Simplify Authorization in Ruby on Rails With the Power of Pundit Gem
Learn how to simplify access control in Ruby on Rails products with Pundit. Guide to policy-based authorization to manage user roles and permissions seamlessly.
Join the DZone community and get the full member experience.
Join For FreeHi, I'm Denis, a backend developer. I’ve been recently working on building a robust all-in-one CRM system for HR and finance, website, and team management. Using the Pundit gem, I was able to build such an efficient role-based access system, and now I'd like to share my experience.
Managing authorization efficiently became a crucial challenge as this system expanded, requiring a solution that was both scalable and easy to maintain. In Ruby on Rails, handling user access can quickly become complex, but the Pundit gem.
In this article, I will explore how Pundit simplifies authorization, its core concepts, and how you can integrate it seamlessly into your Rails project. By the end of this guide, you'll hopefully have a clear understanding of how to use Pundit effectively to manage user permissions and access control in your Rails applications.
Why Choose Pundit for Authorization?
Pundit is a lightweight and straightforward authorization library for Rails that follows the policy-based authorization pattern. Unlike other authorization libraries, such as CanCanCan, which rely on rule-based permissions, Pundit uses plain Ruby classes to define access rules.
Some key benefits of Pundit include:
- Simplicity: Uses plain old Ruby objects (POROs) to define policies, making it easy to read and maintain.
- Flexibility: Provides fine-grained control over permissions, allowing complex authorization rules to be implemented easily.
- Scalability: Easily extendable as your application grows without adding unnecessary complexity.
- Security: Encourages explicit authorization checks, reducing the risk of unauthorized access to resources.
Unlike role-based systems that define broad roles, Pundit allows for granular, action-specific permission handling. This approach improves maintainability and prevents bloated permission models.
Pundit vs. CanCanCan
Pundit and CanCanCan are both popular authorization libraries for Rails, but they take different approaches:
| Feature | Pundit | CanCanCan |
|---|---|---|
| Authorization Method | Policy-based (separate classes for each resource) | Rule-based (centralized abilities file) |
| Flexibility | High (you define logic explicitly) | Medium (relies on DSL rules) |
| Complexity | Lower (straightforward Ruby classes) | Higher (complex rules can be harder to debug) |
| Performance | Generally better for large applications | Can slow down with many rules |
If you need explicit, granular control over access, Pundit is often the better choice. If you prefer a more declarative, centralized way of defining permissions, CanCanCan might be suitable.
Getting Started With Pundit
Before diving into using Pundit, it’s important to understand how it fits into Rails’ authorization system. By relying on clear, independent policies, Pundit keeps your code maintainable and easy to follow. Now, let’s walk through the setup process and see how you can start using Pundit to manage access control in your application.
1. Installing Pundit Gem
To begin using Pundit in your Rails project, add it to your Gemfile and run bundle install:

Then, install Pundit by running:

This command generates an ApplicationPolicy base class that will be used for defining your policies. This base class provides default behavior for authorization checks and serves as a template for specific policies you create for different models.
2. Defining Policies
Policies in Pundit are responsible for defining authorization rules for a given model or resource. A policy is simply a Ruby class stored inside the app/policies/ directory. For example, let’s generate a policy for a Post model:

This generates a PostPolicy class inside app/policies/post_policy.rb. A basic policy class looks like this:
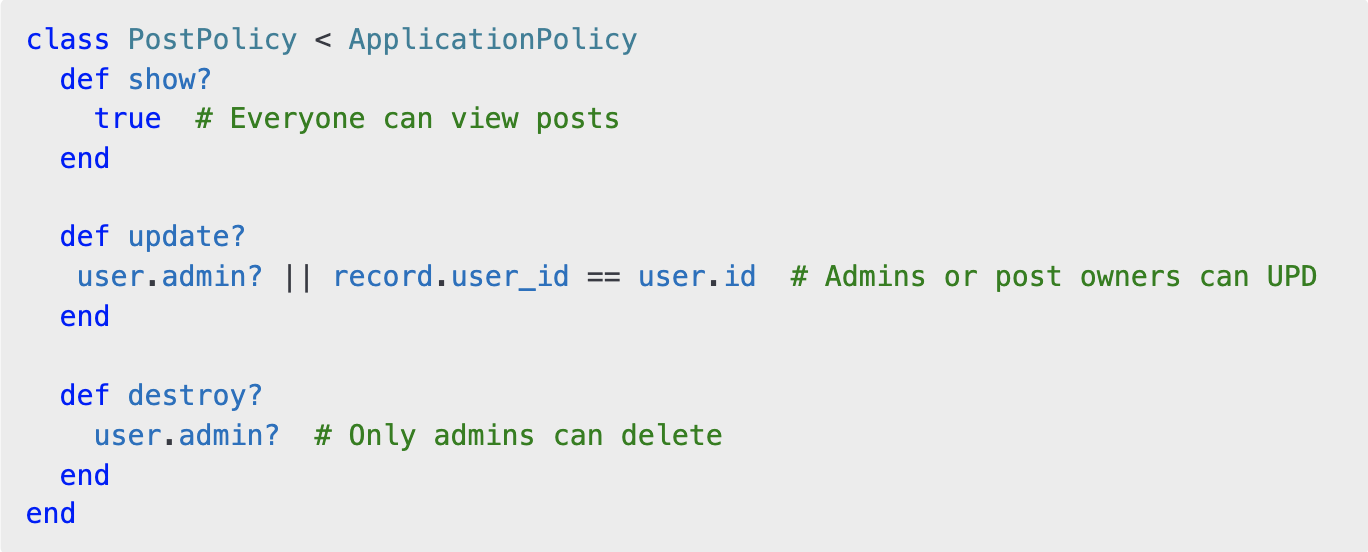
Each method defines an action (e.g., show?, update?, destroy?) and returns true or false based on whether the user has permission to perform that action. Keeping policy methods small and specific makes them easy to read and debug.
3. Using Policies in Controllers
In your controllers, you can leverage Pundit's authorize method to enforce policies. Here’s how you can integrate Pundit into a PostsController:
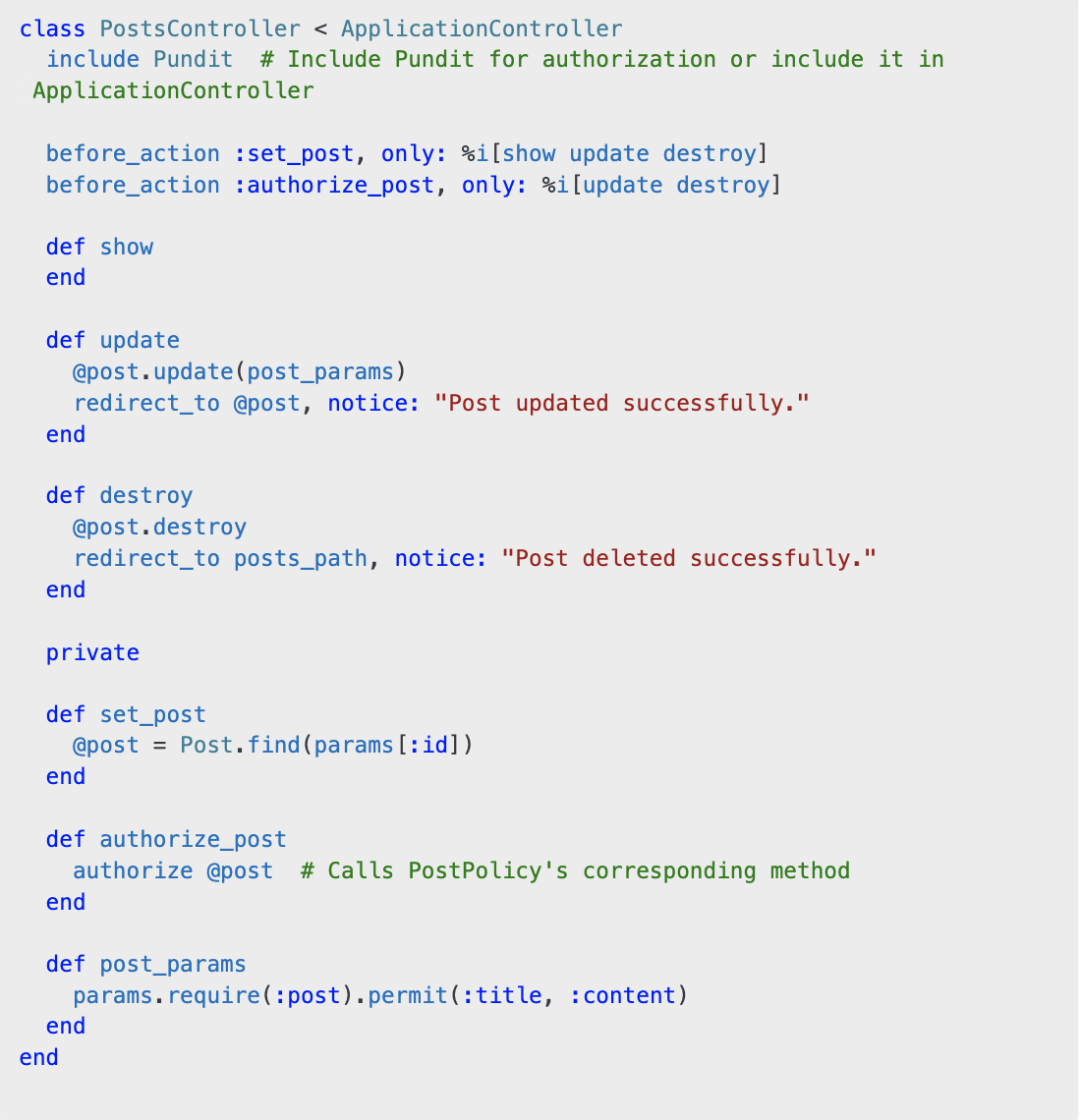
Here, authorize @post automatically maps to PostPolicy and calls the appropriate method based on the controller action. This ensures authorization is consistently checked before performing actions on a resource.
4. Handling Authorization at the View Level
Pundit provides the policy helper, which allows you to check permissions in views:
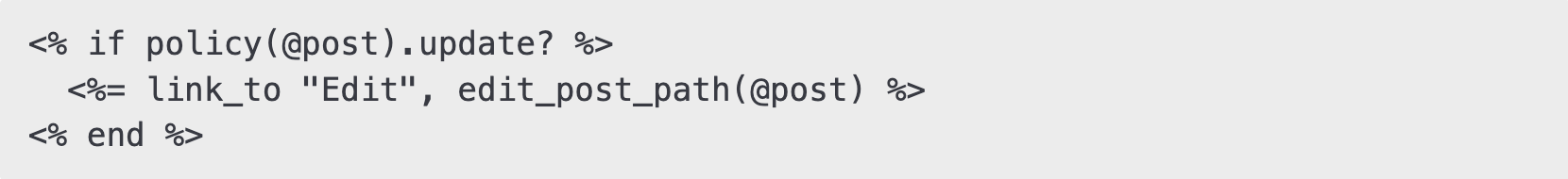
You can also use policy_scope to filter records based on permissions:

This ensures that only authorized data is displayed to the user, preventing unauthorized access even at the UI level (but data loading with policy scope is recommended on the non-view level).
5. Custom Scopes for Querying Data
Pundit allows you to define custom scopes for fetching data based on user roles. Modify PostPolicy to include a Scope class:
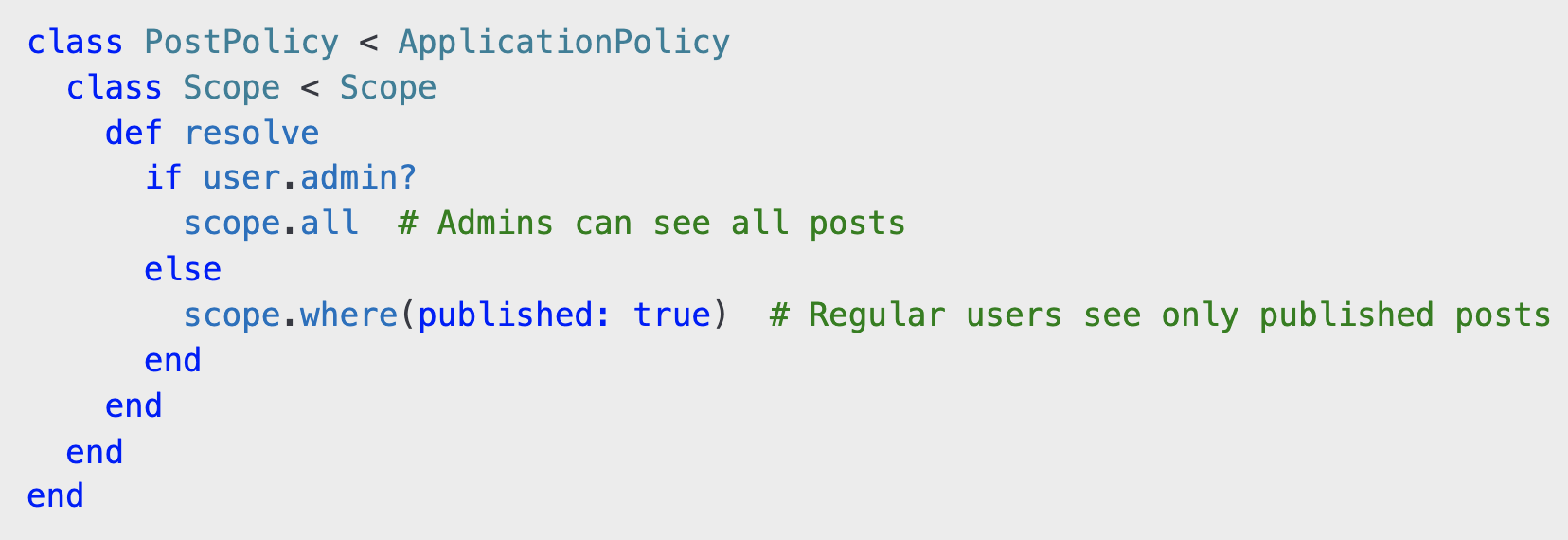
In the controller:

This ensures users only see records they are authorized to view, adding an extra layer of security and data privacy. In our experience, it is often necessary to load data from another scope, and then you need to specify additional parameters when loading data from the policy scope:
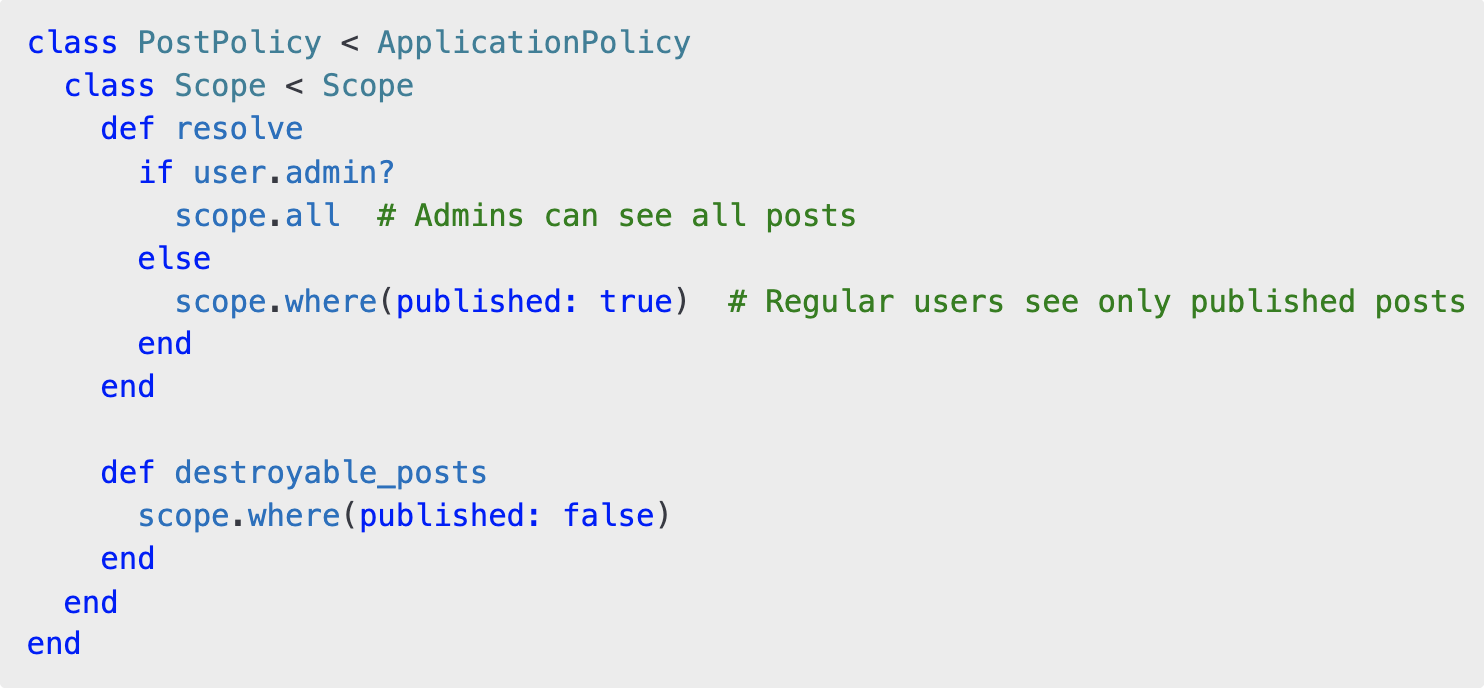
Also, when you have several scopes for one policy, you can specify which one you need (because by default, the scope uses the "resolve" method for scope). For example, in your policy, you have:

And you can call it:

6. Rescuing a Denied Authorization in Rails
It's important not only to verify authorization correctly but also to handle errors and access permissions properly. In my implementation, I used role-based access rules to ensure secure and flexible control over user permissions, preventing unauthorized actions while maintaining a smooth user experience. I won’t be dwelling a lot upon them in this article, as I described them in detail in one of my recent CRM overviews.
Pundit raises a Pundit::NotAuthorizedError you can rescue_from in your ApplicationController. You can customize the user_not_authorized method in every controller.
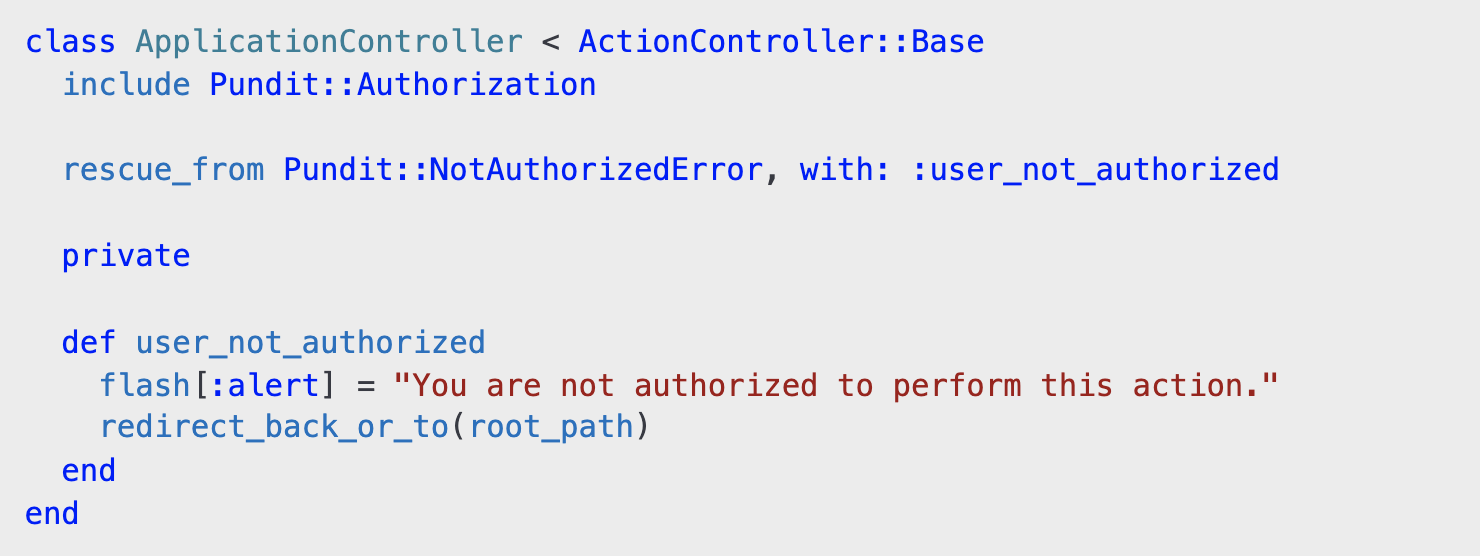
So you can also change the behavior of your application when access is denied.
Best Practices for Using Pundit
To get the most out of Pundit, it's essential to follow best practices that ensure your authorization logic remains clean, efficient, and scalable. Let’s explore some key strategies to keep your policies well-structured and your application secure.
1. Сreating a Separate Module: A Clean and Reusable Approach
A well-structured application benefits from modularization, reducing repetitive code, and improving maintainability. Module encapsulates authorization logic, making it easy to reuse across multiple controllers. Let’s break it down: The load_and_authorize_resource method is a powerful helper that:
- Loads the resource based on controller actions.
- Authorizes the resource using Pundit.
- Automatically assigns the loaded resource to an instance variable for use in the controller actions.
Example:
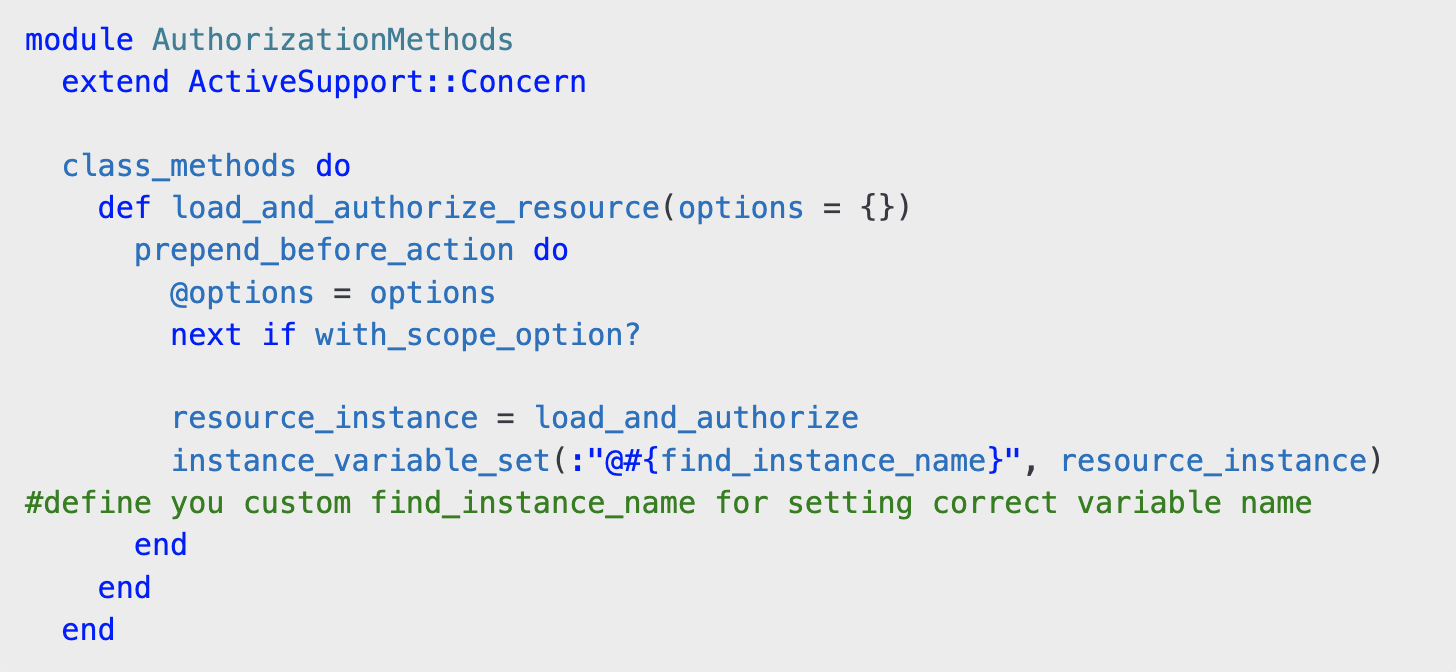
This means that controllers no longer need to explicitly load and authorize records, reducing boilerplate code. For example, the load_and_authorize method dynamically loads records based on controller actions:
index: Loads all records.new/create: Initializes a new record.- Other actions: Fetches a specific record using a flexible find strategy.
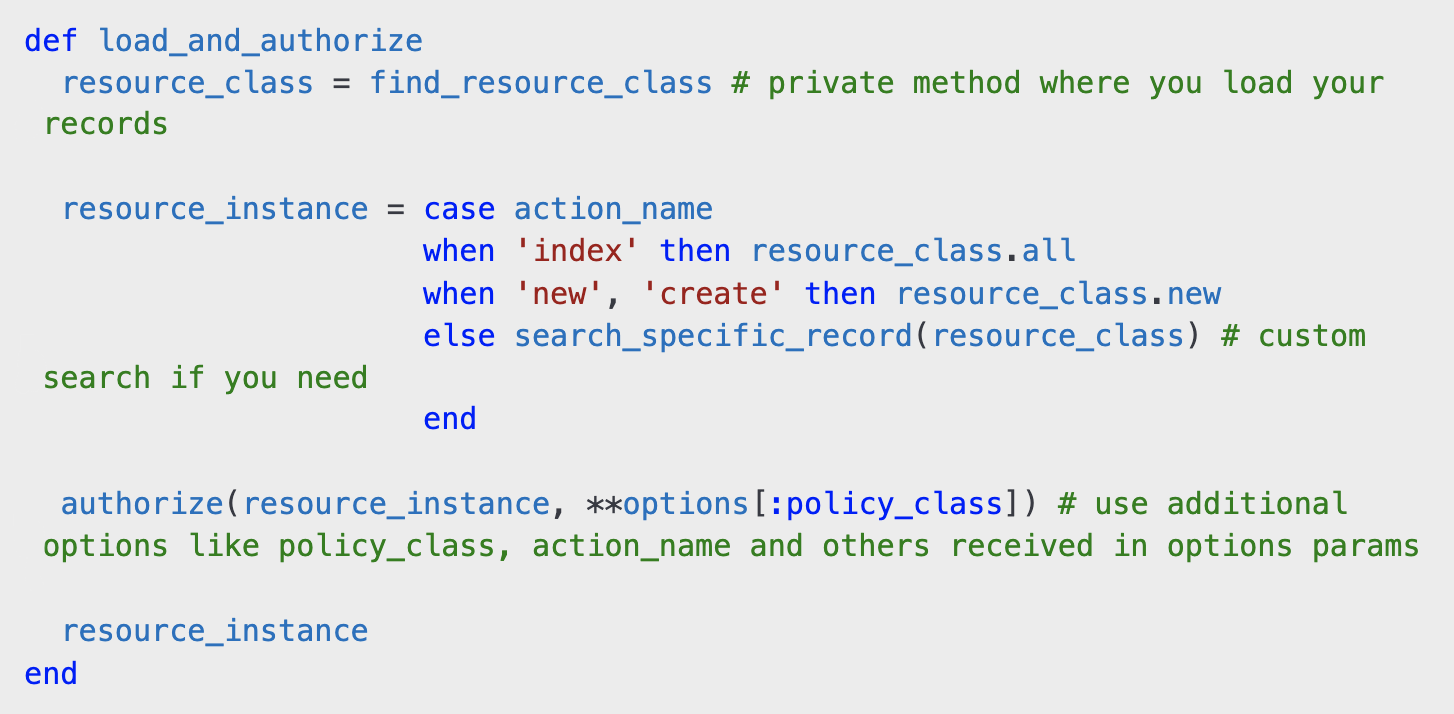
This makes it easy to add authorization without cluttering individual controllers.
2. Applying It in a Controller
With the AuthorizationMethods module included in ApplicationController, controllers become much cleaner. For example, in PostsControllerloading and authorizing a Post record is as simple as:
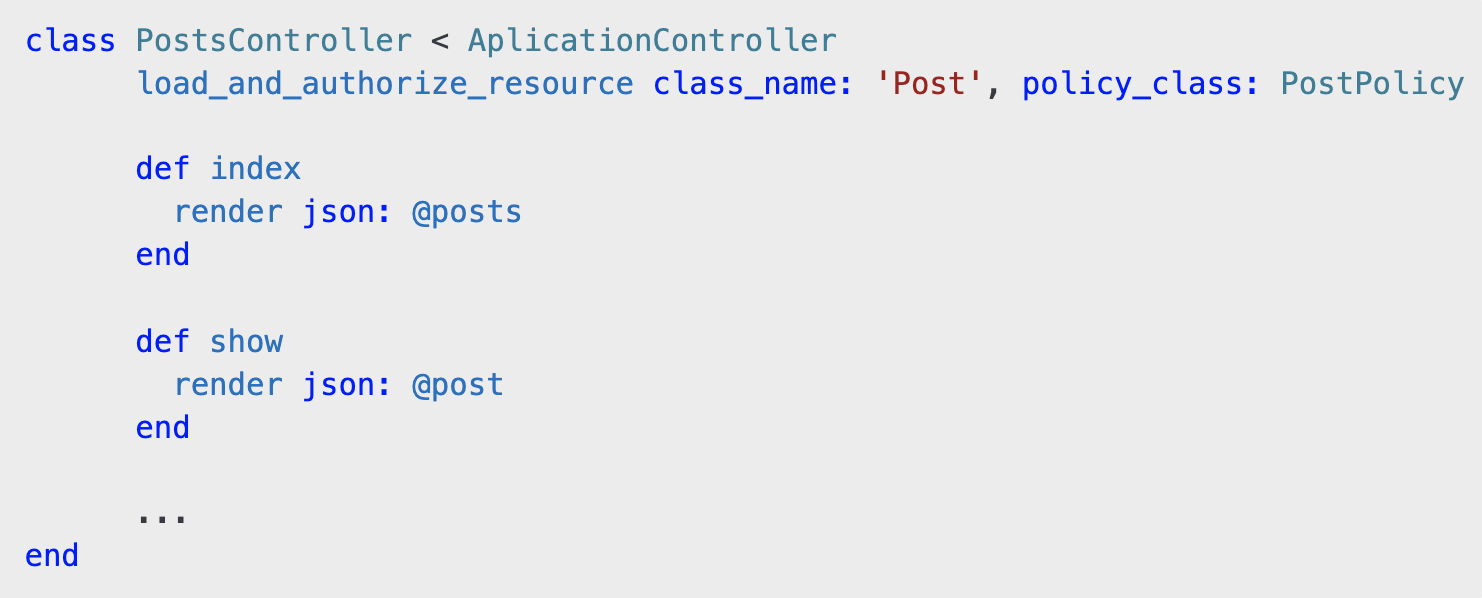
With load_and_authorize_resource, the controller:
- ✅ Automatically loads
Postrecords - ✅ Ensures authorization is enforced
- ✅ Remains clean and maintainable
Other Best Practices for Pundit
- Keep policies concise and focused. Each policy should only contain logic related to authorization to maintain clarity and separation of concerns.
- Use scopes for query-level authorization. This ensures that unauthorized data is never retrieved from the database, improving both security and efficiency.
- Always call
authorizein controllers. This prevents accidental exposure of sensitive actions by ensuring explicit permission checks. - Avoid authorization logic in models. Keep concerns separate by handling authorization in policies rather than embedding logic within models.
Wrap Up
Pundit simplifies authorization in Ruby on Rails by providing a clean and structured way to define and enforce permissions. By using policies, scopes, and controller-based authorization, you can create secure, maintainable, and scalable applications with minimal complexity.
If you’re building a Rails app that requires role-based access control, Pundit is a powerful tool that can streamline your authorization logic while keeping your codebase clean and easy to manage.
Opinions expressed by DZone contributors are their own.

Comments