Components of Container Management: Strategizing Beyond Build and Run
Strategizing beyond build and run: Explore the benefits of containers that are widely evident around the cloud-native world and its modernization journey.
Join the DZone community and get the full member experience.
Join For FreeThis is an article from DZone's 2023 Containers Trend Report.
For more:
Read the Report
Containers are a major catalyst for rapid cloud-native adoption across all kinds of enterprises because they help organizations quickly lift and shift legacy applications or break monoliths into microservices to move to the cloud. They also unlock system architecture to adopt a multi-cloud ecosystem by providing an abstraction between the application and underlying platform. Benefits of containers are widely evident around the cloud-native world and its modernization journey.
Enterprises on the cloud-native roadmap are adopting and running containers at scale. Containers are not only about building and running images — a lot more goes on behind the scenes for container management, including all the tools and processes covering the complete lifecycle of containers. When enterprises start adopting containers, they will only have a handful of containers to look after. In this case, "container management" looks like little more than having docker build and docker run. Ignoring a container management strategy can lead to developer and operator ineffectiveness, poor governance and compliance, and security challenges in the long term.
Giving priority to strategizing and managing the container lifecycle can help boost productivity and the effectiveness of developers and teams. It also contributes toward solution agility and helps in reducing the blast radius and vulnerabilities. Enterprises need to holistically consider container management planning and lifecycle before accelerating container adoption.
Aspects of Container Management Strategy
Let's understand various key parts of container management and its components.
Container and Image Supply Chain
Container images are building blocks for running containers. An image supply chain consists of all the nuts and bolts to make it executable on environments by pull, build, and run. An image supply chain also includes:
- All the layers of images built on top of the base image, which includes libraries and utilities that complement the containerized application package
- CI/CD tools that test and scan your packaging as a container image
- Static and runtime scanning for vulnerability detecting and patching, signing, or hashing of images to validate their sanctity in your registries or pipeline
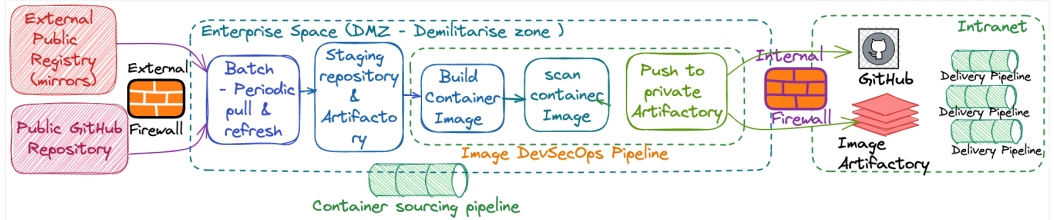
Figure 1: Container management lifecycle - Container image supply chain
Container Infrastructure Handling
Once your container image supply chain has been established (see Figure 1), you next want to run and build your application on top of it. For this, you need something on which you can run or execute containers. This includes compute for running containers and software logistics to schedule and organize them.
If you're working with just a few containers, you can still manually gauge and control where to run the containers, what else will be in the app sidecars, or support ecosystem components. Provisioning the right storage and networking for those containers can be manually or semi-automatically handled. At scale, however, it is almost unmanageable to handle a large workload without an intelligent orchestrator that orchestrates these infrastructures as well as other aspects of container execution.
Container Runtime Security and Policy Enforcement
It is equally important for your container management solution to perform security scans, competence checks, and policy enforcement. A management solution enforces policy and compliance in parallel with a runtime security scan for vulnerabilities inside a container pipeline, and it scans running containers on host nodes.
Container Monitoring and Observability
Images and containers are fully packaged with all the dependencies and prerequisites of apps running on top of an identified compute. Now we need to understand containers' behavior and what they are up to.
A containerization strategy — which covers monitoring and observability of logging, traces, and metrics collection — should include container workloads, orchestration, and tooling that support container execution. Container execution inside a cluster of managed infrastructure includes supporting tools and utilities for running containers. Orchestrators will also have their own logging and monitoring since containers are ephemeral in nature.
Planning Container Management Strategy
So far, we have discussed all major components of container management. Enterprises should address the following aspects while designing a container management lifecycle.
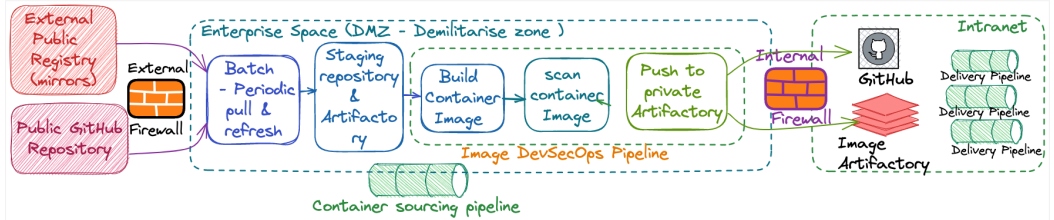
Figure 2: Container governance and policy compliance - Container management stages
Handling Image Supply Chain
Existing CI/CD tools can be leveraged to build container images after compiling code and base references. A few important things to handle while building your enterprise image supply chain are:
- The ability to scan container images in an enterprise repository
- Security and policy compliance
- Hashing or signing the image to avoid any tampering
- Scanning mirror images from a well-known and sanitized registry before bringing them into an enterprise repository
- Tagging and attributing images with details of the teams owning it for better support, portability, and upkeep
Some mature enterprises handle redundancy and replication of an image repository and artifacts to ensure high availability across the DevOps cycle, followed by periodic backups and a recovery process. Elastic, highly available, and fault-tolerant systems are not just limited to an execution environment but are equally important for the end-to-end DevOps cycle.
Infrastructure and Orchestration Handling Strategy
Infrastructure and orchestration handling strategy is all about the allocation of compute, storage, networking, and backups of containers running at scale. Selecting the type and quantum of compute is very important for designing containers.
Containers can only be truly portable if the underlying compute is elastic and supports X (horizontal) and Y (vertical) scalability. Storage requirements for containers can be a mix of OS usage as well as container persistence. It means that container operations require a well-planned storage supply with diverse options of file, block, and blob storage.
Networking is an essential part of the connectivity and delivery of a solution alongside enterprise security. Using a mature orchestrator like Kubernetes, Docker swarm, etc., provides different flavors of inter- and intra-container cluster connectivity.
Backups are an important part of operating containerized environments, which consist of mounted storage that holds data required to persist. A well-managed backup strategy contributes toward resiliency, cross-regional recovery, and autoscaling. For example, you can use image and container backups to recreate immutable read-only containers, given their ephemerality.
Container Security Principles
You are only as secure as your most vulnerable container. One of the main advantages of containers is that they reduce the blast radius and attack surface. Regular scanning and re-scanning of a repository is a good starting point, as you can see in Figure 2. Also, it is vital to consider implementing container runtime scanning — most likely traditional, agent-based host scanning to detect runtime anomalies.
Container images are immutable; hence, vulnerability patching should replace an old image with a new properly scanned and tested image. Patching hundreds or thousands of containers can be cumbersome and should be replaced with new containers based on updated and patched base images.
Container Observability Planning
Looking inside a dense cluster of small ephemeral containers is challenging, and they may grow out of control if not handled maturely. The 12-Factor App guides us through the critical aspect of externalizing your logs. Containers will come and go, but the draining of logs toward an external syslog gives you better insights via log aggregation and mining.
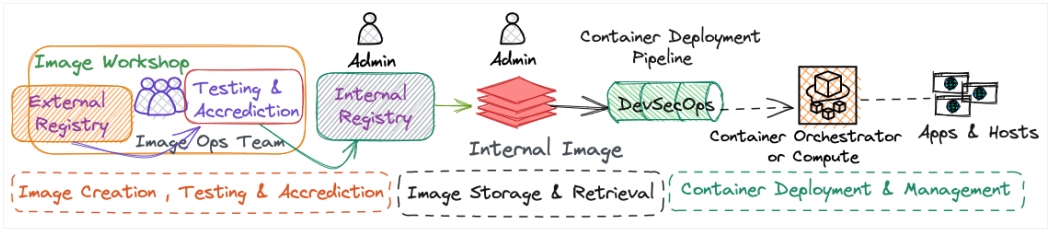
Figure 3: Container strategy phases and execution pipeline
Besides everything, developer experience is crucial in enterprise container management planning. It's important to analyze the productivity and effectiveness that the container lifecycle is bringing to developers and operators working on a DevOps pipeline chain. Enterprises also need to evaluate whether DIY or managed services (like EKS, AKS, or GKE) are a better fit for them.
The answer may depend on the enterprise's maturity around different aspects of infrastructure, networking, and security handling, as you see in Figure 3. Organizations' roadmaps for infrastructure (private vs. hybrid vs. multi-cloud architecture) should be considered in the container management strategy.
Best Practices for Building an Optimized Container Ecosystem
Let's quickly review some best practices to help build better containers:
- Package a single app per container
- Do not treat containers as VMs
- Handle container PIDs and zombie processes carefully
- Optimize
docker buildcache - Remove unnecessary tools and utilities from images
- Be cautious of using publicly sourced images vs. scanned enterprise build images
- Build on the smallest possible images
- Properly tag your images for better lifecycle handling
Conclusion
Finally, I am containerizing and packaging a portable summary of an effective container management strategy (pun intended). The takeaway is to inspect how effectively your engineers and developers are managing a large containerized production environment. How agile you will be in responding to urgent vulnerabilities? How soon you can respond to dynamic scalability requirements of compute and storage?
The 12-Factor App is an effective gauge of measuring container ecosystem maturity. When choosing your tool, consider options that support infrastructure requirements of today and tomorrow. Enterprises also need to determine whether to use DIY or managed services based on in-house maturity around container lifecycle stages. You can always strategize your plan around the re-use of tools and processes to manage containers as well as non-container components optimally.
This is an article from DZone's 2023 Containers Trend Report.
For more:
Read the Report
Opinions expressed by DZone contributors are their own.

Comments