How to Decrypt Views in SQL Server
Read this article in order to view a tutorial on how to decrypt views in SQL server.
Join the DZone community and get the full member experience.
Join For Free“I am using SQL Server 2014. I have made views and I want to migrate those views from one server to another server. But, I need to decrypt my SQL Server 2014 view (encrypted view) as I want to modify the views as per my database requirement.”
Solution:
Sometimes we don’t want anyone to make changes to our views or don’t want anyone to make changes to our database object.
You may come around the situation when you have to make encrypted database objects for security purposes or need to edit your encrypted records.
Companies that rely on SQL Server need to look at or edit encrypted stored procedures, views, functions, etc. So, here, we will be focusing on encrypting and decrypting view in SQL Server Database.
How to Encrypt Views by Using the SQL Server Management Studio:
The encryption of database object can be done by using the WITH ENCRYPTION option while creating the database object. So let us understand how to encrypt view in SQL Server.
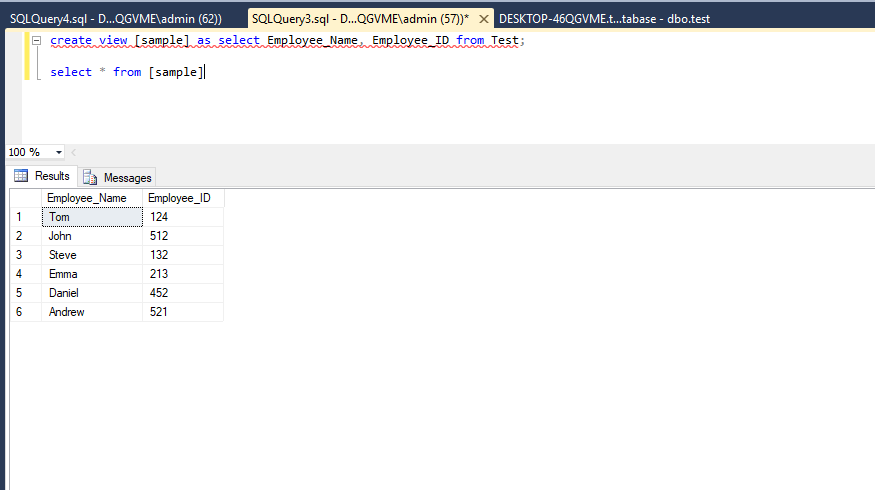
Here is the script for creating the view:
create view [sample] as
select dbo.test.Employee_Name,
Employee_ID from Test;
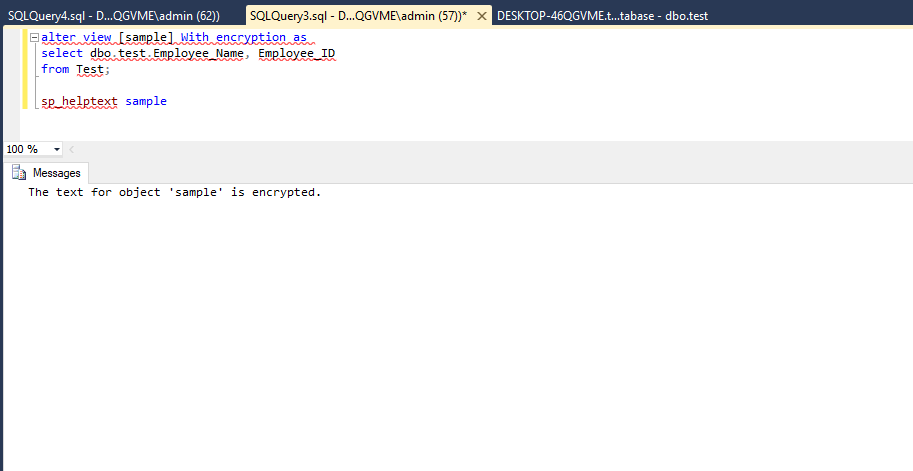
Now encrypt your database by using the WITH ENCRYPTION option:
alter view [sample] With encryption as
select dbo.test.Employee_Name, Employee_ID
from Test;
Now, run sp_help command to check whether your view gets encrypted or not. You will get a pop-up of the successfully encrypted message.
Similarly, you can encrypt other database objects like functions and stored procedures in SQL Server.
How to Decrypt View Using the SysTools SQL Decryptor:
Once encrypted, it becomes quite difficult to decrypt your database object. For this, you can try SysTools SQL Decryptor Tool. Once installed, decrypting an object becomes simple and fast. You can decrypt multiple SQL Database objects at a time. You can decrypt SQL database object of any file size.
The tool provides two different authentication option for decrypting SQL Database object, ie Windows Authentication & SQL Server Authentication. The software supports SQL Server version 2014, 2012, 2008, 2005,2000. You will get two different options for exporting decrypted object ie SQL Server Database & SQL Server Compatible Script.
Lets us know how you can decrypt view using SQL Decryptor Tool.
Launch SQL Decryptor Tool and click on Start Button.
Fill the server credentials required to connect to the SQL Server Database like Server Name, Database name. Choose the Login mode as per your database connection. Click Next

You will be able to preview your decrypted view. Click Next.

You will get two different options to export your decrypted database object: SQL Server Database or SQL Compatible Script. Choose according to your need. Here, I have exported the decrypted database view in SQL Compatible Script so that I can use it for further use.
Click on Export.

Similarly, in this way, you will be able to decrypt other database objects like stored procedure, functions, etc.
Conclusion:
In this article, I have discussed how can you secure your database object by encrypting them using the WITH ENCRYPTION option. You can easily edit or modify your database view by decrypting the encrypted view as discussed above.
Opinions expressed by DZone contributors are their own.

Comments