How to Onboard and Protect Remote Teams With Secure Cloud Environments
Secure cloud environments transform remote software development, aiding organizations with remote teams to onboard and manage them cost-effectively.
Join the DZone community and get the full member experience.
Join For FreeHow Secure Cloud Development Addresses the Challenge of Working Securely With Remote Teams
The landscape of software development is constantly changing, and secure Cloud Development Environments (CDEs) have brought about a remarkable transformation in secure project management and execution when working with geographically dispersed teams using a remote development platform.
Adding security to CDEs is extremely pertinent for organizations dealing with remote software development. These firms often struggle with issues such as remote team onboarding, maintaining uniformity in processes, and safeguarding security. Secure CDEs effectively tackle these issues, leading to a development process that's not only more streamlined and flexible but also more cost-effective by removing the need to send laptops secured against data leaks (I discuss this problem here).
In this discussion, I am going to delve into how secure CDEs are redefining the remote development paradigm, enhancing team collaboration, ensuring process uniformity and security, cutting costs, and offering real-time analytics and monitoring. Connected to this topic, I previously wrote on DZone about the organizational aspects of building a liquid workforce of developers. In the present one, I am looking in more detail at the technical side of implementing a secure process for remote software development.
Here are five aspects of operating a remote development team that benefit from the use of secure Cloud Development Environments, yielding an efficient remote development platform.
Enhanced Collaboration and Accessibility for Remote Teams
The cornerstone of any successful outsourcing endeavor is effective collaboration. Platforms to manage secure CDEs redefine this aspect by offering a mechanism where geographically dispersed teams can work together easily.
Because CDEs are available online, the ability to access a unified development environment, e.g., using pre-defined templates, from anywhere in the world ensures that team members are always on the same page, regardless of their physical location.
This global accessibility not only makes it easier to integrate diverse skill sets into the development process but also ensures that projects can progress around the clock, leveraging different time zones. This setup is ideal for a BYOD strategy. You can actually compare the cost of a BYOD strategy against sending secure laptops with this online calculator tool.
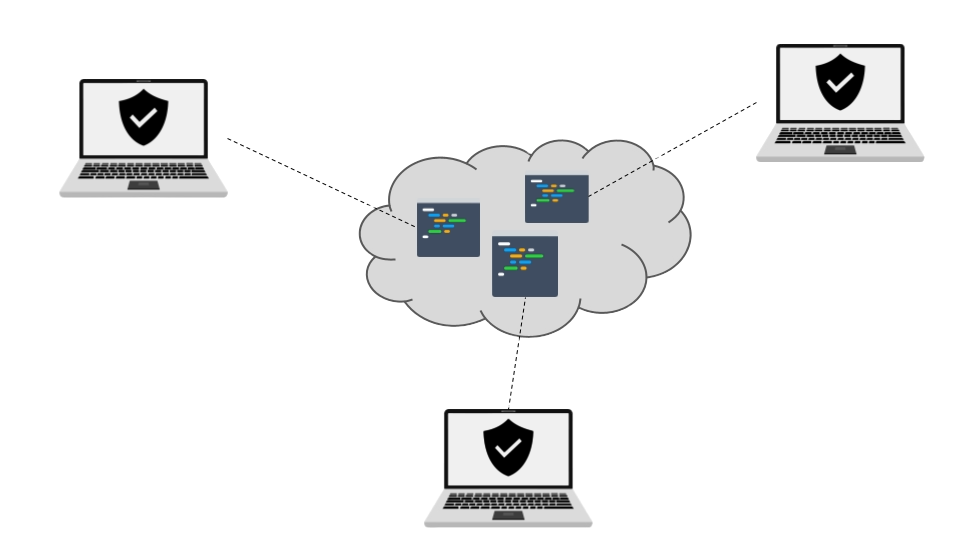
Figure: Coding environments as CDEs are available online, ensuring teams' access regardless of physical location.
Onboarding Remote Teams on Standardized Development Environments
The agility of CDEs is a boon for organizations dealing with fluctuating project demands (which connects to the liquid workforce concept that I discussed previously). The cloud-based nature of CDEs means that onboarding a new team member is as simple as providing access to the platform, significantly reducing the lead time and allowing for rapid scaling as per project requirements.
In addition, CDEs serve as a single source of truth for development teams. By standardizing the development environments using templates, they ensure that every member employed by the outsourcing firm works with a consistent set of tools and configurations in accordance with the customer project. This uniformity plays a crucial role in minimizing compatibility issues and streamlining the development process. It ensures that the code developed is consistent and maintainable, regardless of the number of hands it passes through, which is a common scenario in remote development.
Security and IP Protection With Remote Teams
One of the primary concerns in handling development through remote teams is the security of code and intellectual property. Secure CDEs precisely address this concern by providing robust security features such as controlled data access, as well as data loss prevention mechanisms that prevent data leaks.
The centralized nature of secure CDEs means that sensitive data and intellectual property are stored securely in the cloud rather than on individual devices, reducing the risk of data breaches. To fully realize data protection, the remote development platform needs to provide security against data leaks for the entire developer workflow. In contrast, CDE platform providers such as Codespaces, Google Workstation, Coder, and Gitpod do not focus on preventing data exfiltration. In other words, it is trivial to exfiltrate data from these platforms since their focus is mainly on productivity. In this other article, I explain how and why a secure CDE platform needs to take a “workflow” perspective to protect data while working with remote teams. This is illustrated in the figure below.
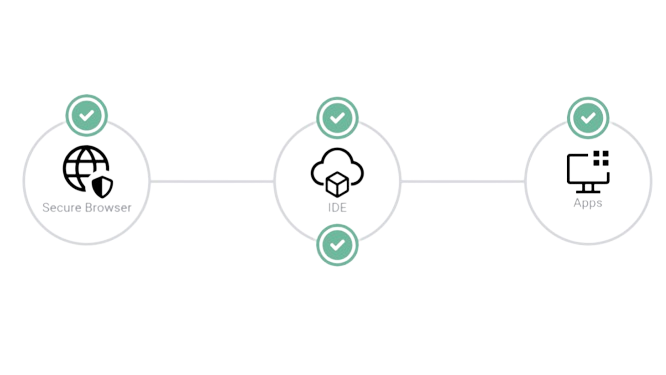
Figure: Secure CDEs, in particular, address this by providing robust security features like controlled data and web application access and data loss prevention mechanisms that prevent data exfiltration.
Cost-Effective Infrastructure With Secure Cloud Environments
CDEs eliminate the need for heavy investment in hardware and software licenses. With cloud-based development environments, outsourcing companies can opt for scalable resource consumption models that are more economical and flexible. This is particularly beneficial for small to medium-sized firms that can now compete with larger organizations by leveraging the power of CDEs without the burden of significant upfront costs.
Here again, using an online calculator, you can assess potential cost reductions in infrastructure expenses (corporate laptop, endpoint security, etc) using secure CDEs as opposed to deploying hardware devices.
Figure: The flexibility of Cloud resource consumption allows organizations to control their capital expenditures when working with remote teams.
Analytic Capabilities of Remote Development Platforms
From a risk control perspective, monitoring security and performance is an important aspect when onboarding and working with remote teams using secure CDEs.
Having access to comprehensive monitoring and analytic capabilities is an essential capability for a remote development platform. Organizations can leverage these features to gain insights into team performance, resource utilization, and process efficiency. This data is invaluable for making informed decisions, optimizing workflows, and continuously improving the service quality offered to clients.
Best-Practices in Secure Remote Development
In conclusion, secure Cloud Development Environments signify a transformative change in the realm of secure remote team onboarding and remote software development. These environments not only streamline collaboration but also bring standardization and heightened security to a remote development platform.
The most important aspect when onboarding remote development teams is to provide an adequate security and performance mechanism for process governance. For that, only secure CDEs can deliver a reliable, secure environment since this requires taking a workflow perspective to secure data.
To fulfill this goal, I explained that secure CDEs precisely address this need by providing robust security features like controlled data, secured web application access, as well as data loss prevention mechanisms that prevent data exfiltration across the IDE and the other applications used by the developer during daily tasks, such as code repository applications, CD/CI applications, etc. More information about this particular technical aspect of secure CDE platforms can be found here.
Published at DZone with permission of Laurent Balmelli, PhD. See the original article here.
Opinions expressed by DZone contributors are their own.

Comments