Mule Runtime Agent Use Case
Learn how to install Mule Runtime Agent and how it works in two important use cases: Maven deployment and Mule Anypoint Platform.
Join the DZone community and get the full member experience.
Join For FreeIn this article, the configuration and use of Mule Runtime Agent will be discussed. I am not going to write in detail about what Mule Runtime Agent is; on the other hand, I am going to explain how to configure the mule-agent.yml file. For more details, please read this link.
Check If You Have Runtime Agent Present
All Enterprise Mule Runtimes above 3.7 come bundled with Mule Runtime Agent. To check, just browse to the bin folder of the runtime and if you see amc_setup stuff; that means it is already present. Mule Agent is not part of the Community Runtime.
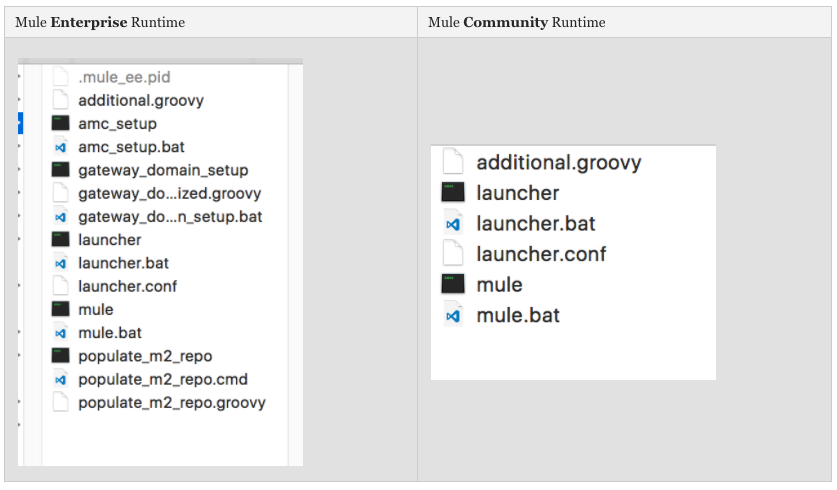
Installation
Now browse to the bin folder of the Mule Runtime and execute the following command in Mac/Linux:
> ./amc_setup -I
It will install the runtime agent and put a configuration file named mule-agent.yml in the conf directory. It looks like as shown below:
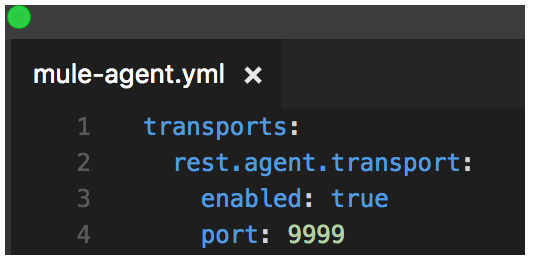
This means that when you run you Mule Runtime (./mule), the the runtime agent will be listening on port 9999, e.g. http://localhost:9999 . Feel free to change the port.
Use of Mule Runtime Agent
You can use Mule Runtime Agent in a number of important aspects. Here I would like to point out two important uses of it.
Maven Deployment
You can do a lot of things using the Mule Runtime Agent. One of the biggest things is you can deploy applications to Mule Runtime by configuring the agent in Maven. Here is a simple example:
<plugin>
<groupId>org.mule.tools.maven</groupId>
<artifactId>mule-maven-plugin</artifactId>
<version>2.0</version>
<configuration>
<deploymentType>agent</deploymentType>
<uri>http://localhost:9999</uri>
</configuration>
<executions>
<execution>
<id>deploy</id>
<phase>deploy</phase>
<goals>
<goal>deploy</goal>
</goals>
</execution>
</executions>
</plugin>
<plugin>
<groupId>org.apache.maven.plugins</groupId>
<artifactId>maven-deploy-plugin</artifactId>
<configuration>
<skip>true</skip>
</configuration>
</plugin>
Add Mule Runtime to Anypoint Platform
You can add servers to the Anypoint Platform, and all the magic happens via Mule Runtime Agent.
When you click the Add Server, it will show you a command as shown below:
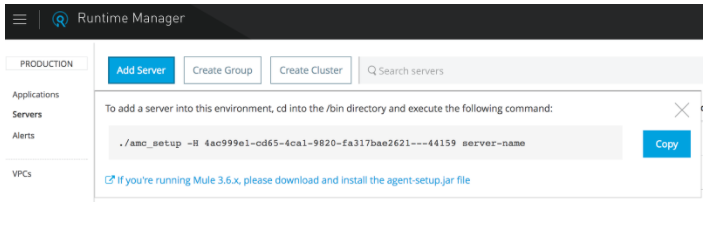
Now copy the command, open a terminal, browse to the bin folder of your Mule Runtime that you are going to add to the Anypoint Platform, and execute. On successful execution, it will CREATE (if does not exist) or OVERWRITE the mule-agent.yml file. So if you have any previous configuration done in the mule-agent.yml, it will be lost.
The file will look something like this:
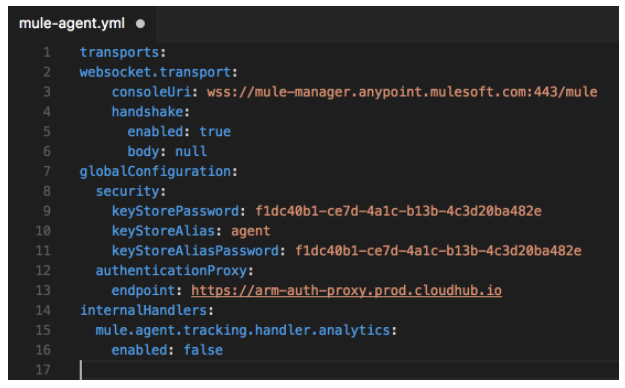
You can see that the previous configuration is lost. Now let's suppose that you want to manage the Mule Runtime from Anypoint Platform as well as you want to deploy applications to Mule Runtime using Maven. So, the desired configuration of the mule-agent.yml should be as shown below:
And that's it. You are done with the agent configuration.
Conclusion
In this article, I have shown how to configure the Mule Agent and some of its uses. Mule Agent is the core part of Mule Runtime that provides lots of other functionalities apart from the use cases cited in the article. In another article, I will try to cover those.
Opinions expressed by DZone contributors are their own.

Comments