PGP-Pretty Good Privacy Using Mule
In this article, we will discuss on how to use one of the most popular data privacy tool with Mule ESB.
Join the DZone community and get the full member experience.
Join For FreeIn today's IT world, data privacy is very important, especially, when it comes to sharing sensitive data over the network.
In this article, we will discuss on how to use one of the most popular data privacy tool with Mule ESB. Mule does support a wide variety of security strategies, PGP-Pretty Good Privacy is one of the most popular and secure encryption and decryption mechanism.
What Is PGP?
PGP - Pretty Good Privacy, created by Phil Zimmermann, is a data encryption and decryption program for data privacy communicated between two parties.
PGP works by encrypting a message using a public key that’s tied to a specific user; when that user receives the message, they use a private key that is known only to them to decrypt it.
How Secure Is PGP?
While it is impossible to say any encryption methodology is safe and secure, PGP is generally considered as being extremely safe and secure. Bruce Schneier, an internationally renowned security technologist, stated PGP is the encryption methodology that is closest to get military-grade encryption and there are no practical weaknesses.
How PGP Can Be Used With Mule and Where?
Mule supports security with Anypoint Enterprise Security module. First thing, we need to make sure to install the Anypoint Enterprise Security module in Anypoint Studio i.e., Mule IDE. In order to add Security module to Anypoint Studio, please follow the instructions from here
Once the Anypoint Enterprise Security module is installed, you should see a new palette group called Security in the studio like this
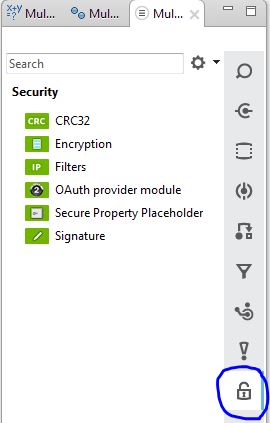
Encryption Module
Mule can encrypt the entire payload or specific parts of the payload depending upon the encryption strategy. Mule supports 3 encryption strategies;
Encryption Strategy Name | Characteristics |
JCE Encrypter (Default) | Encrypts Stream, byte[] or String type of payload |
XML Encrypter | Encrypts String type of payload Encrypts full payload or partial using xpath |
PGP Encrypter | Encrypts Stream, byte[] or String type of payload Adds the processing overload |
Note: PGP is generally considered as being extremely safe and secure over JCE and XML Encrypters.
Let’s consider a small use case to demonstrate on how to implement PGP encryption in mule with ‘Encryption Processor’
Use case: In this article, we will be implementing a flow which will fetch data from a database table and then send the data to a queue in Active MQ, encrypt the data before sending it to queue.
Components used in this use case:
HTTP | To trigger the flow |
Database | Fetch the data from database |
JMS | Enqueue/Dequeue messages |
Encryption | PGP Encryption to encrypt the data |
Object to Byte Array | Convert payload object into byte array for PGP to process |
Byte Array to Object | Convert payload from byte array to object after PGP process |
For Each | Iterate over the database results |
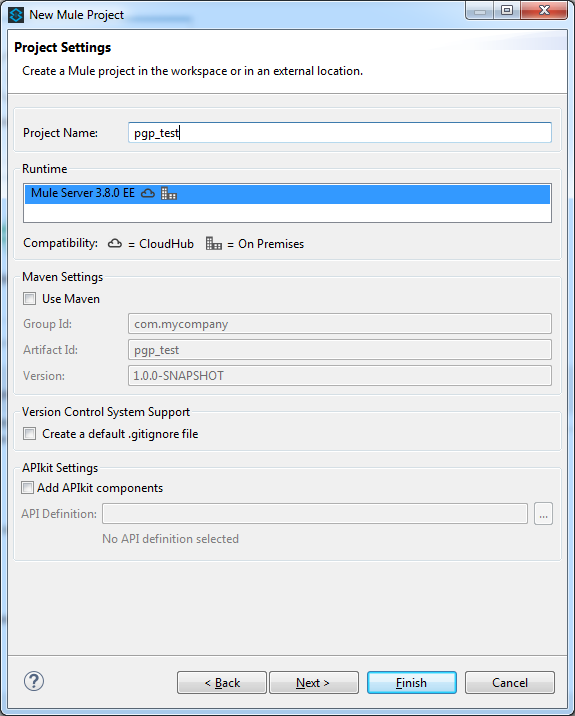
- Create new project viz., pgp_test.
- Create project in Anypoint Studio, by selecting the top menu bar.
- Select File > New > Mule Project.
After project is created, drag and drop the following components and transformers from the palette in the same order onto the canvas:
1. HTTP | URL : http://localhost:8081/pgptest |
2. Database | Configure to select data from a simple table, something like Employee table in your local/remote db |
3. For Each | |
4. Object to Byte Array | |
5. Encryption | Refer next slide/page |
6. JMS | Point to a queue viz., ‘employee’ in your local Active MQ |
And the flow should look like below:
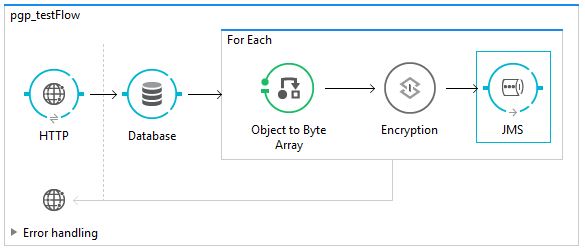
Let’s see what is required to configure the ‘Encryption’ module in detail:
- Configure the Encryption module to use the PGP_ENCRYPTER as shown below.
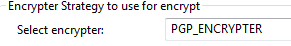
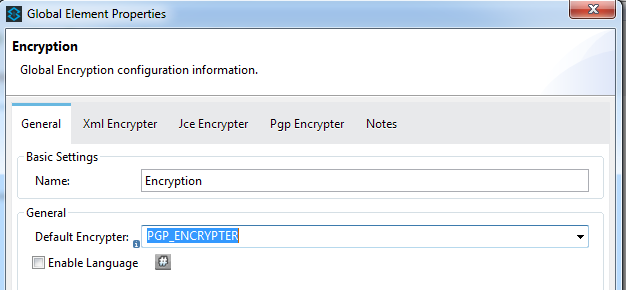
- Add a Global Encryption Configuration by clicking on the Connector Configuration + icon under Basic Settings and set the value to PGP_ENCRYPTER for Default Encrypter as shown below:
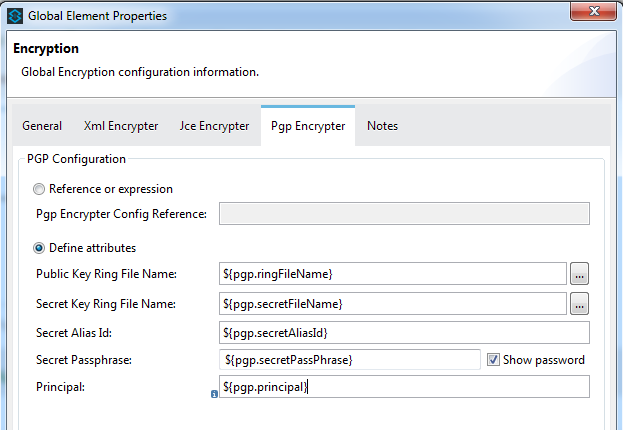
- Select the ‘Pgp Encrypter’ tab and select the ‘Define attributes’.
What is a key ring? In secure data-transmission, a key ring consists of a public key and its corresponding private key both of which are required to read the data.
You can use my Public Key Ring and Secret Key Ring files and use them in the flow. If you intend to do so, set the rest of the values as follows:
Secret Alias Id : 8923421754335606047
Secret Passphrase : mulepgp
Principal : mulepgpIf you prefer to generate your own key ring files, you can make use the gpg command-line utility.
- GPG Keychain Access for Mac OS
- Gpg4win for Windows
This screenshot shows how the keys were generated using the gpg command from Windows. Note that the pubring.gpg and secring.gpg key files will be created in a hidden directory called `gnupg` under the user home directory. On Windows, this will be in:
C:\Users\<username>\AppData\Roaming\gnupg.The Principal will be the USER-ID which is a combination of the Real Name, Email Address, and Comment. To keep it simple, you can just use choose a simple Real Name and leave email and comment blank.
In my example, I simply set the Real Name to `mulepgp` and the Secret Passphrase to `mulepgp`.
Determining the numeric value for the `Secret Alias Id` is not obvious. The GPG utility does not show this numeric value. The best way to derive this is by letting Mule give you some clues. Put any random number initially for the `Secret Alias Id` and run it to let Mule throw an error on purpose. In the exception thrown from the console output, it will show you a message with the keys you can use.
Thanks to Mariano Gonzales for the above tips.
Okay….. We did talk too much isn’t it?
Now it’s time to test the talk.
- Run the flow as Mule Application….. Check the console for successful application deployment.

- Open Postman or something similar then type the URL,
Notice the console messages for before and after encryption, that’s it guys…. It’s pretty simple to encrypt message using PGP in mule… isn’t it?
http://localhost:8081/pgptest with GET method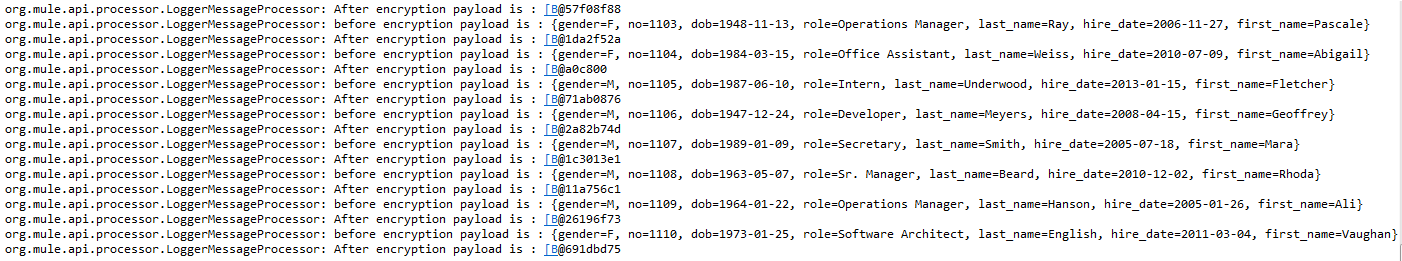
The complete code of this article can be downloaded from here.
Opinions expressed by DZone contributors are their own.

Comments