Infinispan Insights: Security Basics and Secured Caches
This article shows you how to secure your Infinispan cluster, protecting both cluster management and data access in various Infinispan caches.
Join the DZone community and get the full member experience.
Join For FreeSecurity in a Nutshell
When we talk about security, there are two main things to consider: proving who you are (authentication) and deciding what you’re allowed to do (authorization). These tasks are managed by one or more security realms.
Authentication
Authentication is the process of verifying the identity of an entity, such as a user, system, or device, to ensure that it is who or what it claims to be. It can be done through different methods such as password-based authentication, token-based authentication, certificate-based… and more.
Authorization
Authorization is the process of granting or denying access permissions to authenticated users or entities. It defines what actions or resources users are allowed to access based on their verified identity. Authorization works alongside authentication to ensure that only authorized users can perform specific actions within a system. Infinispan uses Role-Based Access Control (RBAC) for authorization.
Security Realms
A security realm is a set of policies and authentication methods governing access to a system or resource. It establishes rules for user authentication and authorization, such as using usernames/passwords or advanced methods like OAuth. Security realms integrate Infinispan Server deployments with the network protocols and infrastructure in your environment that control access and verify user identities. Infinispan integrates with Kerberos, LDAP, Trust stores… and token-based authentication such as OpenID Connect providers such as Keycloak.
Infinispan Server Security
To truly grasp the basics, the best method is hands-on experience. Infinispan 15.0 simplifies understanding authentication and authorization through a visual interface.
Running the Infinispan Server With a Single User
Start by running the Infinispan Server with a Docker or Podman container. Make sure you have the latest version of the Infinispan Server 15.0 image by pulling it locally.
# Podmanpodman run -it -p 11222:11222 -e USER="admin" -e PASS="password" --net=host quay.io/infinispan/server:15.0# Dockerdocker run -it -p 11222:11222 -e USER="admin" -e PASS="password" quay.io/infinispan/server:15.0Infinispan Defaults
In Infinispan, the default security realm relies on properties. Users are established in a local properties file on the active server. By running the container and providing "USER" and "PASS" environment variables, the server generates a user capable of authenticating to Infinispan and is automatically granted the "admin" implicit role.
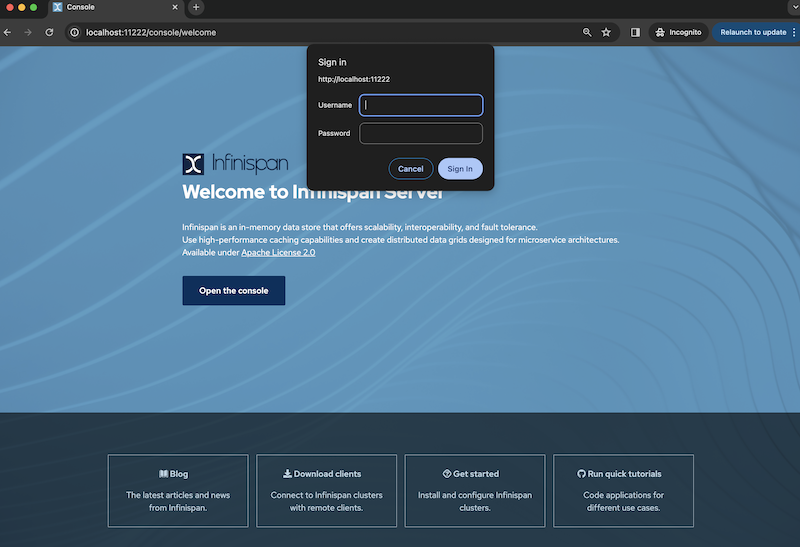
Infinispan doesn’t maintain user authentication through a session management system in the server for its REST API. The REST API operates in a stateless manner, and authentication, as well as role-based access control (RBAC), is facilitated through the AUTHENTICATION header when interacting with the REST API. The console is built using the REST API. DIGEST mechanism is part of the supported mechanism, so the browser will ask for user/password using the native browser authentication mechanism. For security reasons, BASIC authentication is not enabled by default unless TLS is also configured.
Implicit RBAC
Infinispan safeguards operations by specifying various permissions to operations such as creating caches, resetting statistics, uploading data schemas, and more. A role is a set of 1 or more permissions. Implicit authorization is enabled by default, providing predefined roles to which users can be assigned, granting them the ability to execute specific actions.
Starting from Infinispan 15, a new feature in the console allows users to view these roles, their corresponding permissions, and descriptions. It is now also possible to create custom roles with specific permissions directly from the web console (previously, this capability was limited to the Command Line Tool). However, for the purpose of this article, we will focus on utilizing the pre-existing implicit roles.
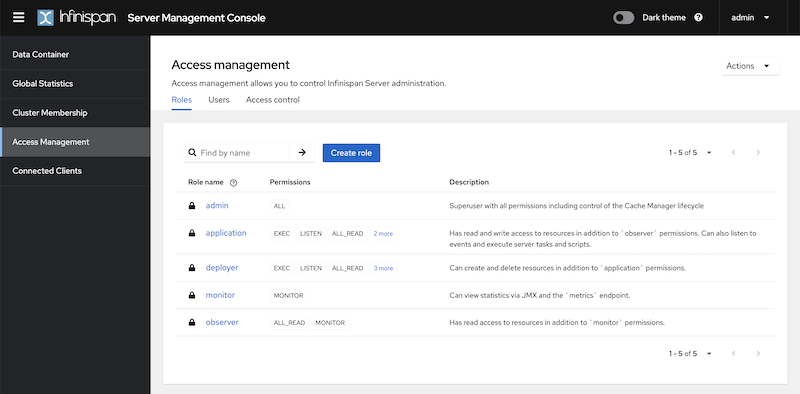
Running the Server With Multiple Users
To start Infinispan locally with multiple users and distinct roles, we can employ an identities batch that is passed to the container during startup.
Create a file called identities.batch with the following content. To simplify matters, we have established a straightforward one-to-one mapping between user names and roles.
identities.batch
user create "admin" -p "password" -g admin user create "observer" -p "password" -g observer user create "monitor" -p "password" -g monitor user create "deployer" -p "password" -g deployer user create "application" -p "password" -g application
Provide the file on the run by creating the user-config volume and passing the IDENTITIES_BATCH env variable.
# Podmanpodman run -it -p 11222:11222 -v $(pwd):/user-config -e IDENTITIES_BATCH="/user-config/identities.batch" --net=host quay.io/infinispan/server:15.0# Dockerdocker run -it -p 11222:11222 -v $(pwd):/user-config -e IDENTITIES_BATCH="/user-config/identities.batch" quay.io/infinispan/server:15.0Those users are now available and listed in the Infinispan Web Console.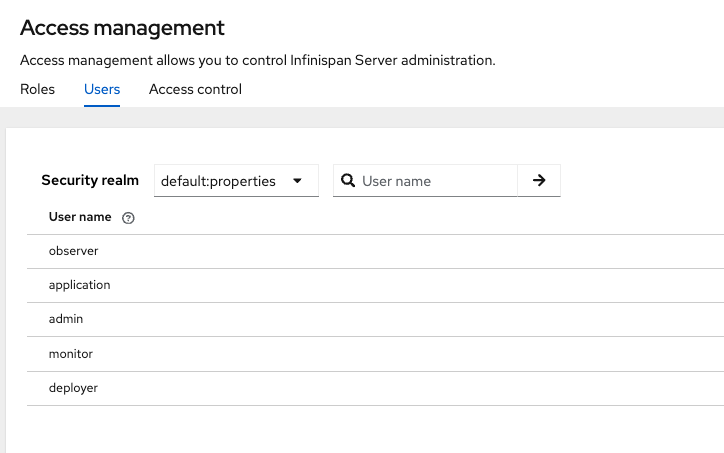
When connecting with the "observer" user, which possesses the "observer" role, it becomes apparent that this user is unable to access certain actions in the console that necessitate the "admin" role’s permissions. Examples include creating a cache, viewing connected clients, or accessing the access management functionalities.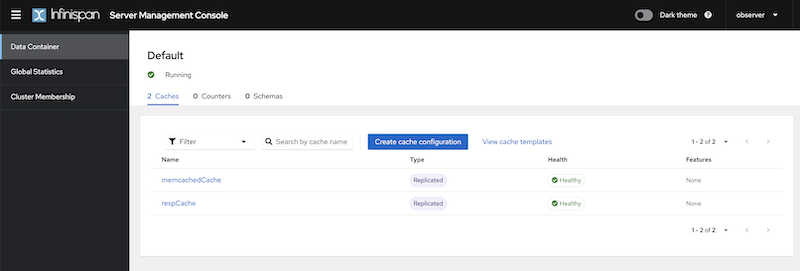
Secured Caches in Infinispan
In Infinispan, it’s possible to create caches with data manipulation permissions restricted to specific roles.
Creating a Secured Cache
For testing purposes, connect using the credentials admin/password and click on the “Create a cache” button on the Data Container page. In the cache creation wizard, after opting for all the default settings, select the "Authorization" capability and the "admin" and "monitor" roles.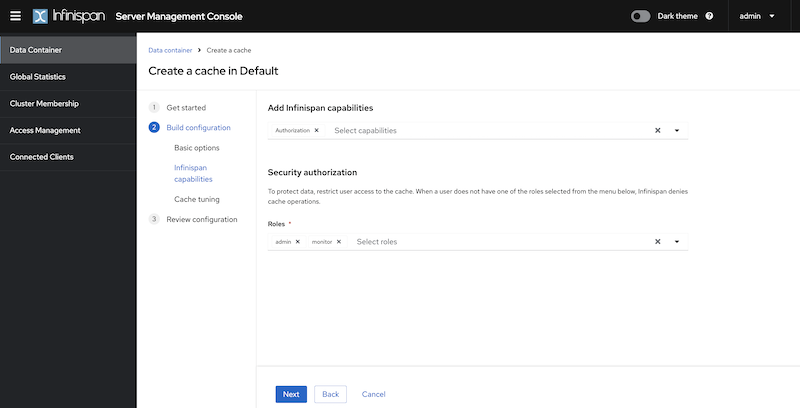
The final cache configuration will look like this:
config.yaml
distributedCache: owners: "2" mode: "SYNC" statistics: "true" encoding: mediaType: "application/x-protostream" security: authorization: enabled: "true" roles: - "admin" - "monitor"Accessing the Secured Cache
When using the "admin" user, the cache will have unrestricted access because the admin role has all the permissions. On the other hand, when connecting with the "monitor" user, which is assigned the monitor role, the cache is visible. However, as the monitor role is designed solely for monitoring and not data creation, only data associated with the cache metrics will be accessible.
For users lacking the admin or monitor role, accessing the cache from the console is not possible.
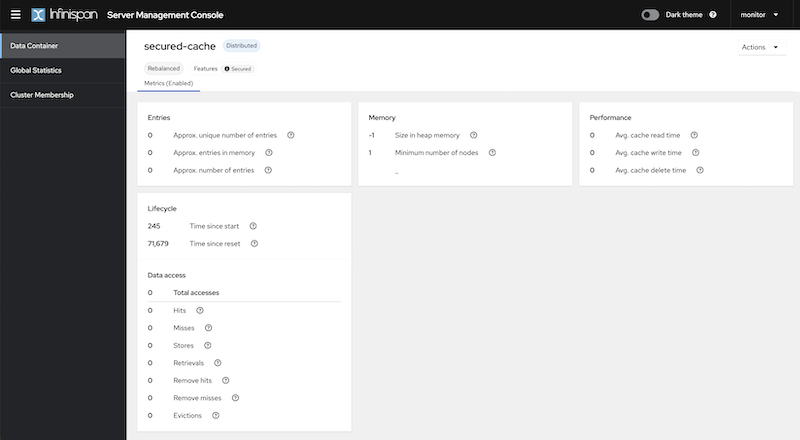
Going Further
In this article, you’ve explored the interplay of permissions, roles, Infinispan Security, and the fundamentals of secured caches. Beyond these, Infinispan Security management offers a range of additional capabilities. These include features like data encryption and advanced security, such as providing access to an entire group of users managed by systems like LDAP. This is achieved through a Principal Role Mapper, which establishes a connection between all these users and a specific role. Infinispan supports many authentication mechanisms, such as token-based authentication, which can be handled with Keycloak. Run the simple tutorial to test it.
Published at DZone with permission of Katia Aresti. See the original article here.
Opinions expressed by DZone contributors are their own.

Comments