DevOps vs. DevSecOps: The Debate
In this blog, we aim to provide insights on DevOps and DevSecOps, empowering you to make informed choices.
Join the DZone community and get the full member experience.
Join For FreeThe DevOps vs. DevSecOps debate has recently been gaining more and more momentum in IT circles. However, these two concepts aren’t competitors; rather, they comprehend each other. It’s important to understand the difference between DevOps and DevSecOps to choose the right model for your software development environments. This blog addresses DevOps and DevSecOps in hopes of helping you make an informed decision.
What Is DevOps?
DevOps is a methodology that integrates development and operations teams to seamlessly coordinate and develop software applications so that each member shares the responsibility of a product throughout its lifecycle. It brings people, processes, and tools together to work as a single entity to automate release cycles, quickly respond to customer needs and deliver quality software faster and more efficiently.
What Is DevSecOps?
DevSecOps basically takes the DevOps model and wraps a security layer around it. Simply put, DevSecOps introduces security professionals early in the software development cycle and in the continuous integrity (CI) and continuous delivery (CD) processes such that security is also a shared responsibility of every member throughout the product life cycle, thereby allowing DevOps teams to deliver secure applications faster. When developers write code with security in mind from day one, it is easier to fix bugs and secure the application while breaking silos between different teams. At the end of the day, it’s not about DevOps vs. DevSecOps but rather about how both approaches can complement each other.
DevSecOps is one of the DevOps Trends that will transform businesses now and beyond.
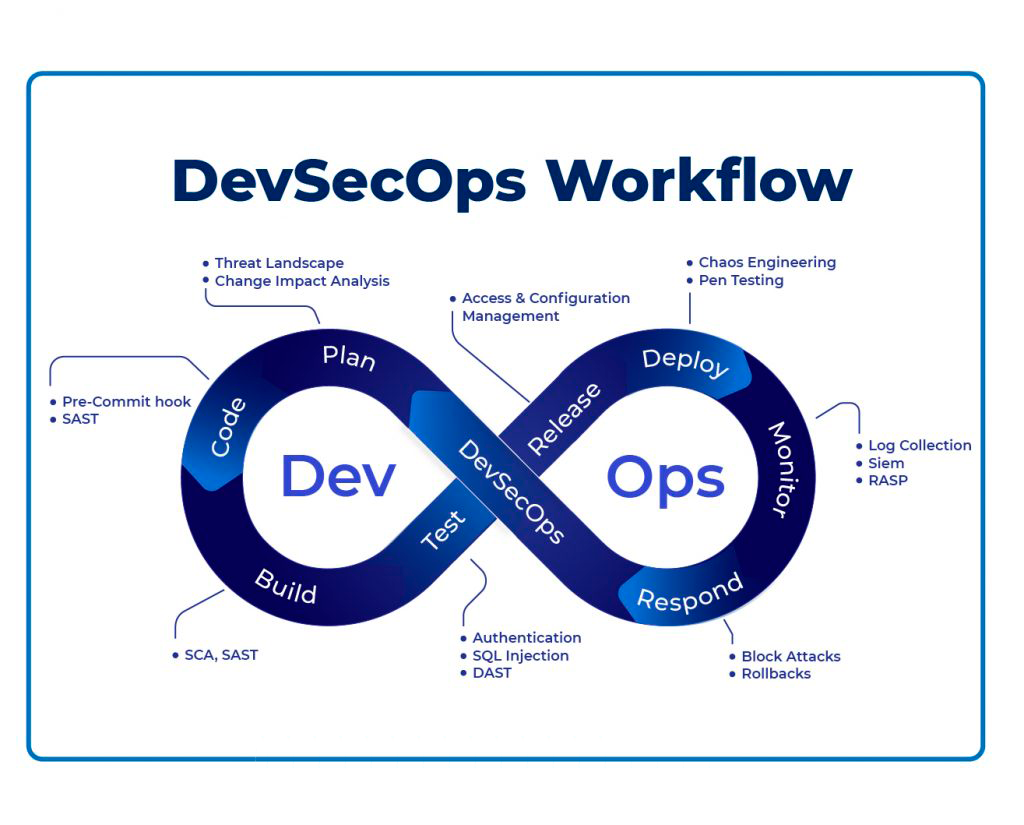
DevOps vs. DevSecOps Diagram
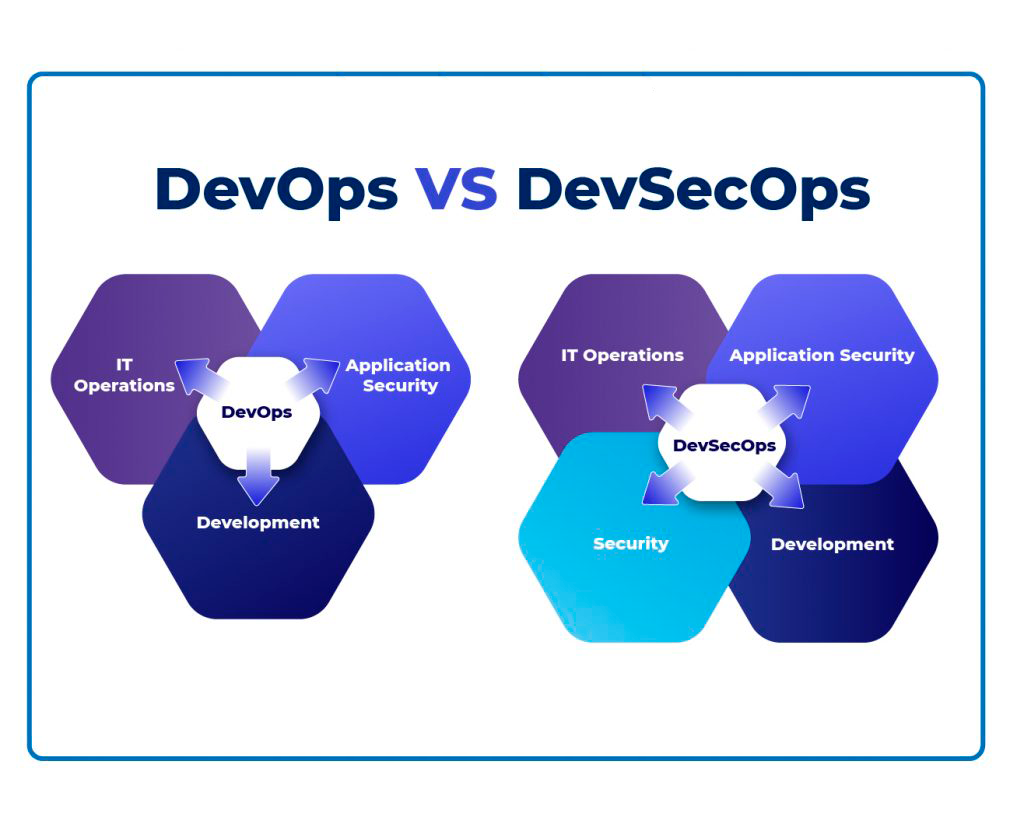
Shift Left Security
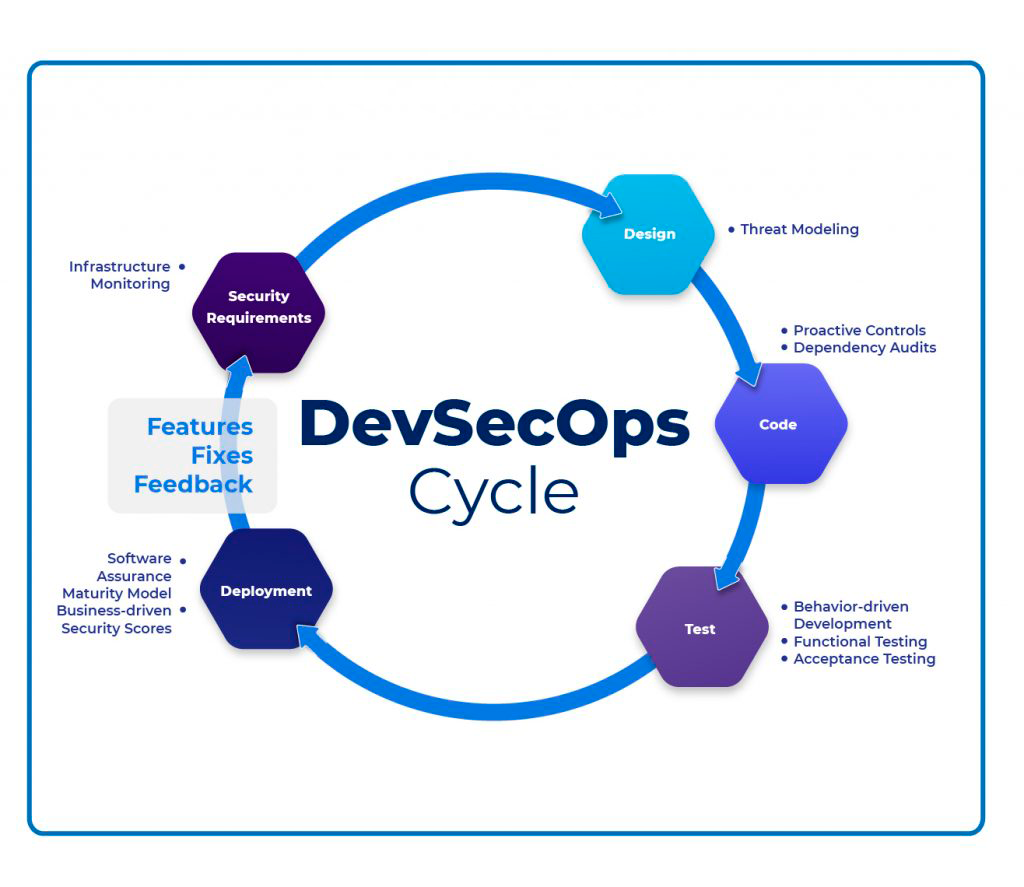
Shift left security is the key aspect of every DevOps vs. DevSecOps or DevSecOps vs. DevOps conversation. Shift left security focuses on where security best practices should be implemented in a CI/CD pipeline and when and how to apply them. As the name suggests, this approach involves moving security measures such as testing, quality, and performance evaluation to the left/beginning phase of the software development pipeline. This means incorporating security checks early and frequently in the software development lifecycle instead of implementing them during the last phase of the application development.
DevSecOps reduces significant bottlenecks concerning security issues as developers can identify and fix bugs early on to improve software quality and streamline the entire SDLC process. While security teams understand how automation culture works and at what speed, developers are equipped with security automation tools and best practices, resulting in a secure end product. Security, governance, and control are incorporated into the development cycle while maintaining the same deployment speed so that security becomes business enablement instead of restriction.
Static Application Security Testing (SAST), Dynamic Application Security Testing (DAST), dependency scans, compliance scans, and container scans are key tools for incorporating shift left security.
DevOps vs. DevSecOps: What Is the Difference?
Regarding DevOps vs. DecSecOps, both approaches may look very similar at first glance. However, there are critical differences that require your attention. DevOps is about integrating development and operations teams throughout the product development life cycle and sharing standard tools and KPI metrics. The focus of a DevOps engineer is to efficiently implement changes to the app without affecting the user experience. DevSecOps is an extension of DevOps, which arose when development teams understood that security was not prioritized and concerns were not appropriately addressed in the current model. As such, security was introduced right from the CI/CD cycle’s build phase so that DevOps engineers can now deploy products with security and user experience in mind. It’s not about DevSecOps vs. DevOps but about adapting the DevOps model from a security perspective.
Security Automation
Security automation is another key aspect of the DevOps vs. DevSecOps discussion. Security automation involves automating systems to investigate, detect and remediate cyber threats without human intervention. From detecting cyber threats and triaging them to determining the appropriate remediation plan and executing mitigation tasks, security automation enables organizations to improve overall security efficiency with reduced overhead.
Security automation identifies threats faster, eliminates manual and error-prone sorting, filtering, and visualizing tasks, and saves you time on repetitive tasks, all while enabling you to easily analyze and share data using intuitive dashboards and reporting tools. With reduced MTTD and MTTR metrics and increased ROI, organizations can enjoy future-proof security across the infrastructure.
Infrastructure as Code (IaC) Security
IaC security is important when considering the DevSecOps vs. DevOps battle. Traditionally, cloud security tasks in an IaC environment were performed after the infrastructure was provisioned. IaC security takes this approach to the next level by addressing the cloud configuration issues before resources are provided, thereby eliminating new issues that arise from manual configurations. By scanning templates, modules, files, and corresponding variables of the cloud, app, and infrastructure against hundreds of policies and known vulnerabilities, IaC security identifies security issues and misconfigurations. Monitoring the security of the deployed resources is then transferred to the IaC layer. Security automation allows organizations to quickly enjoy complete coverage across compliance controls and best practices.
Bridgecrew’s Checkov and Open Policy Agent are two open-source tools that help you scan IaC files against known policies.
CI/CD Security
Securing the CI/CD pipeline at every stage across every tool and environment involved is critical, as all DevOps processes are built on this foundation. CI/CD security addresses this issue by mitigating security risks across all phases of the pipeline. Insecure code (mainly imported by third-party sources), unauthorized access to code repositories, insecure secrets management, and dev/test environment breaches are some of the critical CI/CD security threats which need to be addressed.
Securing a CI/CD pipeline requires a multi-prong approach, as different tools and frameworks are required to address issues in different software stack layers. For instance, Static Software Application Testing (SAST) and Source Composition Analysis (SCA) work in the build phase, scanning the code for vulnerabilities and misconfiguration. Amazon KMS and Hashicorp Vault help manage access controls and secrets management. Understanding the difference between DevOps and DevSecOps is the key to implementing the right tools and processes.
Threat Hunting and Security Incident Response
Automating threat hunting results in faster threat detection and remediation without human intervention, saving the company from overall breach costs. Similarly, remediation across the entire ecosystem comprising multiple apps, platforms, and frameworks is time-consuming and expensive. Automating security incident response helps you quickly and concurrently respond to incidents.
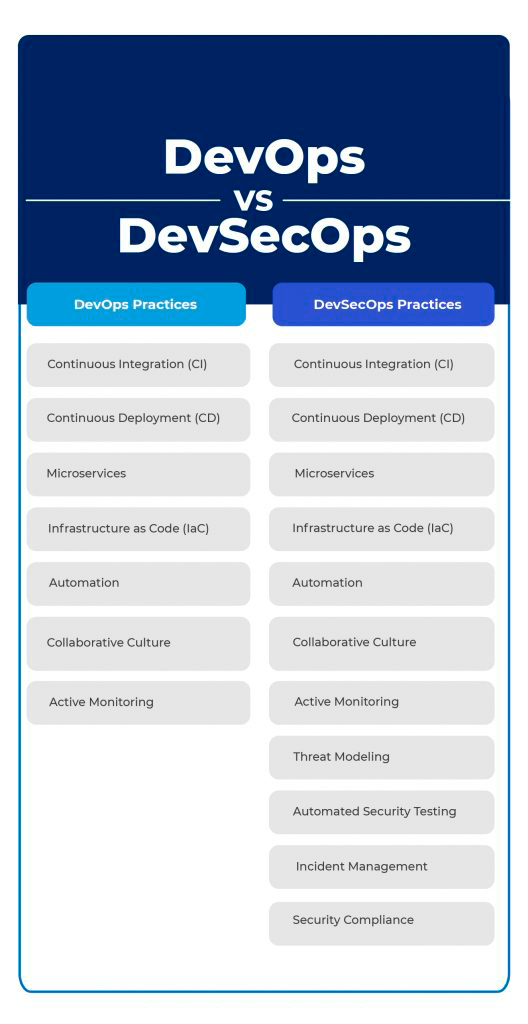
DevSecOps Tools
Integrating security closely into a CI/CD pipeline and automating processes makes application security testing tools highly important in a DevOps vs. DevSecOps environment. While these tools identify bugs in the early stages and reduce risks in CI/CD workflows, they also assist security teams in automating the monitoring and management tasks and improving the overall security of the infrastructure.
Here is a list of the most important application security testing tools:
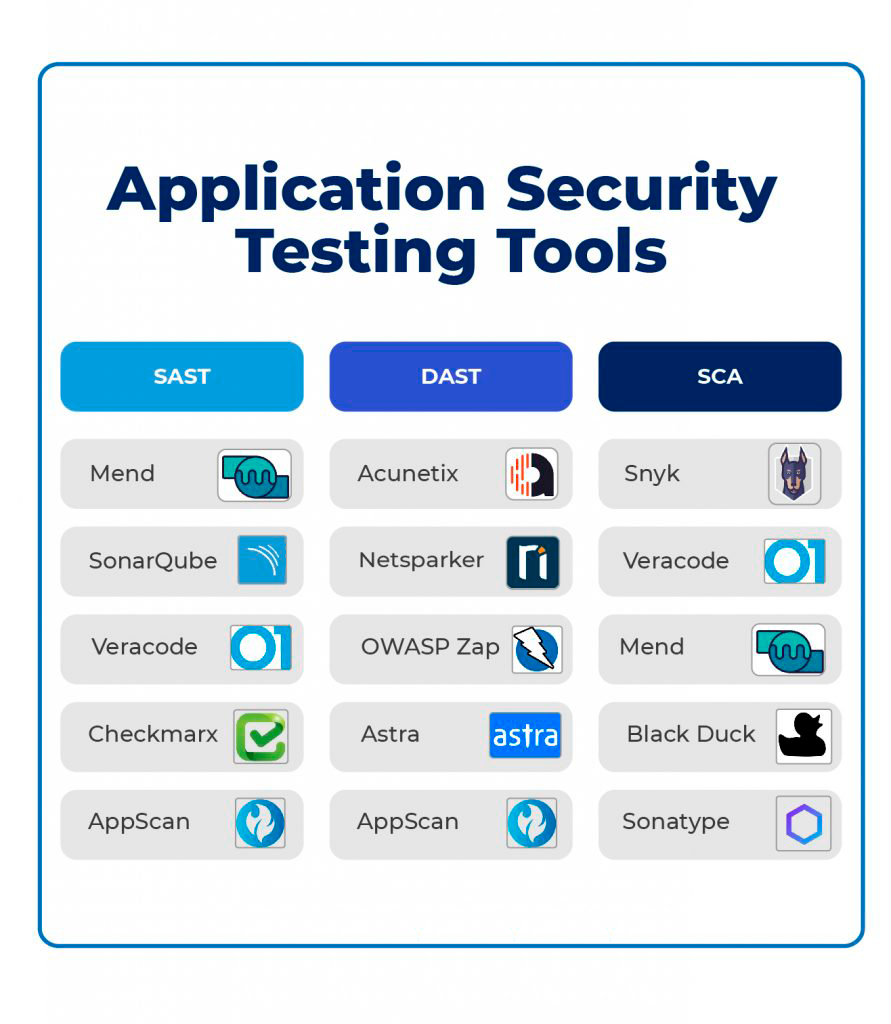
1. Static Application Security Testing (SAST)
SAST is a white box testing method. SAST tools scan the app code, such as byte code, source code, and binary code, for vulnerabilities and potential security issues and assign a level of security weakness to prioritize remediation. As the name implies, SAST tools scan static or non-running files to identify issues such as SQL injection, cross-site scripting, and buffer overflowing scenarios. Following the shift-left security principle, SAST tools work in the build phase of the CI/CD pipeline, securing apps early in the SDLC. The most significant limitation of these tools is that they only analyze code at rest and cannot scan code in staging or production environments.
SAST is generally used for proprietary code. Mend, SonarQube, Veracode, Checkmarx, and AppScan are a few notable examples of SAST tools.
2. Dynamic Application Security Testing (DAST)
DAST falls into the black box testing category. As the name implies, DAST tools are used to check running applications. A DAST tool provides malicious inputs to a running app. It checks for vulnerabilities such as cross-site scripting, SQL injections, OS injections, cookie safety, security headers, and content security policies. DAST is language-agnostic as they work with running applications.
For the same reason, they also don’t need access to source code. Furthermore, they test the HTML and HTTP interfaces of web apps. DAST tools automatically perform security scans in test and production environments and can easily integrate with the CI/CD pipeline.
Acunetix, Netsparker, OWASP Zap, Astra Pentest, and AppScan are a few notable DAST tools available on the market.
3. Security Composition Analysis (SCA)
Security composition analysis is a security testing approach that scans and identifies security vulnerabilities, problematic OSS licenses, and more in open-source software application code. SCA tools also provide a severity score, remediation guidance, and a detailed report to help users easily mitigate risks. With the help of provenance and code quality checks, SCA helps you identify and update poorly maintained software. While SAST deals with proprietary code, SCA is used for open-source code.
Snyk, Veracode, Mend, Black Duck, and Sonatype Nexus Platform are a few notable examples of SCA tools.
DevSecOps Tools and Workflow
OWASP Top Ten Methodology
OWASP stands for open web application security project. Basically, it’s a non-profit foundation that operates under an open community model to improve software security. It also offers free security information to users. As such, anyone can join the community and contribute to OWASP-related projects.
OWASP Top 10 is a program that offers the top 10 security vulnerabilities along with remediation guidance based on the consensus among community contributors who are also security experts and possess vast knowledge and experience in this field. Based on the frequency of the security threats and the severity and magnitude of the impact, the Top 10 program ranks vulnerabilities. Since 2003, the Top 10 program has been updating the list every 2-3 years, considering the changing trends in the AppSec market. Auditing agencies consider implementing the Top 10 in the CI/CD or SDLC as adhering to security compliance and best practices.
These are the top 10 risks and practices that every DevOps engineer and developer should take into account when considering DevOps vs. DevSecOps:

OWASP With DevSecOps
OWASP DevSecOps Guidelines help organizations of all sizes create a secure CI/CD pipeline by implementing the Top 10 security measures with a shift-left security approach.
Below are the steps to implementing OWASP DevSecOps Guidelines in a basic CI/CD pipeline following the Top 10 security controls.
- Git Repo Scanning
- Static Application Security Testing (SAST)
- Software Composition Analysis (SCA)
- Interactive Application Security Testing (IAST)
- Dynamic Application Security Testing (DAST)
- Infrastructure as Code (IaC) Scanning
- Infrastructure Scanning
- Compliance Check
These steps can be customized to fit organizational requirements. By implementing the Top 10 security controls, organizations can reduce operational failures and errors in systems while armoring apps against cyber-attacks. In addition to delivering stronger encryption and more secure end products, organizations can increase their authenticity and brand image as security-compliant companies.
DevOps vs. DevSecOps: Where To Go From Here?
The DevOps vs. DevSecOps discussion doesn’t end here. There are other areas that merit pondering:
Vulnerability Assessment
Vulnerability assessment is about reviewing a system’s potential vulnerabilities and risks to determine the system’s exposure to threats and severity levels, all while offering remediation guidance. From phishing and password weaknesses to SQL injections and faulty authentication mechanisms, vulnerability assessments evaluate apps and systems across a wide range of threat attacks.

Different types of vulnerability assessments:
- Build Assessment: Analyzing the builds of software applications for security and performance issues.
- Database Assessment: Analyzing the vulnerabilities of database systems.
- Web App Assessment: Analyzing the front-end side of the application using methods such as DAST, SAST, and SCA.
- Mobile Application Assessment: Analyzing mobile apps for security threats.
- Wireless Assessment: Analyzing all wireless access points and their distribution across the infrastructure to identify architectural, environmental, and configuration variables which negatively impact the security of the wireless installation.
- Configuration Assessment: Analyzing the configuration of the network and systems across the infrastructure
Penetration Testing
Penetration testing is a security approach that simulates a cyber-attack against a system or network to identify vulnerabilities and evaluate the security strength of the system. Also known as Pen Testing, this approach evaluates front-end services, back-end services, and APIs of applications and systems. Based on the reports, security administrators can patch known vulnerabilities and strengthen their web application firewall (WAF) policies and protocols.
Different Phases of Pen Testing
- Defining the goals and scope of the test and gathering intelligence from various systems.
- Scanning the systems using static and dynamic analysis.
- Gaining access to the system.
- Maintaining access to the system.
- Compiling the results into a detailed report.
Different Types of Penetration Testing Methods
- Internal Pen Testing: Hacker attacks the system from the internal network.
- External Pen Testing: Hacker attacks the network from outside the company.
- Open-box Pen Testing: Hacker is provided with information about network systems.
- Black-box Pen Testing: Hacker doesn’t have any information about the network system.
- Covert Pen Testing: Security professionals are not aware of this attack.
Security Compliance
Security compliance is about monitoring, evaluating, and assessing the security of the network and systems to ensure compliance with regulatory policies and industry security standards. Failing to do so may result in costly data breaches, which imply lawsuits, penalties, and fines.
Here are a few critical compliance requirements for organizations regardless of the implementation of DevOps and DevSecOps:
- PCI Compliance: PCI compliance pertains to the payment card industry. Organizations that process or store payment card information should adhere to operational and technical standards to safeguard the critical data of payment card holders following a set of security guidelines developed by the PCI Security Standards Council (PCI SSC).
- HIPAA Compliance: HIPAA compliance pertains to the healthcare industry. Organizations involved in healthcare should adhere to the Federal Health Insurance Portability and Accountability Act of 1996 to safeguard sensitive data related to patient health.
- HITRUST Compliance: HITRUST refers to the Health Information Trust Alliance, founded in 2007. It is a certifiable security framework that provides a set of guidelines/controls to demonstrate HIPAA compliance in an organization. It’s important to note that HITRUST and HIPAA are not the same. While HIPAA is a law, HITRUST is a framework based on HIPAA legislation requirements.
- SOC2 Compliance: SOC2 is an auditing procedure that defines criteria for securely managing customer data based on five trust principles, namely Security, Privacy, Confidentiality, Availability, and Process Integrity. It is developed by the American Institute of CPAs.

Conclusion
DevOps and DevSecOps look similar in terms of automation, active monitoring, and collaborative culture but come with critical differences. When it comes to DevOps vs. DevSecOps, DevOps teams focus on deployment frequency and performance of applications, while DevSecOps teams are concerned with application security throughout the product life cycle. Organizations that understand the differences between these two approaches can make the right changes to their processes to optimize speed, agility, and security while increasing the overall efficiency of the delivery pipeline.
Published at DZone with permission of William Talluri. See the original article here.
Opinions expressed by DZone contributors are their own.

Comments