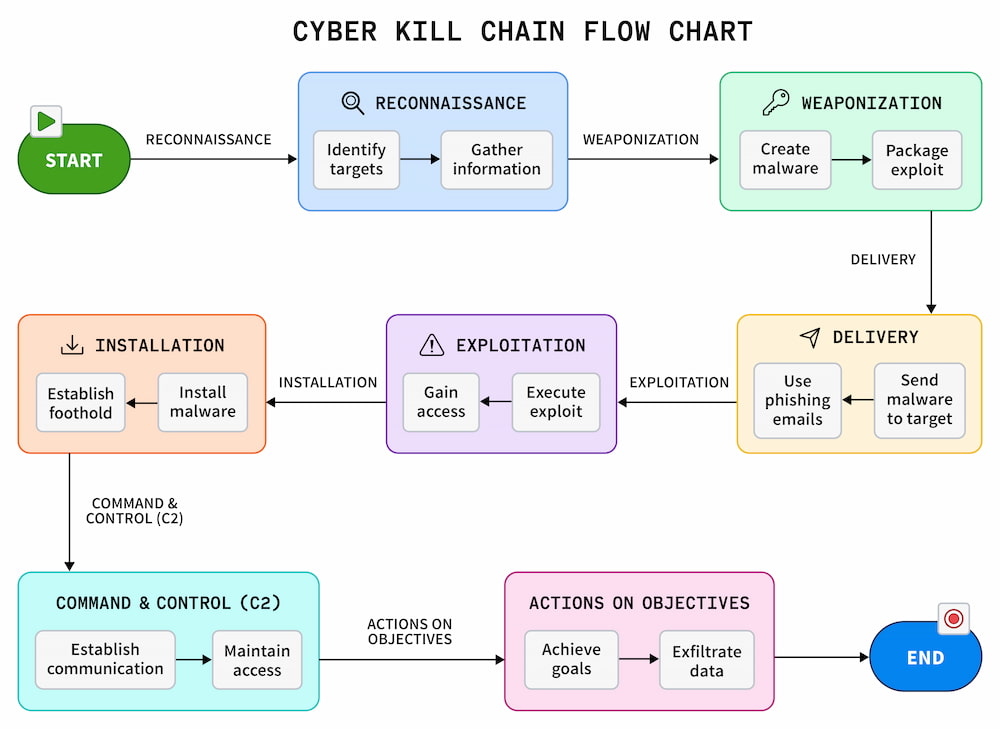
Threat detection requires a multifaceted approach that constantly adapts to the ever-changing cyber landscape. It is also important to note that recognizing the "what" through indicators of compromise (IOCs) and known malicious patterns is only half the equation. The ability to identify the "how" via predictive analytics, anomaly detection, and threat intelligence feeds — all aligned with strategic incident response planning — forms the other essential half.
The progression from foundational techniques, like signature- and behavior-based analysis, to advanced machine learning (ML) and heuristic methods highlights the industry's gradual innovation over the years. The tables below summarize these methodologies and the purposes they serve:
Table 1: Primary threat detection methodologies by threat source
| Approach |
Attributes |
Purpose |
Method
|
|
Internal
|
External
|
Signature-based detection
|
Relies on known patterns and definitions to identify threats |
Identify and block known malicious codes and viruses, originating externally or from those that have already infiltrated the system |
Antivirus software, intrusion detection systems |
Email filtering, web content filtering, network intrusion prevention systems |
|
Behavior-based detection |
Monitors and analyzes unusual system behavior to detect anomalies |
Detect insider threats or attempts to exploit vulnerabilities from external sources |
User and entity behavior monitoring |
Anomaly detection in network traffic, cloud security monitoring |
Table 2: Advanced threat detection methodologies by threat source
| Approach |
Attributes |
Purpose |
Method
|
|
Internal
|
External
|
|
Heuristics |
Utilizes rules and patterns to identify suspicious activities |
Quickly identify potential threats with less data |
Privileged access management, insider threat detection systems |
Email scanning for spam and phishing, web app firewalls, fraud detection |
|
Anomaly detection |
Detects deviations from established baselines, revealing potential threats |
Detect unknown sources by identifying behavioral anomalies |
User behavior analytics, file integrity monitoring |
Network traffic analysis, cloud security, endpoint detection and response |
|
ML algorithms |
Employs algorithms that learn and adapt to detect new and evolving threats |
Adapt to the evolving threat landscape, including new external attack vectors, with continuous learning |
Insider threat detection, user and entity behavior analytics |
Adaptive threat detection, predictive threat analysis, security information and event management |
Core Practices of Threat Detection
Effective threat detection relies on a cohesive set of core practices that collectively form the defense against internal or external threats. The following practices are essential pillars that represent a multifaceted defense strategy, each one tailored to address specific challenges in the modern cyber environment.
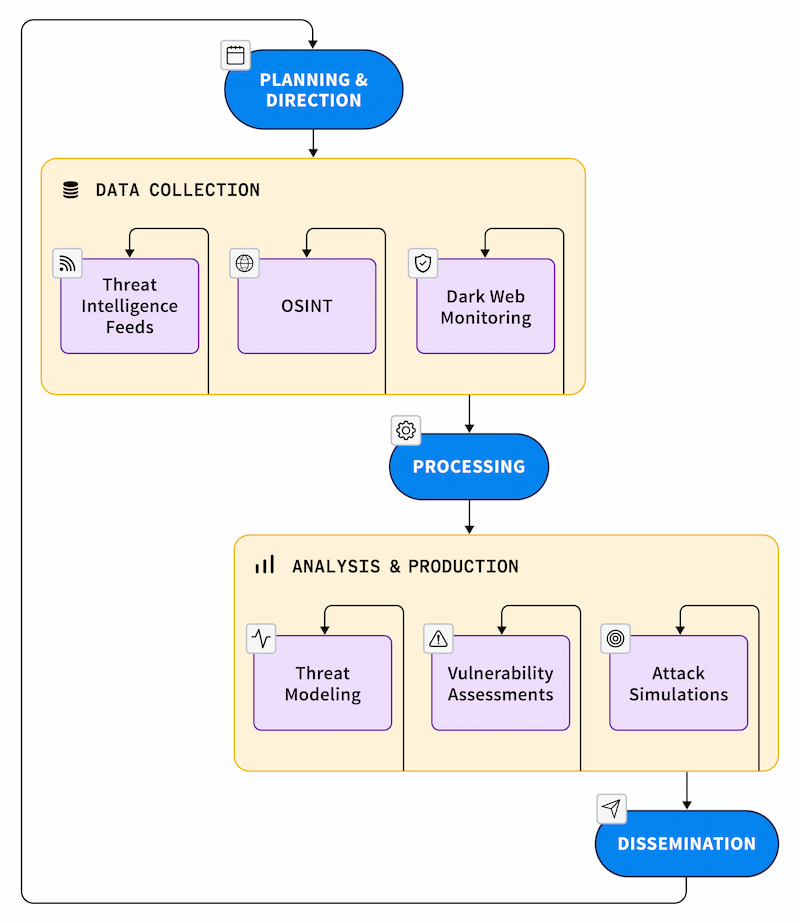
Figure 2: Cyber threat intelligence cycle
Exposure Management
Exposure management functions as a critical threat detection pillar that focuses on the comprehensive assessment of an organization's external-facing attack surface — all the points where external threats can potentially infiltrate your systems and networks. Representing a strategic alignment of technology and process, the primary purpose of this stage is to understand the scope of what needs to be protected, optimizing response mechanisms against an ever-changing cyber environment.
This is typically achieved by implementing the following series of measures:
- Scoping exposure and identifying blind spots – Contrary to popular belief, even the most advanced tools can render an organization vulnerable if they are misconfigured or fall outside of organizational bounds (e.g., cloud services, other IT assets). Detailed and ongoing mapping of exposures accessible from the internet or other external networks is essential. It's critical to understand context like ownership and connections, especially for complex organizations that may have branches, made acquisitions, or have other complicated ownership structures.
- Building and refining risk mitigation processes – Subsequent to identifying gaps, efforts must be made to bridge them and enhance existing risk mitigation processes. Delineating accountability based on security roles is vital as it not only instills a sense of responsibility but also refines the risk mitigation blueprint into a more agile and adaptive system.
- Measuring and aligning remediation efforts – Metrics play a crucial role in this stage, tracking remediation processes (e.g., response times) to critical vulnerabilities. Continuous monitoring and alignment of these metrics with changes in the security infrastructure ensure that the exposure management strategy remains robust and agile.
Proactive Threat Hunting
Going beyond exposure management's focus on known vulnerabilities and visible attack surface, proactive threat hunting delves deeper to actively neutralize unknown, concealed threats originating from external sources. Unlike traditional methods that react to security incidents as they occur, proactive threat hunting searches through networks to detect and isolate advanced threats that have already infiltrated existing security solutions.
Consider the complex role that threat feeds, IOCs, and indicators of attack play together. A diligent analysis of these components can provide significant and actionable insights into attackers' attack patterns. The real challenge, instead, is to separate valuable signals from inconsequential noise, a task demanding both technical expertise and strategic insight.
For a more comprehensive approach, consider the following actions:
- Understand the unusual – Delve into endpoint activity, network architecture, and typical user behavior to spot the unusual. This baseline knowledge should be tested by simulating cyber attacks through red teaming exercises in a controlled environment, revealing weaknesses that might not be apparent otherwise.
- Challenge the standard – Reject the notion of a universal method that fits all use cases. Embrace constant evaluation and change by utilizing key performance metrics and keeping an observant eye on the shifting threat landscape.
- Employ agile tactics – Adapt techniques and maintain vigilance toward evolving cyber threats. Ensure that the threat hunting process remains as adaptable and formidable as the ever-changing cyber environment itself.
Employing Advanced Threat Detection Systems
Evolved cyber threats extending beyond traditional perimeters to target both physical and virtual infrastructures demand an adaptive response. Intrusion detection systems (IDSs) with advanced persistent threat (APT) correlation, and intrusion prevention systems (IPSs) with stateful protocol analysis, serve this purpose by administering a continuous surveillance mechanism against network anomalies.
IDSs' behavior-based detection models raise the alarm on suspicious activity, and IPSs neutralize the threat swiftly. But the dynamics change with the adoption of hybrid cloud and bring-your-own-device (BYOD) approaches, opening up new threat vectors that require specialized attention. Understanding these vectors is crucial as they can extend into previously secure areas, thus demanding a broader perspective on threat management.
Endpoint detection and response (EDR) solutions and cloud access security brokers (CASBs) are designed to tackle these unique vulnerabilities:
- An EDR monitors and mitigates device-level threats through graph-based analytics and automated playbooks. The approach is particularly crucial in countering sophisticated external attacks that often target individual endpoints as a means of gaining a foothold within the network.
- CASBs safeguard cloud accounts from malicious activities, including advanced persistent threats and malware, administering a resilient security architecture.
The integration of these systems is as critical as their individual roles. When properly aligned, they create a holistic security environment that adapts to changing threats, recognizing patterns that might be missed in isolation. For example, combining insights from EDRs and CASBs can provide a complete view of both internal and external threat movements, enhancing the reaction time to incidents.
But in the face of advanced threats, are traditional security systems completely irrelevant? Not really.
Despite their conventional nature, security information and event management (SIEM) systems continue to add depth by correlating and analyzing security events across the threat landscape. Through integration with various security sources and threat intelligence feeds — and employing complex event processing (CEP) — SIEMs detect subtle, sophisticated attacks, ensuring a uniform security posture across all assets.
This layered approach to threat detection, integrating both new solutions and augmenting existing tools, creates a robust, flexible defense strategy capable of not only reacting to current threats but also anticipating future challenges.
Effective Incident Response Planning
The foundation of an effective incident response is a robust incident response plan (IRP), which guides swift action during a security incident, supported by the specialized skills of an incident response team. Regular incident response drills take this preparedness a step further, replicating potential threats and solidifying a proactive stance.
It is, however, important to note that creating a resilient and agile response strategy does not follow a linear path. Instead, it is a continuous cycle that demands both strategic foresight and multi-layer execution. The real art also lies in balancing readiness with continuous adaptation to new threats and vulnerabilities, ultimately crafting an incident response that evolves with the cyber threat landscape.
Table 3: Incident response stages
| Stage |
Key Actions |
Considerations |
|
Prepare |
- Develop policies, guidelines, and procedures
- Assign roles
- Acquire tools
- Implement readiness measures
|
- Consider unique challenges posed by sophisticated attack vectors, targeted campaigns, and data exfiltration attacks
- Ensure the IRP addresses such risks and incorporates relevant tools and techniques for detection and response
|
|
Identify |
- Recognize signs of an incident
- Analyze system logs
- Assess accurately
- Ensure proper communication
|
- Focus on identifying IOCs and IOAs associated with external threats
- Leverage threat intelligence and advanced analytics to facilitate timely detection and accurate assessment of the incident's scope and impact
|
|
Contain |
- Implement short- and long-term strategies
- Isolate systems
- Plan long-term containment strategies
|
- Prioritize containment measures to prevent further lateral movement and data exfiltration by external attackers.
- Implement network segmentation, access controls, and other measures to limit the attacker's reach
|
|
Eradicate |
- Identify root cause
- Remove malware
- Restore functionality and avoid future recurrence
|
- Thoroughly investigate the attack vector and identify any vulnerabilities exploited by external attackers
- Implement patches, updates, and configuration changes to address these weaknesses and prevent future breaches
|
|
Recover |
- Confirm restoration of all functionalities
- Implement additional security measures
- Adjust based on lessons learned
|
- Completely restore systems and data, validating their integrity and functionality
- Implement additional security measures (e.g., enhanced monitoring and detection capabilities) to protect against future external attacks
|
|
Lessons learned
|
- Analyze incidents
- Document insights for future prevention
- Update and adapt strategies and plans
|
- Conduct a thorough post-incident analysis
- Identify areas for improvement in the IRP to enhance resilience against future external threats
|
User Behavior Analytics
Adapting to the dynamic nature of users and triggered transactions, user behavior analytics (UBA) analyzes user activities and interactions to establish a baseline of normal behavior. Anomalies from this baseline signify potential threats, even if they originate from a seemingly legitimate user account.
UBA's capabilities also extend beyond merely identifying insider threats and are known to help uncover external attacks that leverage compromised user accounts or exploit vulnerabilities in user behavior.
- Holistic understanding of user behavior – Traditional security measures often miss sophisticated threats as they focus on predefined rules and signatures, potentially overlooking sophisticated threats that mimic legitimate user activity. UBA provides a nuanced understanding of user behavior by continuously monitoring and learning from user interactions within the network. This enables the detection of subtle behavioral patterns that could signal an external attacker operating under the guise of a legitimate user.
- Detection of insider threats – Whether malicious or accidental, insider threats pose significant risks. UBA's focus on behavior allows it to detect suspicious activities, even from authenticated users or accounts posed by external actors, making it a powerful tool against threats.
- Adaptive and proactive security – UBA adapts to the ever-changing threat landscape by dynamically learning from user behavior and updating its baseline understanding. This proactive approach keeps defenses aligned with emerging threats, making an organization more resilient.
- Enhanced incident response – Regardless of an attack's origin, the real-time monitoring and intelligent alerting offered by UBA enable faster detection and response to suspicious activities. Prompt action can mitigate potential damage and reduce the overall risk.
- Integration and synergy – UBA's strength lies in its ability to integrate smoothly with existing security systems, such as SIEM and EDR, within an enterprise. This synergy amplifies the overall protective measures, creating an enriched layer of defense.