Apache Kafka in Crypto and Finserv for Cybersecurity and Fraud Detection
Data streaming with Apache Kafka in crypto markets + financial services for cybersecurity / fraud detection via real-time threat intelligence
Join the DZone community and get the full member experience.
Join For FreeThe insane growth of the crypto and fintech market brings many unknown risks and successful cyberattacks to steal money and crypto coins. This post explores how data streaming with the Apache Kafka ecosystem enables real-time situational awareness and threat intelligence to detect and prevent hacks, money loss, and data breaches. Enterprises stay compliant with the law and keep customers happy in any innovative Fintech or Crypto application.
The Insane Growth of Crypto and Fintech Markets
The crypto and fintech markets are growing like crazy. Not every new crypto coin or blockchain is successful. Only a few fintech like Robinhood in the US or Trade Republic in Europe are successful. In the last months, the crypto market has been a bear market (writing this in April 2022).
Nevertheless, the overall global interest, investment, and growth in this market are unbelievable. Here is just one of many impressive statistics:
This survey came from NBC News. But you can find similar information in many other new severe portals across the globe.
The Threat Is Real: Data Breaches, Hacks, Stolen Crypto!
With the growth of cryptocurrencies, blockchains, crypto + NFT markets in conjunction with very intuitive crypto trading mobile apps, and popular "normal" trading apps adding crypto support, cyberattacks are more dangerous than ever before.
Let's look at two of the many recent successful cyberattacks against crypto markets to steal cryptocurrencies and explain why any crypto marketplace or trading app can be the next victim.
Supply Chain Attacks for Cyberattacks
While it feels more secure in trusting a well-known and trusted crypto shop (say Binance, Coinbase, or Crypto.com), appearances are deceiving. Many successful cyberattacks these days in the crypto and non-crypto world happen via supply chain attacks:
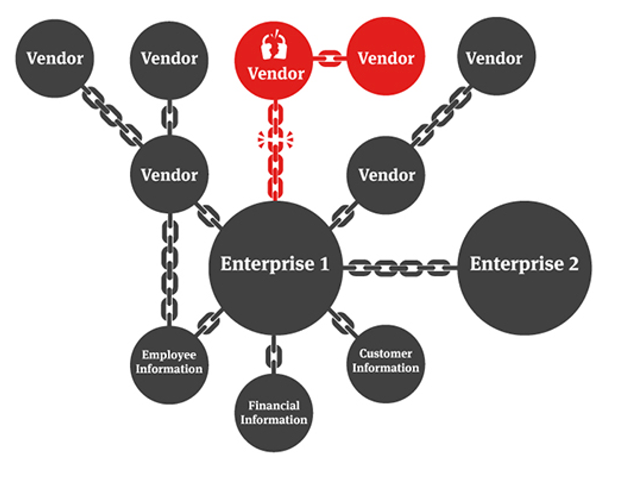
A supply chain attack means even if your infrastructure and applications are secure, attackers still get in via your certified B2B partners (like your CRM system or 3rd party payment integration). If your software or hardware partner gets hacked, the attacker gains access to you.
Hence, a continuous internal cybersecurity strategy with real-time data processing and a zero-trust approach is the only suitable option to provide your customers with a trustworthy and secure environment.
Examples of Successful Crypto Cyberattacks
There are so many successful hacks in the crypto space. Many don't even make it into the prominent newspapers, even though coins worth millions of dollars are usually stolen.
Let's look at two examples of successful supply chain attacks:
- Hubspot CRM was hacked. Consequently, the crypto companies BlockFi, Swan Bitcoin, and Pantera had to advise users on how to stay safe. (source: Crypto News)
- A MailChimp “insider” had carried out the phishing attack by sending malicious links to users of the multimedia platform. This included a successful phishing attack to steal funds stored in Trezor, a popular cryptocurrency wallet company. (source: Crypto Potato)
Obviously, this is not just a problem for crypto and fintech enterprises. Any other customer of hacked software needs to act the same way. For the context, I choose crypto companies in the above examples.
Cybersecurity: Situational Awareness and Threat Intelligence With Apache Kafka
Cybersecurity in real-time is mandatory to fight successfully against cyberattacks. I wrote a blog series about how data streaming with Apache Kafka helps secure any infrastructure.
Cybersecurity With Apache Kafka for Crypto Markets
Many crypto markets today use data streaming with Apache Kafka for various use cases. If done right, Kafka provides a secure, tamper-proof, encrypted data hub for processing events in real-time and for doing analytics of historical events with one scalable infrastructure:
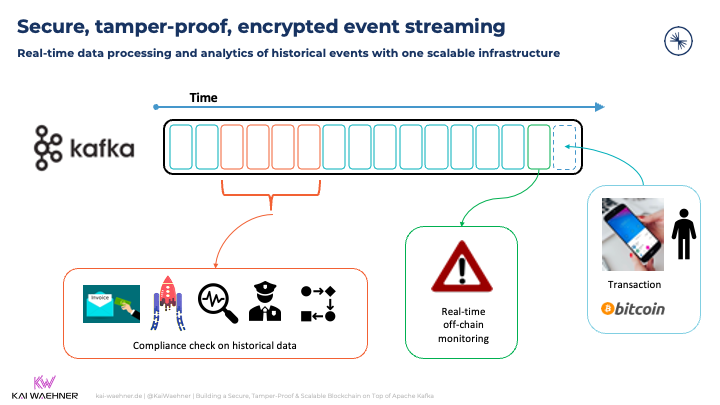
If you want to learn more about "Kafka and Crypto" use cases, architectures, and success stories, check out this blog: Apache Kafka and Blockchain: Friends, Enemies, or Frenemies.
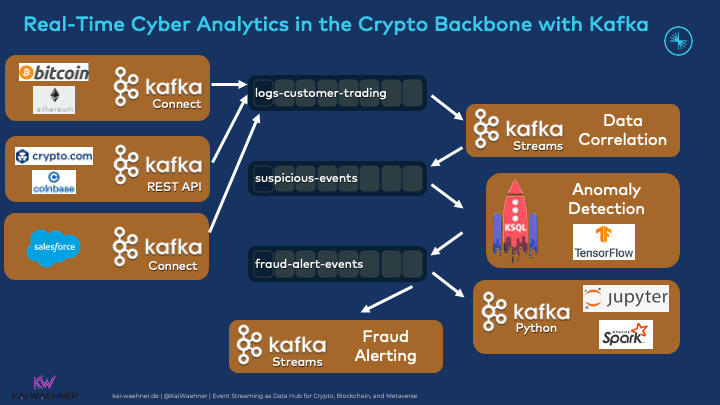
Kafka Architecture for Real-time Cybersecurity in a Crypto Infrastructure
Let's now look at a concrete example for integrating, correlating, and applying transactional and analytical information in a crypto environment with the power of the Kafka ecosystem. Here is the overview:
Data Producers from Blockchains, Crypto Markets, and the CRM system
Data comes from various sources:
- Back-end applications include internal payment processors, fraud applications, customer platforms, and loyalty apps.
- Third-party crypto and trading marketplaces like Coinbase, Binance, and Robinhood and direct transaction data from blockchains like Bitcoin or Ethereum.
- External data and customer SaaS such as Salesforce or Snowflake.
The data includes business information, transactional workloads, and technical logs at different volumes and are integrated via various technologies, communication paradigms, and APIs:
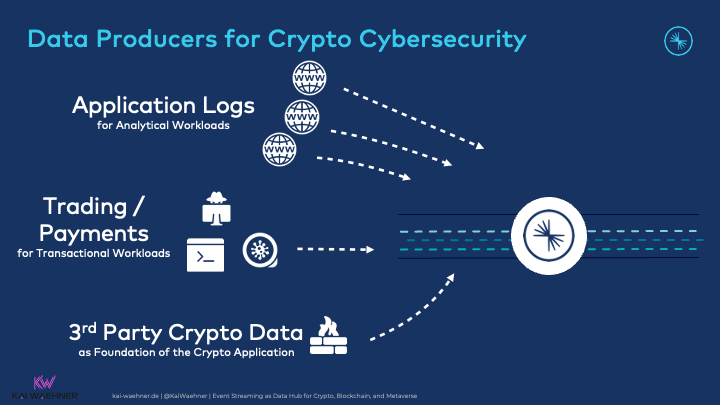
Streaming ETL at any scale is a vital strength of the Kafka ecosystem and is often the first choice in data integration, ETL, and iPaaS evaluations. It is also widespread to combine transactional and analytical workloads within Kafka as the event data hub.
Real-Time Data Processing for Crypto Threat Intelligence with Machine Learning
The key benefit is not sending data from A to B in real-time but correlating the data from different sources. This enables detecting suspicious events that might be the consequence of a cyberattack:
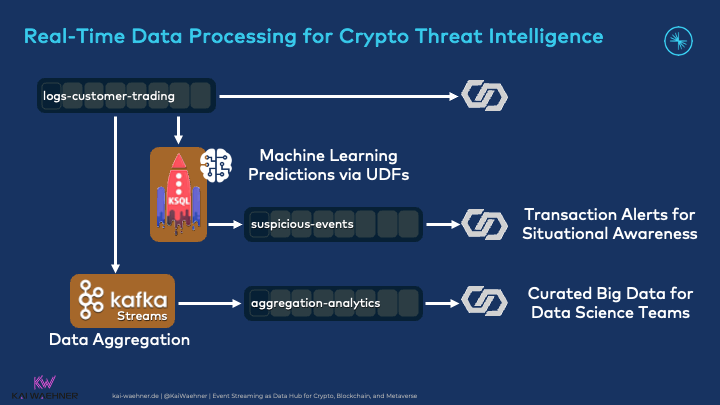
AI and Machine Learning help build more advanced use cases and are very common in the Kafka world.
Data Consumers for Alerting and Regulatory Reporting
Real-time situational awareness and threat intelligence are the most crucial application of data streaming in the cybersecurity space. Additionally, many other data sinks consume the data, for instance, for compliance, regulatory reporting, and batch analytics in a data lake or lakehouse:
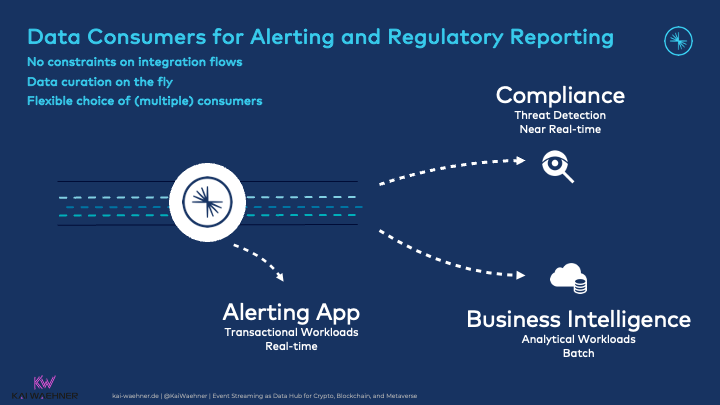
Kafka enables a Kappa architecture that simplifies real-time AND batch architectures compared to the much more complex and costly Lambda architecture.
Data Streaming With Kafka To Fight Cyberattacks in the Crypto and Fintech Space
Supply chain attacks require not just a secure environment but continuous threat intelligence. Data streaming with the Apache Kafka ecosystem builds the foundation. The example architecture showed how to integrate with internal systems, external blockchains, and crypto markets to correlate data in motion.
Kafka is not a silver bullet but the backbone to provide a scalable real-time data hub for your mission-critical cybersecurity infrastructure. If you deploy cloud-native applications (like most fintech and crypto companies), check out serverless data architectures around Kafka and Data Lakes and compare Kafka alternatives in the cloud, like Amazon MSK, Confluent Cloud, or Azure Event Hubs.
How do you use Apache Kafka with cryptocurrencies, blockchain, or other fintech applications? Do you deploy in the public cloud and leverage a serverless Kafka SaaS offering? What other technologies do you combine with Kafka? Let’s connect on LinkedIn and discuss it!
Published at DZone with permission of Kai Wähner, DZone MVB. See the original article here.
Opinions expressed by DZone contributors are their own.


Comments