Optimizing GitHub Access Management for Enterprises: Enhancing Security, Scalability, and Continuity with Jenkins GitHub App Authentication and Load Balancing
Jenkins GitHub App authentication with load balancing boosts security, scalability, and reliability, reducing risks in enterprise CI/CD workflows.
Join the DZone community and get the full member experience.
Join For FreeAs enterprises expand their software development practices and scale their DevOps pipelines, effective management of continuous integration (CI) and continuous deployment (CD) processes becomes increasingly important. GitHub, as one of the most widely used source control platforms, plays a central role in modern development workflows. It is critical for managing code repositories, automating tasks, and enabling collaboration among development teams.
To streamline CI/CD activities and ensure smoother operations, many organizations implement a centralized GitHub admin account that oversees repository management, integrations, and automation. This method helps maintain control and consistency across development environments. However, such an approach can introduce security vulnerabilities, scalability challenges, and operational risks, particularly when it comes to handling increasing complexity and ensuring high availability.
In this article, we will explore the risks associated with centralized GitHub management, particularly for CI/CD processes, and propose a solution that integrates Jenkins GitHub App authentication and load balancing to address these concerns. By leveraging these strategies, enterprises can enhance security, enable seamless scalability, and reduce the risk of single points of failure.
Understanding Centralized GitHub Admin Accounts in Enterprise CI/CD Workflows
A centralized GitHub admin account is often used in enterprises to manage critical GitHub repositories, workflows, and integrations across multiple teams. This single account controls access to various repositories and is responsible for executing automation tasks such as continuous integration, deployment, and testing. With centralized administration, it becomes easier to enforce security policies, monitor activity, and apply configuration updates uniformly.
However, this approach introduces several challenges:
1. Security Risks
- Single point of access: Centralized admin accounts provide a single point of entry for all integrations and access to repositories. If compromised, attackers can potentially gain access to sensitive code, secrets, and integrations.
- Credential management: Centralized management typically requires multiple automation tools and systems to authenticate using shared credentials, increasing the risk of credential theft or misuse.
2. Scalability Limitations
- Growing demands: As an organization scales, managing access for an increasing number of repositories and integrations using a single account becomes cumbersome. It may lead to slower response times, more complex configuration management, and difficulties in maintaining efficient workflows.
- Overloaded admin account: When a single admin account is tasked with managing numerous tasks across a large enterprise, it can be overwhelmed, leading to delays in actions and a lack of flexibility.
3. Operational Continuity Concerns
- Single point of failure: If the centralized admin account encounters issues (e.g., credential errors, revoked access, or network failures), the entire CI/CD pipeline may be disrupted, affecting all dependent workflows.
- Risk of human error: As the account grows in responsibility, human errors in managing repository configurations or automation scripts can have widespread implications across multiple development teams.
Mitigating the Risks With Jenkins GitHub App Authentication
To address these risks, enterprises can adopt a more robust and scalable approach to managing GitHub access, using Jenkins GitHub App Authentication as a primary method of securing interactions between GitHub and Jenkins, the popular CI/CD automation tool.
How Jenkins GitHub App Authentication Works
Jenkins GitHub App Authentication allows Jenkins to securely integrate with GitHub by using an application-specific OAuth token rather than shared credentials. This method provides several benefits:
- Improved security: Instead of relying on a centralized admin account, Jenkins uses GitHub’s App-based authentication, which gives each Jenkins instance its own token with tightly scoped permissions. This reduces the risk of a single point of compromise and allows fine-grained control over access to GitHub repositories.
- Granular permissions: With GitHub Apps, access rights can be restricted to specific repositories, branches, or even specific actions (such as push events or pull request interactions). This minimizes unnecessary access and limits the attack surface.
- Reduced dependency on centralized credentials: GitHub App authentication eliminates the need for central administration accounts to manage credentials across multiple systems, significantly enhancing security posture.
Benefits of Jenkins GitHub App Authentication
- Seamless integration: Jenkins GitHub App authentication streamlines the communication between Jenkins and GitHub, reducing setup complexity and ensuring smoother workflows.
- Centralized control with distributed management: By leveraging GitHub Apps, organizations can distribute authentication responsibilities across different Jenkins instances, avoiding the bottleneck of a single centralized admin account.
Example: Adding GitHub App Credentials to Jenkins Credential Store
Below is an example of how to add GitHub App credentials to the Jenkins credential store for secure authentication.
Step 1: Create a GitHub App
First, create a GitHub App in your GitHub organization. Follow these steps:
- Navigate to your GitHub organization.
- Go to Settings > Developer Settings > GitHub Apps and click New GitHub App.
- Fill in the details for the app and configure the necessary permissions, such as access to repositories, pull requests, and more.
- Application details:
- GitHub App name: Choose a name for your GitHub App (e.g.,
Jenkins GitHub Integration). - Homepage URL: Provide a homepage URL (e.g.,
https://jenkins.example.com). - Callback URL: This is the URL where GitHub will send requests to Jenkins. For now, you can leave this blank.
- Webhook URL: This URL is used to send events from GitHub to Jenkins (typically,
http://<jenkins-url>/github-webhook/).
- GitHub App name: Choose a name for your GitHub App (e.g.,
- Permissions:
- Under Repository permissions, select the required permissions:
- Repository contents (Read and Write): For Jenkins to access the contents of your repositories.
- Pull requests (Read & Write): If you want Jenkins to trigger builds on PR events.
- Commit statuses (Read & Write): To update commit statuses in GitHub.
- Under Organization permissions, choose whether the app should have access to the entire organization or just specific repositories.
- Under Repository permissions, select the required permissions:
- Application details:
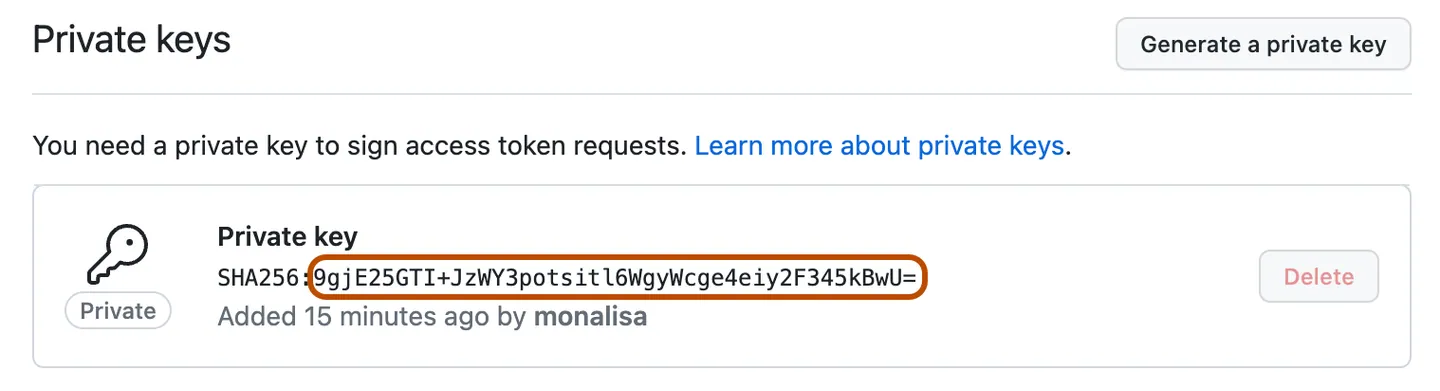
- After creating the app, generate a Private Key and download it. You will need this private key for Jenkins authentication.
![Generate a private key]()
- After creating the app, you will be prompted to install it either on individual repositories or on an entire organization. Select the appropriate repositories or organization.
Step 2: Install the GitHub Plugin in Jenkins
- In Jenkins, go to Manage Jenkins > Manage Plugins.
- Search for and install the GitHub Branch Source plugin. This plugin enables Jenkins to authenticate with GitHub using GitHub Apps.
Step 3: Add the GitHub App Credentials to Jenkins
- In Jenkins, go to Manage Jenkins > Manage Credentials.
- Choose the appropriate domain (or create a new one) and click Add Credentials.
- Select GitHub App as the credential type.
- Fill in the necessary details:
- GitHub App name: This is the name of the GitHub App you created earlier.
- GitHub App ID: You can find this ID on the GitHub App settings page.
- Private Key: Upload the private key you downloaded earlier when creating the GitHub App.
- Installation ID: This is provided when you install the GitHub App on your repositories or organization.
- Click Test Connection to verify that Jenkins can connect to GitHub using the credentials you just added.
Step 4: Configure Jenkins Job to Use GitHub App Credentials
- In your Jenkins job configuration, navigate to the Source Code Management section.
- Select Git and enter your repository URL.
- Choose the GitHub App credentials you created earlier from the Credentials dropdown.
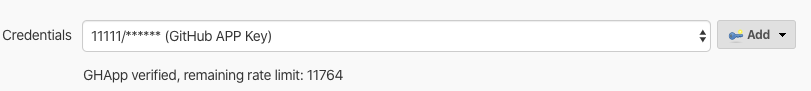
By following these steps, Jenkins will securely authenticate by generating a temporary authentication token for GitHub using the GitHub App credentials, removing the need for a centralized admin account, and the authentication token will be valid only for one hour. Jenkins will also display the remaining rate limit for the GitHub app.
Expanding on the Benefits of Temporary Tokens and GitHub App Private Key Security
Temporary Tokens for Enhanced Security
One of the key benefits of using Jenkins GitHub App authentication is the use of temporary tokens. When Jenkins requests access to GitHub, it does so through a temporary token generated by the GitHub App. This temporary token has the following advantages:
- Reduced exposure: Since these tokens are short-lived (e.g., they expire after a few hours or minutes), they reduce the window of opportunity for attackers to exploit compromised credentials. This makes it more difficult for malicious actors to use stolen credentials to gain access to GitHub repositories.
- Automated token refresh: Jenkins automatically manages the renewal of these temporary tokens, ensuring that the authentication process remains seamless without requiring manual intervention.
- Granular permissions: The temporary token inherits the same granular permissions as the GitHub App, so it has limited access to only the repositories and actions that the app is permitted to perform.
GitHub App Private Key Security
The private key used by the GitHub App is a critical element of the authentication process. Here’s why managing the GitHub App private key securely is paramount:
- High sensitivity: The private key is the only means by which Jenkins can authenticate to GitHub via the GitHub App. If compromised, an attacker could potentially impersonate the app and access GitHub repositories.
- Minimal exposure: The private key should never be exposed to the public or stored in insecure locations. To ensure its security, Jenkins stores the private key in its internal credential store, where access is tightly controlled and monitored.
- Encryption at rest: Jenkins encrypts credentials stored in its credential store, including the GitHub App private key. This ensures that even if the Jenkins instance is compromised, the sensitive keys remain protected.
By securing the private key and ensuring it is never exposed in logs or configuration files, enterprises can significantly mitigate the risk of unauthorized access to their GitHub repositories.
Scaling GitHub Access With Load Balancing for GitHub Apps
In addition to securing access through Jenkins GitHub App Authentication, enterprises can improve the scalability and resilience of their CI/CD pipelines by employing load balancing for GitHub Apps. This strategy distributes traffic and tasks across multiple GitHub Apps and Jenkins instances to prevent bottlenecks and single points of failure.
How Load Balancing Works
Load balancing involves distributing the workload of managing GitHub access among several instances of Jenkins and multiple GitHub Apps, rather than depending on a single instance. In a typical load-balanced setup:
- Multiple Jenkins instances are configured to manage different repositories or workflows.
- Each Jenkins instance integrates with different GitHub Apps, ensuring that tasks like build triggers, deployment, and testing are not confined to one GitHub App.
Benefits of Load Balancing
- Scalability: As an organization scales, new Jenkins instances and GitHub Apps can be added seamlessly to handle the increased volume of CI/CD activities. This ensures that the pipeline remains fast and responsive even as the number of repositories and integrations grows.
- Fault tolerance: Load balancing enhances resilience by distributing traffic. If one Jenkins instance or GitHub App experiences issues, the remaining instances can continue managing operations without disruption.
- Optimized performance: By distributing tasks evenly across multiple instances, the CI/CD process becomes more efficient, with reduced response times and minimized risks of overloading any single component.
Strategic Benefits and Implementation
1. Enhanced Security
By using Jenkins GitHub App authentication, enterprises can ensure that each Jenkins instance has its own authentication token with fine-grained permissions, drastically reducing the attack surface and improving the overall security model.
2. Improved Scalability
Load balancing and distributed GitHub App management make it easier to scale GitHub access as the organization grows, ensuring that new repositories and automation tasks can be efficiently handled by multiple instances without overloading a centralized account.
3. Increased Operational Continuity
By spreading the management of GitHub access across multiple instances and apps, enterprises can mitigate the risks of a single point of failure. This ensures that even if one part of the system encounters an issue, the rest of the CI/CD pipeline remains intact and operational.
4. Flexible and Efficient Management
With a distributed model, teams can manage their own GitHub Apps and Jenkins instances, giving them more control over their workflows while maintaining overall enterprise-level security and scalability.
Conclusion
As enterprises scale their development practices and adopt more complex CI/CD processes, ensuring secure, scalable, and resilient management of GitHub access becomes increasingly important. By replacing centralized GitHub admin accounts with Jenkins GitHub App authentication and implementing load balancing across multiple GitHub Apps, enterprises can significantly reduce security risks, improve scalability, and enhance operational continuity. This combination of strategies ensures a more secure and efficient workflow, capable of handling the demands of modern software development at scale.
Opinions expressed by DZone contributors are their own.

Comments