Secure SDLC: Common Phases and List of Tasks
We take a look at what development and security teams can do to shift security left in the SDLC and achieve a true DevSecOps process.
Join the DZone community and get the full member experience.
Join For FreeDetails
Let’s get started by reviewing the development process and the common phases involved in the SDLC.
Requirement gathering
System/Application designing
Implementation
Testing
The approach where security is ignored in the above phases is a defective approach.
That's where a more secure SDLC comes in.
As a modified approach, teams should bake-in security from the start and make sure all the above phases of the SDLC incorporate a security-minded approach.
Let’s get into the details by understanding what is involved in each phase in order to build secure software.
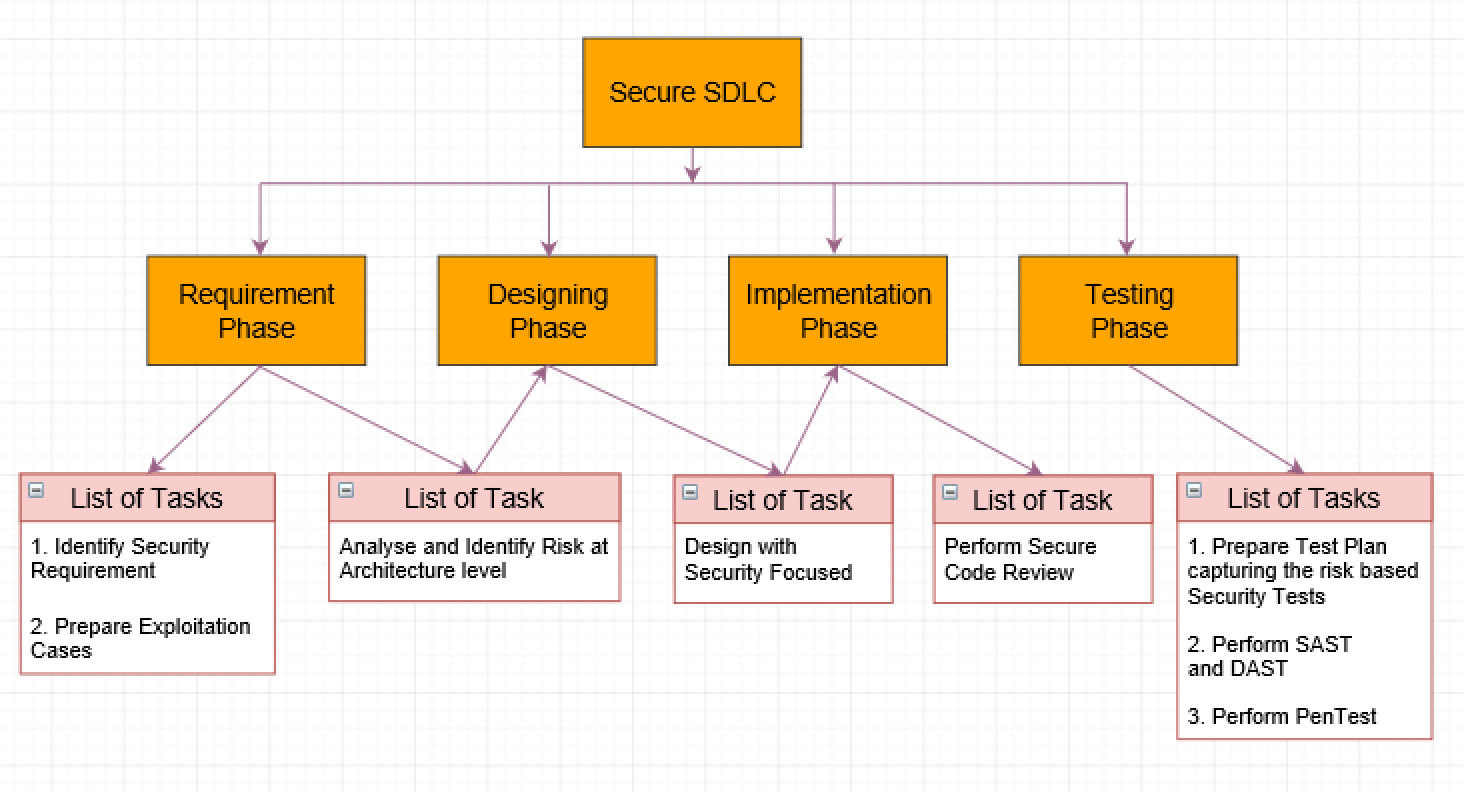
1. Requirement Phase: Identify and write down all the security requirements your team needs to consider.
The security requirements mainly focus on security expectations, such as:
a. Security Policies
i. Confidentiality
ii. Integrity
iii. Availability
b. Mechanisms to enforce those security policies
i. Authentication
ii. Authorization
iii. Accountability
iv. Auditing
Along with the security requirements, the preparation of exploitation test cases can help predict the way attackers could exploit the software so your team can set up proper countermeasures.
2. Designing Phase: During this phase, with the security requirements defined above, a threat model is used to design secure software.
3. Implementation Phase: Based on the security protocols used in the design phase, developers can go ahead and implement the software securely, which will be further reviewed from the security code perspective based on the guidelines and checklist in the next phase.
4. Testing Phase: The focus of this phase is to prepare the test plan and define the risk-based security tests to be used during testing. As part of this phase, the focus will on performing static and dynamic application security tests, which are also known as SAST and DAST. The next step in this phase will be to perform penetration testing in order to make sure any vulnerabilities in the developed software are addressed prior to release.
Conclusion
In order to have a secure SDLC, all the phases listed above should be executed, as each task can help reduce the number of critical vulnerabilities in your software.
Security is essential and shouldn’t be ignored - bake it in from the start.
Opinions expressed by DZone contributors are their own.

Comments