit the impact of any breach.
Key Data Flows
- Secure data transmission. Log producers send data via secure API endpoints, ensuring that data in transit is encrypted.
- Traffic distribution. Load balancers distribute incoming requests efficiently to prevent bottlenecks and mitigate DoS attacks.
- Data validation. The ingestion service validates and batches logs, ensuring data integrity and reducing the risk of injection attacks.
- Data transformation. The processing pipeline transforms the data, applying checks to maintain consistency and detect anomalies.
- Data storage. The storage layer ensures encrypted data management, protecting data at rest from unauthorized access.
Threat Identification With STRIDE
The STRIDE framework (Hernan et al., 2006) has been widely adopted in the industry due to its structured and methodical approach to identifying security threats. Originally developed at Microsoft, STRIDE provides a categorization system that helps security teams systematically analyze vulnerabilities in software systems.
Because it breaks down threats into clear categories — spoofing, tampering, repudiation, information disclosure, denial of service, and elevation of privilege — it has remained one of the most widely used methodologies in security threat modeling.
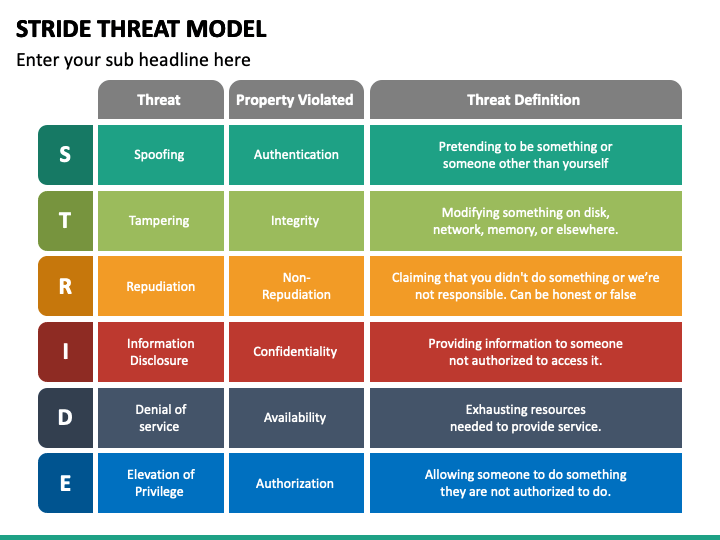
The threat categories are categorized as follows:
- Spoofing – Impersonating identities, leading to unauthorized access
- Tampering – Altering data, which can compromise integrity
- Repudiation – Denying actions or transactions, complicating audits and accountability
- Information disclosure – Unauthorized access to sensitive data, risking confidentiality breaches
- Denial of service – Disrupting service availability, impacting business operations
- Elevation of privilege – Gaining unauthorized system access, escalating user privileges beyond intended limits
Let us identify potential threats to this setup using the STRIDE categories.
| Component | Threat Type | Potential Threats | mitigation strategies |
|---|---|---|---|
|
Load Balancer |
Spoofing |
Credential theft, IP spoofing |
Use short-lived credentials, IP filtering, secure metadata |
|
Tampering |
Protocol downgrade attacks |
Enforce TLS 1.3, strict transport security, secure cipher suites |
|
|
Ingestion Service |
Denial of Service (DoS) |
Resource exhaustion via large request volumes |
Implement adaptive rate limiting, input validation |
|
Information Disclosure |
Data leakage due to improper validation |
Data encryption, strong access controls, input sanitization |
|
|
Processing Pipeline |
Tampering |
Data integrity compromise during transformation |
Data validation, checksums, integrity monitoring |
|
Repudiation |
Lack of audit trails for changes |
Enable comprehensive logging, audit trails |
|
|
Storage Layer |
Information Disclosure |
Unauthorized data access |
Encrypt data at rest, access control policies |
|
Elevation of Privilege |
Privilege escalation to gain unauthorized data access |
Principle of least privilege, regular access reviews |
As we see in this table, effective threat modeling combines systematic analysis with practical implementation. By identifying potential threats and applying targeted controls, organizations can significantly enhance the security and resilience of their cloud monitoring systems.
Secure Ingestion Service Implementation
A crucial part of the cloud monitoring system is the ingestion service. Below is a very rudimentary implementation that incorporates rate limiting, validation, and encryption to secure log ingestion:
@Validated
public class LogIngestionService {
private final EncryptionClient encryptionClient;
private final ValidationService validationService;
private final RateLimiter rateLimiter;
@Transactional
public ProcessingResult ingestLogs(LogBatch batch) {
// Rate limiting implementation
if (!rateLimiter.tryAcquire(batch.getSize())) {
throw new ThrottlingException("Rate limit exceeded");
}
// Batch validation
ValidationResult validation = validationService.validateBatch(batch);
if (!validation.isValid()) {
throw new ValidationException(validation.getErrors());
}
// Process events
List<ProcessedLog> processedLogs = batch.getEvents()
.stream()
.map(this::processLogEvent)
.collect(Collectors.toList());
// Encrypt sensitive data
List<EncryptedLog> encryptedLogs = processedLogs
.stream()
.map(log -> encryptLog(log))
.collect(Collectors.toList());
// Durable storage
return storageService.storeWithReplication(encryptedLogs);
}
}Future Work
Threat modeling is an evolving discipline. As cloud technologies change, new threats will emerge. Organizations should continuously refine their threat models, integrating updated security frameworks and leveraging automation where possible. The next steps for improving cloud security include:

- Enhancing threat modeling with AI-driven security analytics.
- Implementing continuous security assessments in CI/CD pipelines.
- Leveraging automated tools for real-time anomaly detection and response.
- Additional security controls such as adaptive rate limiting and real-time security monitoring can be incorporated into future iterations of this cloud monitoring system.
Conclusion
Threat modeling, particularly using the STRIDE framework, helps developers and security teams proactively identify and mitigate risks in cloud monitoring systems. The structured approach of STRIDE, combined with real-world security controls, ensures better protection of sensitive operational data. Organizations that embed threat modeling into their security strategy will be better equipped to handle evolving cybersecurity challenges.
References
- Chen, S., et al. (2020). “Adaptive Rate Limiting in Cloud Systems.” IEEE Security & Privacy.
- Hernan, S., et al. (2006). “Threat Modeling: The STRIDE Approach.” MSDN Magazine.
- McGraw, G. (2006). Software Security: Building Security In.
- NIST (2011). Special Publication 800-137: Continuous Monitoring.
- OWASP (2023). Application Security Verification Standard 4.0.3.
- Saltzer, J. H., & Schroeder, M. D. (1975). “The Protection of Information in Computer Systems.” IEEE.
- Shostack, A. (2014). Threat Modeling: Designing for Security.
Opinions expressed by DZone contributors are their own.

Comments