Understanding IEEE 802.11(Wi-Fi) Encryption and Authentication: Write Your Own Custom Packet Sniffer
Learn about the most common encryption and authentication methods per the IEEE 802.11 standards, how to write your own packet sniffer and use Wireshark.
Join the DZone community and get the full member experience.
Join For FreeIntroduction
As of 2023, it’s estimated that 42 billion cumulative Wi-Fi enabled devices have been shipped (Wi-Fi® by the Numbers: Technology Momentum in 2023, n.d.). Every new device adds to the increasing wireless attack surface, and it's important for anyone working in the security software industry to have a basic understanding of how wireless networks encrypt traffic and authenticate users. In this article, we’ll go through the 4 currently supported and ratified security standards for Wi-Fi networks. We’ll also look at the IEEE 802.11 packet and header structure. Then we will look at a C program to write your custom packet sniffer linking with libpcap. We will also look at a real-life packet capture using Wireshark GUI.
Outline:
- Common encryption and auth supported by IEEE 802.11 standards <- Theoretical Foundation
- IEEE 802.11 mac header, frame types, Information elements <- Theoretical Foundation
- Custom C program linked with
libpcapto sniff packets <- Practical Application - Wireshark based sniffing of nearby APs <- Practical Application
Common Encryption and Authentication Methods Supported by the Standards
WEP (1997), WPA (2003), WPA2(2004), WPA3 (2018) are the 4 officially ratified IEEE 802.11 security standards by the Wi-Fi Alliance. WPA4 is expected to be rolled out with Wi-Fi 7 but no standard has been formally ratified.
Each of the four ratified standards mentioned above have many methods for “authentication” which is different from how traffic is “encrypted.” In simple terms, encryption dictates how traffic is secured while being transmitted between a transmitter and a receiver. Authentication on the other hand defines how a client can be allowed to join a network.
We will look at some of the supported methods that are most commonly used in both corporate and personal networks.
WEP
- Encryption:
- Uses a key of 10 or 26 hex digits (40 or 104 bits) concatenated with a 24 bit initialization vector to give us 64 bit WEP or 128 bit WEP.
Examples follow:
Secret Key: A1 B2 C3 D4 E5 (40 bits)
IV: 12 34 56 (24 bits)
---------------------------------------
WEP Key: A1B2C3D4E5123456 (64 bits)Secret Key: 00 12 27 33 43 55 66 77 88 99 AB BB CC (104 bits)
IV: DE AC BB (24 bits)
---------------------------------------------------------------
WEP Key: 00122733435566778899ABBBCCDEACBB (128 bits)This is a static key, which means all traffic, regardless of device, is encrypted using a single key. This was one of the major issues, and WPA-* improved it by changing the key used by authenticated systems. As a practical matter, any device supporting/using WEP is an easy attack vector and is prohibited to be used in many government and commercial facilities.
- Authentication: Open System authentication and Shared Key authentication.
WPA
-
Encryption:
-
The WPA protocol implements the Temporal Key Integrity Protocol (TKIP) for encrypting traffic.
-
TKIP employs a per-packet dynamically generated 128-bit key thus preventing the types of attacks that WEP is prone to since it uses a static key.
-
-
Authentication:
-
Personal: Also referred to as WPA-PSK (pre-shared key) mode, for home and small networks. A passphrase is an example of a Pre-Shared Key.
-
Enterprise: Also referred to as WPA-802.1X mode, or WPA-EAP (WPA-Extensible Authentication Protocol), and sometimes just WPA (as opposed to WPA-PSK); this is designed for enterprise networks and requires a RADIUS authentication server.
-
WPA-2
-
Encryption:
-
WPA-2 implements “Counter Mode Cipher Block Chaining Message Authentication Code Protocol (Counter Mode CBC-MAC Protocol)” or “CCM mode Protocol (CCMP)” which is based on AES. The informal names are AES and AES-CCMP.
-
It uses a 128-bit key: “AES-128 in CCM mode”. This is significantly stronger in protection for both privacy and integrity than a 128 bit TKIP
-
AES-128 Key (Temporal Encryption Key or TK) is derived from your WPA2 passphrase using
PBKDF2(if using WPA2-PSK else keys are negotiated with the RADIUS server).PBKDF2is the Password-Based Key Derivation Function 2 as defined in RFC 2898.MarkdownPBKDF2(HMAC-SHA1, passphrase, SSID, 4096 iterations) → 256-bit PSK --------------------------------------------------------------------- The first 128 bits of this output is the TK. The next half is the PTK -
A unique nonce (built from packet number, transmitter MAC, etc.) is used with AES in Counter Mode to encrypt the packet.
-
MIC (Message Integrity Code) is generated for tamper detection.
-
-
-
Authentication:
-
Same as WPA authentication.
-
WPA-3
-
Encryption:
-
WPA3-Personal mode: It mandates the use of CCMP-128 (AES-128 in CCM mode) as the minimum encryption algorithm.
-
WPA3-Enterprise: Minimum 128-bit Advanced Encryption Standard Counter Mode with Cipher Block Chaining Message Authentication CCMP-128 (AES-128 in CCM mode)
-
WPA3-Enterprise-with-192-bit-mode: It uses an equivalent 192-bit cryptographic strength (AES-256 in GCM mode with SHA-384 as HMAC)
-
-
Authentication:
-
Personal: It replaces the PSK exchange with Simultaneous Authentication of Equals (SAE) exchange, resulting in a more secure initial key exchange in personal mode and forward secrecy.
-
WPA3-Enterprise: Multiple Extensible Authentication Protocol (EAP) methods are supported.
-
WPA3-Enterprise-with-192-bit mode: Extensible Authentication Protocol – Transport Layer Security (EAP-TLS) using Elliptic Curve Diffie-Hellman (ECDH) exchange and Elliptic Curve Digital Signature Algorithm (ECDSA) using a 384-bit elliptic curve
-
It is important to note that these encryption and authentication methods above are not the only supported ones, but the most commonly used ones. There are quite a few esoteric implementations that are often more secure/complex variations of those above. The full list of supported types can be found here.
IEEE 802.11 (Wi-Fi) MAC Frame Header
In this section, I will briefly explain IEEE 802.11 header, and show two packet captures using Wireshark that identify a few encryption and authentication methods that were explained above. The Wi-Fi standard is enormous, and it is not practical to cover the entire header in detail in this article, so this section is more suited for folks deeply curious/already somewhat familiar with the Wi-Fi spec, and/or folks working in wireless security, protocol decoding, and allied fields.
Following is the 802.11 MAC layer packet structure:
+----------------+------------+-----------+-----------+-----------+------------------+
| Frame Control | Duration/ID | Address 1 | Address 2 | Address 3 | Sequence Control|
+----------------+------------+-----------+-----------+-----------+------------------+
| Address 4 (optional) | QoS Control (optional) | HT Control (optional) |
+-----------------------------+------------------------+-----------------------------+
| Frame Body (Payload) |
+------------------------------------------------------------------------------------+
| Frame Check Sequence (FCS) |
+------------------------------------------------------------------------------------+
For the purposes of this article, we are going to focus on Frame Control, and Frame Body.
- Frame Control: This is a 2 byte field that contains information about the frame type, the protocol version, the subtype, the distribution system flags etc. We're gonna focus on frame type in the next section as we will eventually be looking at Beacon frames from an Access Point to identify what encryption and authentication it is using.
- Frame Body: This is the actual payload/body being transmitted. In the case of management frames, this body contains Information Elements (IE)—which is important to us, and is explained below.
IEEE 802.11 MAC frame types
Management, control, and data frames make up the 3 types of MAC layer frames.
-
Management frames help establish and maintain wireless network connections. This is what allows clients to join a network, search for a network, leave a network etc. We will focus on this type in the following sections.
-
Control frames are needed for managing the wireless medium and to allow for orderly exchange of data (You can think of them as turn signals/brake lights on your car). Devices send these frames before transmitting data, after successfully receiving data and so on.
-
Data frames as the name implies, allow for devices to exchange actual data, often referred to as "payload."
IEEE 802.11 MAC Management Frame Types
Some common management frame types are:
-
Beacon: Access points (APs) periodically transmit beacon frames to advertise network info.
-
Authentication/De-authentication: Authenticate/De-authenticate clients
-
Association/Disassociation: Used to join/leave a network by clients
-
Probe Request/Response: Used by clients to find available networks. When we open the wi-fi tab on our personal devices and see a list of networks - its being kept up to date by the device ‘probing’.
IEEE 802.11 Information Elements
Information Elements (IE) are type/length/value structures used to express variable metadata in management frames. They are found inside the frame body of management frames. For the purposes of this article we're interested in looking at IE's in Beacon Frames.
Table 1. Some of the common IE's in Beacon frames
| IE ELEMENT ID |
NAME
|
|---|---|
| 0 | SSID (the name of the network) |
| 1 | Supported Rates |
| 3 | DS Parameter set (channels supported) |
| 50 | Extended Supported Rates |
| 48 | RSN (Robust Security Network) |
| 221 | Vendor Specific Info |
It is critical to note that the RSN IE (48) was introduced only in WPA2 and onwards. So when RSN IE is not present, we know that the Beacon is from an access point that does not support WPA2 or higher. Below is the detailed description of all RSN IE fields. The ones pertinent to this article are highlighted in green.
Table 2: RSN IE fields descriptions
| Field | Description |
|---|---|
| Element ID | 48 |
| Length | length of the remaining fields |
| Version | 1 |
| Group Cipher Suite | OUI + cipher for multicast |
| Pairwise Cipher Suite Count | number of unicast cipher suites listed |
| Pairwise Cipher Suite List | list of cipher suites "encryption" |
| AKM Suite Count | number of authentication suites listed |
| AKM Suite List | list of AKM suites "authentication" |
| RSN Capabilities | options like PMF, pre-authentication |
| PMKID List (optional) | optional; only if PMKID Count > 0 |
| PMKID Count (optional) | present in association responses |
| Group Management Cipher (opt) | applicable only for wpa3 - 192 bit |
C Programming To Write Custom Sniffers
Given the theory above, we will put it to use to write our own custom packet sniffer to sniff nearby Access Points.
Pre-requisites:
- libpcap - This is every network programmer/security researcher's favorite.
sudo apt install libpcap-devon linuxbrew install libpcapon mac
- Build environment to compile C code
- Ability to put a wireless interface in monitoring mode
- With newer macs that have Broadcomm chips, low level access is not allowed. So this activity is best done on a linux system or a linux vm.
The program I present here sniffs for Management frames of Beacon type and we specifically print out the RSN information element (48).
#include <pcap.h>
#include <stdio.h>
#include <stdlib.h>
#include <string.h>
#include <stdint.h>
#define BEACON_SUBTYPE 0x80
#define RSN_IE_ID 48
// 802.11 header (simplified)
struct ieee80211_header {
uint8_t frame_control[2];
uint8_t duration[2];
uint8_t addr1[6];
uint8_t addr2[6];
uint8_t addr3[6];
uint8_t seq_ctrl[2];
};
void print_rsn_ie(const u_char *ie_data, int len) {
printf("RSN IE (len=%d): ", len);
for (int i = 0; i < len; i++) {
printf("%02X ", ie_data[i]);
}
printf("\n");
}
void proc_packets(u_char *user, const struct pcap_pkthdr *h, const u_char *bytes) {
const struct ieee80211_header *hdr = (const struct ieee80211_header *)bytes;
uint8_t fc0 = hdr->frame_control[0];
// management subtype beacon
if ((fc0 & 0xF0) == BEACON_SUBTYPE) {
int offset = 24; // skip MAC header
// need not print timestamp, beacon interval, capability info
offset += 12;
// parse IEs
while (offset < h->caplen) {
uint8_t id = bytes[offset];
uint8_t len = bytes[offset + 1];
if (offset + 2 + len > h->caplen)
break;
if (id == RSN_IE_ID) {
print_rsn_ie(&bytes[offset + 2], len);
break; // print rsn ie and break
}
offset += 2 + len;
}
}
}
int main(int argc, char *argv[]) {
if (argc != 2) {
fprintf(stderr, "usage: %s <monitor-mode-interface>\n", argv[0]);
return 1;
}
char errbuf[PCAP_ERRBUF_SIZE];
pcap_t *handle = pcap_open_live(argv[1], 65535, 1, 1000, errbuf);
if (!handle) {
fprintf(stderr, "pcap_open_live failed: %s\n", errbuf);
return 1;
}
// look for mgmt and beacon
struct bpf_program fp;
if (pcap_compile(handle, &fp, "type mgt subtype beacon", 0, PCAP_NETMASK_UNKNOWN) == -1 ||
pcap_setfilter(handle, &fp) == -1) {
fprintf(stderr, "failed to apply filter\n");
return 1;
}
printf("listening for beacons with interface %s...\n", argv[1]);
pcap_loop(handle, 0, proc_packets, NULL);
pcap_close(handle);
return 0;
}To put the interface in monitor mode in linux:
sudo ip link set wlan0 down
sudo iw wlan0 set monitor control
sudo ip link set wlan0 upThen the program can be compiled and ran as follows:
gcc my_custom_sniffer.c -o my_custom_sniffer -lpcap
sudo ./my_custom_sniffer wlan0monWireshark and Packet Sniffing
Wireshark is the most popular packet sniffing tool that many developers, enthusiasts, and security researchers use to sniff packets from wired and wireless networks and inspect their content. Newer versions of Macs also have the network analyzer tool that has some of this functionality. Wireshark can be installed from here. If you pull up wireshark, it should look like this:
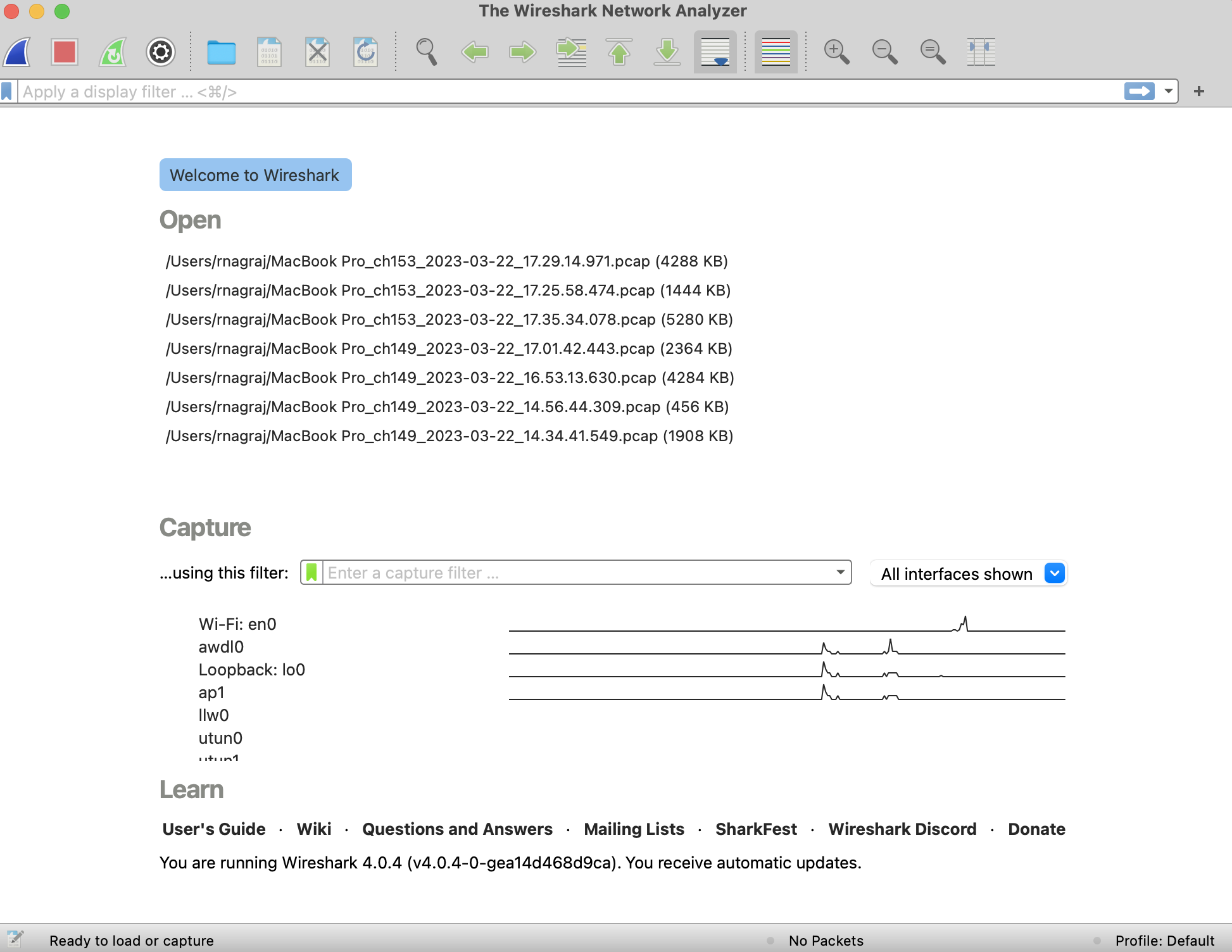
- As you can see, I have a few "pcap" files - these are packet captures I have made and/or analyzed in the past.
- You can also see traffic on few of the interfaces in the form of line graphs.
- We will use the Wi-Fi: en0 interface (as this is my wireless interface) to capture packets.
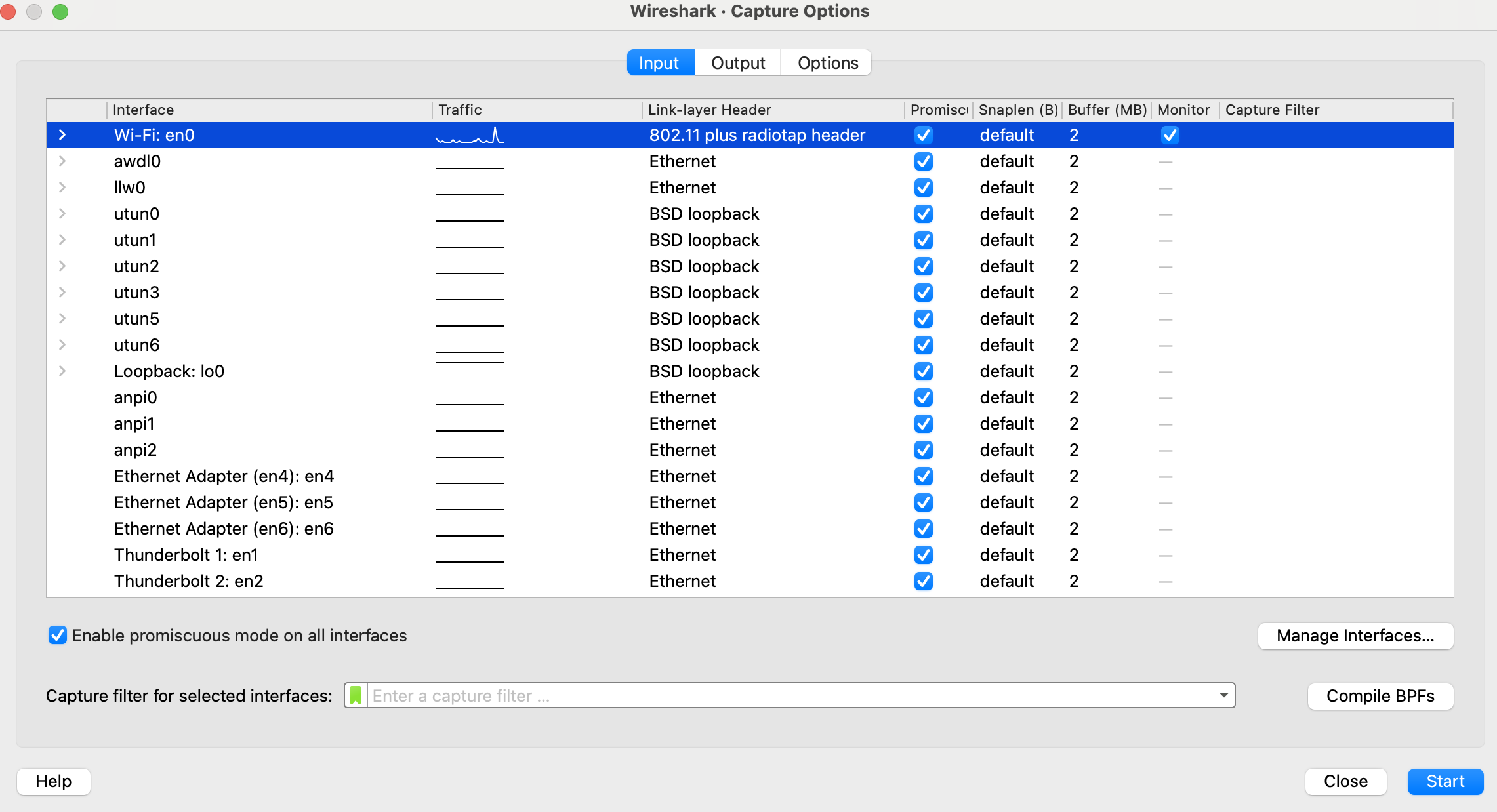
- To do so, we'd need to put this interface in monitor mode. We select the interface first, and press the "capture options button" which is the fourth icon at the top—and once pulled up, we check "monitor mode" as shown below and hit start.
- You can run a raw capture or you can run with filters. Since we want to look at "management frames" only, you could set the filter to
wlan.fc.type == 0. - Note: If your Mac has a Broadcom chipset, monitor mode may not be supported. In this case you can use a USB wireless adapter in conjunction with a Linux VM inside virtualbox. I have used Panda PAU09 with a Kali Linux VM on my newer M1 mac.
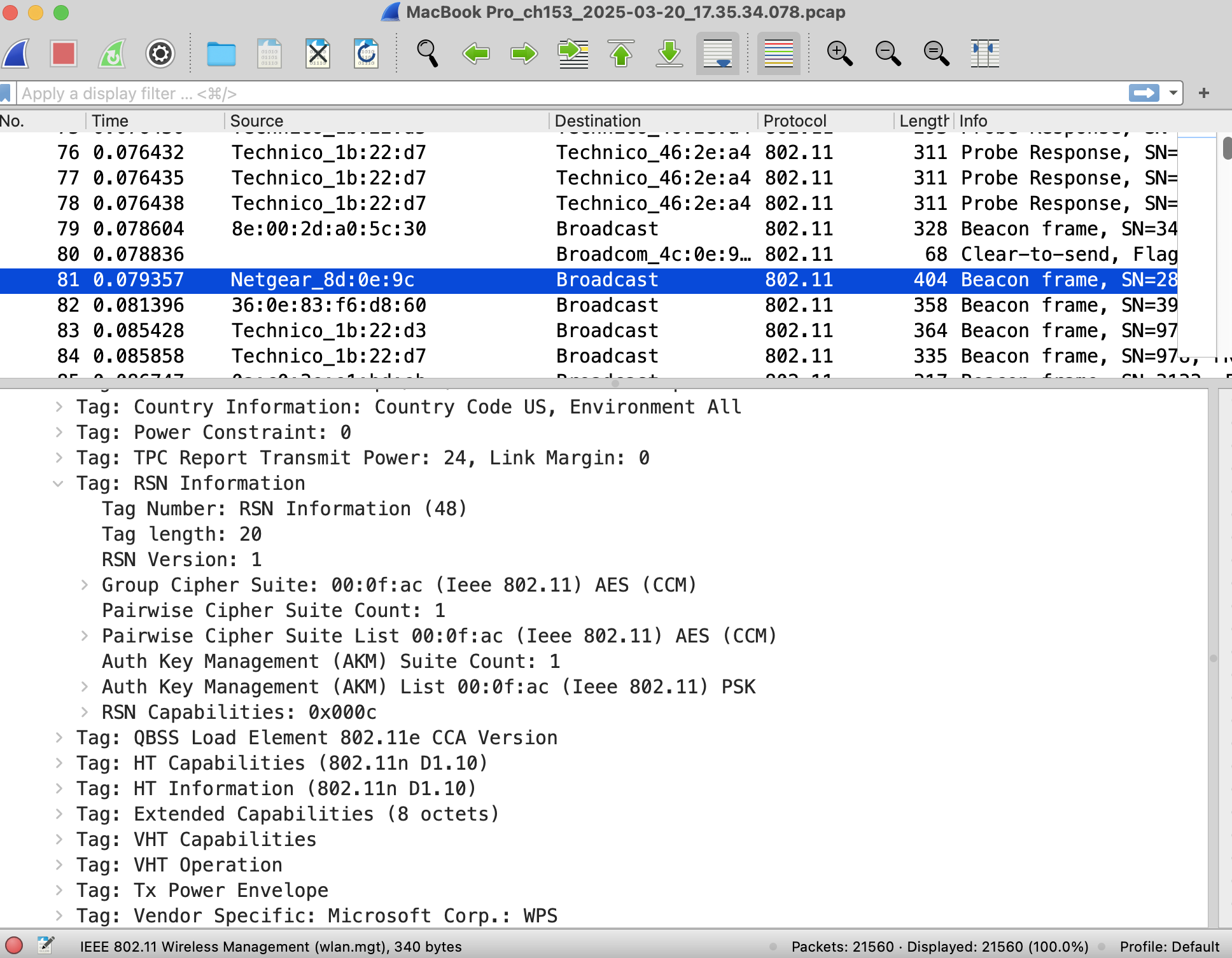
- After stopping the capture, you can pick any management frame of Beacon type and inspect the frame body, specifically IE 48 as explained above, which is the RSN element. It is very unlikely you will find a frame without this IE since most personal and commercial Access Points are configured to be WPA2 at least.
- Inside this IE 48 you will see all the fields listed in Table 2. You want to look at specifically the highlighted ones in green to identify what "encryption" and "authentication" are being offered by the Access Point whose beacon you're inspecting.
Interpreting the RSN Information Element
Here is an example of a Beacon Frame's Information Element (IE) 48 - Robust Security Network as seen in a management frame from my capture. As explained in Table 2, we're going to be looking at the Pairwise Cipher Suite List, and the AKM List.
If not using Wireshark/other pcap readers, this info will be in hex and one would have to consult this code mapping to decipher the encryption and authentication. Here's is the full list of all types of Cipher values and Auth values from the IEEE spec:
CIPHER_MAP = {
"0": None, # "open" network
"1": "wep(40-bit)",
"2": "tkip",
"3": "aes(ocb)",
"4": "aes(ccm)",
"5": "wep(104-bit)",
"6": "bip(128)",
"7": "group addressed traffic not allowed",
"8": "gcmp(128)",
"9": "gcmp(256)",
"10": "ccmp(256)",
"11": "bip(gmac-128)",
"12": "bip(gmac-256)",
"13": "bip(cmac-256)",
}
AUTH_MAP = {
"0": "none",
"1": "wpa",
"2": "psk",
"3": "ft over ieee 802.1X",
"4": "ft using psk",
"5": "wpa (sha256)",
"6": "psk (sha256)",
"7": "tdls / tpk handshake (sha256)",
"8": "sae (sha256)",
"9": "ft using sae (sha256)",
"10": "appeerkey (sha256)",
"11": "wpa (sha256-suiteb)",
"12": "wpa (sha384-suiteb)",
"13": "ft over ieee 802.1x (sha384)",
"14": "fils (sha256 and aes-siv-256)",
"15": "fils (sha384 and aes-siv-512)",
"16": "ft over fils (sha256 and aes-siv-256)",
"17": "ft over fils (sha384 and aes-siv-512)",
"18": "opportunistic wireless encryption",
"19": "ft using psk (sha384)",
"20": "psk (sha384)",
"21": "pasn",
}However when using Wireshark/other pcap tools - the parsing is done for us, and we get the human readable values. We can see from the capture below, that the highlighted Netgear AP is a WPA2 - Personal Access Point.
This is because the encryption (pairwise cipher suite list) shows AES/CCM and the AKM shows us PSK.
Summary
We covered the four Wi-Fi security standards and their technical specifications. We looked at the IEEE 802.11 MAC packet structure, the three frame types, and the four types of Management frames. C programming to write custom sniffers was covered. We also looked at a real-life packet capture using Wireshark; specifically a Beacon frame from a nearby network and determined it is using WPA-2 with a Pre-shared Key (PSK).
Opinions expressed by DZone contributors are their own.

Comments