Real-Time Fraud Detection Using AI and Machine Learning
Real-time fraud detection using AI and ML techniques like behavioral analytics, device fingerprinting, and risk scoring.
Join the DZone community and get the full member experience.
Join For FreeProblem Statement
With the rapid increase of online applications in industries such as finance, e-commerce, and social media, the frequency and sophistication of fraud attempts have surged. E-commerce apps face challenges like unauthorized transactions, fake bank account creation, and bot-driven attacks, leading to financial losses, reputational harm, and decreased user trust.
Current fraud detection methods often rely on post-event analysis, failing to address the need for real-time mitigation. The critical problem is to develop a system capable of detecting and preventing fraud as it occurs while balancing performance, user experience, and data privacy.
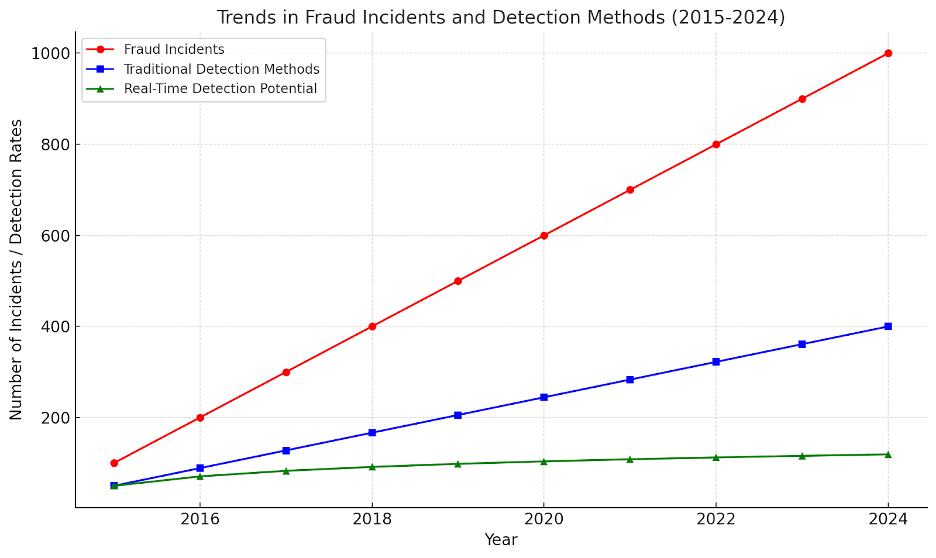
Graph showing trends in fraud incidents and detection methods from 2015 to 2024. It illustrates:
- Red line – The growing number of fraud incidents over time.
- Blue line – The plateau in the effectiveness of traditional detection methods.
- Green line – The upward trend in the potential of real-time fraud detection systems, keeping pace with the increasing sophistication of fraud.
In the U.K., nearly 1.4 million thefts were attributed to fraudsters in the first half of 2023, occurring at a rate of one every 12 seconds.
AI/ML Techniques for Real-Time Fraud Detection
Behavioral Analytics
Behavioral analysis has emerged as a cornerstone of real-time fraud detection in e-commerce applications. E-commerce apps can detect anomalies that indicate fraudulent activity by analyzing user behavior patterns.
Unlike static rule-based systems, behavioral analysis relies on machine learning algorithms and behavioral biometrics to identify subtle deviations in user actions, such as typing speed, touch patterns, and navigation sequences.
For instance, legitimate users often follow predictable paths when interacting with an app (e.g., login → search → purchase). Fraudulent actors or bots, on the other hand, may exhibit erratic or overly systematic behavior. Behavioral analysis systems monitor these patterns in real-time, leveraging features like:
- Behavioral biometrics – Monitoring unique user traits such as keystrokes, touch pressure, or swipe speed
- Session analysis – Tracking user actions during a session to detect deviations from normal usage patterns
- Continuous authentication – Continuously validating user identity based on behavioral patterns instead of relying solely on a one-time login
Device Fingerprinting
Device fingerprinting for real-time fraud detection leverages AI/ML techniques to uniquely identify devices and track their behavior. By extracting both static attributes (like device model, OS version, and screen resolution) and dynamic features (such as IP address changes or login times), machine learning algorithms like Random Forests and XGBoost classify devices as legitimate or fraudulent.
Anomaly detection techniques, such as Isolation Forest and Local Outlier Factor (LOF), help identify unusual device behavior by evaluating deviations from typical patterns. Pattern recognition methods like Markov Chains and Dynamic Time Warping are used to analyze the sequence of actions performed by a device, detecting irregular behaviors over time that might indicate fraud.
Real-time fraud detection systems continuously improve through adaptive learning. Semi-supervised learning enables models to improve by using both labeled and unlabeled data, while reinforcement learning allows systems to learn from feedback and adapt to new fraud tactics. These advanced AI/ML techniques allow device fingerprinting systems to evolve in response to emerging threats, ensuring that fraud detection remains accurate and dynamic. By combining these techniques, e-commerce apps can detect suspicious devices and behavior with high accuracy in real-time, effectively mitigating fraud risks.
- XGBoost – An advanced gradient boosting algorithm known for high performance in classification and regression tasks
- Gradient boosting – A machine learning technique that sequentially builds decision trees to correct errors made by previous models
- Regularization – A technique used to avoid overfitting by adding a penalty to the model complexity
- Tree pruning – The process of removing branches from decision trees to enhance performance and prevent overfitting
- Parallel processing – The ability to perform multiple computations at once, speeding up model training
- Second-order approximation – An optimization approach that uses both first and second derivatives of a loss function for faster convergence
Real-Time Risk Scoring
Real-time risk scoring evaluates the likelihood of fraudulent activity during a user session or transaction. It assigns a dynamic risk score based on behavioral patterns, device information, geolocation, and historical data.
How it works:
- Data collection – Captures user actions (e.g., login time, device, location)
- Analysis – Compares against normal behavior and known fraud patterns
- Scoring – Assigns a risk score (e.g., 0-100, with higher values indicating higher risk)
- Action – Based on the score, triggers actions like flagging, additional verification, or blocking
Document Verification With AI
AI-driven document verification automates identity checks by analyzing uploaded IDs (e.g., passports and driver’s licenses) in real time. It uses OCR to extract data, validates authenticity, and employs liveness detection to match user selfies with ID photos.
Below are examples of apps that are using AI for document verification:
- Revolut – Verifies user identity for account creation and KYC compliance
- Airbnb – Confirms host and guest identities to ensure platform trust
- Uber – Validates driver licenses and identities for new driver registrations
- PayPal – Ensures secure onboarding by verifying customer IDs
This technology enhances security, speeds up onboarding, and prevents fraud.
Implementation Challenges and Future Trends in AI-Powered Fraud Detection
| category | implementation challenges |
|---|---|
|
Data Privacy and Security |
AI/ML models require large volumes of data for training, raising concerns about data privacy. E-commerce app developers must ensure compliance with regulations such as GDPR and CCPA. |
|
False Positive |
Overly sensitive models can generate false positives, inconveniencing legitimate users. Balancing precision and recall is essential. |
|
Scalability |
Fraud detection models must handle high volumes of transactions in real time without compromising app performance. |
|
Adversarial Attacks |
Fraudsters can deploy adversarial techniques to deceive AI models, highlighting the need for continuous model retraining and improvement. |
| category | future trends in ai-powered fraud detection |
|---|---|
|
Federated Learning |
Federated learning enables AI models to be trained across multiple devices without sharing raw data, addressing privacy concerns while leveraging large-scale behavioral data. |
|
Explainable AI (XAI) |
XAI techniques make AI decision-making transparent, enhancing trust in fraud detection systems and ensuring compliance with regulatory requirements. |
|
Integration with Blockchain |
Combining AI/ML with blockchain can create immutable records of transactions, adding an extra layer of security and traceability. |
|
Cross-Platform Threat Intelligence |
Sharing fraud patterns across apps and platforms enables faster detection and response to emerging threats. |
Conclusion
The integration of AI and ML in e-commerce applications is improving fraud detection, offering real-time, adaptive, and highly effective solutions. As cyber threats evolve, so must our detection systems. We can build safer, more secure online ecosystems by addressing challenges and embracing emerging technologies.
Thanks for reading this! You can connect with us on Swapnil’s, Vikesh’s, and Milav's LinkedIn!
Opinions expressed by DZone contributors are their own.

Comments