Deconstructing the Azure Point-to-Site VPN for Command Line usage
Join the DZone community and get the full member experience.
Join For Freewhen configuring an azure virtual network one of the most common things you'll want to do is setup a point-to-site vpn so that you can actually get to your servers to manage and maintain them. azure point-to-site vpns use client certificates to secure connections which can be quite complicated to configure so microsoft has gone the extra mile to make it easy for you to configure and get setup – sadly at the cost of losing the ability to connect through the command line or through powershell – let's change that.
current state of play == no command line vpn connections
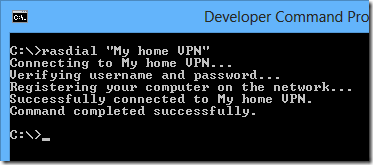
normally when you want to launch a vpn from the cli or powershell in windows you can simply use the following command:
rasdial "my home vpn"
the azure pre-packaged vpn doesn't allow this because it's really just not a normal vpn. it's something else , something mysterious - not a normal native windows vpn connection.
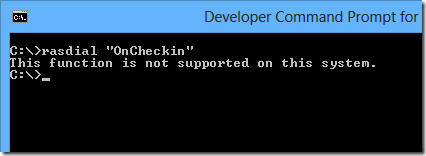
when you run the azure vpn through the command line you get this (you'll see a hint as to why i'd be using azure point-to-site in this screenshot):
azure vpns don't appear to support this.
if you want to keep your servers behind a private network in azure and use continuous deployment to get your code into production this makes it hard to deploy without a human being around. not really the best case scenario – especially when you remind yourself that automated builds aim to do away with human error altogether.
what the azure point-to-site looks like out of the box
when you first go to setup a point-to-site vpn into your azure virtual network microsoft points you at a page that walks you through creating a client certificate on your local machine to use as authentication.
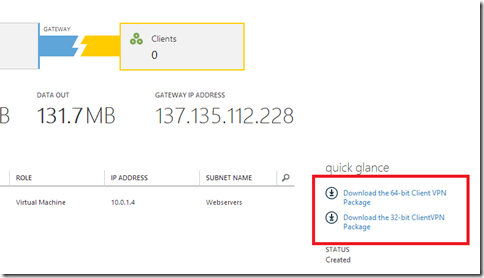
they then get you to download a package for setting up the azure vpn ras dialler on your local machine.
this is accessed from within the azure "networks" page for your virtual network.
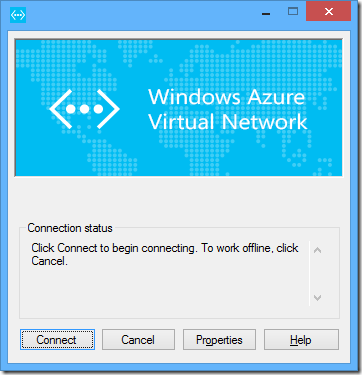
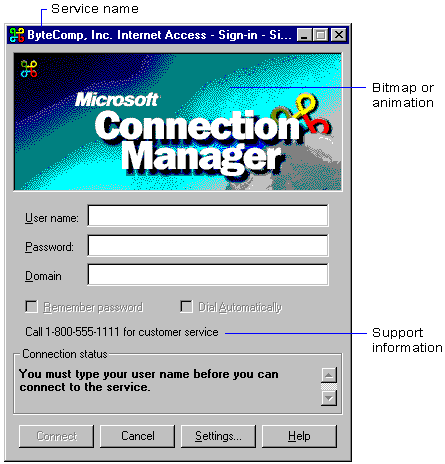
you install this package and then whenever connecting you're greeted with a connection screen that you might of seen in a previous life. and by seen i don't mean that windows azure virtual networks have been around for ages. but more that the login screen may look familiar.
this is because this login screen is a microsoft " connection manager " login screen and has been around for a while.
example from technet (note extremely dated bitmap awesomeness):
connection manager is used to pre-package vpn and dial up connections for easy-install distribution in a large organisation. this also means we can reconstruct the underlying vpn connection and use it as a normal vpn – claiming back our cli super powers.
digging through the details
so what we really want to know is:
what is this mystical vpn technology the people at microsoft have bestowed upon us?
here's how i started getting more information about the implementation:
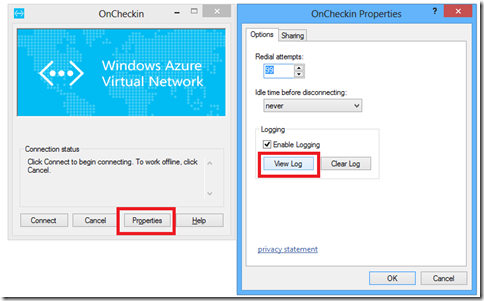
- connecting once successfully then disconnect.
- open it up again to connect and click on properties
- then clicking on view log
you'll then be greeted by something that looks like this:
****************************************************************** operating system : windows nt 6.2 dialler version : 7.2.9200.16384 connection name : my azure virtual network all users/single user : single user start date/time : 24/11/2013, 7:50:31 ****************************************************************** module name, time, log id, log item name, other info for connection type, 0=dial-up, 1=vpn, 2=vpn over dial-up ****************************************************************** [cmdial32] 7:50:31 03 pre-init event callingprocess = c:\windows\system32\cmmon32.exe [cmdial32] 7:50:39 04 pre-connect event connectiontype = 1 [cmdial32] 7:50:39 06 pre-tunnel event username = myclientsslcertificate domain = dunsetting = [obfuscated azure gateway id] tunnel devicename = tunneladdress = [obfuscated azure gateway id].cloudapp.net [cmdial32] 7:50:44 07 connect event [cmdial32] 7:50:44 08 custom action dll actiontype = connect actions description = to update your routing table actionpath = c:\users\doug\appdata\roaming\microsoft\network\connections\cm\[obfuscated azure gateway id]\cmroute.dll returnvalue = 0x0 [cmmon32] 7:56:21 23 external disconnect [cmdial32] 7:56:21 13 disconnect event callingprocess = c:\windows\explorer.exe
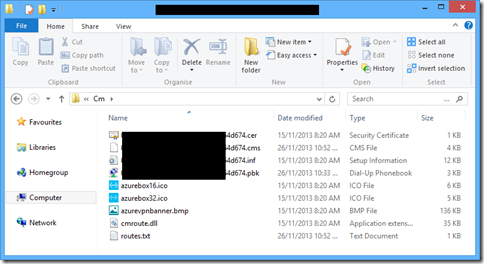
more importantly you'll see this path included in the connection:
within this folder is all the magic connection manager odds and ends. apologies for the [obfuscated], simply the path contains information to my azure endpoint.
within this folder you'll see a bunch of files:
most importantly there is a pbk file – a personal phonebook. this is what stores the connect settings for the vpn as is a commonly distributed way of sending out connection settings in the enterprise. if you run this on its own you'll actually be able to connect to the vpn directly (without your network routes being updated).
this phonebook is where we can steal our settings from to recreate a command line driven connection.
setting it up
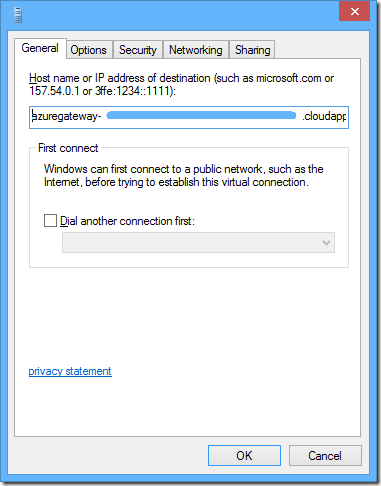
open up the properties of your azure point-to-site vpn phonebook above, and copy the connection address.
it will look like this:
azuregateway-[guid].cloudapp.net
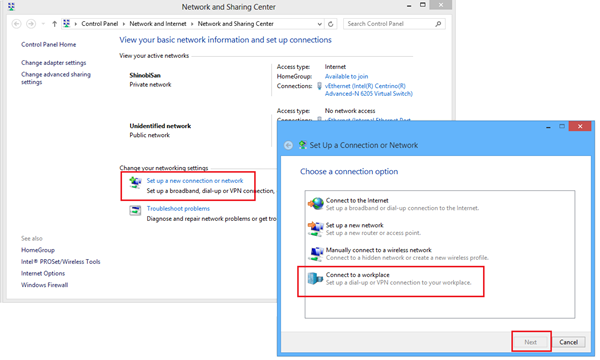
open network sharing centre , and create a new connection. then select connect to a workplace .
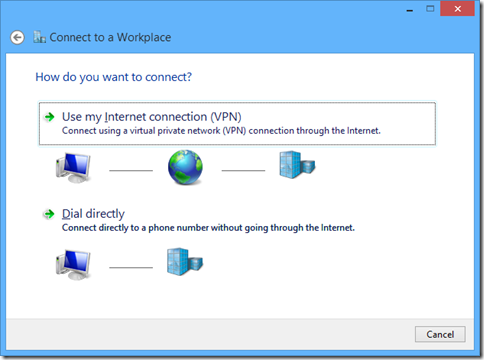
select that you'll "use my internet connection".
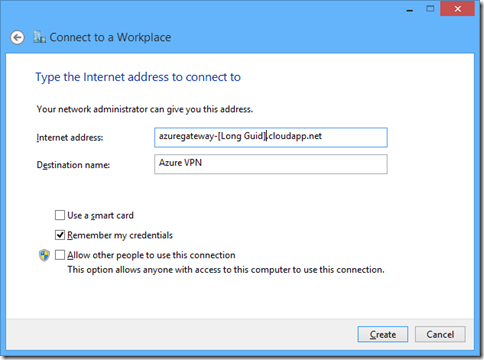
then enter your azure point-to-site vpn address and then give your new connection a name. remember this name for later
then click create to save your vpn.
now open the connection properties for your newly created vpn. this is where we'll use the settings in your azure diallers config to setup your connection.
i'll save you the hassle of showing you me copying the settings from one connection to another and instead i'll just focus on what you need to set them to.
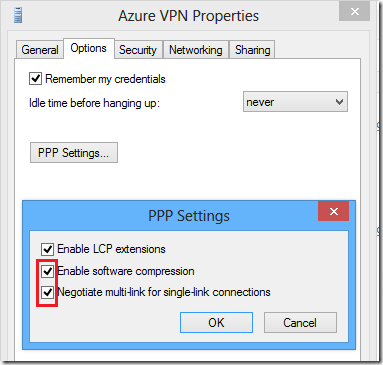
flick over to the options tab and then click ppp settings . click the 2 missing options enable software compression and negotiate multi-link for single-link connections .
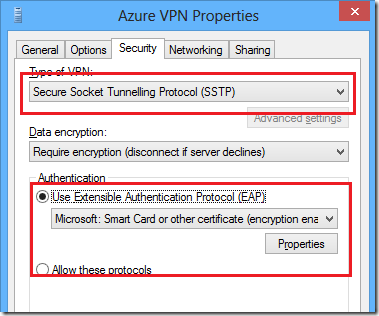
set the type of vpn to secure socket tunnelling protocol (sstp), turn on eap and select microsoft: smart card of other certificate as the authentication type.
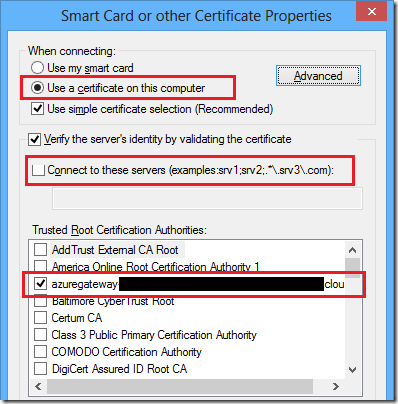
then click on properties .
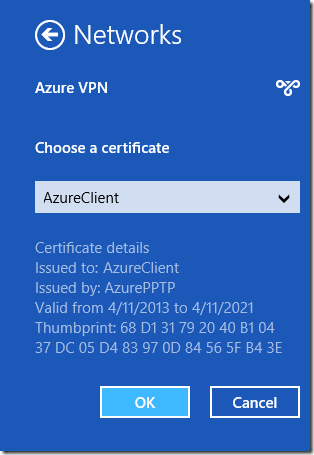
select "use a certificate on this computer", un-tick "connect to these servers", and then select the certificate that uses your azure endpoint uri as its certificate name and then save out.
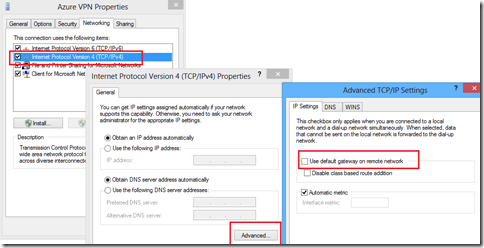
then flick over to the network tab. open tcp/ipv4 then advanced then untick use default gateway on remote network . this setting stops internet traffic going over the vpn while you're connected so you can still surf reddit while managing your azure environment.
close the vpn configuration panel.
you now have a working vpn connection to azure.
when you connect using windows you'll be asked to select the name of the client certificate you'll be authenticating with. you select the certificate you created and uploaded into azure before you setup your connection.
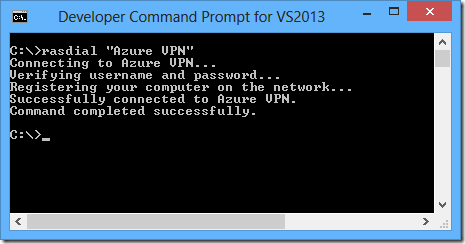
when you connect using the command line you don't need to specify your certificate:
rasdial "azure vpn"
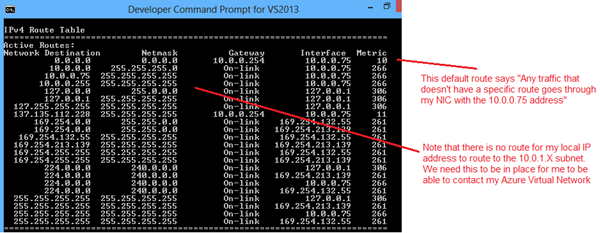
but there's one catch: your local machine's route table doesn't know when to send any traffic to your azure virtual network. the network link is there, but windows doesn't know what to send over your internet link and what to send over the vpn link.
you see microsoft did a few things when they packaged your connection manager, and one of these things was to also copy a file called "cmroute.dll" and call this after connection to route your traffic onto your virtual network. this file altered your routing table to route traffic to your virtual network subnets through the vpn connection .
we can do the same thing – so lets go about it.
what's this about routing... rooting (for the english speakers in the room)
my azure virtual network consists of the following network range:
10.0.0.0/8
i also have the following subnets for different machines groups.
10.0.1.0/24 (web servers)
10.0.2.0/24 (application servers)
10.0.3.0/24 (management services)
my pptp connections, or point-to-site connections sit on the range: 172.16.0/24
this means that when i connect to the azure vpn i will get an ip address in this range. example: 172.16.0.17
when this happens we need to tell windows to route all traffic going to my 10.0.x.x range ip addresses through the ip address that has been given to us by azure's vpn rras service.
you can see your current routing table by entering route print into a command prompt or powershell console.
automating the routing additions
luckily the windows task scheduler supports event listeners that allow us to watch for vpn connections and run commands off the back of them.
take the below powershell script below and save it for arguments sake in c:\scripts\updateroutetableforazurevpn.ps1
#############################################################
# adds ip routes to azure vpn through the point-to-site vpn
#############################################################
# define your azure subnets
$ips = @("10.0.1.0", "10.0.2.0","10.0.3.0")
# point-to-site ip address range
# should be the first 4 octets of the ip address '172.16.0.14' == '172.16.0.
$azurepptprange = "172.16.0."
# find the current new dhcp assigned ip address from azure
$azureipaddress = ipconfig | findstr $azurepptprange
# if azure hasn't given us one yet, exit and let u know
if (!$azureipaddress){
"you do not currently have an ip address in your azure subnet."
exit 1
}
$azureipaddress = $azureipaddress.split(": ")
$azureipaddress = $azureipaddress[$azureipaddress.length-1]
$azureipaddress = $azureipaddress.trim()
# delete any previous configured routes for these ip ranges
foreach($ip in $ips) {
$routeexists = route print | findstr $ip
if($routeexists) {
"deleting route to azure: " + $ip
route delete $ip
}
}
# add our new routes to azure virtual network
foreach($subnet in $ips) {
"adding route to azure: " + $subnet
echo "route add $ip mask 255.255.255.0 $azureipaddress"
route add $subnet mask 255.255.255.0 $azureipaddress
}
now execute the following from an elevated command prompt window. this tells windows to add an event listener based task that looks for events to our "azure vpn" connection and if it sees them, it runs our powershell script.
schtasks /create /f /tn "vpn connection update" /tr "powershell.exe -noninteractive -command c:\scripts\updateroutetableforazurevpn.ps1" /sc onevent /ec application /mo "*[system[(level=4 or level=0) and (eventid=20225)]] and *[eventdata[data='azure vpn']] "
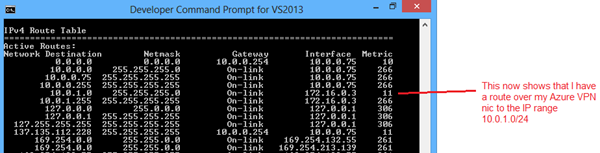
if i then connect to my vpn the above script should execute.
after connecting if i check my routing table by entering route print into a console application we have our routes to azure added correctly.
we're done!
with that we're now able to fully use an azure point-to-site vpn simply from the command line. this means we can use it as part of a build server deployment, or if you're working on it all the time you can simply set it up to connect every time you login to windows .
command line usage
rasdial "[connection name]" rasdial "[connection name]" /disconnect
for my connection named "azure vpn" this command line usage becomes:
rasdial "azure vpn" rasdial "azure vpn" /disconnect
Published at DZone with permission of Douglas Rathbone, DZone MVB. See the original article here.
Opinions expressed by DZone contributors are their own.

Comments