A Discussion on Managing Vulnerabilities
Breaches are common due to unpatched vulnerabilities. Learn why a strong vulnerability management program is crucial for any security strategy.
Join the DZone community and get the full member experience.
Join For FreeLeaks and breaches are becoming a frequent concern. The saying "information is the new oil" highlights the immense value of data and information, making them targets for both legitimate businesses and criminals. Most security breaches stem from exploiting vulnerabilities, some of which may be unknown or not properly managed. Hence, a robust vulnerability management strategy is essential for any comprehensive information security program.
Vulnerability management involves more than just generating reports via scans (often formatted in Excel or PDF). Since vulnerabilities pose risks and new ones emerge daily, they constantly alter the landscape of existing security risks.
Why prioritize vulnerability management? While numerous reasons exist, two particularly stand out.
Firstly, it's considered best practice and part of due diligence. Although some frameworks lean more towards compliance than actual security, they are instrumental in guiding the development and evaluation of a cybersecurity program. For example, the CIS Controls framework provides a comprehensive set of controls to aid organizations in enhancing their information security. It categorizes controls into Basic, Foundation, and Organization levels, tailored according to an organization's security maturity, information sensitivity, and business type. More details on this can be found in their resources online. Notably, continuous vulnerability management is a fundamental aspect of any information security program according to the CIS Controls framework.
The Foundation of Security: Visibility and Control
The first principle, the Foundational level, emphasizes visibility and control. This makes perfect sense: you can't protect what you can't see or manage.
But let's face it, sometimes the importance of foundational practices isn't readily apparent. So, let's explore another reason for a strong vulnerability management program.
The Equifax Example: A Case of Patching Neglect
Remember the massive Equifax data breach in 2017? A staggering 143 million customers were affected. This breach occurred because of a known flaw in a popular Java framework called Struts.
A patch fixing this flaw was released in March 2017. Yet, just three days later, attackers were already actively exploiting it. Shockingly, Equifax was compromised roughly two months after the patch became available.
The takeaway? This breach could have been prevented with a simple patch.
Vulnerability Management: Due Diligence in Action
A vulnerability management program demonstrates that your organization is actively working to secure its systems. It's a key indicator of due diligence.
The Unseen Protector: Like Car Maintenance
Think about it like car ownership. Buying a new car is exciting, but the ongoing costs of maintenance and insurance can be a drag.
Vulnerability management is similar. It's a continuous, often unseen effort that doesn't win awards, but it's essential for preventing major problems down the road.

The significant challenge is to demonstrate the value of a vulnerability management program, ensuring that teams tasked with remediation are addressing the right issues and effectively reducing risk, rather than merely applying patches in a perpetual cycle.
Answer: Prioritization
During a vulnerability assessment, any given environment will reveal a high number of vulnerabilities, regardless of its maturity level. The sheer volume of newly reported vulnerabilities can be overwhelming, making the goal of fixing all of them unrealistic and setting the program up for failure. So, what’s the best approach?
Focus on Exploited Vulnerabilities
In a time when both human and financial resources must be optimized, why expend considerable effort patching every system for a medium-criticality vulnerability that lacks an active exploit? The phrase "exploited in the wild" is critical here—it refers to vulnerabilities for which there is an active, mature exploit affecting a recent, critical vulnerability. These are the issues that truly need prioritization.
A commonly used method for this prioritization is the CVSS Score, which assesses factors like the criticality, impact, and notoriety of a vulnerability. Yet, this scoring isn't always contextual enough. Modern vulnerability assessment tools enhance this by providing more tailored metrics of real risk, for example:
- The current level of exploitation activity for a specific vulnerability.
- Future trends that could pose larger threats.
- The comparative importance of different assets to the business, guiding prioritization efforts.
Setting Up a Vulnerability Management Program
This discussion aims to align us on why a vulnerability management program is critical and the pitfalls it might face. Establishing such a program requires understanding its importance and the practical steps necessary for its implementation and success.
Building a Successful Vulnerability Management Program: Key Ingredients
Here's a breakdown of some crucial elements for building a successful vulnerability management program:
Program Sign-Off and Accreditation
This isn't just about a signature on a piece of paper. Program sign-off signifies a shared understanding among stakeholders of the program's importance and a commitment to its success. The form of accreditation can vary depending on your organization (size, culture, maturity). It could be a formal policy signed by senior management or a documented agreement between involved teams. The key is to ensure everyone understands that the program's success is crucial for your overall risk management and business continuity strategy.
Metrics, SLAs, and KPIs
- Metrics are the measurements that track your program's effectiveness. Examples include the number of vulnerabilities identified, the time it takes to patch vulnerabilities, and the percentage of systems that are compliant with your security policies.
- SLAs (Service Level Agreements) define the expected performance standards for different aspects of the program. For example, an SLA might specify how quickly a critical vulnerability needs to be patched.
- KPIs (Key Performance Indicators) are a specific set of metrics that are most important for measuring the overall success of your program. These should be aligned with your organization's security goals.
Vulnerability Management Process and Policy
This defines the steps involved in identifying, classifying, prioritizing, remediating, and retesting vulnerabilities. The policy establishes clear guidelines for vulnerability management activities, including roles and responsibilities, reporting procedures, and escalation processes.
Asset Inventory
Having a comprehensive and accurate inventory of all your IT assets (hardware, software, applications) is essential. This allows you to identify which systems are vulnerable and prioritize remediation efforts based on criticality.
Tools
There are various vulnerability scanning tools available to automate the process of identifying vulnerabilities in your systems. These tools can help you save time and resources, but they should be used in conjunction with other vulnerability management activities.
Program Measurement
Regularly measuring your program's performance is critical for identifying areas for improvement. By tracking your metrics and KPIs over time, you can assess the program's effectiveness and make adjustments as needed.
Leadership Buy-In and Program Ownership
This is the cornerstone. Program sign-off isn't just about a document: it signifies a shared understanding of the program's importance and commitment to see it through. The specific form of endorsement (e.g., policy signed by executives, team alignment) can vary depending on your organization's size, culture, and maturity level. The key takeaway is that leadership recognizes vulnerability management as a vital component of your overall risk management and business continuity strategy.
Program vs. Project Mindset
This is an ongoing effort, not a one-time fix. Projects have a defined start, middle, and end. A vulnerability management program is continuous. It involves ongoing monitoring, communication, evaluation, and adjustments as needed. Think of it like this: Implementing a vulnerability management tool is a project. Actively managing vulnerabilities through continuous monitoring, communication, and results analysis is the program itself.
Setting Expectations: Metrics, SLAs, and KPIs
With leadership buy-in secured, we now need to define what success looks like for our vulnerability management program. Remember, managing vulnerabilities is essentially managing risk, and every company has its own risk tolerance. Fixing vulnerabilities takes time and resources, and it's up to the business to decide how quickly they want to address different levels of risk.
While the CISO (Chief Information Security Officer) can recommend ideal remediation times, imposing SLAs (Service Level Agreements) that clash with the company's risk appetite is a recipe for failure.
Here's a more collaborative approach:
- Risk Registration for Extended Remediation: Similar to other risks, exceptionally long remediation times can be registered and accepted, acknowledging the associated risk.
- KPIs: Measuring Success Through SLAs: Key Performance Indicators (KPIs) are the yardstick for measuring program success. They should track how well the program meets established SLAs. For instance, a KPI might show that 95% of SLAs are met within the defined timeframe, although the target was 98%.
Metrics: Defining What Matters
Metrics are crucial for understanding if the program is achieving its goals. Here's a breakdown of key terms:
- SLAs (Service Level Agreements): These define the expected performance for different program aspects. An example SLA might specify that a critical vulnerability must be patched within 30 days, with a tighter window (e.g., 72 hours) if a severe exploit campaign is underway.
- KPIs (Key Performance Indicators): These are specific metrics that are most important for gauging the program's overall effectiveness. They should be aligned with the organization's security goals.
Tailoring SLAs to Risk Levels
It's important to define SLAs based on vulnerability or risk criticality. Here's a possible example breakdown:
- Reviews: 1 month
- High: 3 months
- Medium: 6 months
- Low: Ongoing monitoring
Measuring Program Efficiency With KPIs
Here are some interesting KPIs to assess program effectiveness:
- Vulnerability remediation timeframe by criticality: Are vulnerabilities being fixed within expected timeframes for their criticality level?
- Remediation time by asset type: Which types of assets take the longest to remediate?
- Exposure level reduction: How has the program impacted the overall level of exposure to vulnerabilities? Is the program's progress meeting expectations?
- Most frequent vulnerability types: What types of vulnerabilities are most commonly found (e.g., patching issues, configuration errors, code flaws)? Are we focusing on the right problems?
- Vulnerability recurrence on new systems: Are previously addressed vulnerabilities reappearing on new systems? Are baseline security standards being followed?
Collaboration Is Key
Remember, these are just examples. Agreed-upon metrics should be established collaboratively with business and support teams. The goal is to define realistic expectations that align with the organization's risk appetite.
Defining metrics is a critical step, as it sets the stage for program success by establishing clear expectations. Good metrics will provide the foundation for measuring program effectiveness and ensuring it delivers the desired level of security.
The Backbone of Security: Vulnerability Management Standards
Once the groundwork is laid, it's time to solidify the program's rules in a vulnerability management standard (or policy). Here are some key elements this standard should encompass:
1. Program Goals: Setting the Direction
Clearly defined goals provide direction and purpose for the program. This establishes what the program aims to achieve.
2. Roles and Responsibilities: A Shared Effort
The standard should outline the roles and responsibilities of various stakeholders involved in the program. This could be achieved using a RACI Matrix (Responsible, Accountable, Consulted, Informed) to ensure clear ownership and accountability.
3. Vulnerability Classification: Prioritizing Risks
The standard should define criteria for classifying vulnerabilities based on severity (critical, high, medium, low). This helps prioritize remediation efforts by focusing on vulnerabilities with the most potential impact.
4. Measuring Success: Tracking Performance
The standard should specify the expected metrics for measuring program effectiveness. Examples include the time taken to patch vulnerabilities and the percentage of systems compliant with security policies.
5. Sign-Off: Ensuring Alignment
Involving business, development, and system support teams in creating the policy fosters program awareness and understanding of individual responsibilities.
Senior management approval and sign-off are crucial. They will ultimately be responsible for monitoring program results and ensuring its ongoing success.
The Importance of Asset Inventory: Knowing What to Protect
An information security program revolves around protecting assets and information. Effective prioritization (including budget allocation) hinges on understanding potential impact, as discussed earlier. Critical business assets and those containing sensitive information warrant prioritized security investments.
A comprehensive asset inventory is fundamental for this prioritization. This goes beyond just hardware or software versions but encompasses systems, data, and information itself.
With data privacy regulations like LGPD (Brazil's General Data Protection Law), data governance is more relevant than ever. Knowing what data you have, its location, classification, and ownership becomes increasingly crucial.
A vulnerability management program will be a cornerstone for risk management decisions, and the asset and data inventory will guide these choices. While vulnerability management tools can identify and classify vulnerabilities based on exploitability and potential impact, the actual impact depends on the vulnerability's materialization and the criticality of the affected asset and its data.
Effective inventory management becomes essential for prioritizing resource allocation (time and budget) for vulnerability remediation.
Vulnerability Management Tools: Unveiling the Tech Arsenal
Now, for the techies, here's where things get exciting! This is where technology comes into play and we start seeing tangible results.
While I won't delve into specific tool recommendations (decisions depend on factors like budget, features, and vendor support), I can offer some guidance on what to expect from a continuous vulnerability management tool.
Types of Vulnerability Assessment Tools
There are two main categories of tools:
- Stand-alone/professional: These are typically used by consultants performing one-time assessments like risk assessments, audits, or penetration tests. The tool is installed on a personal computer, scans are run, reports are delivered, and the consultant moves on. There's no ongoing monitoring.
- Enterprise/continuous monitoring: These function as a continuous service. They often operate in a client-server model, with scanners running periodically and sending reports to a central console. The key difference from stand-alone versions is the ability to schedule continuous scans, analyze trends, and leverage prioritization indicators based on vulnerability evolution.
Continuous Monitoring With Enterprise-Grade Tools
For an ongoing vulnerability management program, an enterprise-type tool is highly recommended. Here's what you can expect from such a tool:
- Automated scheduling: Run scans automatically and repeatedly based on predefined schedules.
- Trend analysis: Track trends and compare results over time to monitor program effectiveness.
- Vulnerability prioritization: Utilize pre-defined rules (often based on labels or tags) to prioritize vulnerabilities for remediation.
- Remediation views and dashboards: Create customizable dashboards that track vulnerability remediation by asset type, vulnerability class, or software version.
- SLA and KPI monitoring: Monitor adherence to defined SLAs (Service Level Agreements) and KPIs (Key Performance Indicators).
- Reporting: Generate clear, customizable reports for informed decision-making.
- System Compatibility: Ensure the tool supports the various types of systems within your environment.
SAST and DAST: Securing the Code
Static Application Security Testing (SAST) and Dynamic Application Security Testing (DAST) have been around for a while, but their importance has grown with the rise of agile development models like DevOps.
- SAST (Static Testing): This testing occurs at deployment time and analyzes code directly, searching for errors that could create vulnerabilities. SAST tools recommend fixes to developers.
- DAST (Dynamic Testing): These tests are conducted with the application already in production. DAST tools use data inputs and fuzzy logic to discover vulnerabilities during runtime.
The good news: Integration with CI/CD (Continuous Integration/Continuous Delivery) pipelines is possible using automation software like Jenkins. This allows for automated SAST and DAST testing after each new release, proactively identifying and addressing vulnerabilities early in the development lifecycle.
Keeping Your Finger on the Pulse: Program Monitoring
Just like any program, vulnerability management requires ongoing monitoring and management to ensure it's meeting its objectives. The goal, after all, is to continuously reduce your organization's overall attack surface and risk. Metrics provide valuable insights, but sometimes additional actions are necessary to address program deviations or refine management strategies.
The Continuous Improvement Cycle: PDCA in Action
Vulnerability management follows a continuous improvement cycle similar to the PDCA (Plan-Do-Check-Act) model. Here's a breakdown of the phases:
- Plan: Identify new vulnerabilities, prioritize them based on risk, and establish remediation plans.
- Do: Implement the remediation plans, patching vulnerabilities and addressing security weaknesses.
- Check: Continuously monitor the program's effectiveness using metrics and identify areas for improvement.
- Act: Take corrective actions based on your findings, such as adjusting prioritization strategies or refining vulnerability scanning schedules.
This cyclical process ensures your program remains dynamic and adapts to evolving threats and vulnerabilities.
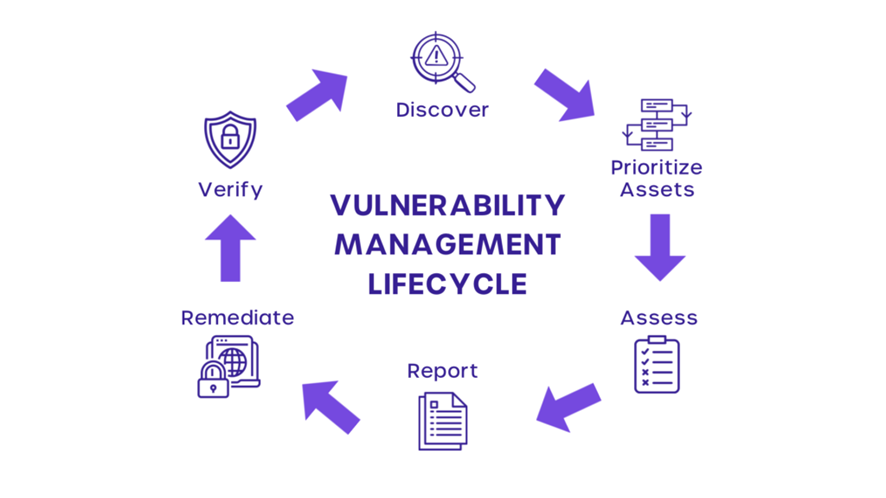
Wrapping Up: Monitoring and Continuous Improvement
Here are some key takeaways for effective program monitoring:
- Embrace the PDCA cycle: Continuously identify areas for improvement through the Plan-Do-Check-Act cycle. Refine your program based on ongoing monitoring and analysis.
- Risk-based prioritization: Prioritize vulnerability remediation efforts based on their associated risk levels. Focus on addressing the most critical vulnerabilities first.
- Transparency is key: Ensure clear visibility into the program for all stakeholders involved. This fosters program awareness and understanding.
- Reporting for accountability: Regularly report to stakeholders on the program's effectiveness in reducing overall risk. Demonstrate the program's value in improving your organization's security posture.
For Further Reading
Published at DZone with permission of Tchule Ribeiro. See the original article here.
Opinions expressed by DZone contributors are their own.

Comments