A Hands-On Guide to Enable Amazon GuardDuty on AWS Account
This hands-on guide will help you enable Amazon GuardDuty via the AWS Console in order to monitor and detect security threats in your AWS environment.
Join the DZone community and get the full member experience.
Join For FreeIn today’s digital era, cybersecurity is a cornerstone of maintaining trust and reliability in cloud operations. A managed threat detection service by AWS, like Amazon GuardDuty, can help secure your environment by analyzing activity and identifying potential risks. This hands-on guide will help you enable Amazon GuardDuty on your AWS account and begin monitoring your resources for security threats.
Amazon GuardDuty is a threat detection service that uses machine learning, anomaly detection, and integrated threat intelligence to protect your AWS environment. It continuously monitors for malicious activity, unauthorized access, and security vulnerabilities by analyzing data sources like AWS CloudTrail logs, VPC Flow Logs, and DNS logs.
Benefits of GuardDuty
- Automated threat detection: GuardDuty identifies suspicious behavior in real time, such as unusual API calls, unauthorized access attempts, and data exfiltration activities.
- Ease of use: There’s no need to deploy or manage additional security infrastructure — GuardDuty is fully managed by AWS.
- Cost-effective: You only pay for what you use, making it an affordable solution for proactive threat detection.
- Seamless integration: GuardDuty integrates with other AWS security tools such as AWS Security Hub, Amazon CloudWatch, and Amazon SNS for notifications.
How to Enable Amazon GuardDuty
Follow these steps to enable GuardDuty on your AWS account:
Step 1: Prepare Your AWS Account
Before you begin, ensure that:
- You have an active AWS account.
- Your IAM user or role has the necessary permissions. Assign the AmazonGuardDutyFullAccess policy to the user or role to enable and manage GuardDuty.
Step 2: Access GuardDuty in the AWS Console
- Sign in to the AWS Management Console.
- Navigate to the GuardDuty service under the Security, Identity, and Compliance section.
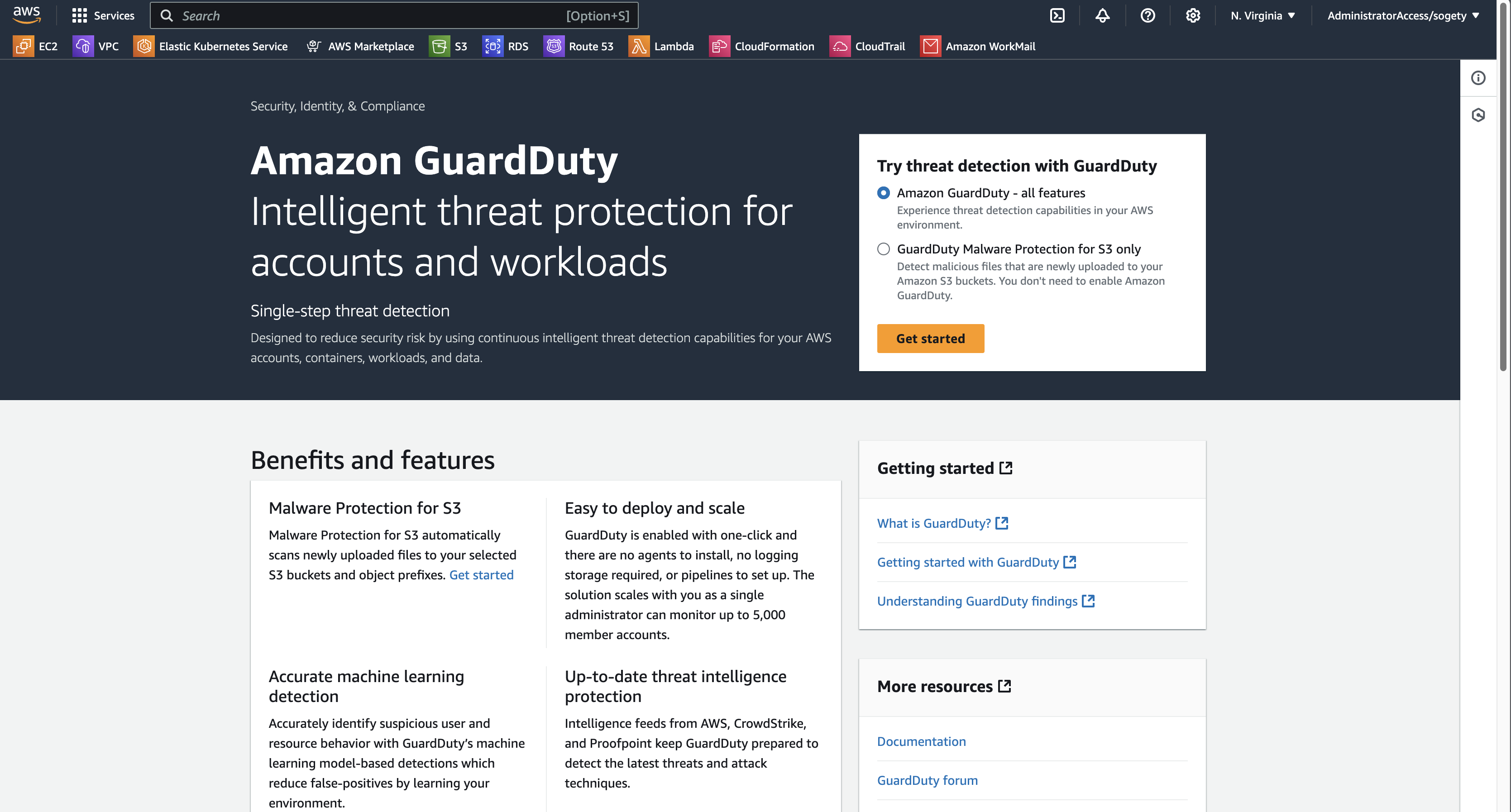
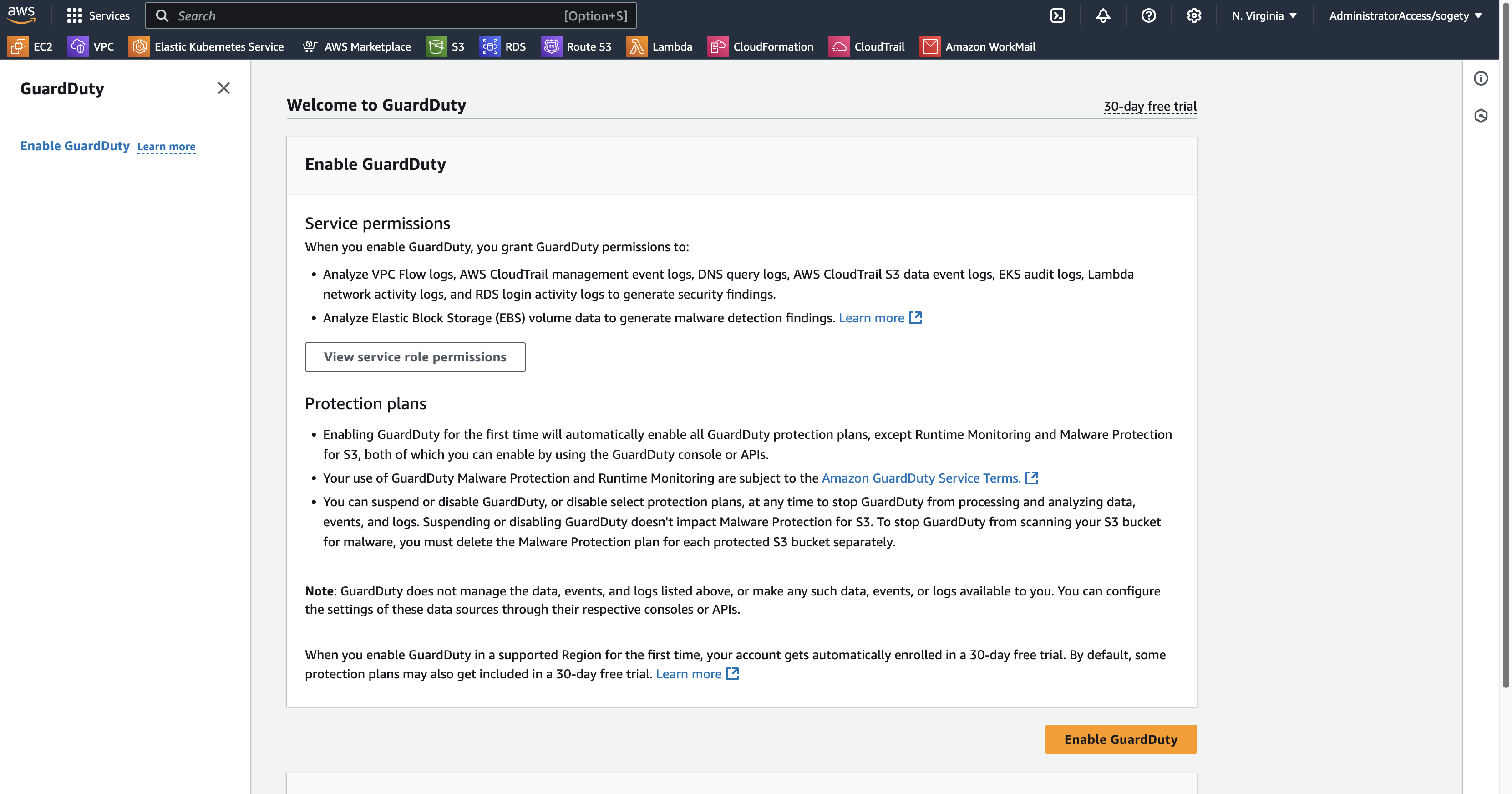
Step 3: Enable the Service
- On the GuardDuty dashboard, click Get Started or Enable GuardDuty.
- Review the terms of use and configurations.
- Confirm the setup by clicking Enable.
Once GuardDuty is activated, it will begin analyzing data from various sources like CloudTrail logs, VPC Flow Logs, and DNS queries to detect anomalies.
Note: You can choose one of the options below to enable Guard Duty:
- Try threat detection with GuardDuty
- GuardDuty Malware Protection for S3 only
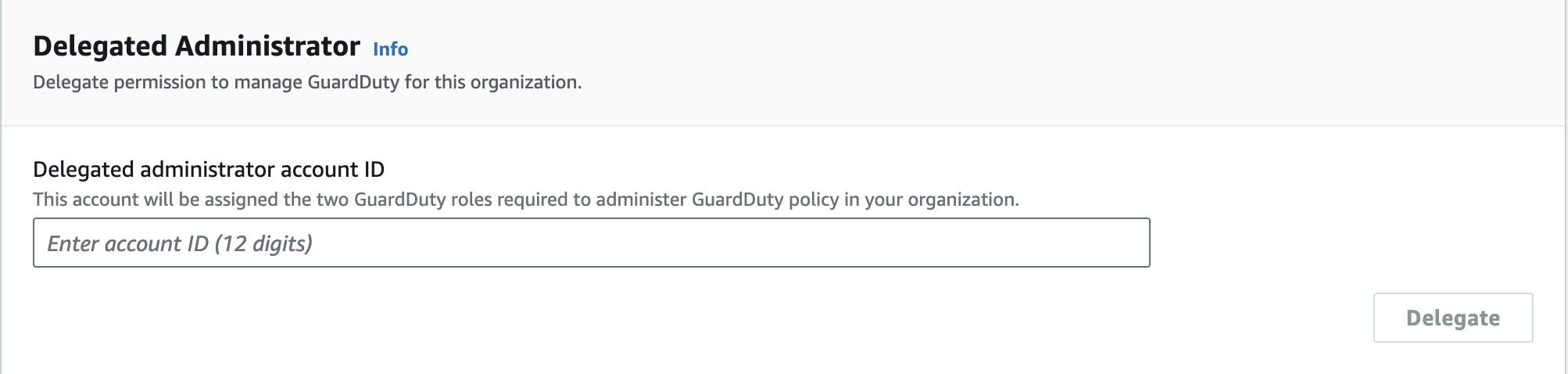
Step 4: Configure Multi-Account Support (Optional)
If you manage multiple AWS accounts, consider enabling multi-account support. Use AWS Organizations to designate a GuardDuty administrator account that can manage the service across all linked accounts.
Step 5: Monitor and Respond to Findings
After enabling GuardDuty, its findings will populate the dashboard. GuardDuty classifies findings by severity — low, medium, or high — allowing you to prioritize actions. Integrate GuardDuty with:
- AWS Security Hub: For centralized security management.
- Amazon CloudWatch: To set up alarms and trigger workflows.
- Amazon SNS: For email or SMS notifications about threats.
Best Practices for Using GuardDuty
- Enable logging: Ensure that CloudTrail logs and VPC Flow Logs are active for comprehensive monitoring.
- Integrate with automation: Use AWS Lambda to automate responses to high-severity findings.
- Review regularly: Periodically review findings and update security policies based on GuardDuty insights.
Conclusion
Amazon GuardDuty is a helpful tool for improving the security of your AWS environment. Enabling this service will help you stay proactive in detecting and responding to potential threats. Its ease of use and robust threat detection capabilities make it a valuable option for organizations using AWS.
Author's Note: Take the first step today by enabling GuardDuty on your AWS account to protect your cloud environment against modern security challenges.
Opinions expressed by DZone contributors are their own.

Comments