Introduction to AWS Config: Simplified Cloud Auditing
Modern cloud environments are ever-changing, and so is the nature of cloud computing. The growing cloud assets accompany the attack surface expansion problem for organizations, which unveils the need for visibility of cloud resources. AWS Config addresses that exact demand.
Join the DZone community and get the full member experience.
Join For FreeModern cloud environments are ever-changing, and so is the nature of cloud computing. The growing cloud assets accompany the attack surface expansion problem for organizations, which unveils the need for visibility of cloud resources. AWS Config addresses that exact demand. It can be challenging to understand resources within your infrastructure like:
- Seeing what resources you have
- Understanding your current configurations
- Knowledge of configuration changes and change histories
- Assessing if your resources are compliant with specific governances controls
- Having accurate and up-to-date audit information
Depending on the size of your AWS resources or deployment, overcoming these challenges and obtaining this information can become time-consuming and budget-intensive unless you use resource visibility and auditing tool like AWS Config.
This blog aims to get you started with AWS Config and understand its basic concepts, advantages, and disadvantages. Let's dive in with an introduction.
What is AWS Config?
AWS Config is an AWS service that allows you to audit, assess, and evaluate your AWS resource configurations. The service records and evaluates the configurations of your AWS resources against desired configurations, a set of rules, or conformance packs. It's an optimal service for cloud auditing and asset visibility.
In terms of visibility, Config also enables you to view configuration histories, which streamlines change management, operational troubleshooting, and security analysis.
Here's a breakdown of what Config offers for cloud auditing:
- Configuration history of AWS resources and software
- Customizable rules
- Conformance packs
- Tracking resource relationships
- Configuration snapshots
- Governance dashboard
- Integrations with other AWS services
Get started with Bite-Size Key Concepts
AWS Resources
AWS resources are entities that are created and managed within the AWS Management Console or using the AWS Command Line Interface (CLI), SDKs, or AWS partner tools. For example, Amazon EC2 instances, VPCs, and Elastic Block Store are resources. See the current list of supported resource types.
Configuration Items
A configuration item, or CI, is a point-in-time view of a supported resource. It comprises a JSON file holding the resource configuration information, relationship information, or related metadata as a point-in-time snapshot. So, Config forms a CI every time a resource configuration change takes place. Config records directly related resources to ensure they aren't affected by the changed configuration.
Configuration Stream
A configuration stream is a list of all your configuration items for the resources being recorded by Config. The list is automatically updated every time a resource is created, modified, or deleted. This configuration stream operates by using Amazon Simple Notification Service (SNS) topic. It helps to be aware whenever a change occurs.
Configuration History
As the name gives away, a configuration history is a collection of your configuration items for a given resource over a specific time period. It enables you to understand, for example, how the resource has been configured over a period when the resource was created or what configuration changes took place at a specific time.
Configuration Snapshots
A configuration snapshot refers to a complete, point-in-time picture of the resources that Config is recording and their configurations. Additionally, configuration snapshots can be sent to an S3 bucket.
Configuration Recorder
The AWS Config configuration recorder stores the configurations of supported resources as configuration items. You can start, restart, and stop the recorder at any time.
Resource Relationships
AWS Config enables you to discover AWS resources and map their relationships. For example, you can find out if an EBS volume is attached to an EC2 instance associated with a security group.
Managed and Custom Rules
Config offers a set of predefined rules and the ability to create custom ones. An AWS Config rule refers to your desired configuration settings for a specific resource or your entire AWS account. Once you activate a rule, Config compares resources against the conditions of a particular rule. This process can be triggered either when a change occurs or periodically based on the frequency of your choice (e.g., every 24 hours).
How Does AWS Config Work?
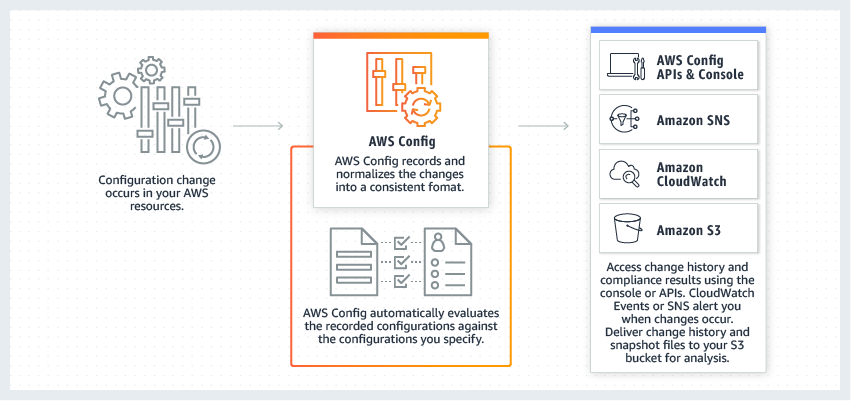
(source: AWS)
Once switched on, AWS Config starts discovering the supported AWS resources in your account and generates a configuration item for each resource. It also creates configuration items whenever a resource configuration changes. It records and holds the historical records of your resources from the time you start the recorder until you stop it.
AWS Config keeps track of configuration changes and examines them periodically or based on rule triggers. If you use AWS Config rules, it continuously evaluates your resources and compares them against desired settings. If a resource violates a rule you set up, Config flags it as non-compliant. Subsequently, when the compliance status changes, the service delivers a notification to your Amazon SNS topic.
Note: AWS Config's supported resource types cover many Amazon services, including CloudFront, CloudWatch, DynamoDB, EC2, CloudTrail, Elastic Beanstalk, and Lambda Function. It provides 200+ predefined rules and custom ones with limitations.
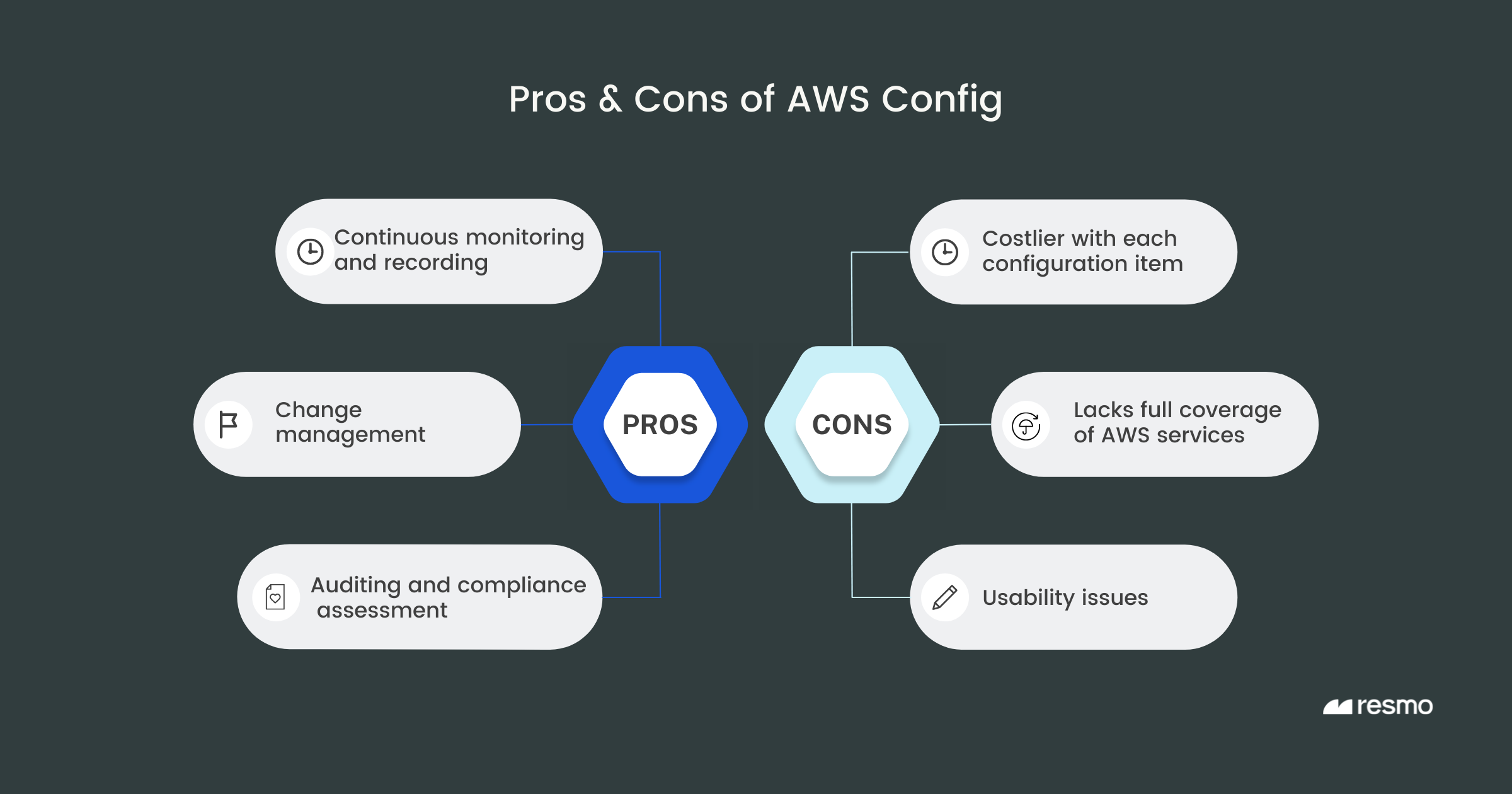
Advantages AWS Config Bring
The ultimate benefit to reap from AWS Config is the ability to discover AWS resources and track configuration changes without a doubt. In addition, we can expand on the benefits, including:
- Continuous monitoring and recording of configuration changes across your AWS resources
- Change management: Ability to observe historical configuration changes
- Continuous cloud resource auditing and compliance assessment
- Operational troubleshooting with AWS CloudTrail
- Multi-account and multi-region data aggregation
AWS Config Disadvantages
While AWS Config is a good service to monitor AWS resources, we can also point to its disadvantages for a more accurate and objective view of the service.
- The more configuration items it generates, the costlier it becomes.
- While it supports third-party services, the service is best for AWS resources. That means multi-cloud users and organizations that seek configuration visibility for SaaS assets will need additional tools.
- Config lacks full coverage for AWS services. In 2019, it supported 26 services and 72 resource types. It supports 45 AWS services and 200+ rules at the time of this writing. However, even for its own services, the coverage still falls behind what other services offer.
- It poses usability issues. AWS Config is a regional service; that is to say, you need to set up the service in all regions for all your AWS accounts. This translates into an excessive effort for those with a considerable number of AWS accounts. And this is only one possible situation where it would demand a lot of effort on your part.
Wrap-Up
AWS Config is a practical service to audit AWS cloud resources and gains asset visibility, which is invaluable for organizations to avoid misconfigurations, understand and secure resources, and faster troubleshooting.
Depending on your deployment size within AWS, it might be best to use Config. However, for expanding digital assets dispersed across multi-cloud environments and SaaS toolchains, you may want to replace Config with an alternative service like Resmo. It would be much more profitable in the long run:
- SQL querying across multiple clouds and SaaS resources, including many AWS Config rules, a heap of ready-to-use queries, rules, and room to create custom ones
- Configuration change histories in relation to who did the change, when the change occurred, the change date, etc.
- Collecting compliance evidence faster and using compliance packs
- Setting up integrations in minutes and start aggregating assets with ease
Know what needs to be detected in real-time, and secure your digital landscapes.
Published at DZone with permission of Hatice Ozsahan. See the original article here.
Opinions expressed by DZone contributors are their own.

Comments