Data Protection: Utilizing the Power of SIEM and CASB
This article will evaluate how these two technology can complement each other to provide holistic security to organizations.
Join the DZone community and get the full member experience.
Join For FreeThe requirement for monitoring, identifying harmful behaviors, and preventing or notifying of these activities is growing quickly as the number of malicious insider and external attacks rises. The threat landscape is constantly changing, making strong security monitoring and detection solutions essential. Security Information and Event Management (SIEM) and Cloud Access Security Broker (CASB) are two essential technologies that support this effort. While they both aim to improve security visibility and posture, their scopes and functionality are different. Let's examine their similarities and differences, recognize the advantages of each, and see how these two approaches might be combined to improve the security infrastructure of an organization.
![utilizing power of SIEM and CASB]() Similarities Between SIEM and CASB
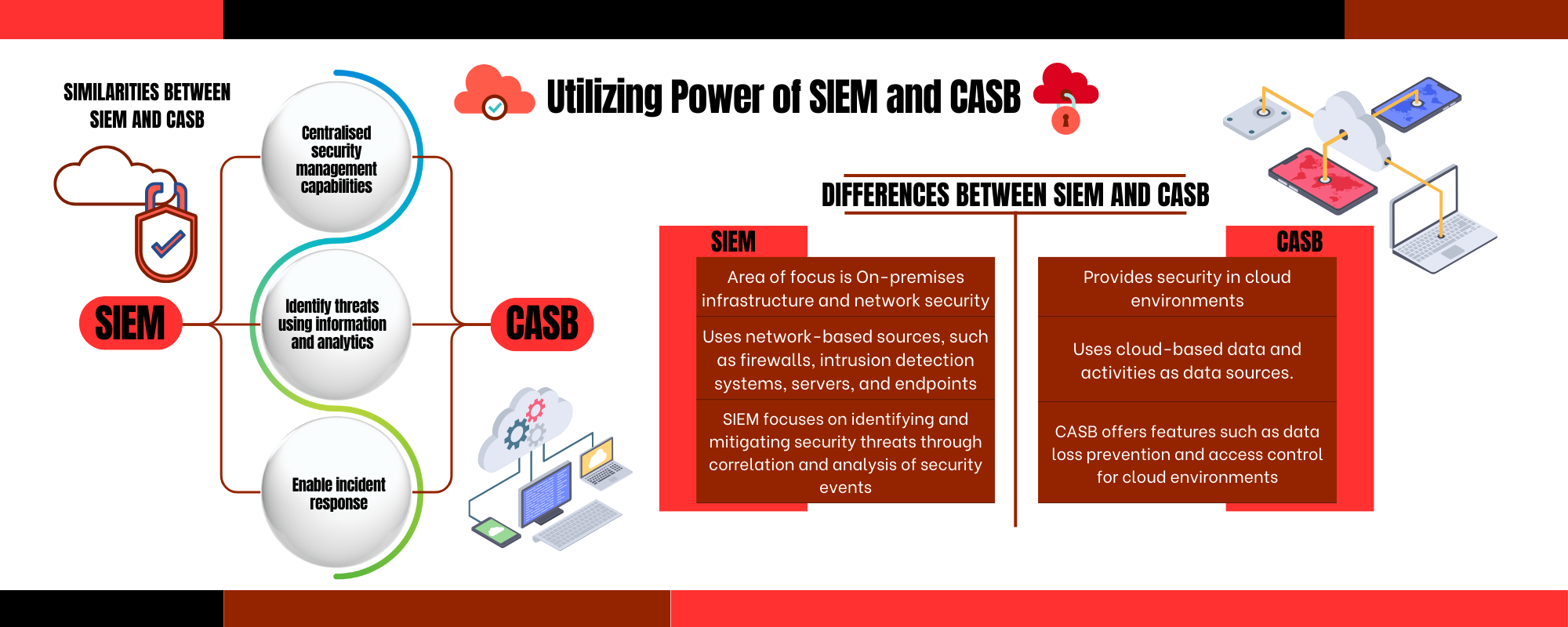
Similarities Between SIEM and CASB
- Centralized security management capabilities: Centralized security management capabilities are provided by both CASB and SIEM, respectively. Security event logs and data from many sources, including network devices, servers, and apps, are gathered and analyzed by SIEM solutions. The same is true for CASB systems, which offer centralized visibility and control over user activities, data, and cloud application usage across many cloud service providers.
- Identify threats using information and analytics: Both SIEM and CASB solutions help in threat detection using dynamic content and intelligence. To find trends and abnormalities suggestive of possible security incidents, SIEM systems use advanced analytics and correlation techniques. Cloud usage is tracked by CASB systems, which also spot unusual activity and send out alerts for possible threats or rule violations.
- Enable incident response: The Security Orchestration, Automation, and Response (SOAR) system or Incident management can use the incidents and detection produced by SIEM and CASB.
Comparison of SIEM and CASB
- Focus and Scope: On-premises infrastructure and network security are the main areas that SIEM systems concentrate on. To give thorough security insights and facilitate efficient incident response, they gather and analyze logs and events from numerous sources across the organization's network. CASB solutions, on the other hand, are experts in securing cloud environments. They concentrate on tracking and protecting user interactions, data, and cloud applications across a range of cloud service providers.
- Data Source and Visibility: SIEM tools gather information from a variety of network-based sources, such as firewalls, intrusion detection systems, servers, and endpoints. This makes the organization's infrastructure completely visible. While offering fine-grained insight into cloud applications, data flows, user activities, and compliance posture within the cloud environment, CASB solutions, in contrast, concentrate on cloud-based data and activities.
- Security Controls and Enforcement: The main goal of SIEM systems is to find and examine security incidents while also producing alerts. Insights into security incidents are provided, and incident response is supported by the correlation of data from diverse sources. On the other hand, CASB solutions provide a selection of security measures tailored to cloud environments. They give organizations the tools to implement security policies and reduce cloud-specific risks, including data loss prevention (DLP), access control, encryption, and activity monitoring.
- Integration and Extensibility: SIEM solutions frequently integrate with a variety of security tools and technologies, enabling businesses to gather and correlate data from diverse sources. To improve total security visibility and reaction, they can be integrated with intrusion prevention systems, vulnerability scanners, and other security solutions. By integrating with the APIs of cloud service providers, CASB solutions give users insight and control over cloud data and apps.
Complete Data Protection With Integration of SIEM and CASB
The problem of protecting company data from malicious insiders or outside attackers is one that these two powerful solutions address on two separate sides. The two technologies work well together. These days, the majority of insider leaks involve transferring data from a cloud or SaaS application to an endpoint and then to another cloud or web destination.
A complete time series picture of activity and data movement graph can be obtained by combining these two systems. This can assist give a complete view of activity, develop analytics utilizing an activity graph, and more confidently identify malicious behavior.
Additionally, given total visibility of data movement and user activity, discovered incidents can be completely cleaned up or prevented from endpoints as well as from cloud and SaaS using automated incident response or SOAR systems.
Conclusion
Solutions like CASB and SIEM are essential for improving an organization's security posture. CASB focuses on securing cloud settings, whereas SIEM is more concerned with on-premises infrastructure and network security. Both platforms offer capabilities for centralized management, threat detection, and incident response, but their range and depth of functionality vary greatly.
Organizations might think about merging SIEM and CASB systems to achieve thorough security coverage. Through this connectivity, on-premises and cloud environments can have a single picture of security, improving visibility, connecting security events, and facilitating more efficient incident response. Organizations can ensure a more robust and well-rounded security infrastructure to successfully tackle the changing threat landscape and secure their crucial assets by combining the strengths of both SIEM and CASB.
Opinions expressed by DZone contributors are their own.

 Similarities Between SIEM and CASB
Similarities Between SIEM and CASB
Comments