AWS Security Groups Basics
A Security Group is a virtual firewall for your EC2 instance to control Inbound/Outbound traffic to/from your instance.
Join the DZone community and get the full member experience.
Join For FreeIntroduction
Security Groups are one of the fundamental concepts you need to learn when you are setting up infrastructure in AWS. Having a good understanding of their workings will help you not only design proper access for your EC2 instances but you will be also able to quickly spot and deal with issues with existing designs.
We have been using security groups in the earlier posts in this series and today we will learn a little bit more about those.
In my previous post on AWS Basics: Bastian Hosts and NATS, we used security groups to manage access to EC2 instances.
Here is the architecture diagram for reference. As you can see that it already has a few security groups set up which control access to different instances.
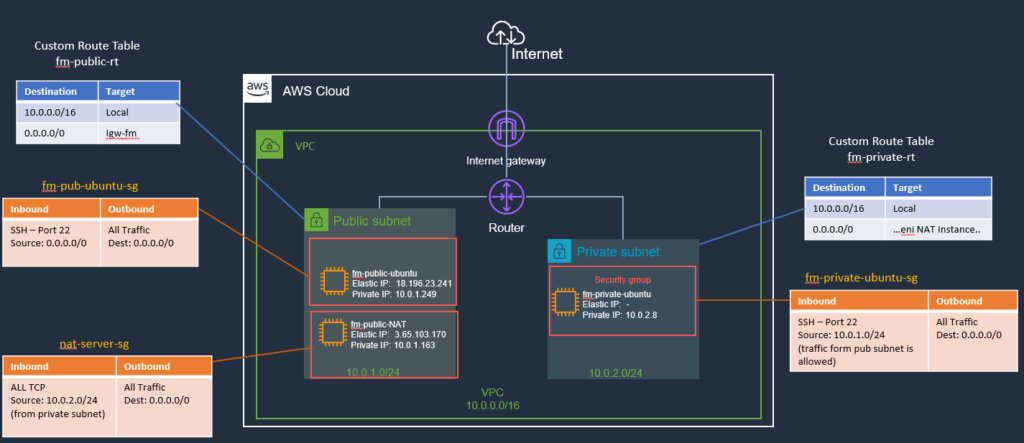
Security Groups in AWS
A Security Group is a virtual firewall for your EC2 instance to control Inbound/Outbound traffic to/from your instance.
A Security group is made up of a set of inbound and outbound rules.
A security group that belongs to a VPC and is assigned at the instance level and can be shared among many instances. You can use the same Security Group in different subnets in the same VPC. Subnets can also have different Security Groups.
Security Groups allow access. They do not use the word deny, yet they implicitly deny. For example, I need access to my webserver through port 80. I am allowing access through port 80. Am I allowing access through port 90? Not, if it is not listed. So, implicitly denying, you can’t get to port 90 or any other port unless it is listed as a rule.
You can even set security group rules to allow access from other security groups instead of by IP address(s).
They are stateful in design. If you think of A as coming in and B going out, well... inbound traffic is noted. If the traffic got in, it gets back out. if the traffic goes out, it gets back in.
As mentioned earlier, security groups are assigned to the instance. Security groups are firewalls and they are protecting the network interface cards of that instance. They are controlling packet flow.
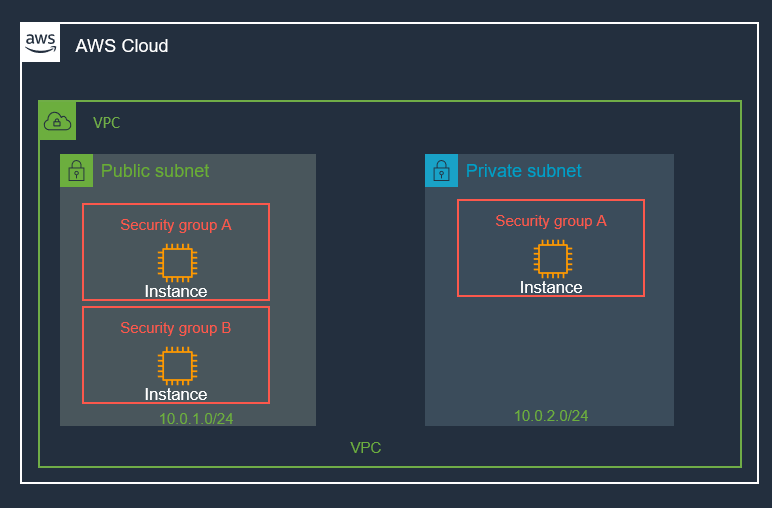
Traffic Flow to Instance
Let’s look at traffic flow to individual instances to understand how security groups fit in:
- Internet or VPN
- Router
- Route-Table
- Network Access Control List (NACL)
- Security Group (SG)
If traffic is allowed by the Inbound rule, then and only then, it will go to the instance.
Create Security Group
We can create security groups from the VPC dashboard:

Security Group Rules
We learned earlier that a security group is a set of inbound/outbound rules.
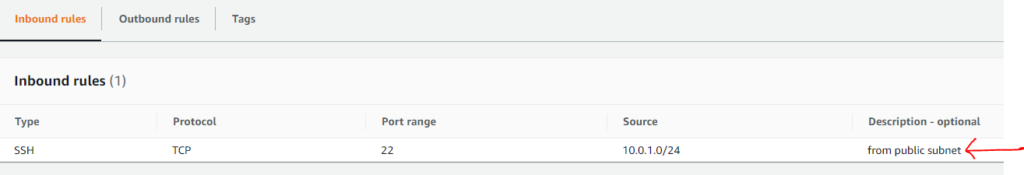
When creating the rule, you can also specify the Type (e.g TCP), Port, along with source or destination. Following picture shows Inbound Rules example:
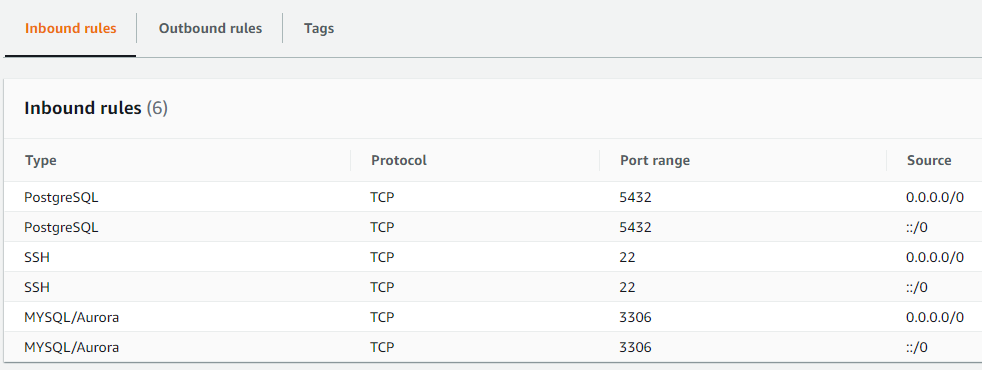
You can see that in the example, few Inbound rules are allowing incoming traffic, on certain ports from a certain source(s) (in this example from anywhere in the world).
Following picture show an example for Outbound rules:
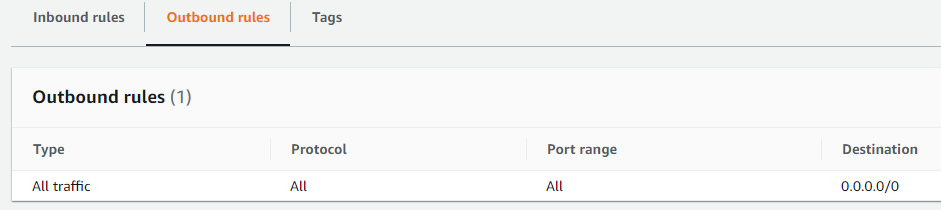
Here, in this example, we have a single outbound rule, which is allowing 'All traffic' to any destination.
In this example, both types of these Inbound/Outbound rules are defined in the same security group and when attaching to an EC2 instance, they act as a firewall for incoming/outgoing traffic.
Source/Destination
Given a rule, you can specify a few different things as source or destination of a rule:
- Security Group: First, you can define a security group (ID of another sg) in your VPC or a peered VPC (start typing
sgto see options). - IP Address: Next, you can have an IP address or a range of IP addresses from a certain subnet in your VPC. It can also be a single IP address of a particular machine that needs to have access (use
/32for a single IPV4 address).
When you set a Security Group as a source/destination; you are saying that any machine that is assigned to that security group can have access over the port or protocol that you defined and allowed through that rule.
Outbound rules follow the same format (called destination instead of source).
Use the description field for documentation. It is good when dealing with IPs or when reviewing your security groups to understand its purpose e.g.:
Summary
Security Groups allow (deny) access. They are virtual firewalls for your EC2 instances. They are stateful in design (unlike NACL, which is stateless). Let me know if you have any comments or questions. Till next time, Happy Coding!
Published at DZone with permission of Jawad Hasan Shani. See the original article here.
Opinions expressed by DZone contributors are their own.

Comments