7 Essential Steps for Conducting a DLP Risk Assessment
By using DLP to address potential weaknesses before they are exploited, organizations can avoid the devastating consequences of data breaches.
Join the DZone community and get the full member experience.
Join For FreeA thorough DLP risk assessment empowers organizations to move beyond simply reacting to data breaches and toward proactively mitigating risks. It provides the necessary insights to identify vulnerabilities, evaluate the effectiveness of current DLP solutions, and implement effective security policies.
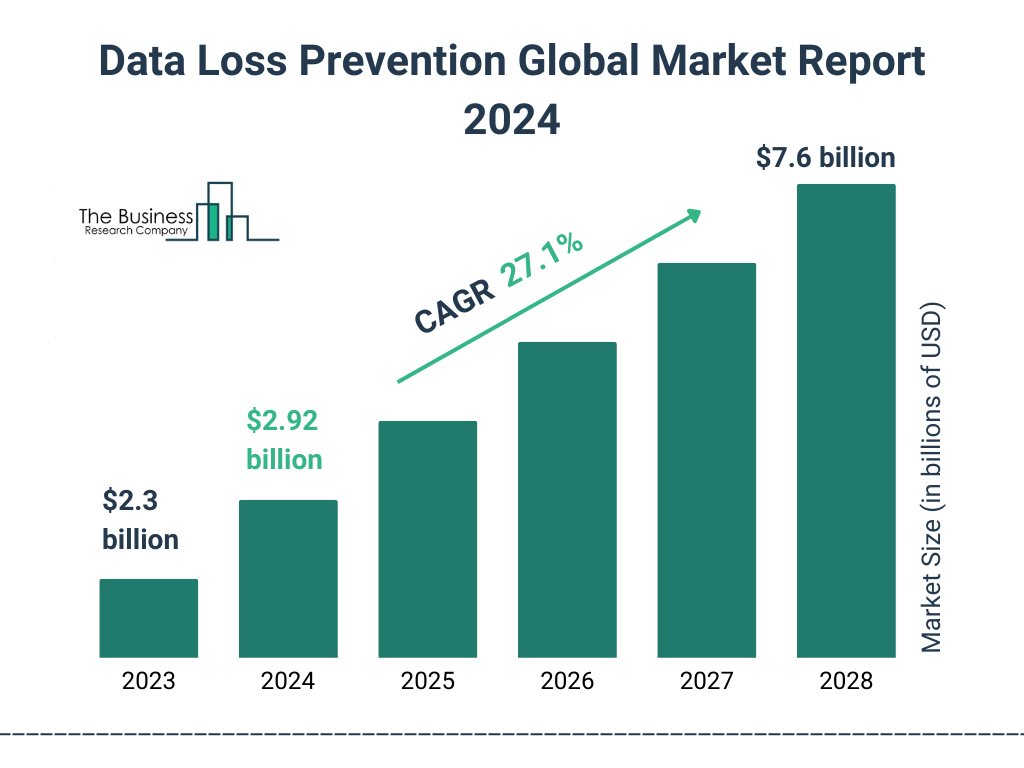
Thus, by addressing potential weaknesses before they are exploited, organizations can avoid the devastating consequences of data breaches. The seven steps highlighted below will help organizations build a resilient defense against data loss and unauthorized access to sensitive data assets.
1. Set Clear Objectives and Define the Scope
The first step in conducting a DLP risk assessment is to establish well-defined objectives and clearly delineate the scope of the assessment. This foundational step is crucial for ensuring that the assessment remains focused and aligned with the organization’s overall security goals.
For instance, objectives might include identifying the most vulnerable data repositories, evaluating the effectiveness of existing DLP solutions against existing threats, or assessing compliance with specific regulatory frameworks.
Defining the scope is equally essential, as it establishes the boundaries of the assessment, such as the systems, data types, and departments that will be included. Clearly defining the scope ahead helps in allocating resources effectively and ensures that the assessment is exhaustive within the defined boundaries
2. Identify and Classify Sensitive Data
Once the preliminaries are done, the next crucial step, where the ‘real’ assessment starts, is to create a comprehensive inventory of all the organization’s data assets, with the aim of classifying data based on sensitivity level and the applicable regulatory requirements. This step is paramount because it lays the groundwork for understanding the value of the data and the potential impact of its loss.
Typically, classifying data involves pre-defined policies and rules based on factors such as data type, content, purpose, etc. Often, the most sensitive data usually include some kind of personally identifiable information (PII), financial data, healthcare information, company secrets, intellectual property, etc., and they require stringent protection.
3. Analyze Potential Threats
The more sensitive a piece of data is, the more significant the threats are. This is why the previous step is crucial. Still, it is at this third stage that you evaluate and quantify the likelihood and potential impact of the loss of such data because they vary based on various factors like industry, current protection measures, geographical region, and so on.
Particularly, pay attention to the risks of negligent and malicious insider threats, which comprise the vast majority of data breaches today. DLP systems play a crucial role in mitigating insider threats by preventing unauthorized access to sensitive data.

4. Evaluate Current DLP Controls and Policies
In order not to leave your data loss prevention to chance, a thorough evaluation of your security measures against known threats will spotlight vulnerabilities before they turn into breaches. So, it’s necessary to take time to assess your DLP tools, understand how your employees handle sensitive information, test your access controls, and ensure your incident response plan holds up under pressure.
When it comes to DLP, you need several pieces of the security puzzle working together to protect different areas of your network and systems. But installing these tools isn’t enough. You need to ensure they are doing their job: stopping potential unauthorized access, flagging suspicious transfers, identifying sensitive data, etc.
5. Quantify Risk Levels and Prioritize
Now that you can see where your sensitive data lives and how well your security measures stack up, at this stage, it's time to get practical. Look at each vulnerability you've found and give it a risk score by considering both how likely it is that someone could exploit it and how much damage a breach could cause. Factor in your current DLP safeguards, too - they might be more robust in some areas than others.
In any case, you need to understand that fixing everything at once is impossible. Prioritization is crucial so you can determine where to focus your time and money. This requires thinking about what matters most: How sensitive is the data? How valuable is it to your organization? What kind of damage could a breach cause?
6. Develop and Adopt Mitigation Measures
Now that you know which risks matter most, it's time to put real solutions in place. Your fixes should do two things: make data breaches less likely to happen and reduce the damage if they do occur.
Your risk assessment findings should guide your security fixes, keeping them in line with your bigger data protection picture and strategy. These measures can encompass a wide range of actions, including:
- Implementing or upgrading DLP solutions
- Strengthening security policies
- Enhancing access controls
- Providing employee training and awareness programs
- Conducting regular security audits
7. Implement Continuous Monitoring
Data protection isn't a one-and-done project; it needs to become part of your company's DNA. That means you need to set up ways to keep watching and testing your security measures because threats keep changing, and new vulnerabilities constantly pop up.
Data Loss Prevention tools act as watchdogs, tracking how data flows through an organization in real time. When suspicious activity occurs, security teams can spot and address the issue immediately. These tools work even better when connected to the organization's broader security ecosystem, particularly SIEM platforms and threat intelligence systems.
Conclusion
Don't think of a DLP risk assessment as just another box to check - it's really your best defense against data breaches. By spotting and fixing security weak points before they become problems, you're protecting what matters most to your organization. Follow these steps, and you'll be in a strong position to keep your critical data safe.
Opinions expressed by DZone contributors are their own.

Comments