Security Considerations for Observability: Enhancing Reliability and Protecting Systems Through Unified Monitoring and Threat Detection
Security is a crucial part of managing site reliability. Learn how to unify observability with security practices to mitigate risks and increase resiliency.
Join the DZone community and get the full member experience.
Join For FreeEditor's Note: The following is an article written for and published in DZone's 2024 Trend Report, Observability and Performance: The Precipice of Building Highly Performant Software Systems.
In a world where organizations are considering migrating to the cloud or have already migrated their workloads to the cloud, ensuring all critical workloads are running seamlessly is a complicated task. As organizations scale their infrastructure, maintaining system uptime, performance, and resilience becomes increasingly challenging. Observability plays a crucial role in monitoring, collecting, and analyzing system data to gain insights into the health and performance of services. However, observability is not just about uptime and availability; it also intersects with security.
Managing site reliability involves addressing any security concerns such as data breaches, unauthorized access, and misconfigurations, all of which can lead to system downtime or compromise. Observability often comes with a powerful toolset that allows site reliability engineering (SRE) and security teams to collaborate, detect potential threats in real time, and ensure that both performance and security objectives are met.
This article reviews the biggest security challenges in managing site reliability, examines how observability can help mitigate these risks, and explores critical areas such as incident response and how observability can be unified with security practices to build more resilient, secure systems.
The Role of Observability in Security
Observability is a critical instrument that helps both security and SRE teams by providing real-time insights into system behavior.
Unified Telemetry for Proactive Threat Detection
Observability unifies telemetry data — logs, traces, and metrics — into a centralized system, providing comprehensive visibility across the entire infrastructure. This convergence of data is essential for both site reliability and security. By monitoring this unified telemetry, teams can proactively detect anomalies that may indicate potential threats, such as system failures, misconfigurations, or security breaches.
SRE teams may use this data to identify issues that could affect system availability, while security teams can use the same data to uncover patterns that suggest a cyberattack. For example, abnormal spikes in CPU usage may indicate a denial-of-service attack, and unexpected traffic from unknown IPs could be a sign of unauthorized access attempts.
Incident Detection and Root Cause Analysis
Effective incident detection and root cause analysis are critical for resolving both security breaches and performance issues. Observability empowers SRE and cybersecurity teams with the data needed to detect, analyze, and respond to a wide range of incidents. Logs provide detailed records of actions leading up to an incident, traces illustrate how transactions flow through the system, and metrics spotlight unusual patterns that may indicate anomalies.
Observability integrated with automated systems enables faster detection and response to diverse cybersecurity incidents:
- Data exfiltration. Observability detects unusual data access patterns and spikes in outbound traffic, limiting data loss and regulatory risks.
- Insider threats. Continuous monitoring identifies suspicious access patterns and privilege escalations, allowing swift mitigation of insider risks.
- Malware infiltration. Anomalies in resource usage or unauthorized code execution indicate potential malware, enabling quick containment and limiting system impact.
- Lateral movement. Unexpected cross-system access reveals attacker pathways, helping contain threats before they reach critical systems.
Automated observability shortens detection and response times, minimizing downtime and strengthening system security and performance.
Monitoring Configuration and Access Changes
One of the critical benefits of observability is its ability to monitor configuration changes and user access in real time. Configuration drift — when system configurations deviate from their intended state — can lead to vulnerabilities that expose the system to security risks or reliability issues. Observability platforms track these changes and alert teams when unauthorized or suspicious modifications are detected, enabling rapid responses before any damage is done.
How Observability Can Be Unified With Security
The integration of observability with security is essential for ensuring both the reliability and safety of cloud environments. By embedding security directly into observability pipelines and fostering collaboration between SRE and security teams, organizations can more effectively detect, investigate, and respond to potential threats.
Security-First Observability
Embedding security principles into observability pipelines is a key strategy for uniting observability with security. Security-first observability ensures that the data generated from logs, metrics, and traces is encrypted and accessible only to authorized personnel using access control mechanisms such as role-based access control.
Figure 1. Observability data encrypted in transit and at rest
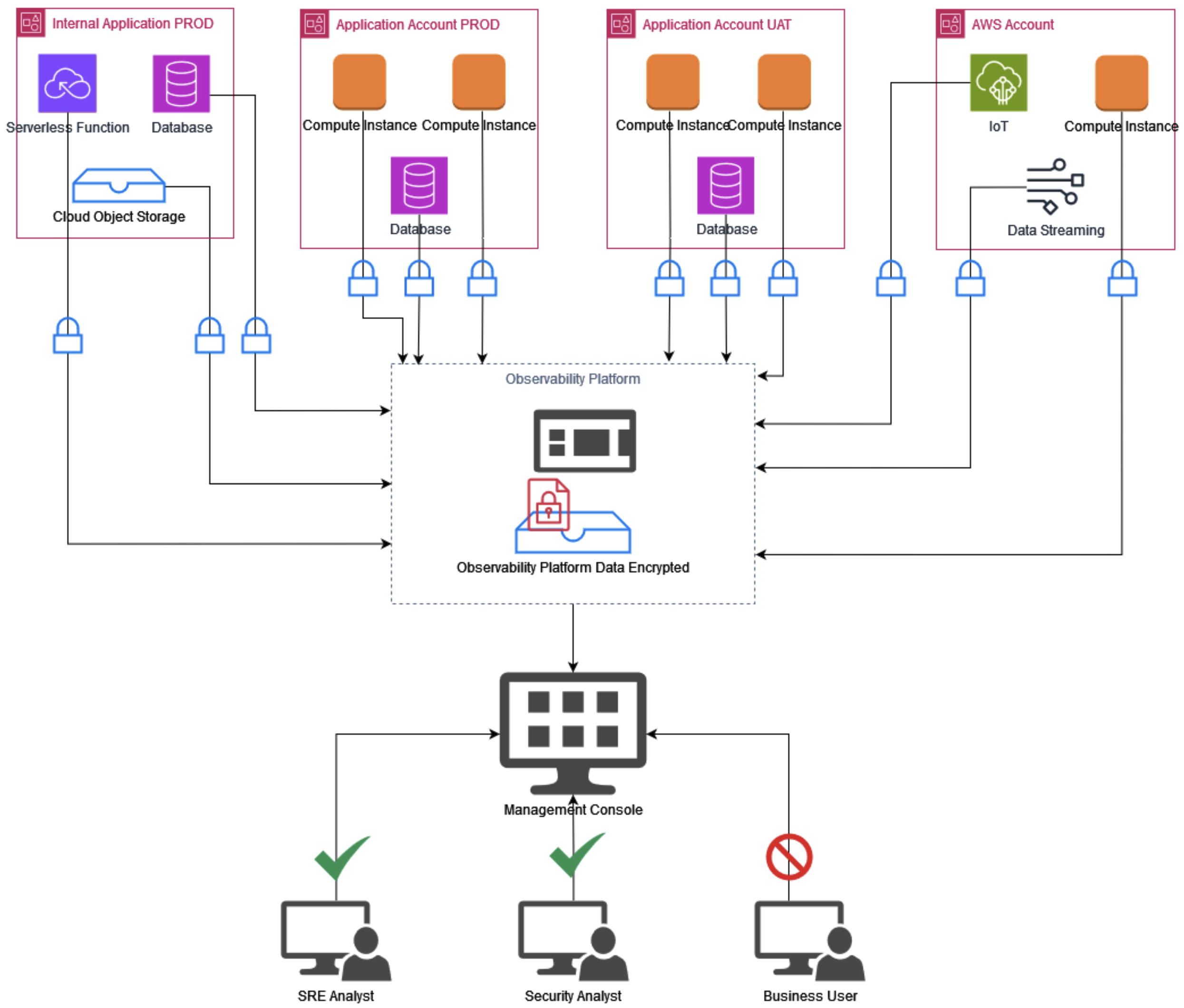
Additionally, security teams can leverage SRE-generated telemetry to detect vulnerabilities or attack patterns in real time. By analyzing data streams that contain information on system performance, resource usage, and user behavior, security teams can pinpoint anomalies indicative of potential threats, such as brute-force login attempts or distributed denial-of-service (DDoS) attacks, all while maintaining system reliability.
SRE and Security Collaboration
Collaboration between SRE and security teams is essential for creating a unified approach to observability. One of the best ways to foster this collaboration is by developing joint observability dashboards that combine performance metrics with security alerts. These dashboards provide a holistic view of both system health and security status, allowing teams to identify anomalies related to both performance degradation and security breaches simultaneously.
Another key collaboration point is integrating observability tools with security information and event management (SIEM) systems. This integration enables the correlation of security incidents with reliability events, such as service outages or configuration changes. For instance, if an unauthorized configuration change leads to an outage, both security and SRE teams can trace the root cause through the combined observability and SIEM data, enhancing incident response effectiveness.
Incident Response Synergy
Unified observability also strengthens incident response capabilities, allowing for quicker detection and faster recovery from security incidents. Observability data, such as logs, traces, and metrics, provide real-time insights that are crucial for detecting and understanding security breaches. When suspicious activities (e.g., unauthorized access, unusual traffic patterns) are detected, observability data can help security teams isolate the affected systems or services with precision.
Figure 2. Automating security response based on alerts generated
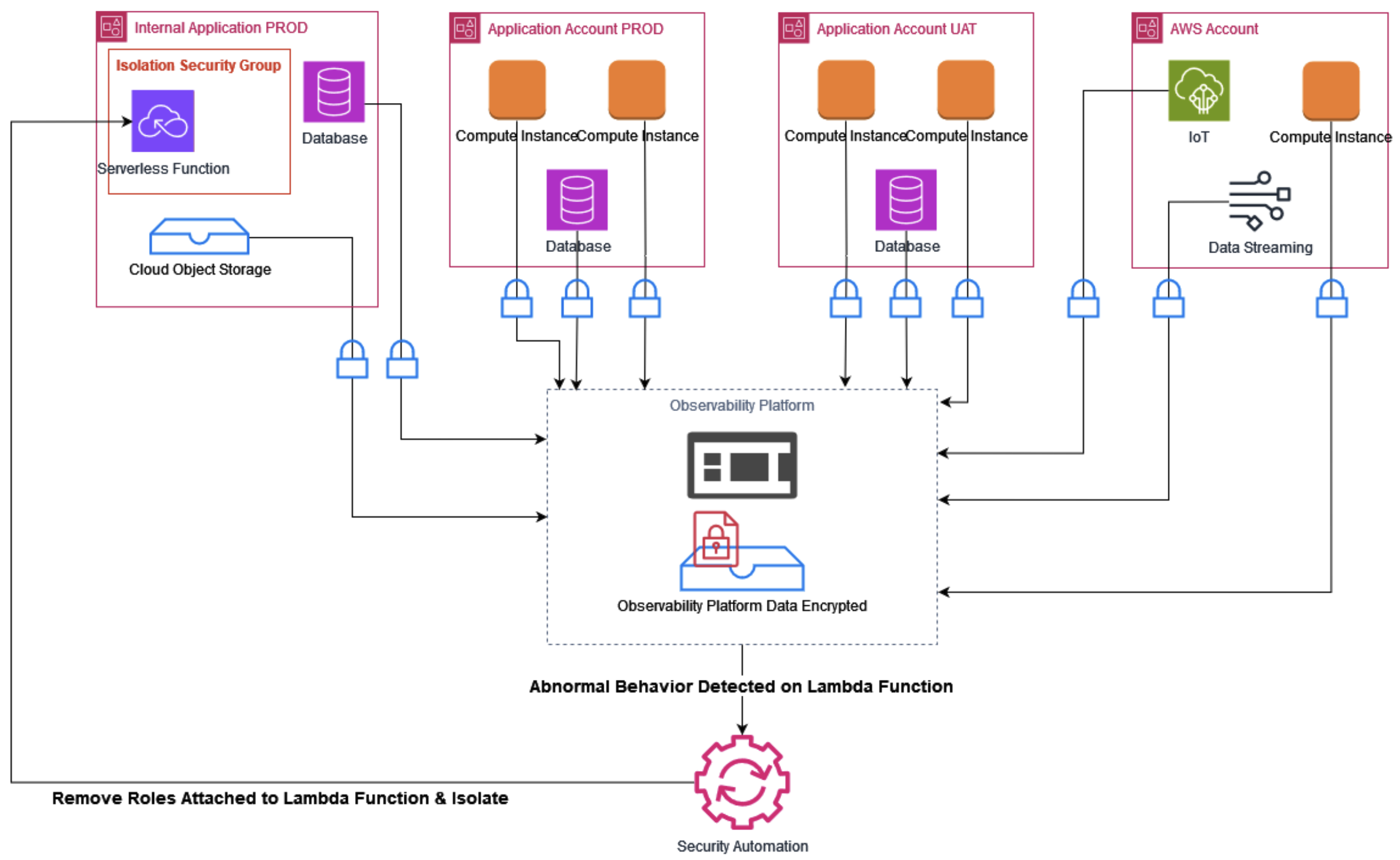
Moreover, automating incident response workflows based on observability telemetry can significantly reduce response times. For instance, if an intrusion is detected in one part of the system, automated actions such as isolating the compromised components or locking down user accounts can be triggered immediately, minimizing the potential damage. By integrating observability data into security response systems, organizations can ensure that their response is both swift and efficient.
Penetration Testing and Threat Modeling
Observability also strengthens proactive security measures like penetration testing and threat modeling. Penetration testing simulates real-world attacks, and observability tools provide a detailed view of how those attacks affect system behavior. Logs and traces generated during these tests help security teams understand the attack path and identify vulnerabilities.
Threat modeling anticipates potential attack vectors by analyzing system architecture. Observability ensures that these predicted risks are continuously monitored in real time. For example, if a threat model identifies potential vulnerabilities in APIs, observability tools can track API traffic and detect any unauthorized access attempts or suspicious behavior.
By unifying observability with penetration testing and threat modeling, organizations can detect vulnerabilities early, improve system resilience, and strengthen their defenses against potential attacks.
Mitigating Common Threats in Site Reliability With Observability
Observability is essential for detecting and mitigating threats that can impact site reliability. By providing real-time insights into system performance and user behavior, observability enables proactive responses to potential risks. Table 1 reviews how observability helps address common threats:
Table 1. Common threats and mitigation strategies
| Threat | Mitigation Strategy |
| Preventing service outages from cyberattacks |
|
| Preventing data breaches |
|
| Handling insider threats |
|
| Automation for incident resolution |
|
Building a Secure SRE Pipeline With Observability
Integrating observability into SRE and security workflows creates a robust pipeline that enhances threat detection and response. This section outlines key components for building an effective and secure SRE pipeline.
End-to-End Integration
To build a secure SRE pipeline, it is essential to seamlessly integrate observability tools with existing security infrastructure (e.g., SIEM); security orchestration, automation, and response (SOAR); and extended detection and response (XDR) platforms. This integration allows for comprehensive monitoring of system performance alongside security events.
Figure 3. Security and observability platform integration with automated response
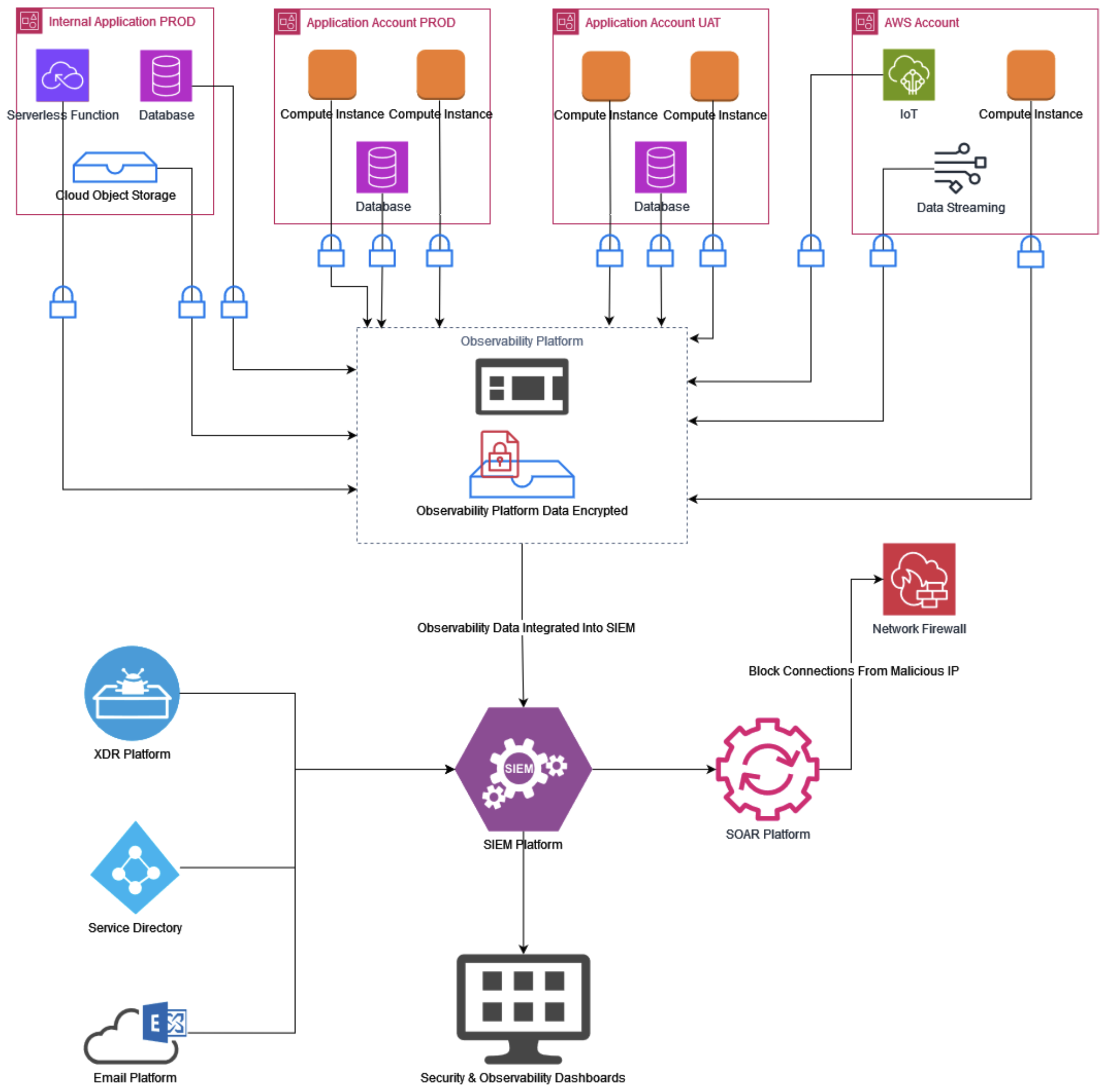
By creating a unified dashboard, teams can gain visibility into both reliability metrics and security alerts in one place. This holistic view enables faster detection of issues, improves incident response times, and fosters collaboration between SRE and security teams.
Proactive Monitoring and Auto-Remediation
Leveraging artificial intelligence (AI) and machine learning (ML) within observability systems allows for the analysis of historical data to predict potential security or reliability issues before they escalate. For example, by learning historical data, AI and ML can identify patterns and anomalies in system behavior. Additionally, automated remediation processes can be triggered when specific thresholds are met, allowing for quick resolution without manual intervention.
Custom Security and SRE Alerts
A secure SRE pipeline requires creating tailored alerting systems that combine security and SRE data. By customizing alerts to focus on meaningful insights, teams can ensure they receive relevant notifications that prioritize critical issues. For instance, alerts can be set up to notify SRE teams of security misconfigurations that could impact system performance or alerts that would notify the security teams of system performance issues that could indicate a potential security incident. This synergy ensures that both teams are aligned and can respond to incidents swiftly, maintaining a balance between operational reliability and security.
Conclusion
As organizations and their environments grow in complexity, integrating observability with security is crucial for effective site reliability management. Observability provides the real-time insights needed to detect threats, prevent incidents, and maintain system resilience. By aligning SRE and security efforts, organizations can proactively address vulnerabilities, minimize downtime, and respond swiftly to breaches.
Unified observability not only enhances uptime but also strengthens security, making it a key component in building reliable, secure systems. In an era when both performance and security are critical, this integrated approach is essential for success.
This is an excerpt from DZone's 2024 Trend Report, Observability and Performance: The Precipice of Building Highly Performant Software Systems.
Read the Free Report
Opinions expressed by DZone contributors are their own.

Comments