Microservices and Its Security Patterns
Common security patterns used in most of the API architecture practices
Join the DZone community and get the full member experience.
Join For FreeWhat Are Microservices?
A microservice is a single business unit where all data and functions that are relevant to a single business purpose are put into one service.
Well, this is the general understanding of a microservice, but what do we really mean by it?
Here we can take the example of Legos, yes, you read that right, Legos.
You may remember when we used to play with Legos that we start building our whole piece from an individual Lego brick.
Just like each Lego brick is independent of each other, each microservices is independent, but come together to make something greater.
Here we can compare each microservice to a single Lego brick.

A single microservice

A complete application (containing multiple loosely coupled microservices)
Benefits of Using a Microservices Architecture
- Isolation
- Scalability
- Productivity
- Flexibility
- Faster project development
- Evolutionary
There are many more benefits and features of microservices, but we can hold them for some other time. Here we need to discuss the security patterns of microservices.
Microservices Security Patterns
Layered Defense
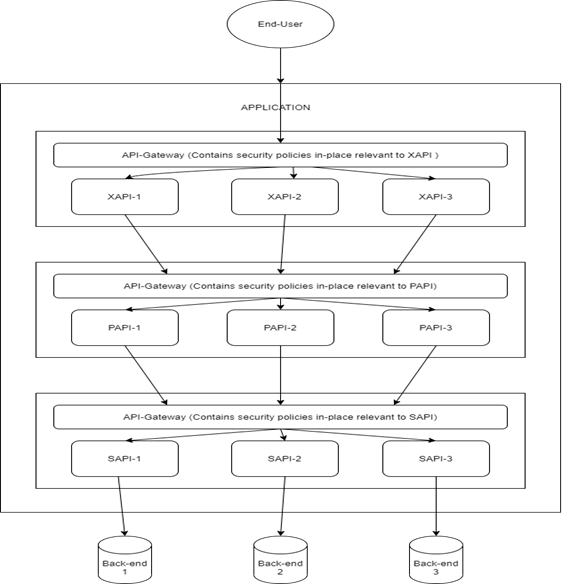
In the world of microservices, a term called “API-led architecture” is very widely used. API-led architecture means that we convert our whole application into different layers of APIs based on their functionality domain.
Here comes the concept of a layered defense. By introducing various layers into the application we are also introducing API-gateways for each layer.
Having multiple API-gateways makes it harder for a potential hacker to penetrate deep into the system due to a different set of AuthN and AuthZ policies for each layer.
Use Access and Identity Tokens
An access token is an object encapsulating the security identity of a process or thread.
It contains the security credentials for a login session and identifies the user, the user's groups, the user's privileges, and, in some cases, a particular application.
OAuth and OpenID are proper implementations of this concept.

The Most Widely Used Tokens
SAML (Security Assertion Markup Language)
SAML is an open standard that allows identity providers to pass authorization credentials to service providers. With SAML, you can use one set of credentials to log in to many different websites. It’s much simpler to manage one login per user than it is to manage separate logins for every account you have.
JWT (JSON Web Token) and the JOSE Standards Family
JWT is an open standard that defines a compact and self-contained way of securely transmitting information between parties as a JSON object. This information can be verified and trusted because it is digitally signed. JWTs can be signed using a secret (with HMAC algorithm) or a public/private key pair using RSA.

PASETO (Platform Agnostic SEcurity TOken)
PASETO is a cryptographically secure, compact, and URL-safe representation of claims intended for space-constrained environments such as HTTP Cookies, HTTP Authorization headers, and URI query parameters. A PASETO encodes claims to be transmitted in a JSON object and is either encrypted symmetrically or signed using public-key cryptography.
The key difference between PASETO and the JOSE standards family is that JOSE allows implementors and users to mix and match their own choice of cryptographic algorithms (specified by the "alg" header in JWT), while PASETO has clearly defined protocol versions to prevent unsafe configurations from being selected.

Secure by Code
Here we can discuss the core coding style/standards of APIs. Every API’s code should be written in such a way that it automatically avoids all possible vulnerabilities. If avoiding vulnerabilities is not possible, then your API should at least it avoid the top 10 vulnerabilities featured by OWASP.

Scan Dependencies
As most of the modern APIs use a containerized approach to package and deploy APIs on the cloud, it is highly important to scan all dependencies that will be used to support API operations.
Vulnerabilities found in Docker Hub images:

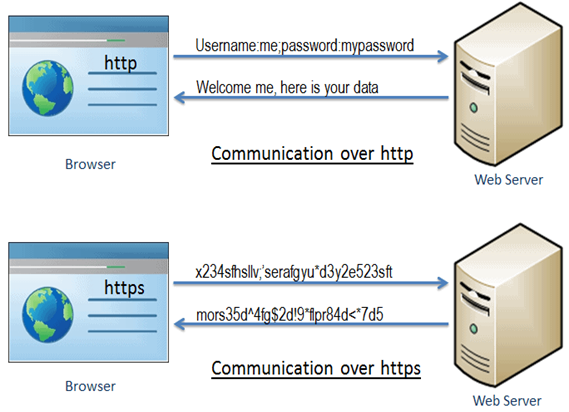
HTTPS Enforcement
SSL is a protocol for secured traffic connections. By using the SSL, HTTPS has been designed to prevent eavesdroppers and malicious users from gaining access to web application services. The HTTPS is essentially HTTP over SSL. SSL establishes an encrypted link using an SSL certificate which is also known as a digital certificate.
References
- https://owasp.org/www-project-top-ten/
- https://speakerdeck.com/rdegges/an-introduction-to-paseto-tokens
- https://developer.okta.com/blog/2019/10/17/a-thorough-introduction-to-paseto#:~:text=If%20you've%20heard%20of,Tokens%3A%20The%20Good%20Parts%E2%80%9D
- https://en.wikipedia.org/wiki/Access_token
- https://en.wikipedia.org/wiki/Security_Assertion_Markup_Language
- https://jwt.io/
- https://en.wikipedia.org/wiki/JSON_Web_Token
- https://en.wikipedia.org/wiki/HTTPS
Opinions expressed by DZone contributors are their own.

Comments