Analysis of Flubot Malware on Android OS
Explore research that focuses on the possible methods of Flubot malware's signature, behavior, and future strikes.
Join the DZone community and get the full member experience.
Join For FreeEvery day, the use of smartphones increases, together with the advancement of the operating system of Android. Subsequently, there have been reports of malicious individuals and hackers capitalizing on the exploits that Android has to offer to gain access to the data that users hold dear. Such threats have included, for instance, the Flubot malware attack that was released for Android devices globally in the year 2021. Notably, this malware targeted banking apps used by victims on their gadgets to carry out the cyberattacks. That is why, with reference to the understanding of the Flubot malware’s signature and behavior, our research focuses on the possible methods of the cyber threat’s future strikes.
Originally, our research included an exploratory analysis of three different samples of Flubot malware found in the free repository of the Hatching Triage platform.
In order to achieve this, we utilized Android Virtual Device (AVD) as our base for testing using the Android Debug Bridge (ADB) for dynamic analysis along with BurpSuite for the same. For static analysis, the current samples were analyzed with the help of the Mobile Security Framework (MobSF) and Bytecode Viewer in order to examine the malware samples’ source code.
Believing that our conclusions might be incomplete, we explored further into the operations of the Flubot virus and found that it delivers or places dex files on the victim’s device. These files act as the framework of the malware, and the additional files are used to enhance its functionality. For instance, the Flubot virus disguises itself as applications that deliver messages or the Short Message Service (SMS) on the host device. We also came across another variant of Flubot Malware which utilizes the Domain Generation Algorithm (DGA) to create channels to communicate with the C&C server.
Introduction
With the advancement and availability of information technology across borders, this has also brought about a corresponding increase in cybercrimes [1]. For instance, Indonesia experienced one instance where it had failed to implement these reforms and was now managing the fallout. According to the recent findings, there have been 6 billion cybersecurity incidents reported in 2021 and it is comprised of a large number of malware attacks [2]. Malware is a term that is an abbreviation for malicious software mainly for cybercrime is operational in different operating systems including, Android, iOS, Windows, and macOS [3]. According to the given references, the world record of mobile device-based hacks till December 2021 was 2, 228, 801 [4]. In particular, Android, with 1 million copies, is recognized as one of the most successful platforms. According to Facebook’s 1. 2 6 billion users, they have been attacked 1,451,660 times by malicious Android packages [4][5]. Specifically, Flubot emerged among the latest threats aimed at Android devices in 2021, originating mainly in New Zealand, Australia, France, and Germany [6][7]. Another source of information reveals that Flubot’s primary motivation is to steal information from the affected device in a process where it poses as an actual application [8].
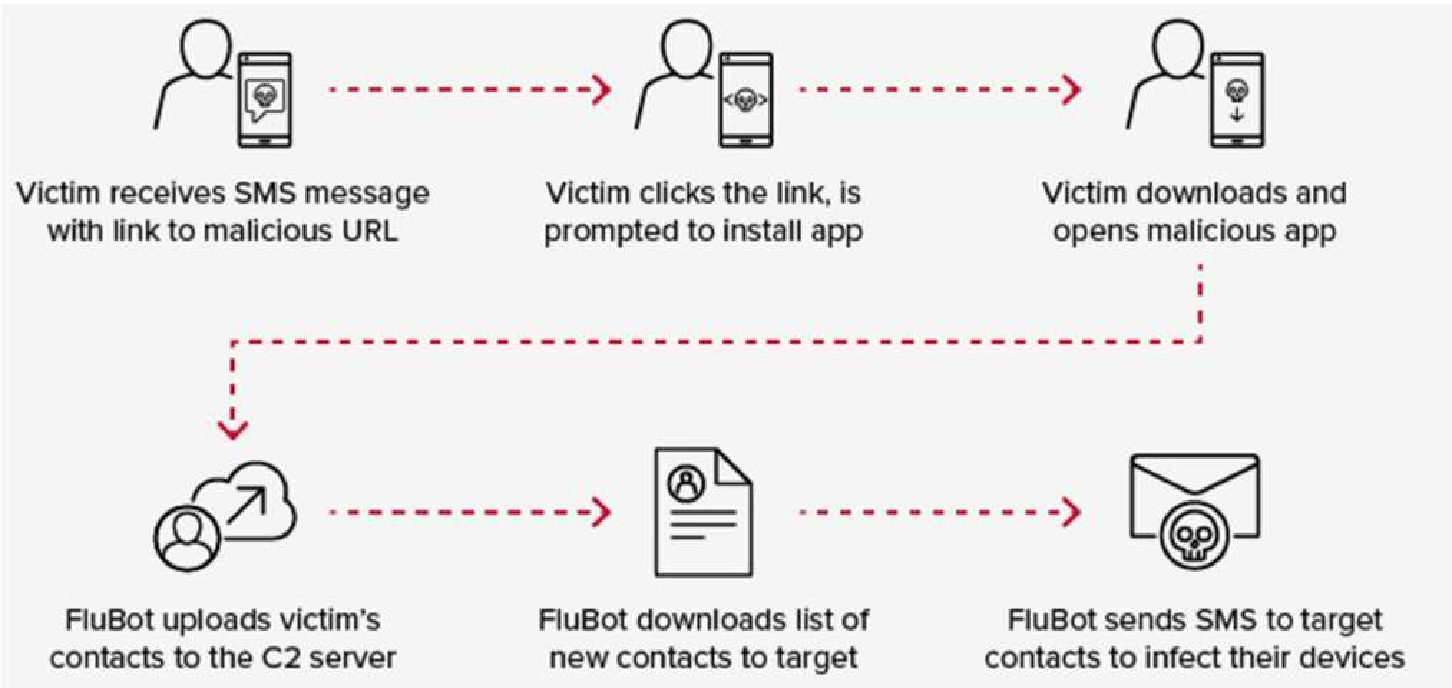
Figure 1: Flubot malware spread method
Methodologies for Malware Detection
Detection methodologies for malware typically fall into two categories: while there are many approaches in software testing, two of the most common ones are known as static and dynamic analysis [9].
Static analysis of malware samples means studying their code and structure without actually allowing the code to execute, while dynamic analysis refers to running the actual samples in a controlled context. In essence, static analysis invokes signature detection whereby it compares the patterns of analyzed software with a database of other notorious applications. However, this approach has a weakness whereby the "bad" code can be unstructured and hard to follow or "obfuscated"[10]. The use of M and P kind of malware, which has the ability to change its code in the course of executing its function, cannot be detected through the above methods of static analysis [11].
Dynamic analysis, on the other hand, investigates malware behavior through runtime analysis of the malware in question such as the API calls and system changes that the virus makes and registry changes [12]. While dynamic analysis presents several benefits, the fundamental disadvantage is that it necessitates creating testing environments, which are time-bound.
Hybrid Analysis Approach
Hybrid analysis is another type of analysis that is a combination of both static and dynamic analysis and also it can detect more thoroughly than the other two. Flubot is an Android malware recently discovered in the market that targets the operating system of the same name specifically. To achieve static analysis, we use tools like MobSF — Reverse Engineering Analysis, APKtool, Dex2jar, and JD-GUI for analyzing the malware signature and behavior. As for the dynamic analysis, we get to use tools such as BurpSuite, Android Virtual Device, Android Debug Bridge, and Frida to interact with the virus to study the behavioral pattern in a contained environment. In this way, we would like to define the signature and behavioral patterns of Flubot malware and study its effect on Android devices.
Methodology
Therefore, we proactively examined the Flubot malware activity in detail, so as to gain insight into its behavior and effect within the system. For this purpose, with reference to the concept of "virtual environments," we utilized the related software for data extraction that was essential for identifying our key findings. In this qualitative prospective study, APK application files affected by Flubot malicious malware are examined with three randomly selected samples examined for analysis.
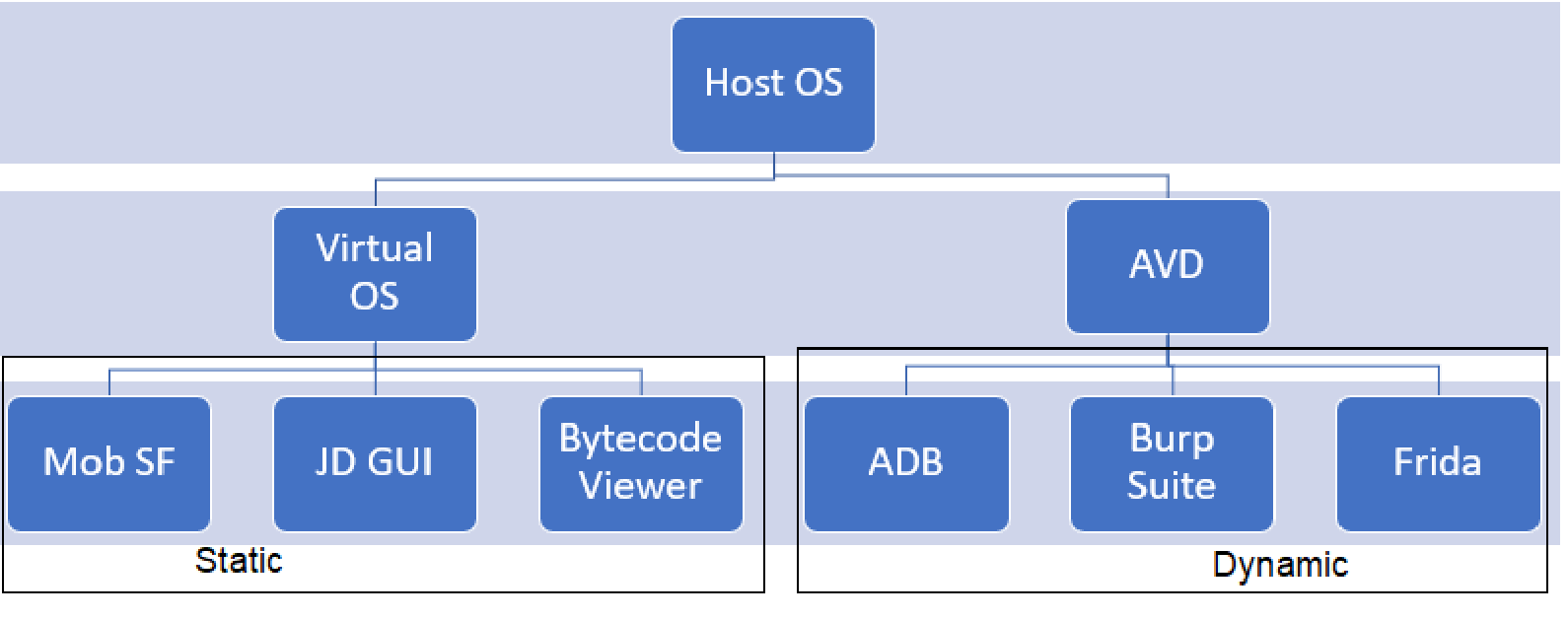
Figure 2: Malware analysis tools
Flubot is malicious software or malware designed to function secretly and has very little record that indicates its presence. However, there are certain indicators that the presence is indicated such as constant use of voicemail application that seems fake, any delivery service like FedEx or DHL, automatic continuous sending of short messages to contacts, and other distortion of the settings of the mobile device.
1. Establishing a Testing Environment
They will be discussed in the subsequent section, where we have delineated the tools that are needed and have created an online context for research. This was done to ensure that the contamination by malicious programs in the network was restricted to a separate environment within the network system.
2. Hybrid Analysis Approach
I called the approach to identifying the solutions a hybrid analysis approach because we used both static and dynamic analyses to accomplish the task. Figure 2 shows the algorithm of the employed method.
3. Tools Utilized Analysis
- Host environment: This report seeks to present the findings of the analysis of statistical data and key characteristics of the Windows 10 operating system, where the key points include:
- Virtual environments: Android Virtual Device (AVD) is an Android emulator where users get a chance to live in the world of Android and experience its features and functions while Kali Linux is a Debian-based Linux distribution, designed for advanced penetration testing and security analysis.
- Static analysis tools: MobSF - Although JD-Gui cannot disassemble code attributes, Bytecode Viewer is an excellent tool for examining classes and code attributes, and using the two instruments together can be efficient.
- Dynamic analysis tools: ADB and Frida, BurpSuite
4. Execution of Analysis
- Configuration of AVD: Android stood out as an image appropriate for running the Flubot malware, and for creating the AVD virtualization engine. For this image, we chose one from Google Nexus, using the Android operating system version 8. 0 API 26.
- Static Analysis
- MobSF: They are typically used for extracting the manifest XML file documents from APK samples in order to analyze the latter for info on the intentions and permissions of the malware in question.
- Bytecode Viewer: Bytecode Viewer is downloaded on the Kali Linux to reverse engineer and analyze the source code from the dex files.
- Dynamic analysis:
- Execution of malicious applications: By infecting the AVD with malware samples and analyzing their behavior in real-time, further experimentation was performed based on the installation of actual samples of the malware on the AVD and following the execution they performed in real-time mode.
- Monitoring tools: ADB and Frida were used in monitoring Flubot malware activity; BurpSuite was used to determine whether the engine identified system calls and analyzed all net traffic generated by the malware. Figure 3 provides an overview of the organization of our framework for malware analysis.
To this end, we found it crucial to adopt a more holistic approach to understanding Flubot malware’s signature, behavior, and effects on the system being explored; the Android operating system, in this case.
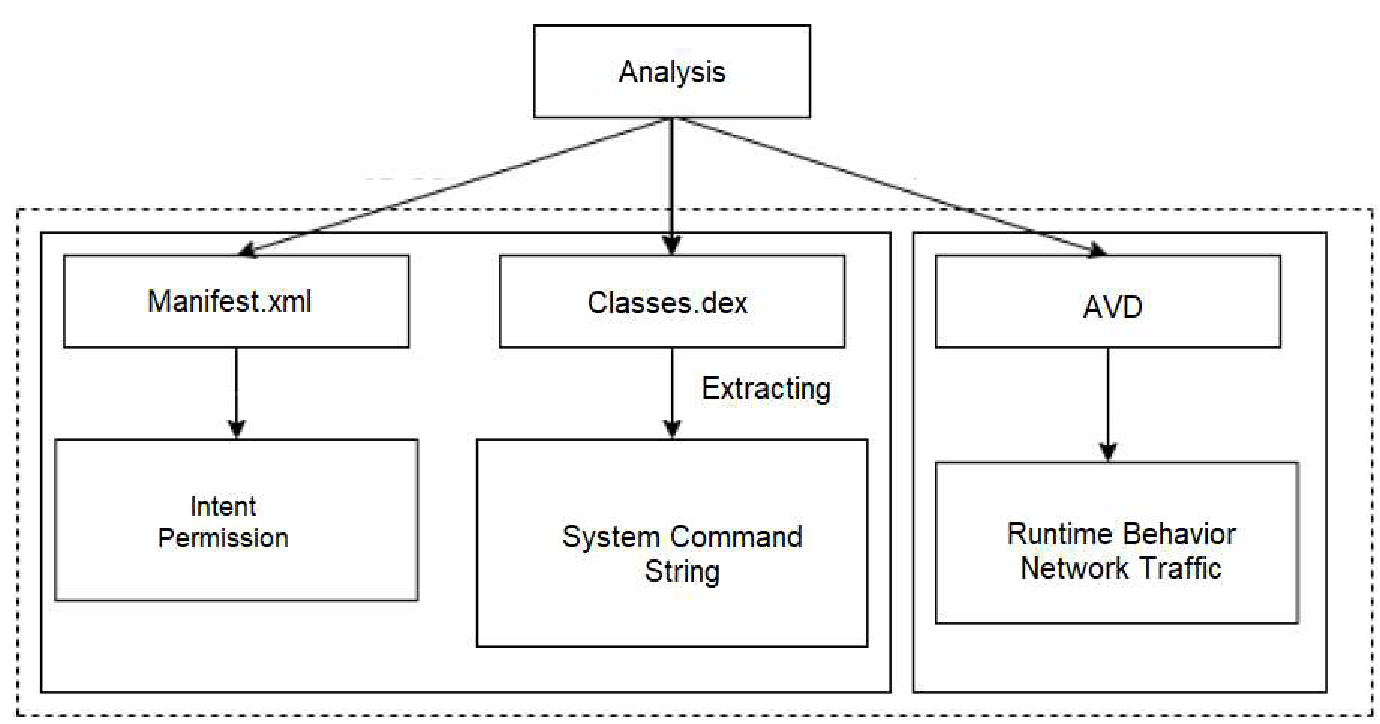
Figure 3: Methods of malware analysis
Configuration and Setup
For interception and analysis purposes, we set up a proxy listener at BurpSuite and included the right AVD proxy. On the AVD, proxy settings were configured manually, using the same proxy hostname and port number as those set up in the BurpSuite listener. Then a CA certificate available on the BurpSuite website needs to be installed on both the BurpSuite host computer and the AVD emulator for a secure connection to be created. Initially after completing the setup of BurpSuite, it was ready to capture the AVD traffic.
Results and Discussion
A combined study of static and dynamic analysis was performed on Flubot samples obtained from the Hatching Triage platform using open-source intelligence methodology. Scanning performed by the MobSF application brought out the following: with a security score of 48/100, its risk rating was estimated at a medium level. Having examined the Indicators of Compromise (IoC) for the samples of the malware, more traces were identified on the Android-based systems such as the package name or the APK hash.
The second type of permissions posited for further examination originated from the Android Manifest in the XML form and identified 15 permissions out of which are permissions to access the internet, SMS, contacts, and phone calls. Some of the key permissions included QUERY_ALL_PACKAGES, which facilitates inventory of installed applications on the device, and REQUEST_DELETE_PACKAGES, which enables the uninstallation of applications installed on the device.
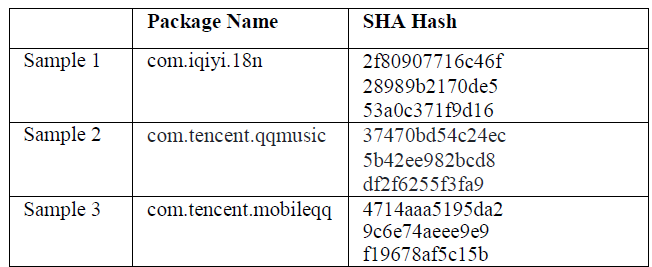
Table 1: Indicator of compromise from the perspective of the three areas of information management namely: collection, processing, and distribution.
The string analysis revealed functional information inherent in the structure of the malware. These include communication with C&C servers, generation of random domains, and connection testing on devices. The static mechanism in connection with the dynamic analysis in a virtual scenario showed the efforts made by the malware in trying to install its payloads and further clone the genuine application such as the messaging application.
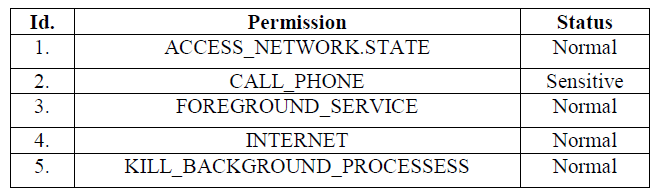
Table 2: Permission list in sample
An analysis of the traffic identified infrequent connections to C&C domains created by using the Domain Generation Algorithm (DGA). Data obtained from infected devices was reported to include text messaging information and data related to cryptocurrency usage.
Conclusion
The observation of Flubot malware samples uncovered permissions to capture sensitive data, command communication with domains, and possible payloads that may affect applications for cryptocurrency. Due to its ability to sneak in and remain undetected in a computer system, it is recommended that the malware be avoided through careful use of the Internet. Being careful not to click on suspicious links or install any applications originating from possibly compromised websites or random emails, Flubot malware can be prevented since it mostly spreads through spam or phishing rather than getting through app markets such as Google Play.
References
- M. Ribka Akhyari and A. Rizal Pratama, “Peranän Perlunya Kepedalian akan Ancaman Serangan Berbasis Backdoor pada Pengguna Smartphone Android,” Automata, 2017. 2, no. 1, pg. 7, 2021, [Online].
- Badan Siber dan Sandi Negara, “Laporan Tahunan Monitoring Keamanan Siber 2015,” pg. 54–55, 2022, [Online].
- A. Test, "Malware Statistics & Trends Report," Magdeburg, 2021. [Online].
- D. Maslennikov, “IT Threat Evolution: The next quarter, Q1 2021,” July 2015 [Online].
- S. R. Department, Statistic, Android by Statistics and Facts, Statista Infographics Available from statista.com. 2018, [Online].
- Flubot scams, Scamwatch, accessed 3rd January 2021. Text message scam infecting Android phones with FluBot _ CERT NZ, New Zealand, on October 1, 2021, accessed on October 2021.
- V. D. M. T. Mark, “FluBot Malware – All You Need to Know & to Act Now,” 2021.
- S. Arshad, M. Ali, A. Khan, dan M. Ahmed, “Android Malware Detection & Protection: A Survey,” Int.
- BPPT, “Guideline of Handling Malware Incident,” Insid. malware, pg. 1–39, 2018.
- Y. Zhou dan X. Jiang, “Dissecting Android malware: “Characterization and evolution,” Priv. , no. 4, pg. 95–109,2012, doi: 10. 1109/SP. 2012. 16.
- A. F. Febrianto; A. Budiono; Studi; Informasi; F. R. ; Industri; S. P. Telkom; P. Menggunakan; Analisis; Malware; Network; Traffic; Android; Operasi; “Metode,” vol. 6, no. 2, pg. 7837–7844, 2019.
- G. Aaron dan C. Strutt, “Malware Landscape 2021 A Study of the Scope and Distribution of Malware,” no. November 2021.
- N. C. S. Center, “FluBot – Android Text Message Scam,” United Kingdom: January 2021. [Online].
- M. F. Zolkipli dan A. Jantan, “Malware Behavior Analysis: Schettini, Andrea, and Riccardo. Learning and Understanding Current Malware Threats,” Proceedings of the 2nd International Conference on Network Applications, Protocols and Services, NETAPPS 2010, 2010, hal. 218–221, doi: 10. 1109/NETAPPS. 2010. 46.
- K. Demertzis & L. Iliadis, “Evolving smart URL filter in a zone-based policy firewall for detecting algorithmically generated malicious domains,” Lect. Notes Comput. Sci. (traditionally collectively referred to as I, e. g., LNCS, Subser. Lect. Notes Artif. Intell. Lect. Notes Bioinformatics), vol. Afonin DN № 9047 October 2016 p. 223–233, 2015, doi: 10. 1007/978-3-319- 17091-6_17.
- D. Uppal, V. Mehra, and V. Verma, “Basic survey on Malware Analysis, Tools and Techniques,” Int. J. Comput. Sci. Appl. , vol. 4, no. 1, pg. 103–112, 2014, doi: 10. 5121/ijcsa. 2014. 4110.
- M. Sikorski dan A. Honig, Practical malware analysis: the live, practical approach to pulling apart viruses, worms, Trojan horses, and other forms of malware. No. Starch Press, 2012.
- M. Zaman, T. Siddiqui, M. R. Amin, and M. S. Hossain, “Malware Detection in Android by Network Traffic Analysis,” in Proceedings of 2015 International Conference on Networking Systems and Security, NSysS 2015, 2015, doi: 10.
- M. Ali Egele, Thijs Scholte, Evren Kirda, and Christopher Kruegel, “A Survey on Automated Dynamic Malware-Analysis Techniques and Tools,” ACM Comput. Surv. , vol. 44, no. 2, 2012, doi: 10.
- A. Kosasih, Febriansyah, T. Sari, I. Harahap, A. N. Jamaludin, A. F. Febrianto, and A. Budiono, “Pemerintaan yang Efektif, Techno, Perencanaan dan Pengendalian Keuangan daerah, Future,” 2018, vol. 6, no. 2, pg. 7837–7844, 2019
- Samir M. pair/Touseef Juithi, A. Bilal, “FluBot - Malware Analysis Report,” Phishing Malware, Switzerland, 2022. [Online].
Opinions expressed by DZone contributors are their own.

Comments