How to Exploit a Microservice Architecture
With an emerging pattern of organizations embracing the DevOps framework, adopting Microservice Architecture is steadily gaining the respect it deserves.
Join the DZone community and get the full member experience.
Join For FreeWith an emerging pattern of organizations embracing the DevOps framework, adopting Microservice Architecture is steadily gaining the respect it deserves.
While DevOps eliminate organizational silos by enabling efficient collaboration, streamlining workflow integration, and automating application delivery. Microservice Architecture acts as an essential enabler to achieve a DevOps model by distributing an application into multiple deployable services. Microservices work as autonomous applications, decoupled from each other, and can be built, scaled, and deployed independently. This lets teams comprehend the application architecture easily and speed up delivery pipelines.
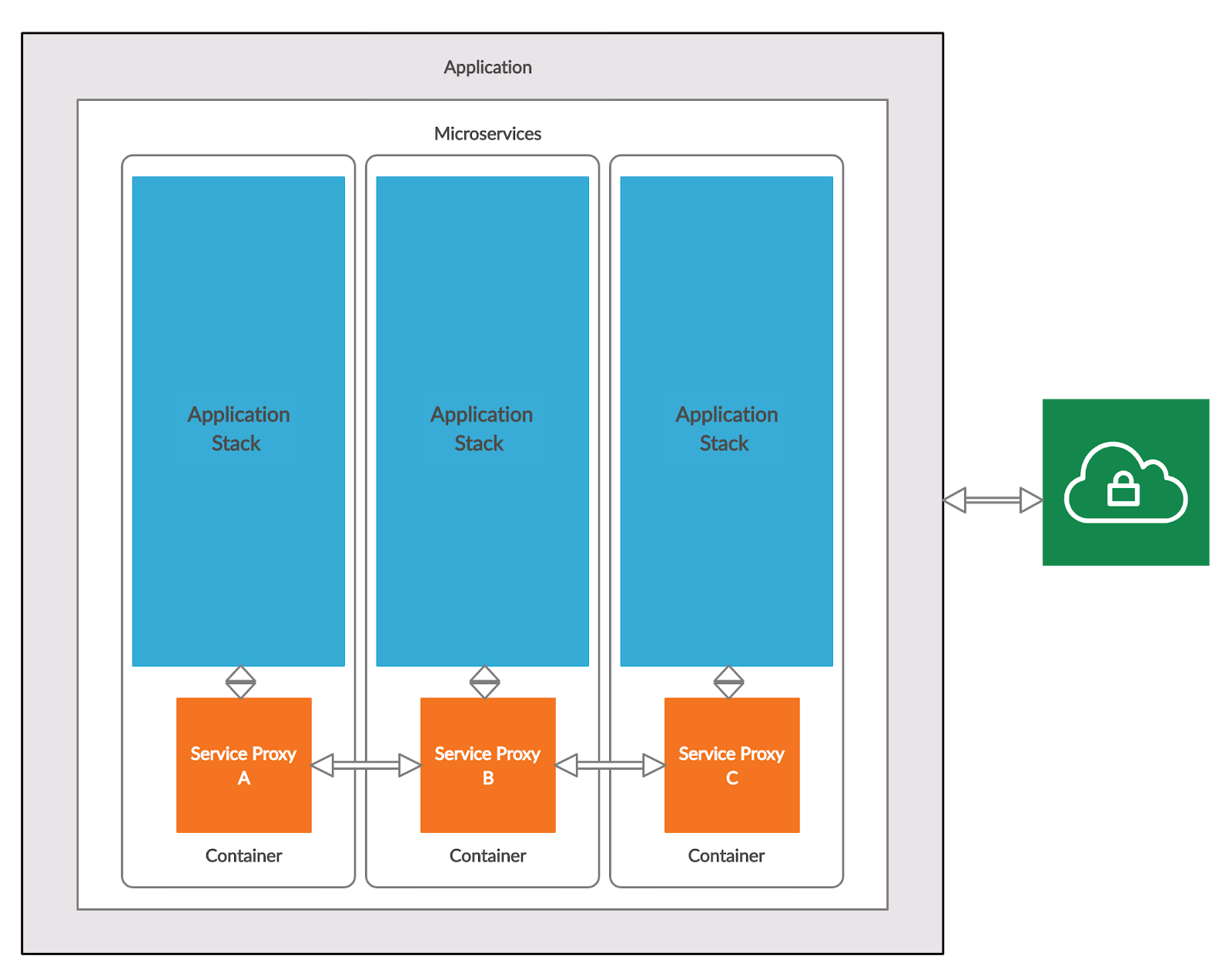
The above image shows a typical application broken down into a set of microservices. Each of these services are essentially miniature applications hosted on individual containers, while communicating with each other through a Service Proxy. Any external entity(depicted in Green), be it a user or an external service, would access the application (through a secured API Gateway) as a whole rather than an individual microservice.
Apparently, the benefits of a Microservices based DevOps model are a dime a dozen. But then, there are challenges in maintaining a Microservice Architecture too. Specifically, dealing with an elaborate security implementation.
Vulnerabilities Within a Microservice Architecture
Microservices are considered to be four times more vulnerable than traditional monolithic applications. Due to its distributed structure, each service API and network layer expose susceptible entry points to potential attack vectors.
Microservices are uniquely orchestrated using a broad range of tools when compared to a monolithic framework. Usually, such tools rely on pre-built repositories, open-source code, and containers with/without validated security protocols. With extensive usage of third-party unpatched libraries within each of those containers, implementing a security strategy gets complicated, thereby increasing overall risk. Additionally, as microservices are containerized applications in its core, a single compromised container enables attack vectors to replicate the hack across a wider surface quickly.
Typically service calls are secured by implementing an API gateway, which acts as the single entry point to receive a call and then route traffic onto different services. This approach of having a single entry point through authentication has its own merits and demerits. Theoretically, an API gateway limits the attack surface; however, it also turns out to be a single point of failure for potential attack vectors. Recent research also suggests that most traditional attack vectors target an application through API calls.
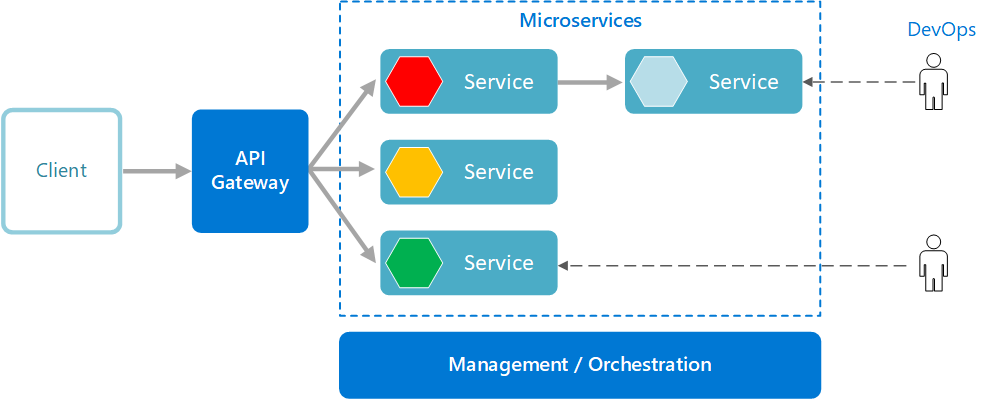
Image Source: https://docs.microsoft.com/
Additionally, monitoring of microservices is considered as a critical aspect in maintaining security within a microservice framework. The absence of an efficient load balancing and application monitoring worsens an organization's combat position in isolating threats and negating a quick quarantine. Effective monitoring for microservices is crucial to be administered across all layers, including API Payload, query strings, cookies, and HTTP headers.
Securing Microservices
The approach to enable secured access to Microservices remains substantially different than a traditional monolithic framework. As a rule of thumb, administering secure authentication by provisioning on-demand identity tokens remains crucial. Through a Zero-Trust strategy, short-lived, encrypted access secrets are distributed to pass the right level of authorization on an application, service, or pipeline layer.
With an increase in the application's attack surface, a cross-platform centralized security module doesn't hold ground. Securing microservices through only a network-segmentation or a perimeter-based approach is usually considered ineffective and insufficient to limit application threats.
Instead, securing Microservices starts with the holistic approach of embedding security by transforming DevOps into a DevSecOps model. This begins with the mindset of considering Security at par with Development and Operations since the beginning of the SDLC, by essentially analyzing Risk Tolerance since day-one of a software lifecycle. With a DevSecOps model in place, performance, scalability, and security are weighed equally without any bias.
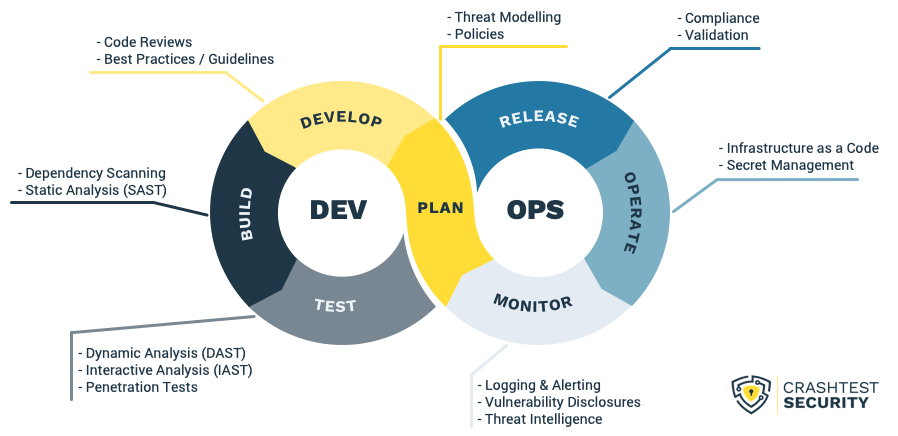
With a source control monitoring and dependency scanning in place, Continuous Hacking adjoins Continuous Integration and Continuous Delivery; to ensure CI/CD pipelines are tested during execution for run-time checks. To do so, a common practice is through employing Static Application Security Testing (SAST) and Dynamic Application Security Testing (DAST) approaches since the early stages of an SDLC. While SAST helps to analyze source code vulnerabilities before compiling the code and ensuring developers mitigate security flaws with real-time feedback, DAST helps identify architectural and code level weaknesses while running in production.
This article was originally published on https://blog.crashtest-security.com/how-to-exploit-microservices and has been authorized by Crashtest Security for a republish.
Opinions expressed by DZone contributors are their own.

Comments