AI-Powered Ransomware Attacks
This article examines AI's impact on cybersecurity and its role in boosting security measures and ransomware threats with multi-layered defense strategies.
Join the DZone community and get the full member experience.
Join For FreeThe improvement of artificial brainpower (artificial intelligence) has improved many fields, including digital protection. Notwithstanding, this mechanical improvement is a two-sided deal. While computerized reasoning brings many advantages, it also empowers cybercriminals to send off progressively complex and disastrous assaults.
One of the most upsetting viewpoints is using AI in ransomware assaults. These AI-controlled assaults are robotized at different levels and find unpretentious procedures to make them greener, more complex, and more impressive. Most importantly, the danger scene quickly develops, creating more difficulties for people and associations.
This blog investigates how computer-based intelligence is reshaping the network protection ramifications of ransomware assaults and the procedures expected to guard against this developing danger.
The Rise of AI in Cyber Attacks
Computerized reasoning (artificial intelligence) and machine insight have upset many fields, and the field of cyberattacks is no exception. Generally, cybercriminals have depended on manual methods to break into tedious frameworks that require a ton of expertise and exertion. As it may, AI aggressors can computerize and further develop their assault strategies, making their assaults more refined and complex to recognize.
Computer-based intelligence calculations can rapidly handle a lot of information and distinguish examples and weaknesses that people can't identify within a sensible measure of time. This component permits cybercriminals to send off additional exact and designated assaults, improving the probability of achievement. Computer-based intelligence is utilized to mechanize many cyberattacks, including robotized undercover work where aggressors assemble data about their objectives.
AI calculations can use public information from web-based entertainment and different sources to make profiles of potential objective casualties. This data is used for exceptionally altered phishing messages that are, in fact, more solid than customary spam. Computer-based intelligence can likewise be used to control hacking endeavors progressively to enhance the objective’s reaction or conduct and improve the probability of a break.
AI improves malware capabilities. AI can detect the impact of malware from the environment by creating miles around and adapting to avoid detection using conventional security measures. For example, AI can identify malware as it travels miles around the arena and delay its execution to avoid detection. This means that AI can identify malware and delay its execution to avoid detection, thereby making AI-driven cyber-attacks more sophisticated and challenging to defend against.
These developments make AI-driven cyber-attacks more sophisticated, presenting an essential scenario for cyber security professionals. As the next generation of AI is said to transform the methods used by cybercriminals, new generations of cyber threats are exposed, and the latest security is required.
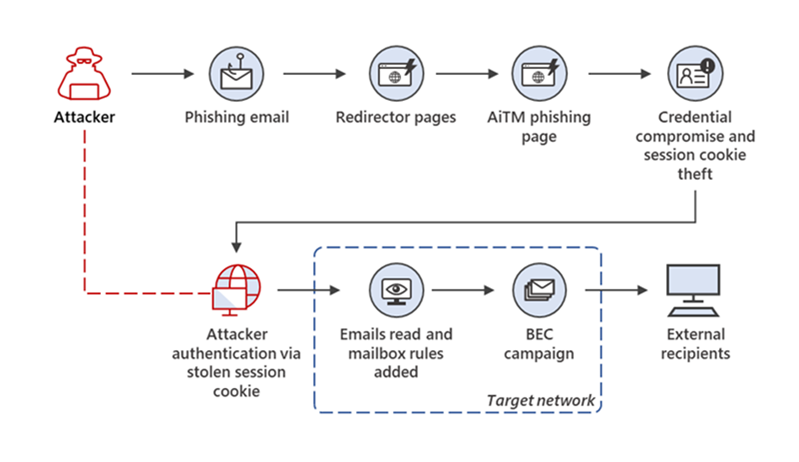
AI-Enhanced Phishing
Phishing, a fraudulent attempt to obtain sensitive information such as usernames, passwords, and credit card details by disguising it as a trustworthy entity in an electronic communication, has long been a cornerstone of cyber-attacks. However, integrating AI has elevated this threat to new heights.
The delivery of a phishing attack involves sending mass messages with generic messages in hopes of tricking specific recipients into revealing sensitive information. As people and communities become more aware and cautious, these practices become less potent. AI algorithms can analyze publicized social media profiles and large amounts of information from various online sources to create legitimate members' personal profiles. These email partners mimic how friends or credit institutions write to provide more details. AI can also dynamically modify the content of phishing emails based on recipient responses or behavior that increases the likelihood of success.
Automating Attack Processes With AI
Computer-based intelligence's capacity to mechanize assault designs has tremendous ramifications for people and associations. Cybercriminals can utilize AI to make their assaults more successful and harder to assault.
For instance, with the assistance of organizations and designs, AI can naturally examine and recognize weaknesses and gather information more quickly than people. This permits aggressors to distinguish weaknesses and foster methodologies to take advantage of. Simulated intelligence-based devices can mechanize malware organization at a palatable rate and time utilizing restrictive calculations. Simulated intelligence in the framework forestalls malware recognition through security highlights and identification strategies customized to its current circumstance.
Furthermore, simulated intelligence robotizes sidelong developments inside the organization, distinguishing and exploiting outside weaknesses to expand harm. This degree of robotization implies that problematic assaults will increment and represent a more severe gamble to people and associations.
The Changing Threat Landscape
Consolidating artificial consciousness (simulated intelligence) into cyberattacks is, in a general sense, changing the dangerous scene, creating difficulties for all people and organizations. Generally, digital dangers have been, to a great extent, manual, depending on the inventiveness and flexibility of the aggressor. The idea of these dangers has developed as artificial brainpower has become more computerized, versatile, and practical.
AI-based assaults can dissect immense measures of information to recognize weaknesses and send off profoundly designated phishing efforts to spread the most recent malware with negligible human intercession. The speed and execution of computer-based intelligence-fueled assaults imply that dangers can arise more suddenly than at any time in recent memory.
For instance, simulated intelligence can mechanize the surveillance and observation stages and guide targets rapidly and precisely. This fast weakness, recognizable proof permits aggressors to take advantage of weaknesses before they are fixed, giving organizations less chance to respond. Additionally, AI can create modified malware that constantly evolves to evade detection using traditional security frameworks, making it more difficult to defend against.
The level of risk that AI introduces is a significant concern. Automated tools can launch hundreds of attacks simultaneously against numerous companies and individuals. This level of automation will escalate cybercriminal attacks and overwhelm existing security features, which are generally not designed to handle such volumes and levels.
AI can leverage more personal attack history to lend credibility to compromised messages or social engineering approaches tailored to specific individuals. The gap between attackers and defenders may widen as the AI era emerges. Cybersecurity professionals must stay ahead of technology and the skills necessary for everyday life.
This includes using AI for security purposes, such as predictive analysis, comprehensive anomaly detection, and risk assessment and mitigation. The constantly evolving threat landscape necessitates a proactive and adaptable approach to cybersecurity, and the adoption of AI for security purposes is crucial to prevent AI-based attacks.
Defense Strategies Against AI-Powered Ransomware
Safeguarding against AI-fuelled ransomware requires a complex methodology that utilizes cutting-edge innovation and robust procedures. Customary security highlights are presently inadequate to manage AI-driven dangers that can be adjusted and developed. Associations should use a blend of preventive insight and responsive systems to battle these assaults. Simulated intelligence and gadget first screening should be joined with network safety securities.
The innovation can continuously break down enormous volumes of logs to recognize peculiarities and potential dangers that are unclear to human examiners. For instance, a simulated intelligence-controlled security framework can see uncommon ways of behaving or quick reaction examples and access information that shows progressing assaults. AI calculations can likewise work over the long haul to be more adept at distinguishing simulated intelligence-fuelled ransomware highlights.
It is vital to carry out a staggered security approach. This incorporates the utilization of firewalls, the upkeep of refreshed enemies of infection and against malware programming, and the utilization of interruption location and counteraction structures. Routinely endlessly refreshing the product is vital to close weaknesses that can take advantage of the payoff.
Also, end identification and reaction (EDR) apparatuses can give non-problematic following and final stage appraisals to help rapidly distinguish and alleviate dangers. Staff preparation and application centers are other fundamental perspectives. Since phishing is a typical vector of ransomware assaults, preparing representatives to recognize and report dubious messages can decrease risk.
Mimicked sport fishing exercises can assist with working on these norms and guarantee that administrators keep on track. Furthermore, it is critical to have a strong reaction plan. This plan should incorporate customary reinforcements of fundamental information, so reinforcements are put away disconnected or in a distant stockpiling climate. In case of this assault, the gathering can reestablish their designs without capitulating to recover requests.
Conclusion
Campaigns focusing on AI-fuelled ransomware address another period in network safety, causing what is happening to people and organizations. As cyber criminals influence artificial brainpower to build the complexity and size of assaults, conventional security capacities are becoming progressively deficient.
Viable insurance requires a thorough methodology that integrates artificial reasoning innovation and high-level motors into the security structure, utilizes numerous layers of security, keeps up with thorough representative preparation, and executes preventive measures.
Also, organizations need to execute hearty occurrence reaction plans and consistently minimize essential reinforcements to relieve the effect of assaults on usefulness. Remaining before the always-changing dangerous scene requires advancement and steady watchfulness.
By proactively adjusting to these high-level dangers, people and organizations can more likely safeguard their virtual merchandise and guarantee security against the developing threat of computer-based intelligence-controlled ransomware.
Opinions expressed by DZone contributors are their own.

Comments