How Passwordless Authentication Works
Securing your authentication and authorization process can't be overemphasized. In this article, you'll get to understand the nitty-gritty of passwordless authentication.
Join the DZone community and get the full member experience.
Join For FreeWhat Is Passwordless Authentication?
Passwordless authentication is a type of authentication where users do not need to log in with passwords. This form of authentication totally makes passwords obsolete. With this form of authentication, users are presented with the options of either logging in simply via a magic link, fingerprint, or using a token that is delivered via email or text message.
How Did Passwordless Authentication Come About?
Over the years, cases of stolen and hacked passwords have been on the rise. So many cases, such as the Yahoo data breach, Dropbox user accounts leak, and LinkedIn Data Breach had to do with having several passwords leaked.
In addition, platforms and applications keep emerging by the day and users have to register and set passwords for almost every one of them. Users are finding it really hard to keep up, thus encouraging them to use the same password for several applications. This is a very common occurrence. Now, there is a problem with this approach. Once a hacker gets access to user's password for one application, the hacker has a high probability of gaining access to every other account the user possesses. Password managers like LastPass and 1Password attempt to combat the challenge of users having to remember strong, crazy, and unique passwords across various systems.
With these challenges staring down at us like a monster, what if there are no more passwords to be hacked? What if there are no more passwords for users to remember? What if we discard the use of passwords totally? Passwordless authentication to the rescue!
Benefits of Passwordless Authentication
Without much ado, passwordless authentication helps:
- Improve User Experience: The faster users can sign up and use your service, the more users your app tends to attract. Users dread having to fill out forms and go through a rigorous registration process. Imagine eliminating that extra five minutes of asking users to remember their grandmother's maiden name as a security question. Passwordless authentication helps improve user experience in this regard!
- Increase Security: Once you go passwordless, there are no passwords to be hacked.
How Does Passwordless Authentication Really Work?
Having given a refresher on what passwordless authentication is and the benefits of its implementation, let's take an in-depth look at the process of implementing passwordless authentication in a typical application. Passwordless authentication can be implemented in various forms:
- Authentication with a magic link via email: With this form of authentication, the user is asked to enter their email address. Once the user submits the email address, a unique token or code is created and stored. An email with a URL that contains the unique token will be generated and sent to the user. When the link is clicked by the user, your server verifies that the unique token is valid and exchanges it for a long-lived token, which is stored in your database and sent back to the client to be stored typically as a browser cookie. There will also be checks on the server to ensure that the link was clicked within a certain period, e.g. three minutes.
Let's take a look at Auth0's magic link implementation below:
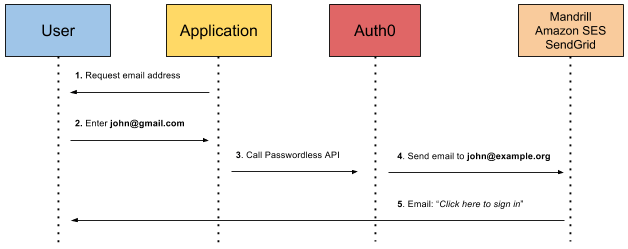
Auth0 sends a clickable link to your email
The user is then logged in.

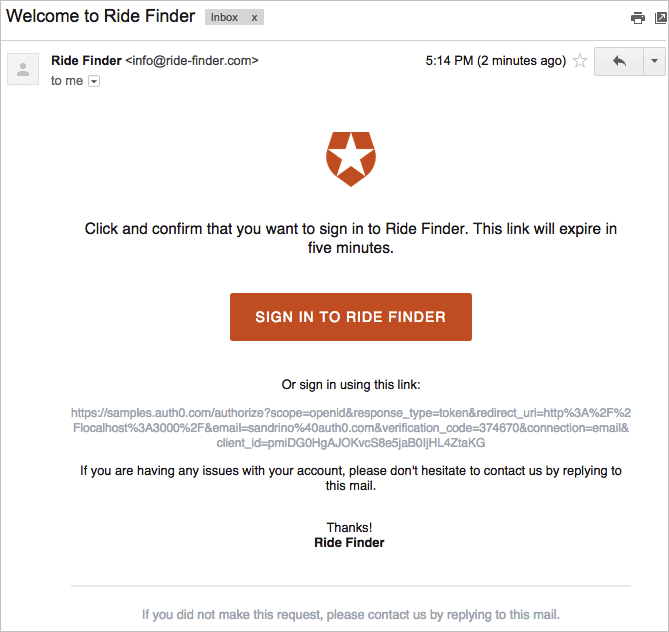
- Authentication with a one-time code via e-mail: With this form of authentication, the user is requested to enter their email address. An email is sent to the user with a unique, one-time code. Once the user enters this code into your application, your app validates that the code is correct, a session is initiated, and the user is logged in.
Let's take a look at Auth0's one-time code via email implementation below:
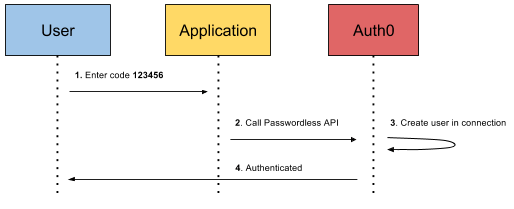
If the email address matches an existing user, Auth0 just authenticates the user like so:

- Authentication with a one-time code via SMS: With this form of authentication, the user is asked to enter a valid phone number. A unique, one-time code is then sent to the phone number. Once the user enters this code into your application, your app validates that the code is correct and that the phone number exists and belongs to a user, a session is initiated, and the user is logged in.
Let's take a look at Auth0's one-time code via SMS implementation below:

If the phone number matches an existing user, Auth0 just authenticates the user like so:

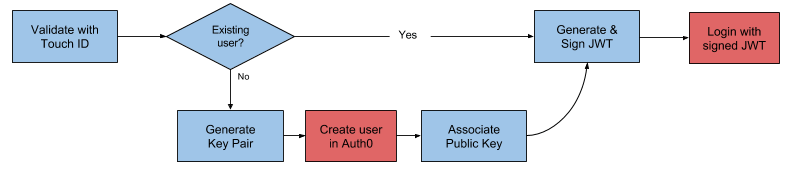
- Authentication with Fingerprint: With this form of authentication, the user is asked to place their finger on a mobile device. A unique key pair is generated on the device and a new user is created on the server that maps to the key. A session is initiated and the user is logged in.
Let's take a look at Auth0's fingerprint implementation. Auth0 supports Touch ID for iOS. This is the authentication flow:
Aside: Passwordless Authentication With Auth0
With Auth0, passwordless authentication is dead simple to implement. There are diagrams earlier in this post that already show the passwordless authentication flow using Auth0. You must have noticed a Passwordless API in those diagrams. This is a battle-tested and efficient API implementation of passwordless authentication. You can check out how it works under the hood or simply build your own implementation on top of it.
We can also easily configure our applications to use Auth0 Lock for passwordless authentication. Let's quickly create an application that implements a magic link by following the steps below:
- Clone this repo.
- Create an .
- On the dashboard, click on the red
Create Clientbutton to create a new app like so: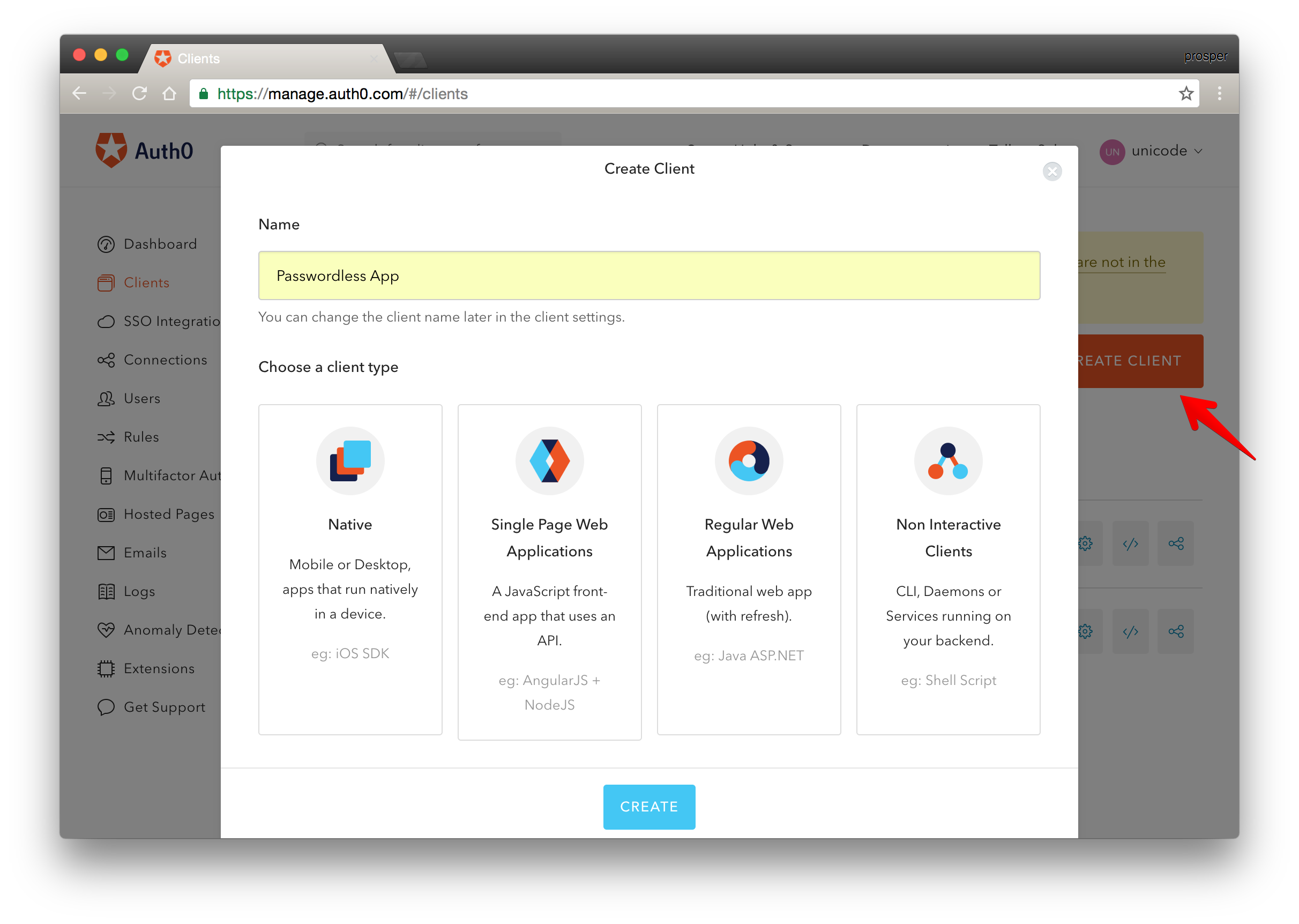
- Head over to the Passwordless Connections side of the dashboard and enable the email option.
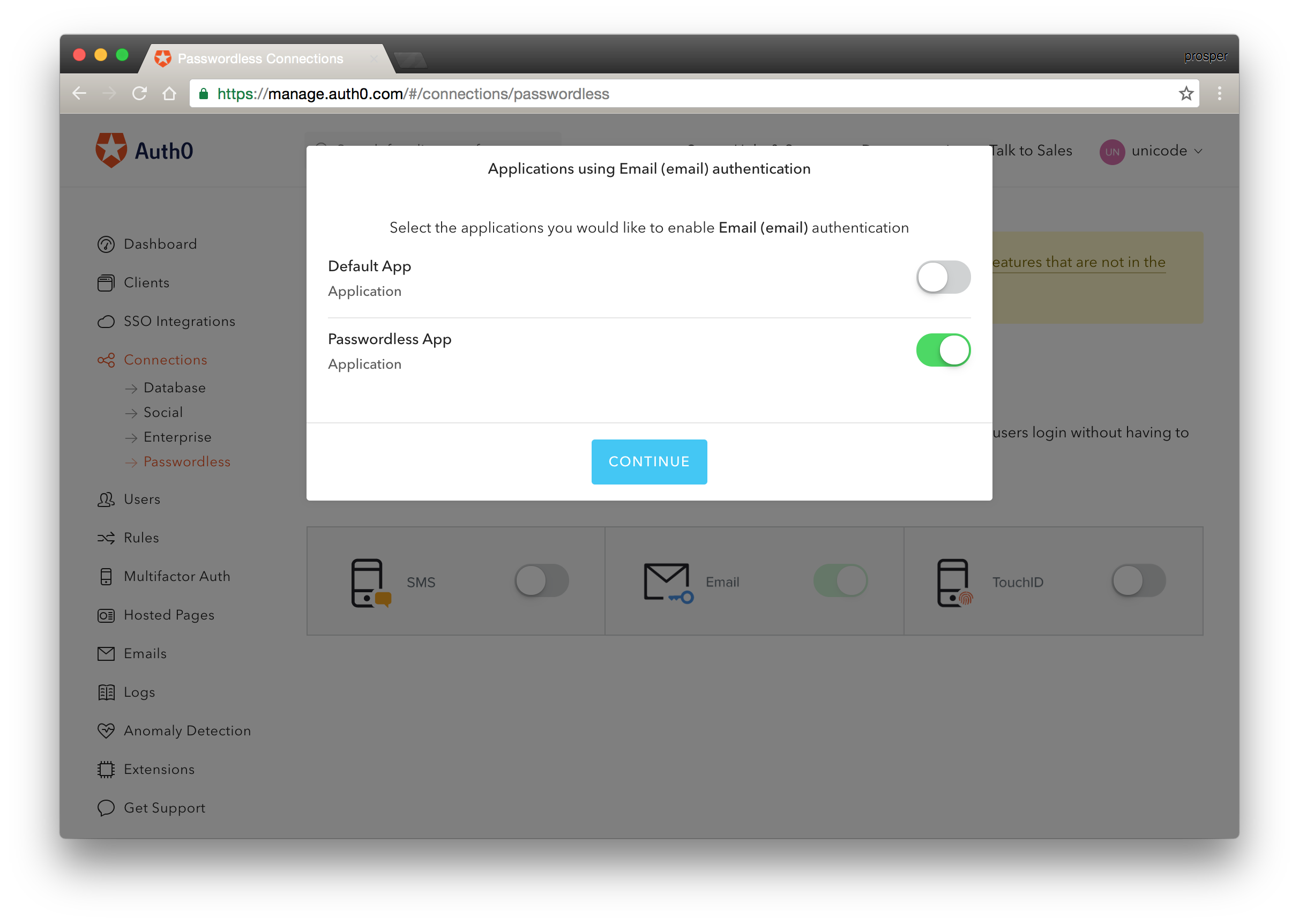 Enable Passwordless App
Enable Passwordless App
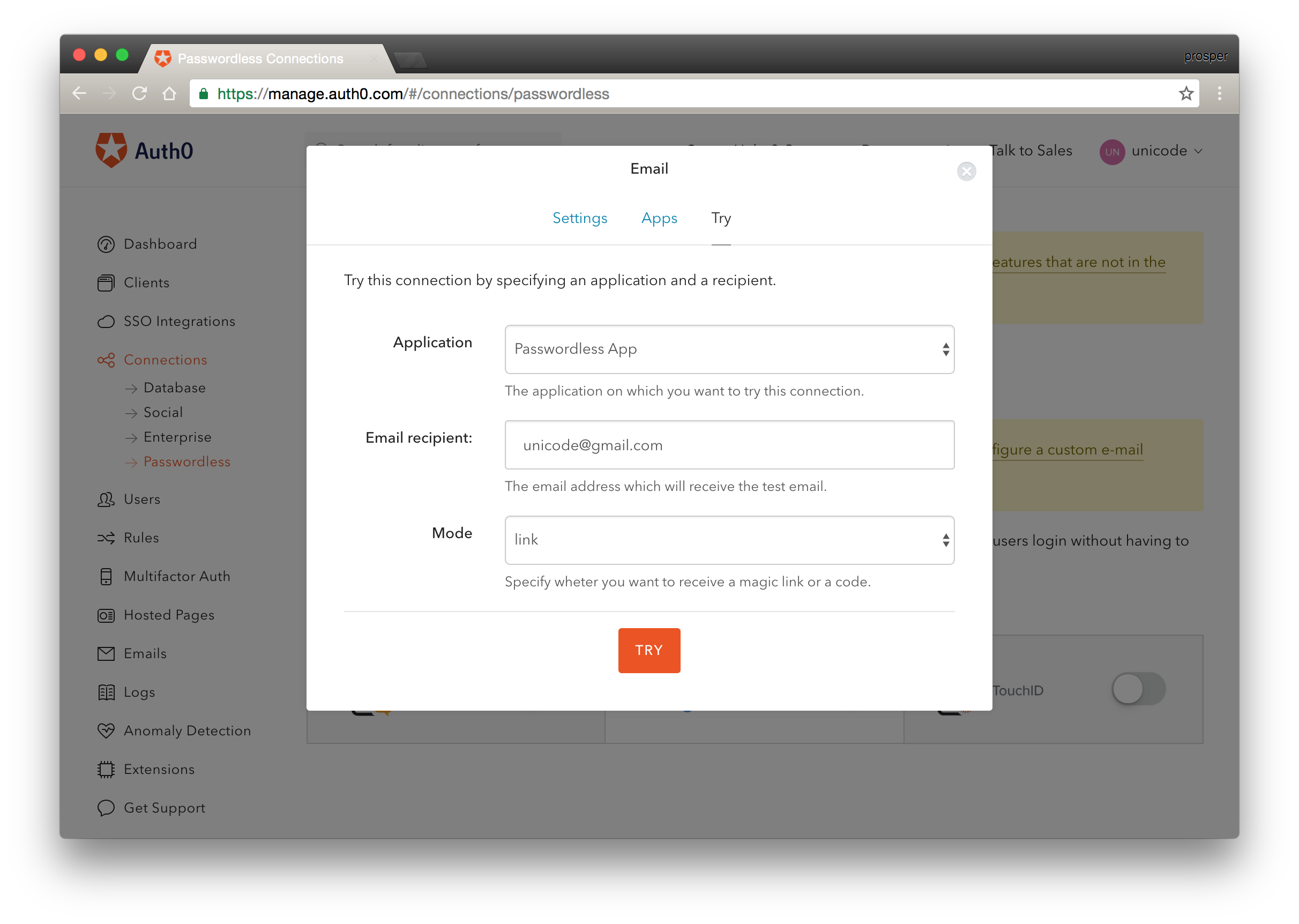 Enable Magic Link
Enable Magic Link
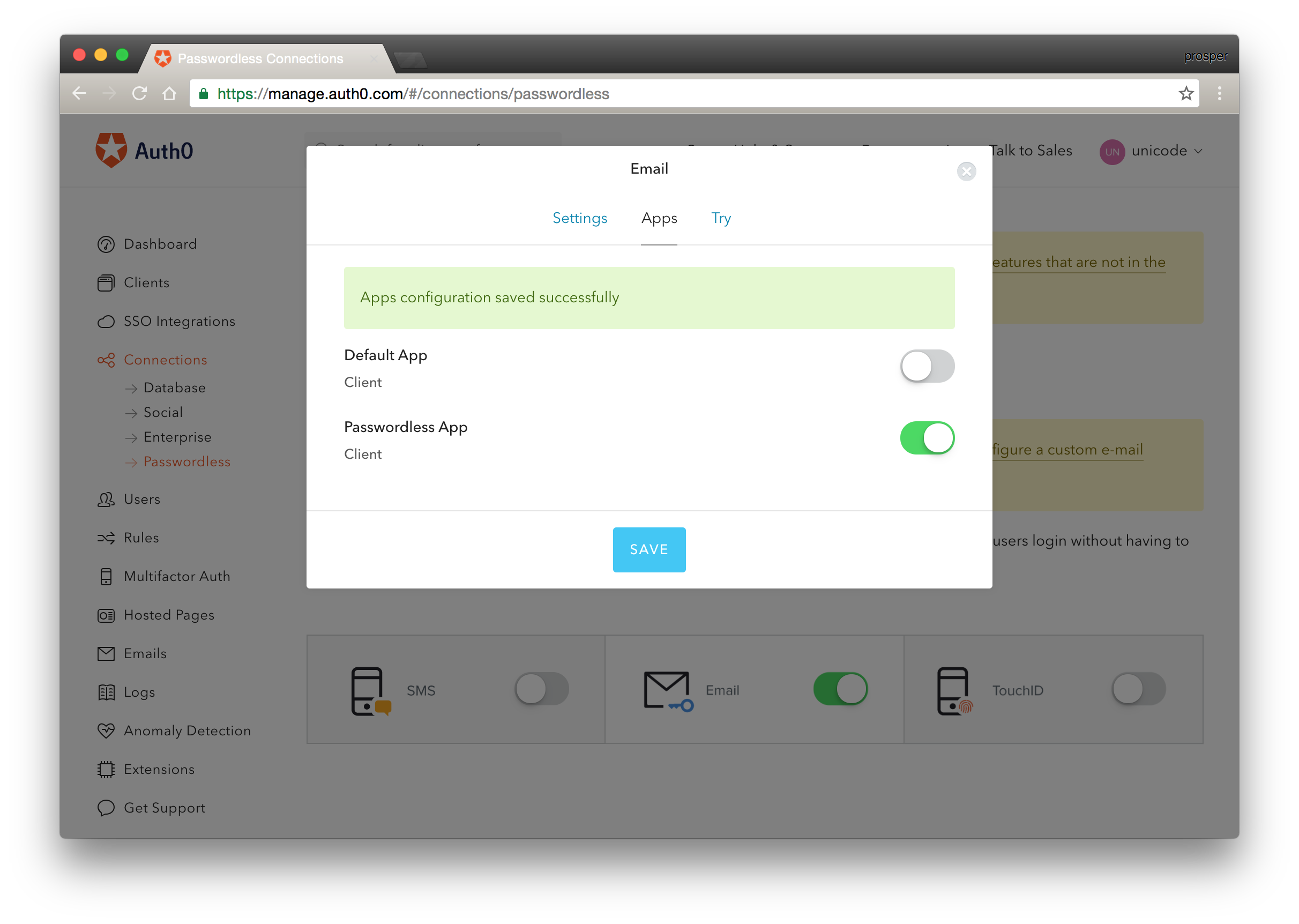 Save Configuration for Passwordless App
Save Configuration for Passwordless App
- Head over to your settings tab for the
Passwordless Appand copy yourclient_idanddomain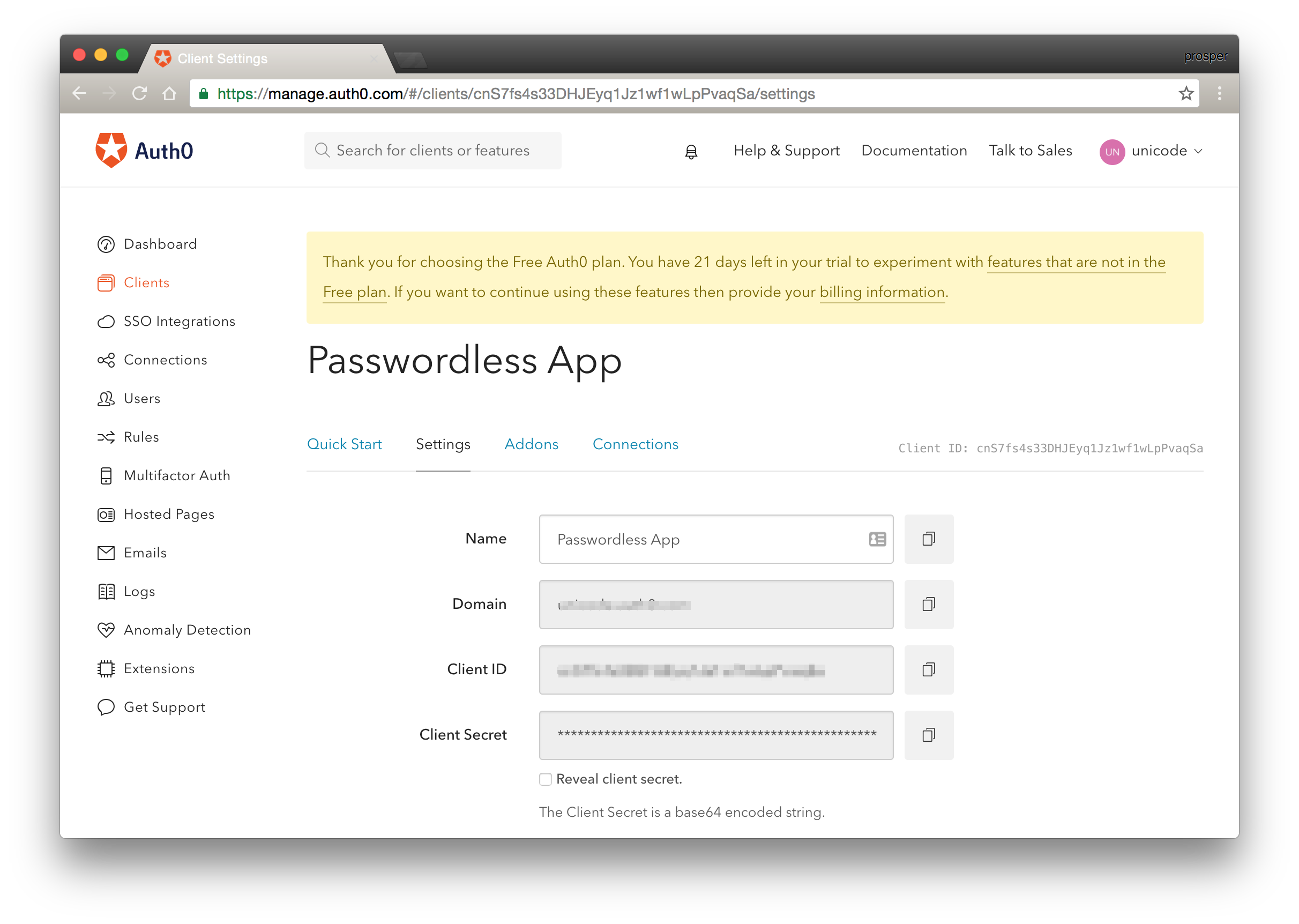 Settings Tab
Settings Tab - Open up
auth0-variables.jsin your code and replace theAUTH0_CLIENT_IDandAUTH0_DOMAINvalues with your real Auth0 keys. - Run and test the app.
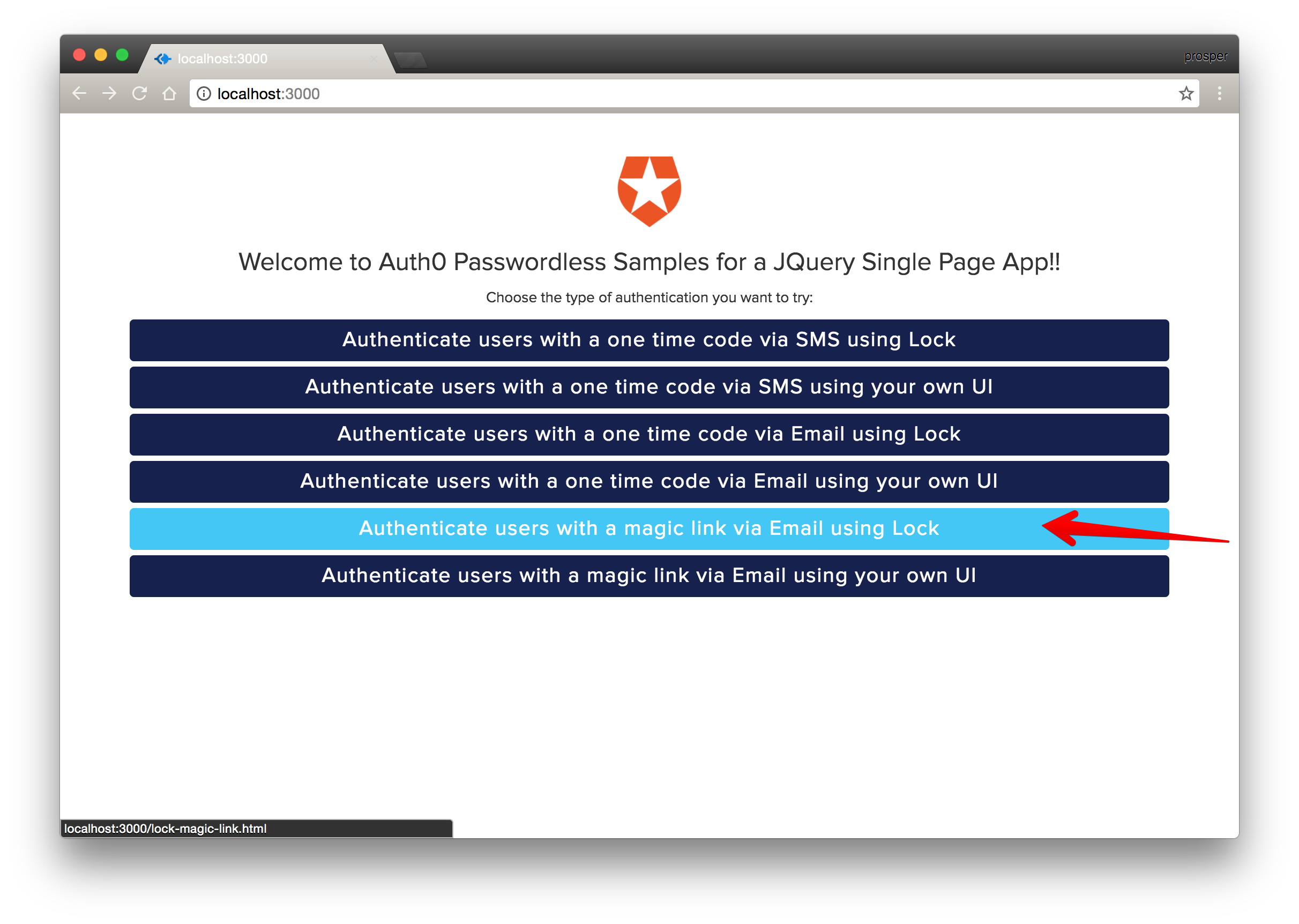 Click the Magic Link Button
Click the Magic Link Button
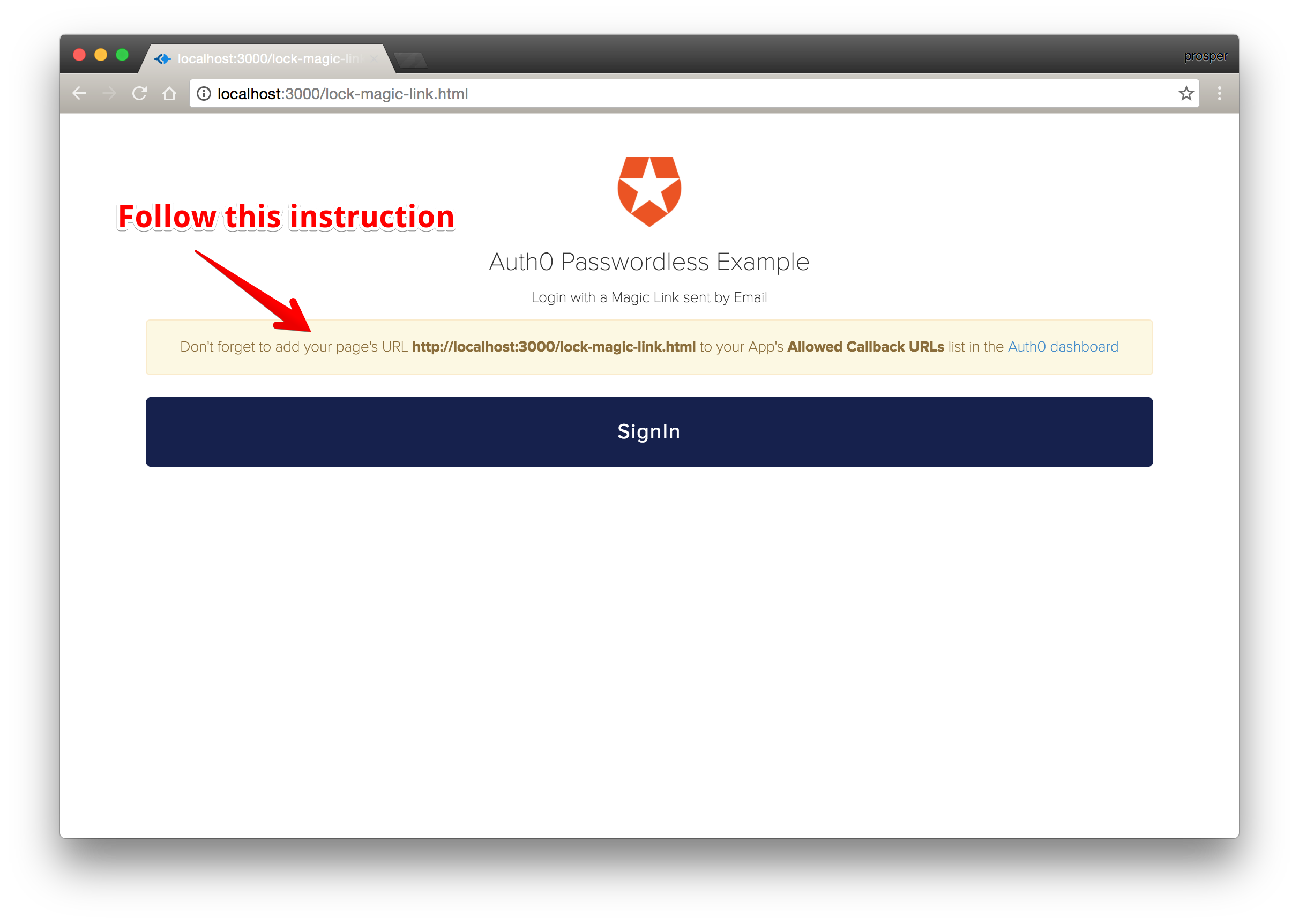 Follow the instructions and sign in
Follow the instructions and sign in
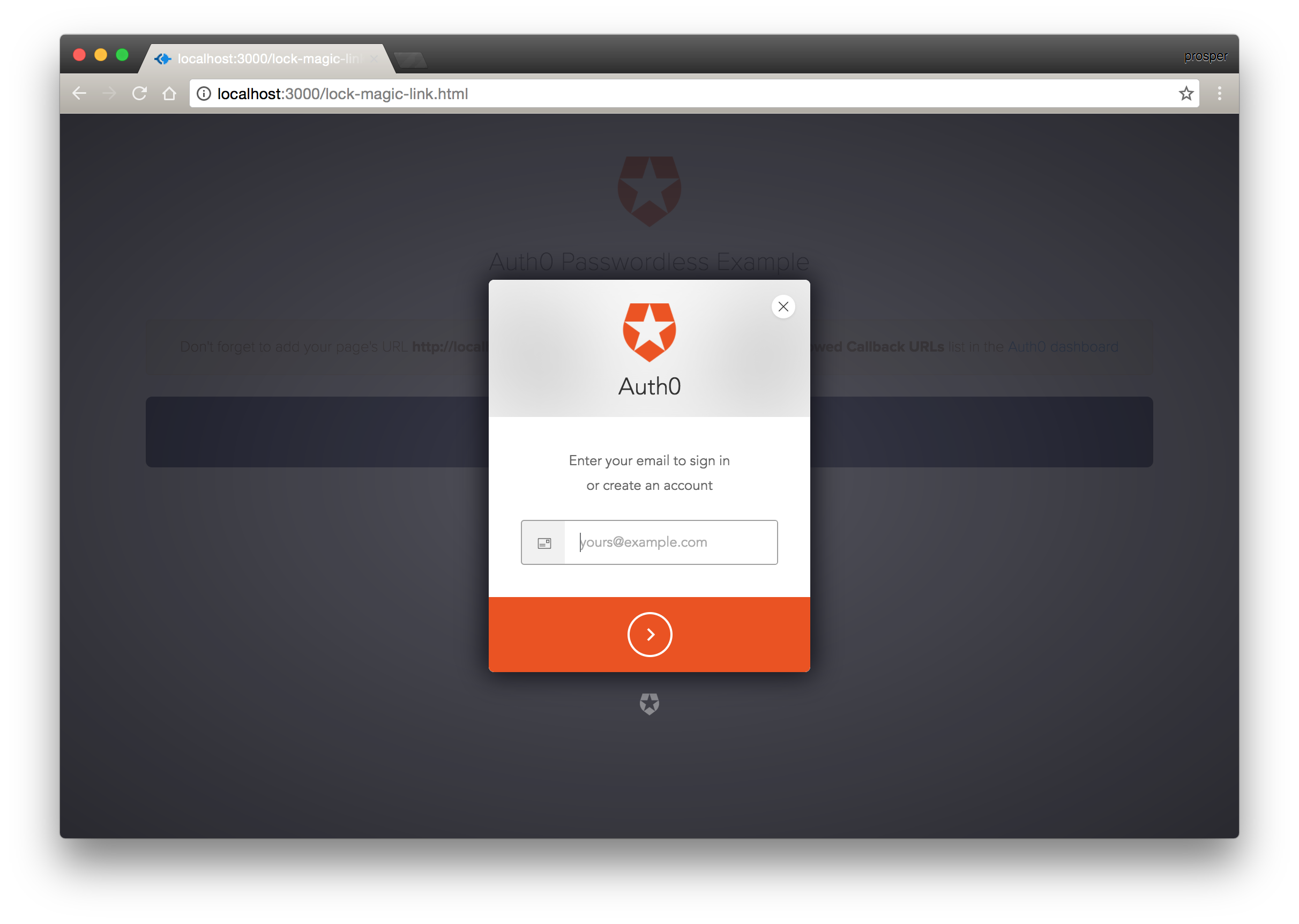 Submit your email on the Lock Widget
Submit your email on the Lock Widget
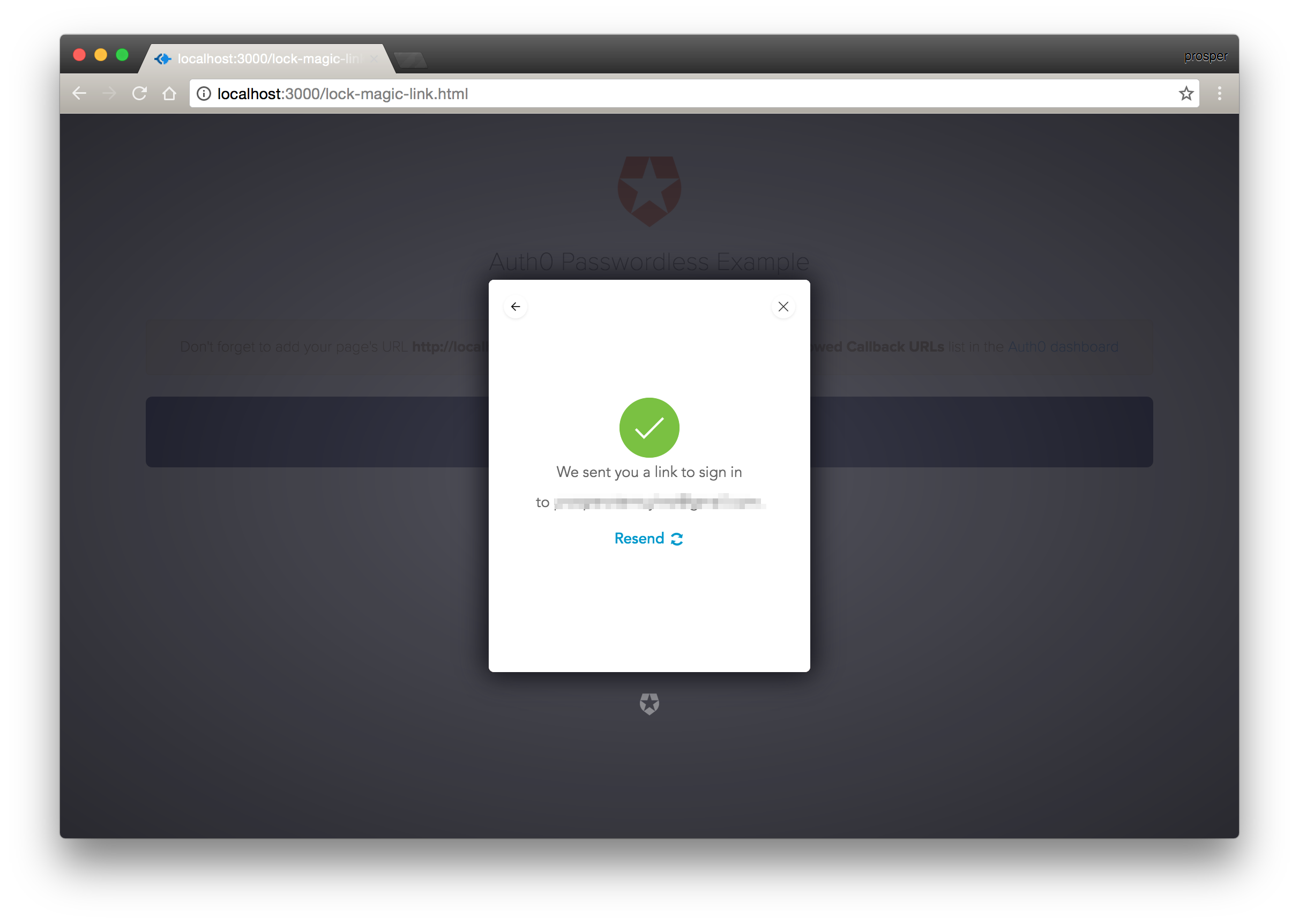 Notification Modal to show that the link has been sent
Notification Modal to show that the link has been sent
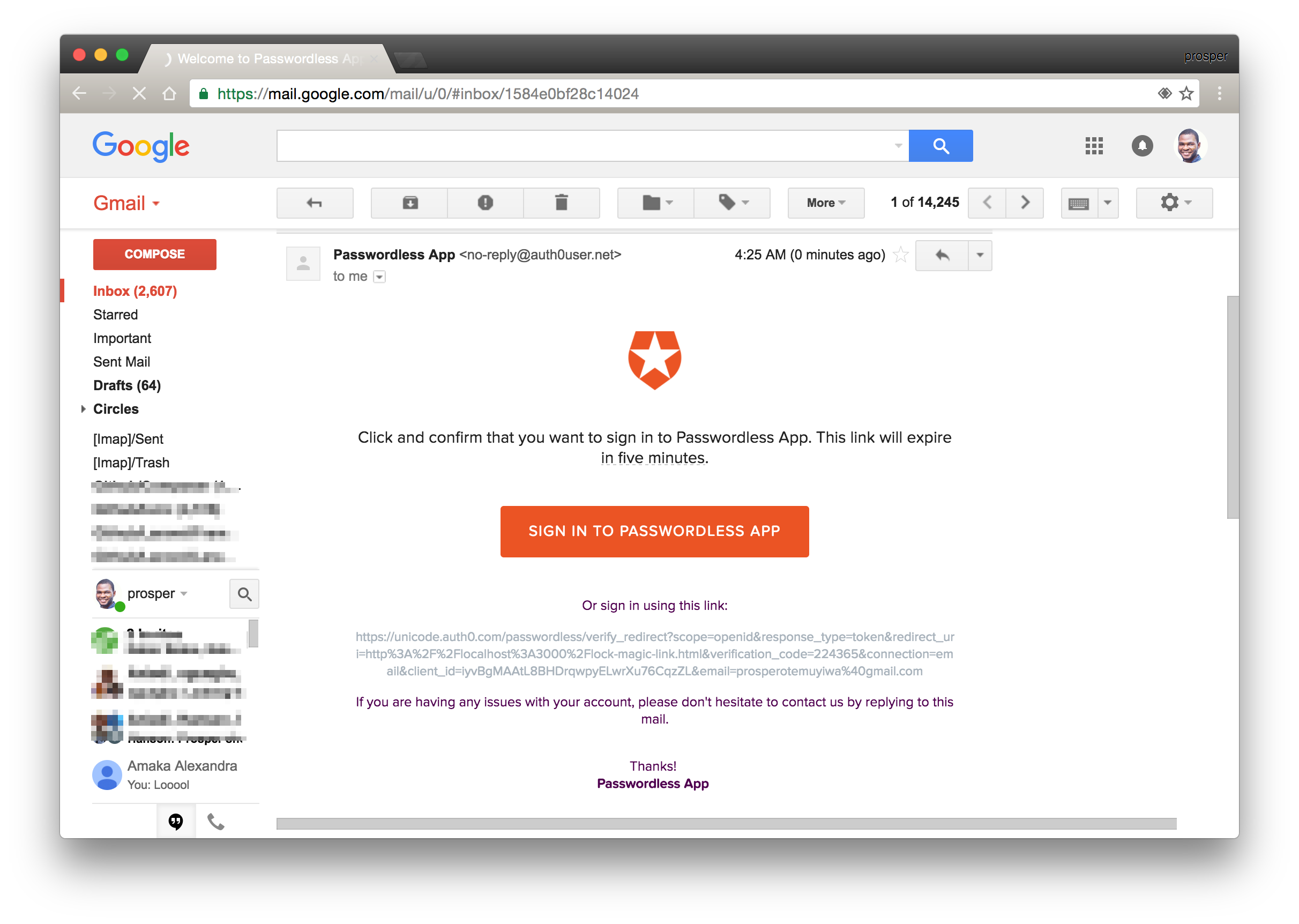 Magic Link From Email
Magic Link From Email
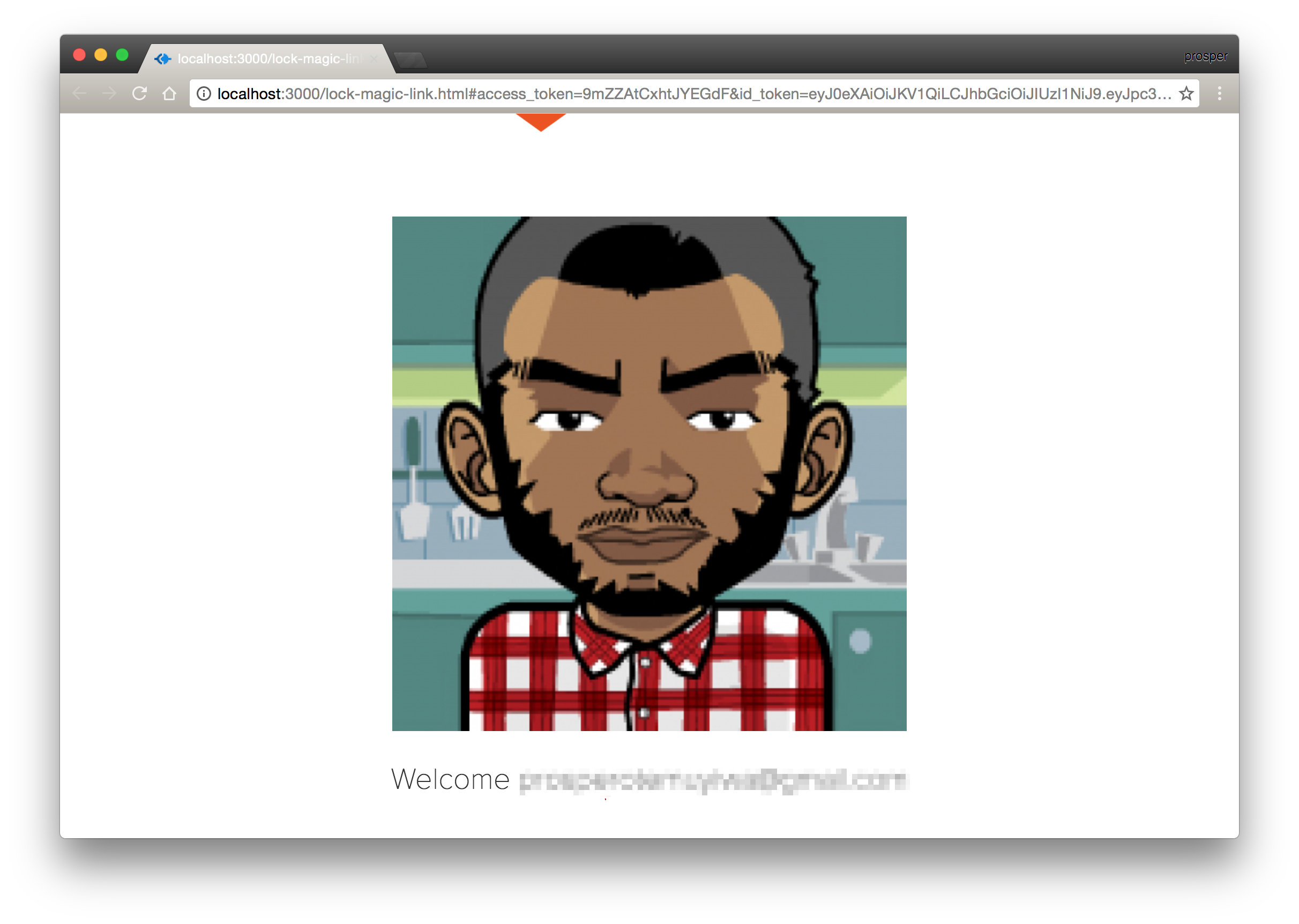 Signed in via the Magic Link
Signed in via the Magic Link
If you don't want to go through the process of creating an app, there is an online version you can play with here.
Conclusion
There is no doubt that passwords have become more susceptible to being compromised in recent years. Passwordless authentication aims to eliminate authentication vulnerabilities. This recent analysis of passwordless connections shows that passwordless adoption is increasing. Passwordless authentication is also very useful and gaining ground in the IoT world. It's easier, friendlier, and faster to be authenticated into an IoT device via Touch ID, push notification, or even a one-time passcode than with traditional means. If you really care about security, you should look into passwordless authentication!
We have covered how to implement practical passwordless authentication in an application using magic links. You can follow a similar process to achieve the same objective using a one-time code via SMS, and implement passwordless authentication today!
Published at DZone with permission of Prosper Otemuyiwa, DZone MVB. See the original article here.
Opinions expressed by DZone contributors are their own.

Comments