BSides SLC: Community, Fun, and Security Best Practices in Salt Lake City
BSidesSLC brought together security experts, developers, and students from all over Utah and beyond. Read the highlights!
Join the DZone community and get the full member experience.
Join For FreeWith 2022 coming to a close, there was one last conference for the year, which happened in the snowy cold of Salt Lake City on December 16th. This event brought together security experts from multiple backgrounds, developers working to bring better security practices into their work, as well as students who were just starting down the path into InfoSec. No matter what skill level or area of security you forced on, there was something for everyone at BSidesSLC.
What Are BSides?
There are a lot of security conferences out there, but BSides stands out as unique. Rather than just a collection of talks, BSides is a community lead event that features hands-on labs, workshops, and collaboration, as well as industry experts presenting on a wide variety of cybersecurity topics.
I was encouraged by the number of students participating in this event. Thinking about the forecasted number of needed security professionals and open roles at companies vs. the currently too-small pool of applicants, it was great to see so many folks on the path toward meeting that challenge.
I will be covering some of the highlights of the talks a little later in this post, but first, let's take a look at some of the ways BSides stands out as a special event.
Unique Community-Built Badges
A very fun part of BSidesSLC is a tradition of electronic badges built by volunteers. These badges give participants something to hack into in real-time while the event was happening. This year's badge followed a "Rick and Morty" theme and ran off a Raspberry Pi Pico. The badges contained games, puzzles, and an eye-jiggling animation on the LCD. Best of all, these devices were fully hackable.
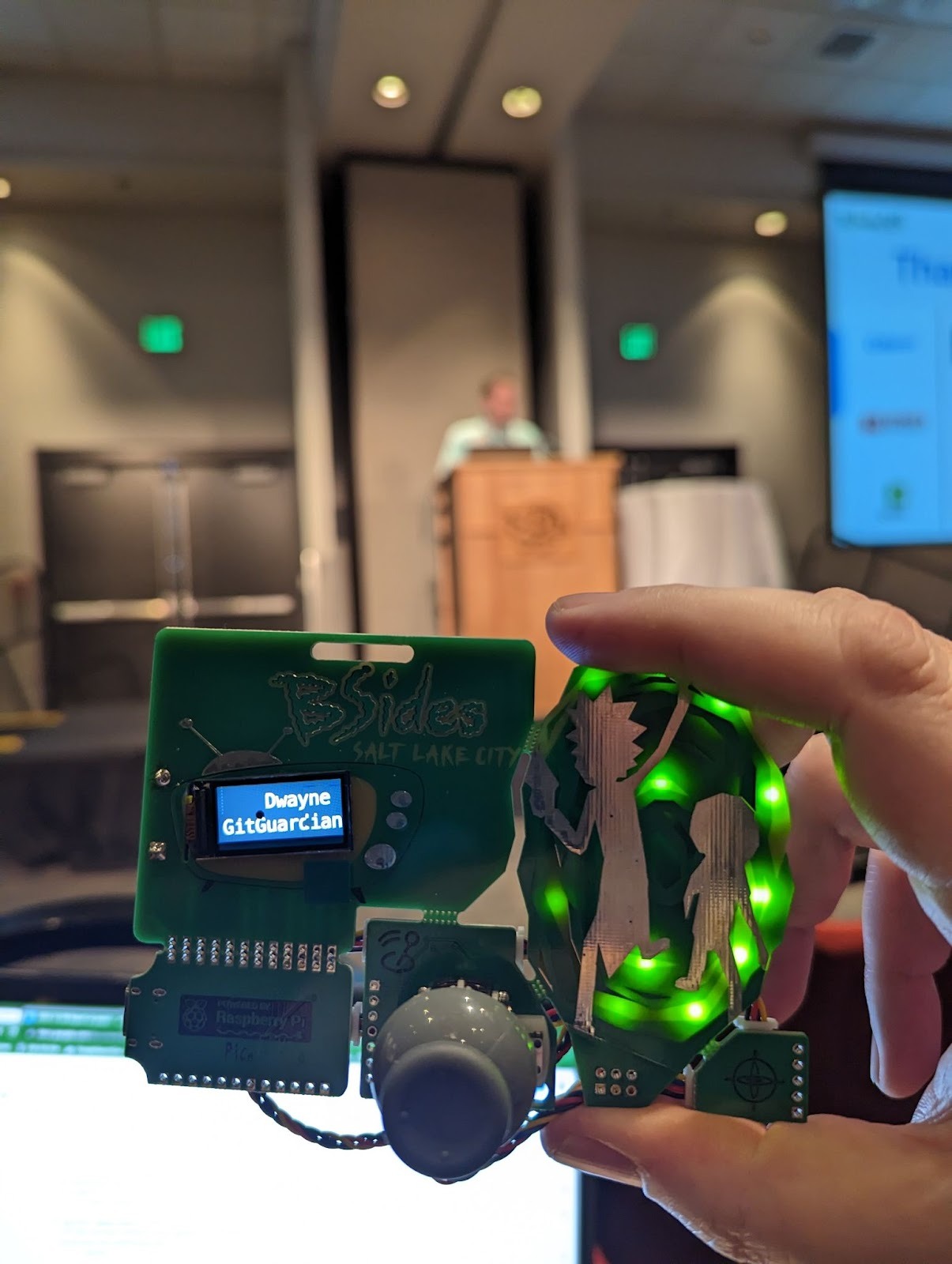
Not only were attendees encouraged to modify the software, as I did, adding my name to my badge as seen in the picture above, but there was a contest to see who could modify the hardware in the most unique way. Folks added more functionality and LEDs to these wearable microcomputers, with a winner named at the end of the event. Special thanks to community lead Professor Plum for creating these awesome badges and the team who lead the hardware modification lab.
Labs and Workshops
One advantage of in-person events is the chance to be very hands-on in labs and workshops. You can physically touch hardware and tools, as well as get help and encouragement from experts in the room. While online events offer the convenience of being able to participate from anywhere, there is nothing quite like being face-to-face while learning a new skill.
This year's workshops included:
- Raspberry Pi Pico 101 Basics — this was also the lab where you could modify your badge with the available tools and extra components they had available.
- Network Traffic Analysis and Suricata Signatures Lab
- Metasploit Intro & 101 Basics
In addition to the workshops, there were also labs and community events going on at the same time. These included:
- A physical security/lock-picking lab
- Hardware modification lab
- Home Lab — focused on understanding and modifying smart home devices and networks.
- Capture the Flag — a set of point-based security challenges that helps individuals and teams learn about real-world exploits in a fun tournament atmosphere.
The Hallway Track
While not an official part of the schedule, one of the best parts of any live event is the "hallway track." This is the general term for informally connecting with others in between sessions, in the hallways. Since BSidesSLC was spread across two buildings this year, folks had plenty of space and opportunities to connect as they moved between sessions and workshops throughout the day.
This is one of the biggest reasons I would encourage anyone to attend a BSides or any in-person community event in their area. You never know who you will meet or what conversations you will have. For example, at this event, I learned a good deal about incident response, security staff augmentation, and security operations centers, SOCs, from folks I met in between sessions. I made some awesome new connections and can't wait to run into them again at future events.
Session Highlights
No live event would be complete without sessions. There were over 30 speakers who covered topics from starting a career in InfoSec to in-depth sessions about using specific tools like BloodHound, Here are just a few high-level themes and highlights. All of these sessions, including mine, will be made available on the BSidesSLC YouTube channel soon.
Communication Between Teams Is Important
One theme I heard reiterated throughout all the talks was the value of communication for good security posture. In her talk "Building Stronger Relationships between Security and Engineering Teams," Senior Security Program Manager Astrid Bailey discussed how Adobe organizes and prioritizes communication between over 200 product teams. She described the process of getting security requests integrated early in the product roadmap and how the security teams worked closely with the product team leaders to ensure they were on the same page from the start of any new initiative.
One of the biggest takeaways from her session was the importance of executive buy-in. She said to present narratives instead of reports full of dry facts and walked us through using dashboards to present stories to the executive team. She suggested highlighting how each department and product measured up against one another as a way to motivate VPs to elevate security in their list of competing priorities.
Storytelling came up again in AppSec specialist Shelby Pettit's talk "Document It, Or It Did Not Happen: Writing a Quality Pentest Report." Shelby explained that while she is not a penetration tester, she is someone who consumes pentest reports regularly. This has given her a lot of experience with what formats are the most effective, and she was happy to share multiple tips and best practices for getting your message across clearly.
She stressed the importance of assuming most people reading pen-testing reports will not be security experts. If cybersecurity jargon is needed to explain any points, a short explanation of the concept will help the readers, from product managers to senior VPs, grasp the importance of your report. If a reader has to go investigate something independently to read your report, then there is a good chance they will not be able really to understand your proposed solutions and changes. Getting buy-in is critical to advancing security.
Another session that emphasized communication and storytelling to get buy-in was "Building a Cybersecurity Strategy" from David Bowman, Systems & Security Manager at one of Utah's largest school districts. One way David starts conversations is with a cape. He occasionally puts on a cape with big security "S" on it and runs through the administration offices. While humorous, this gets the school officials' attention immediately and lets them know that a serious security matter has appeared that must be addressed.
David also stressed the importance of executive sponsorship in any security endeavor. If the business level can not understand the 'why,' then there is not much that will likely be done. Addressing the executive team with stories of how they are undeserving their end users, rather than just presenting facts and figures around potential security threats, delivers the same basic information but frames it in a way where executives what to do something about it to improve the organization overall.
Understanding Security Events To Help Us Prepare for the Future
Another common thread throughout BSidesSLC was building for a more secure future by looking at recent incidents. The session that highlighted this idea most directly was "Why Data Breaches Aren’t Like Plane Crashes, But Should Be," by security researcher Doug Hubbard. He gave a quick overview of several Boeing 747 Max disasters from 2018. He noted how the reporting and disclosure from Boeing and investigators were very open and honest. Everyone developed a clear and direct understanding of the issues and solutions being put forth. While these incidents were tragic for all those involved, overall, air travel is safer because of these learnings.
He then compared the airline industry's openness to how most security incidents are reported and communicated. Where the airlines are very open to the causes and remedies, most security teams are very vague in their reporting and try to downplay the severity of the incident's effect on the overall business. He posits that this closed-off approach is doing us all a disservice, and we need to be able to thoroughly dissect incidents at other organizations as part of the process of securing our own.
He recommended several places he looks for security news on a daily basis and suggested everyone make a habit of routinely seeking out such news and staying on top of trends. His list contained sources like The Register, Krebs on Security, and BleepingComputer, among others. The landscape is always changing, and staying informed is one of the best ways to know where to focus your attention for better security.
Taking a slightly different approach, Wyatt Schirmer's talk "How Small Businesses can Prepare for Big Attacks" focused on clearing up historical misconceptions that keep small to medium-sized businesses, SMBs, from embracing better security posture. In his work as an Incident Response Lead at Tanium, he shared objections he hears from businesses as well as the truth of the matter. These objections include:
- We are too small to be a target — The truth is attackers don't care about the size of the business; they will exploit any vulnerability wherever they find one.
- Recovery from a cyber attack happens just like any other disaster — The truth is unlike a flood or a fire, public trust is eroded, many of the costs appear down the road as any data stolen is leveraged in future illegal activities, and unless you fix the underlying problems, you are likely to have the same thing happen again.
- We don't have the budget for in-depth cybersecurity — In reality, there are a lot of ways to protect your business that are free or low-cost to implement. Multi-factor authentication is a prime example, as most all applications allow or encourage you to use it without additional costs.
Wyatt went on to list a number of low-cost ways to better secure enterprises of all sizes and shapes. This included educating employees on phishing, which is the number one way attackers gain access to an internal system. It is also extremely helpful to talk to security professionals to help clear up misconceptions and myths about protecting your business, as there are a lot of third-party security teams that are very willing to advise any size company.
Security Automation
One other idea came up in multiple talks throughout the day; Automation.
In his talk "Building an Auto-Remediation Platform for the Cloud," Director of Cloud Security at Nu Skin Taylor Wilson covered Cloud Security Posture Management, CSPM, tooling, and the importance of automating your response. In short, CSPMs are tools that detect risk in cloud configurations. While there are a lot of options on the market, with most platforms offering their own flavor of tooling, Taylor stressed the importance of doing due diligence in selecting a tool that is going to cover your organization the best overall.
Once you have the right CSPM tooling in place, it will only be as valuable as the actions you take once an alarm is raised. The faster you can act, the more secure overall you will be. He shared his approach of building easy-to-maintain sets of AWS Lambda functions that can kick off a response in under 10 seconds from the alert being issued. These short executable bits of code can also be expanded as your infrastructure evolves.
While not every incident response is fully automatable, certain functions can and should be, such as gathering information about the vulnerable system, as well as facts about the incident; these are things you would otherwise manually need to do every time. You can also automate initiating communications through email or pulling all the needed players into a dedicated Slack channel to start finding a solution.
Taylor also suggested looking into what automation capabilities your Security Orchestration, Automation, and Response tooling, SOAR, offers before building your own, as often they will offer a no-code or low-code option that will require the least amount of effort to implement and maintain.
While Taylor stressed no-code or low-code approaches to automation, the session from John Gillis, Senior Security Analyst at Adobe, entitled "Next Level SOC Automation You Never Thought Of," immediately dug into the code for an approach to extending the Chrome browser for overall better security.
In his talk, John unveiled his example public GitHub project Chrome Extension MV3 Get Started, designed to "help you get started with your own Chrome extension." The basic idea, which you can test for yourself, is to help speed up a developer's research by creating a "Check Vulnerabilities" button that will appear when you are looking at a Pypi project page which will take you to a search for all known vulnerabilities for that package.
This approach might sound like it can only save a few seconds, but as John said, seconds quickly become minutes, which quickly add up to hours and days. Having the button inserted into the page also promotes consistent usage, truly automating it into the process, always reminding the developer to take the extra step to make sure they are aware of the risks they might be introducing into the code.
The repository he shared is marked as "intended for training purposes only" but gives a solid foundation to build from for building your own extensions that can help automate just about anything inside Chrome.
Looking Forward to More BSides in 2023 and Beyond
BSidesSLC was the last cyber security event of 2022, but it is far from the last BSides or security event on our calendars. We are proud to support the BSides community. You will see GitGuardian as a participant and sponsor of upcoming BSides in 2023, including Las Vegas, Montreal, Orlando, San Francisco, St Louis, and of course, Salt Lake City. Start marking your calendars now for the BSides in your area. You don't want to miss taking part in these awesome community experiences.
Published at DZone with permission of Dwayne McDaniel. See the original article here.
Opinions expressed by DZone contributors are their own.

Comments