Architecture Patterns: The Circuit-Breaker
In every architectural design lies a shadowy pitfall. Delve into the lurking dangers within popular patterns, revealing the haunting consequences of misapplication.
Join the DZone community and get the full member experience.
Join For FreeIn the world of distributed systems, the likelihood of components failing or becoming unresponsive is higher compared to monolithic systems. Given the interdependence of microservices or modules in a distributed setup, the failure of one component can lead to cascading failures throughout the system, potentially causing the entire system to malfunction or shut down. Therefore, resilience — the ability of a system to handle and recover from failures — becomes critically important in distributed environments.
Much like how an electrical circuit breaker prevents an overload by stopping the flow of electricity when excessive current is detected, the Circuit Breaker pattern in software engineering stops the flow of requests to a service when the number of failures exceeds a predefined threshold. This ensures that a failing service doesn’t continue receiving traffic until it recovers, preventing further strain and potential cascading failures.
Conceptual Understanding
The Circuit Breaker pattern is designed to detect failures and encapsulates the logic of preventing a system from executing an operation that’s set to fail. Instead of repeatedly making requests to a service that is likely unavailable or facing issues, the circuit breaker stops all attempts for a while, giving the troubled service time to recover.
How It Works
In order to manage this possible failure, the circuit breaker is composed of three possible states, allowing the system to understand the failure and react appropriately.
- Closed State: This is the default state of the circuit breaker. In this state, all requests to the service are allowed. If the service responds without errors, everything continues as normal. However, if errors start cropping up and cross a predefined threshold (which can be set based on the number of errors, response time, etc.), the circuit breaker transitions to the open state.
- Open State: In the open state, the circuit breaker prevents any requests to the failing service, providing an immediate fail mechanism. This state is maintained for a predefined time (reset interval). After this period, the circuit breaker transitions to the half-open state.
- Half-Open State: In this state, the circuit breaker allows a few test requests to determine the health and status of the failing service. If those requests succeed without errors, it’s an indication that the service might have recovered, and the circuit breaker transitions back to the closed state. If they fail, the circuit breaker goes back to the open state, continuing to block requests.
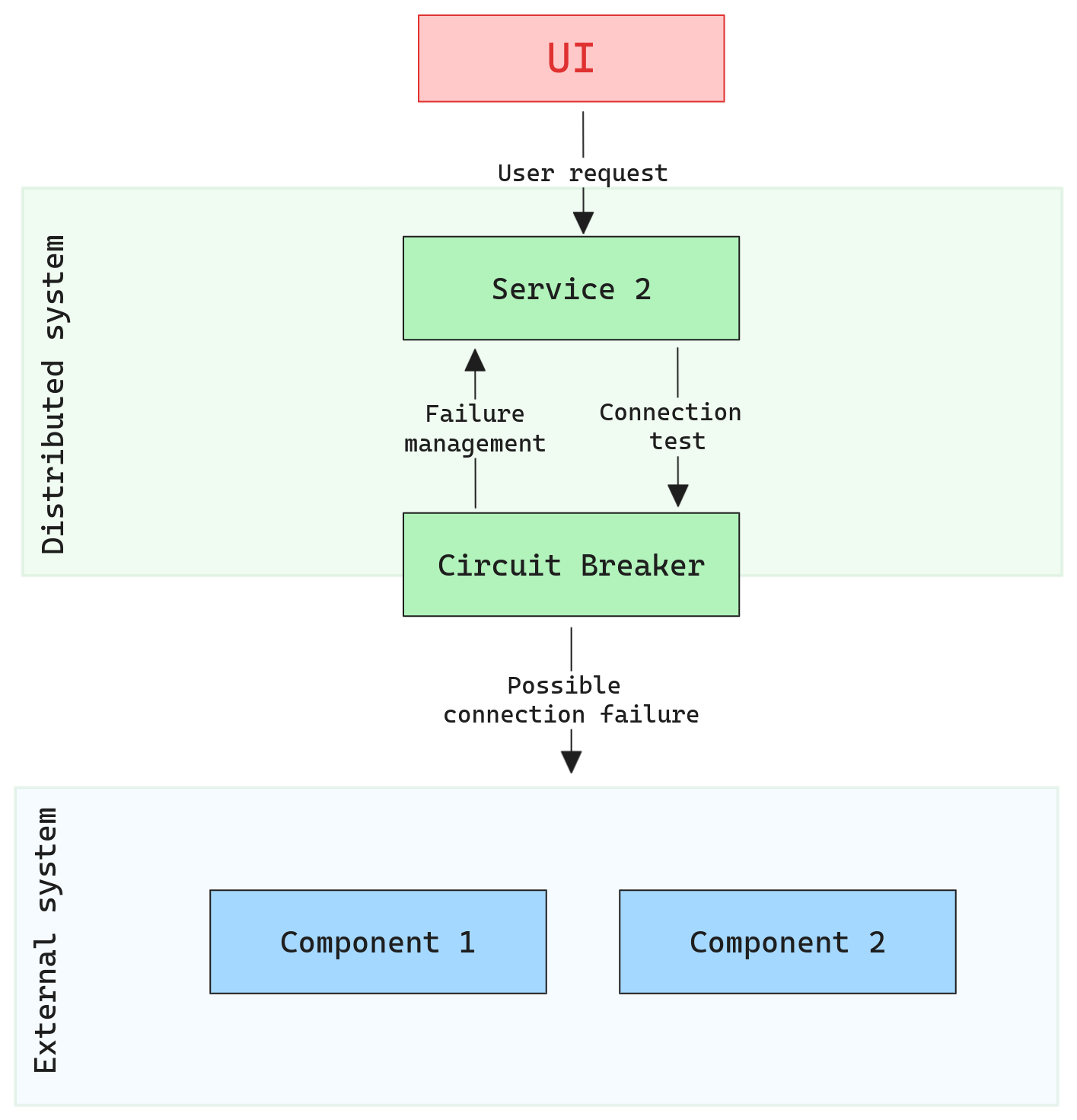
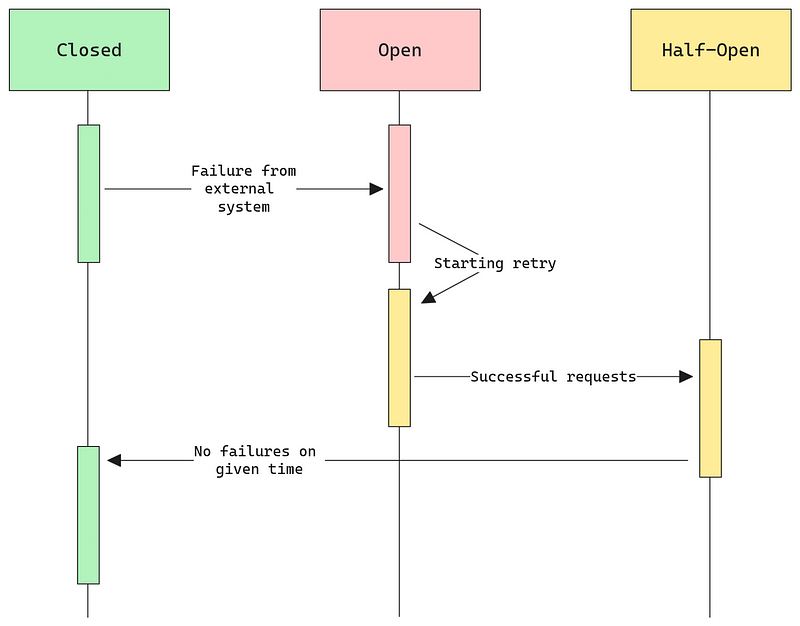
Benefits and Trade-Offs
Benefits
Resilience and Fail Fast
Resilience in software refers to the ability of an application to bounce back from unforeseen failures and continue its operations. “Fail Fast” is a concept where the system promptly fails without prolonging the issue, ensuring it doesn’t waste resources or time.
In the context of the Circuit Breaker pattern, this means that the system can quickly identify when a component or service is failing and halt the operations related to it. This instant detection and action prevent the application from repeatedly making futile requests, ensuring that it remains operational and responsive to other, unaffected parts of the system.
Resource Optimization
This is about making the best use of system resources, such as memory, CPU, and network bandwidth.
If a component of the system is constantly failing and the system keeps making requests to it, it wastes valuable resources. By recognizing such failures and preventing further requests using the Circuit Breaker pattern, the system conserves resources, which can then be used for other operational tasks.
System Protection
This ensures that parts of the system have a chance to recover from failures without being overwhelmed with more requests.
When a service is down or not performing optimally, continually sending traffic to it can exacerbate the problem. The Circuit Breaker pattern effectively “shields” the failing service, ensuring that it isn’t bogged down with more traffic, giving it breathing room to recover.
Enhanced User Experience
While a user might be initially disappointed with a service failing, they would prefer an immediate error message over a long, uncertain wait time. The Circuit Breaker pattern ensures that users get prompt feedback, allowing them to either retry or perform alternative actions rather than being left in the dark.
Trade-Offs
Flakiness in Circuit Breakers
Flakiness denotes the inconsistent behavior of a system component. For the Circuit Breaker pattern, it’s the unpredictability in state transitions due to various influences.
- Threshold configuration: Improper thresholds can lead to the breaker opening too frequently for minor issues or not activating when necessary, causing perceived instability.
Also, if the transition from Open to Half-Open is not managed properly, the service might never recover, which could lead to a system that never returns to normal behavior, even if it is working. - False positives: Transient issues like brief network disruptions can trigger the breaker, making a healthy service appear unreliable.
- External dependencies: Inconsistencies in services or resources the protected service relies on can induce flakiness in the breaker’s behavior.
- Monitoring gaps: Insufficient monitoring makes it challenging to understand the breaker’s transitions, adding to its unpredictable nature.
- Retry mechanisms: Aggressive retries can intensify flakiness, especially when combined with temporary glitches in the service.
Complexity
Implementing a Circuit Breaker pattern introduces new logic, states, and transitions that the system has to handle. This can add complexity, both in terms of coding and monitoring the system.
Configuration Challenges
To work effectively, the Circuit Breaker needs to be tuned correctly. Deciding on the right thresholds for failure detection, the duration to keep the breaker open, and when to test for recovery (half-open state) can be tricky. Incorrect configurations can lead to suboptimal performance and unwanted system behaviors.
Conclusion
As distributed systems grow in complexity, the chances of a single point of failure bringing down the entire system increase. The Circuit Breaker pattern is an essential tool in a developer’s toolkit to prevent cascading failures and ensure system reliability.
It’s important to balance the benefits of using a circuit breaker with the complexity it introduces. The correct configuration of a circuit breaker is critical to its effectiveness and, as with end-to-end testing, flakiness is its worst enemy.
As with all patterns, it’s essential to monitor, gather data, and adjust configurations as needed to ensure that the Circuit Breaker serves its intended purpose.
Published at DZone with permission of Pier-Jean MALANDRINO. See the original article here.
Opinions expressed by DZone contributors are their own.

Comments