Cryptography Module in Mule 4
Join the DZone community and get the full member experience.
Join For FreeSteps to Use JCE Encrypt and JCE Decrypt Connectors
- Check if Crypto module is available in Mule Palette. If not, download it from exchange.
- Then, search for JCE in the Mule palette. The Crypto module should be visible now.
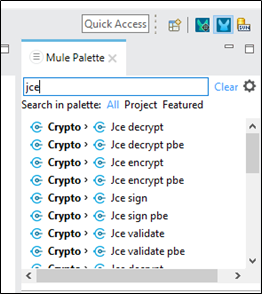
3. To use Jce encrypt and decrypt connector, we need a keystore.
- Generate a keystore using following command:
keytool.exe -genseckey -alias jksvalue -keyalg Blowfish -keystore encKeystore.jceks -keysize 128 -storeType JCEKS
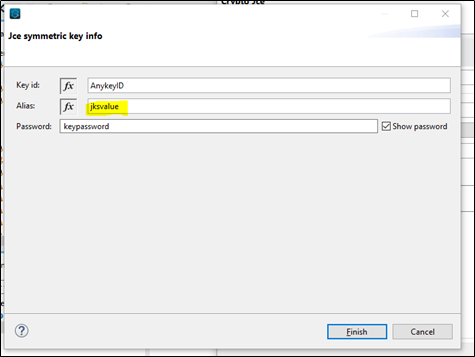
Alias name : jksvalue
Algorithm used : Blowfish
Keystore file name : encKeystore
Keystore file type : jceks
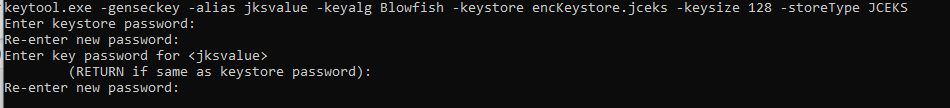
Keep the keystore and key passwords. These passwords need to be use in JCE configuration.
- Store the generated encKeystore.jceks file in resource folder of mule project.
- Take Jce encrypt connector from the Mule palette and do the module configuration as shown below :
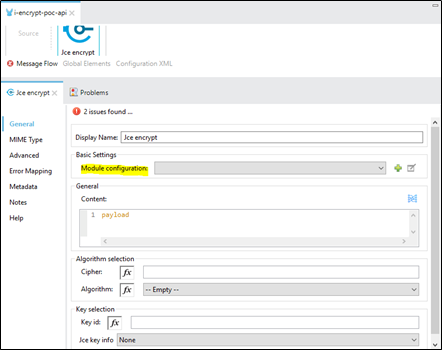
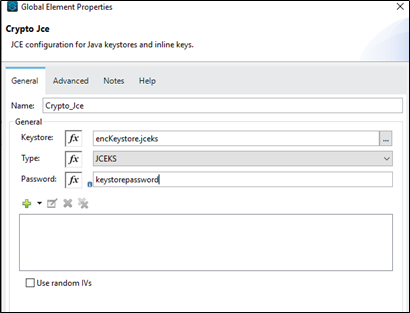
We are using a symmetric key (same key for encryption and decryption). Add the symmetric key details using the + button in the above image.
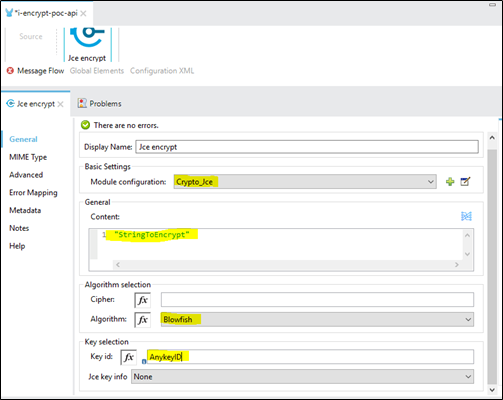
Do the remaining configuration just shown in the above image. Note that the algorithm should be the same, which we used for creating the Keystore and the Key id in the above two images should be identical.
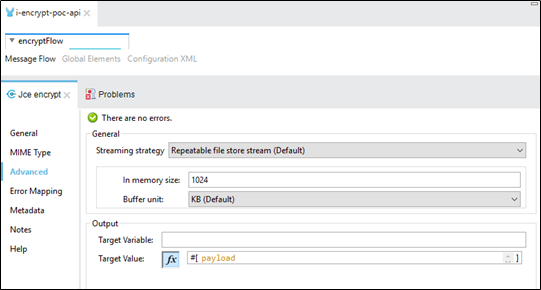
Check the advanced section.
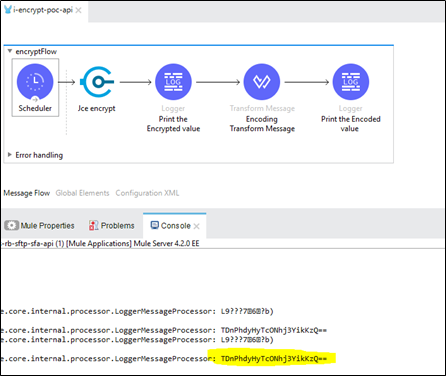
The output of this component below is the encrypted value :
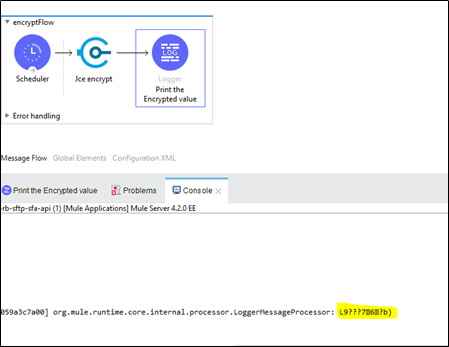
The encrypted value has a few characters, which cannot be shared or we cannot type it. Here comes the encoding part to convert the encrypted string to Base64 format.
Encoding can be done using the below transformation:
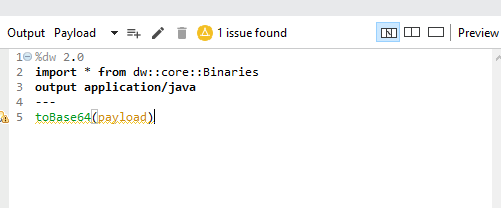
The output of encoding is below:
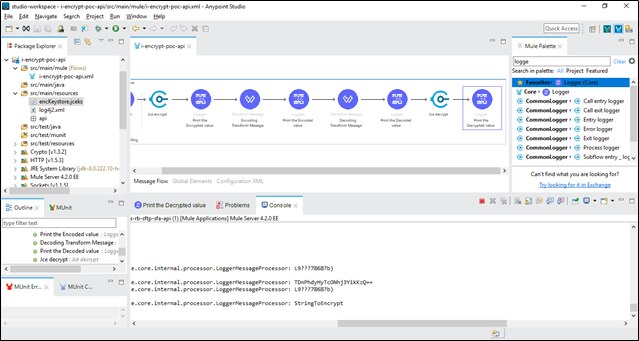
In the same way, we have to first decode the payload and then decrypt it:

Opinions expressed by DZone contributors are their own.

Comments