A Comprehensive Approach To Enhancing IoT Security With Artificial Intelligence
Transform IoT security with AI-powered solutions. Safeguard your devices from potential threats for end-to-end protection in digital transformation.
Join the DZone community and get the full member experience.
Join For FreeIn today's interconnected society, the Internet of Things (IoT) has seamlessly integrated itself into our daily lives. From smart homes to industrial automation, the number of IoT devices continues to grow exponentially. However, along with these advancements comes the need for robust security measures to protect the sensitive data flowing through these interconnected devices. It is predicted that the global IoT security market will grow significantly. This growth results from the increasing deployment of IoT devices and the growing sophistication of cyberattacks. According to Markets and Markets, the size of the global IoT security market will increase from USD 20.9 billion in 2023 to USD 59.2 billion by 2028 at a Compound Annual Growth Rate (CAGR) of 23.1%. This article explores the challenges of IoT security and how Artificial Intelligence (AI) can be an effective approach to addressing these challenges.
Artificial intelligence (AI) can significantly enhance IoT security by analyzing vast data volumes to pinpoint potential threats like malware or unauthorized access, along with identifying anomalies in device behavior that may signal a breach. This integration of AI and IoT security strategies has emerged as a powerful response to these challenges. IoT security encompasses safeguarding devices, networks, and data against unauthorized access, tampering, and malicious activities. Given the proliferation of IoT devices and the critical concern of securing their generated data, various measures are vital, including data encryption, authentication, access control, threat detection, and ensuring up-to-date firmware and software.
Understanding IoT Security Challenges
The IoT has brought about several advancements and convenience through interconnected devices. However, this connectivity has also given rise to significant security challenges. Let us see those challenges below.
Remote Exposure and Vulnerability
The basic architecture of IoT devices, which is designed for seamless internet connectivity, introduces a significant remote exposure challenge. As a result, they are vulnerable to data breaches initiated by third parties. Because of the inherent accessibility, attackers can infiltrate systems, remotely manipulates devices, and execute malicious activities. These vulnerabilities enable the effectiveness of tactics like phishing attacks. To mitigate this challenge, IoT security strategies must encompass rigorous intrusion detection systems that analyze network traffic patterns, device interactions, and anomalies. Employing technologies like AI and machine learning, and behavior analysis can identify irregularities indicative of unauthorized access, allowing for real-time response and mitigation. Furthermore, to strengthen the security of IoT devices, asset protection, secure boot processes, encryption, and robust access controls must be implemented at every entry point, which includes cloud security.
Industry Transformation and Cybersecurity Preparedness
The seamless integration of IoT devices within digital transformation industries such as automotive and healthcare introduces a critical cybersecurity challenge. While these devices enhance efficiency, their increased reliance on interconnected technology enhances the impact of successful data breaches. A comprehensive cybersecurity framework is required due to the complex interplay of IoT devices, legacy systems, and data flows. To address this issue, businesses must implement proactive threat modeling and risk assessment practices. Penetration testing, continuous monitoring, and threat intelligence might help in the early detection of vulnerabilities and deploying appropriate solutions. Setting industry-specific security standards, encouraging cross-industry collaboration, and prioritizing security investments are critical steps in improving preparedness for evolving cyber threats.
Resource-Constrained Device Security
IoT devices with limited processing power and memory present a significant technical challenge for implementing effective security. Devices in the automotive sector, such as Bluetooth-enabled ones, face resource constraints that limit the deployment of traditional security mechanisms, such as powerful firewalls or resource-intensive antivirus software. To address this challenge, security approaches must emphasize resource-efficient cryptographic protocols and lightweight encryption algorithms that maintain data integrity and confidentiality without overwhelming device resources. Adopting device-specific security policies and runtime protection mechanisms can also dynamically adapt to resource constraints while providing continuous cyber threat defense. Balancing security needs with resource constraints remains a top priority in IoT device security strategies. Implementing device-specific security policies and runtime protection mechanisms can also dynamically adapt to resource constraints while providing continuous cyber threat defense. Balancing security needs with resource constraints remains a top priority in IoT device security strategies.
AI's Effective Approach to Addressing IoT Security Challenges
AI can significantly enhance IoT security. By leveraging AI's advanced capabilities in data analysis and pattern recognition, IoT security systems can become more intelligent and adaptive. Some of the ways AI can enhance IoT security include:
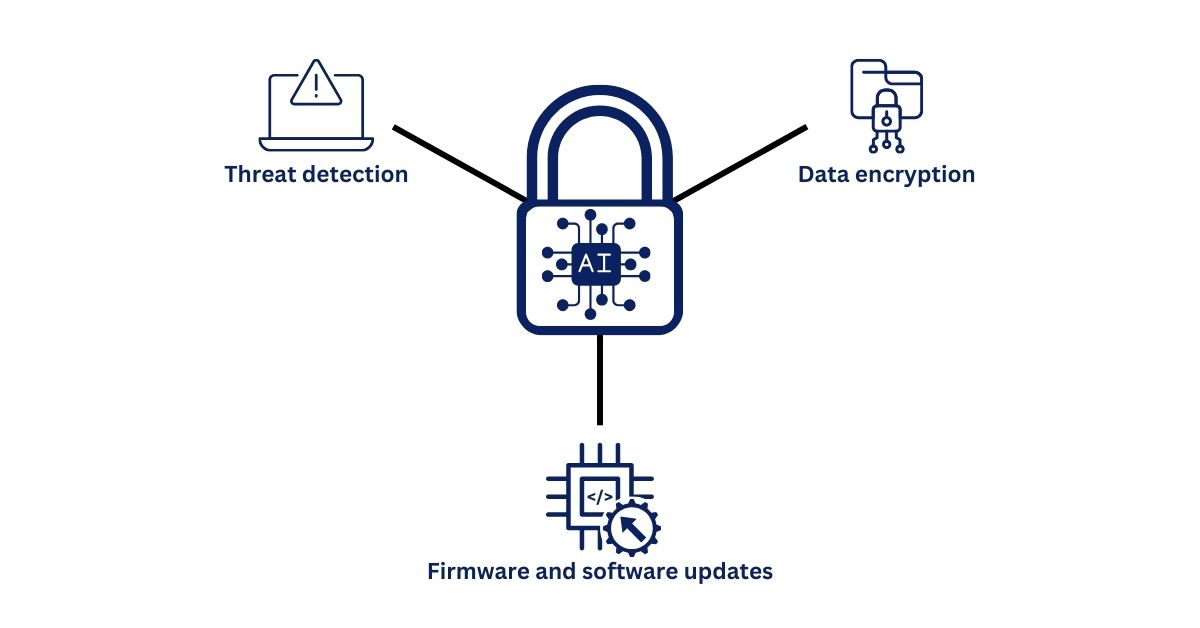
Threat Detection and Authentication/Access Control
Integrating AI in IoT devices enhances both threat detection and authentication/access control mechanisms. AI's exceptional ability to detect anomalies and patterns in real time enables proactive threat detection, reducing the risk of data breaches or unauthorized access. By leveraging advanced AI and machine learning algorithms, network traffic patterns and device behavior can be expertly evaluated, distinguishing between legitimate activities and potential threats. Moreover, AI-powered authentication and access control systems utilize machine learning techniques to detect complex user behavior patterns and identify potential unauthorized access attempts. This combination of AI algorithms and authentication raises the security bar, ensuring that only authorized users interact with IoT devices while preventing unauthorized access. Overall, the integration of AI improves device security through refined threat detection and adaptive authentication mechanisms.
Data Encryption
AI can revolutionize data protection in IoT networks by developing strong encryption algorithms. These algorithms can dynamically adapt encryption protocols based on traffic patterns and data sensitivity, thanks to AI's predictive capabilities. Furthermore, AI-powered encryption key management promotes secure key exchange and storage. The role of AI in encryption goes beyond algorithms to include the efficient management of passwords, which are the foundation of data privacy. The combination of AI and encryption improves data security on multiple levels, from algorithmic improvements to key management optimization.
AI's approach towards IoT security challenges
Firmware and Software Updates
AI-powered systems are proficient at maintaining IoT devices that are protected against changing threats. By leveraging AI's capacity for pattern recognition and prediction, these systems can automate the identification of vulnerabilities that necessitate firmware and software updates. The AI-driven automation streamlines the update process, ensuring minimal latency between vulnerability discovery and implementation of necessary patches. This not only improves the security posture of IoT devices but also reduces the load on human-intensive update management processes. The synergy of AI and update management constitutes a proactive stance against potential threats.
The Future of AI and IoT Security
The intersection of AI and IoT is an area of rapid development and innovation. As AI technology progresses, we can expect further advancements in IoT security. AI systems will become more intelligent, capable of adapting to new, emerging threats and thwarting sophisticated attacks. Additionally, AI engineering and machine learning development will drive the creation of more advanced and specialized IoT security solutions.
In conclusion, the security of IoT devices and networks is of paramount importance in our increasingly connected world. The comprehensive approach of integrating Artificial Intelligence and Machine Learning services can greatly enhance IoT security by detecting threats, encrypting data, enforcing authentication and access control, and automating firmware and software updates. As the field continues to advance, AI solutions will become indispensable in protecting our IoT ecosystems and preserving the privacy and integrity of the data they generate.
Published at DZone with permission of Ambuj Nandanwar. See the original article here.
Opinions expressed by DZone contributors are their own.

Comments