Seeing the Forest for the Trees: Data Preservation Starts With a Keen Eye
Initiating a successful data preservation strategy hinges on the foundation of meticulous observation and an unwavering focus on details.
Join the DZone community and get the full member experience.
Join For FreeEverywhere you turn, data security is a major challenge for several organizations. This makes it difficult to ensure that data is reliable and accurate for use. This is why organizations must now take data preservation more seriously than they ever have, especially when you consider what cybercriminals have in store.
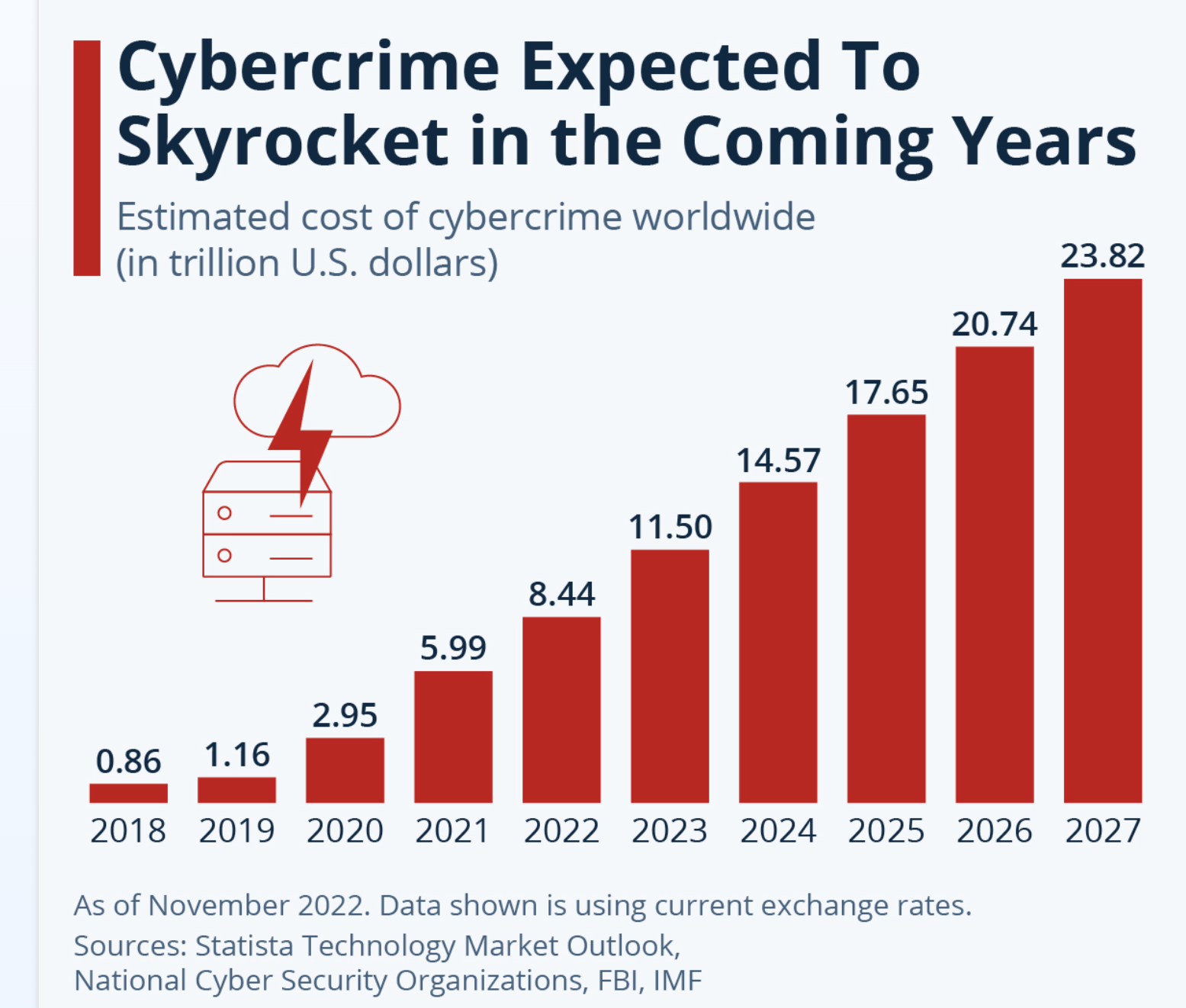
Effective data preservation starts with a keen eye: achieving holistic visibility. Organizations of all sizes and industries have come to rely heavily on the seamless flow of information, making data protection an essential pillar in maintaining integrity, competitiveness, and resilience.
This article explores seven major factors that will enable organizations today to enhance their data preservation capabilities, beginning with the foremost factor of real-time visibility.
1. Real-Time Visibility and Monitoring
Data preservation hinges on detecting and responding to any suspicious activity that could compromise the integrity of an organization’s digital assets. So, real-time monitoring is the crux of modern data security, and every other point following this directly or indirectly ties in with this first one.
Robust real-time monitoring guarantees holistic visibility, allowing you to detect internal and external threats. Endpoint detection and response systems rely on continuous surveillance of devices and users to prevent unauthorized access to critical data – a risk that is now exacerbated because of the greater distribution of endpoints due to modern work arrangements.
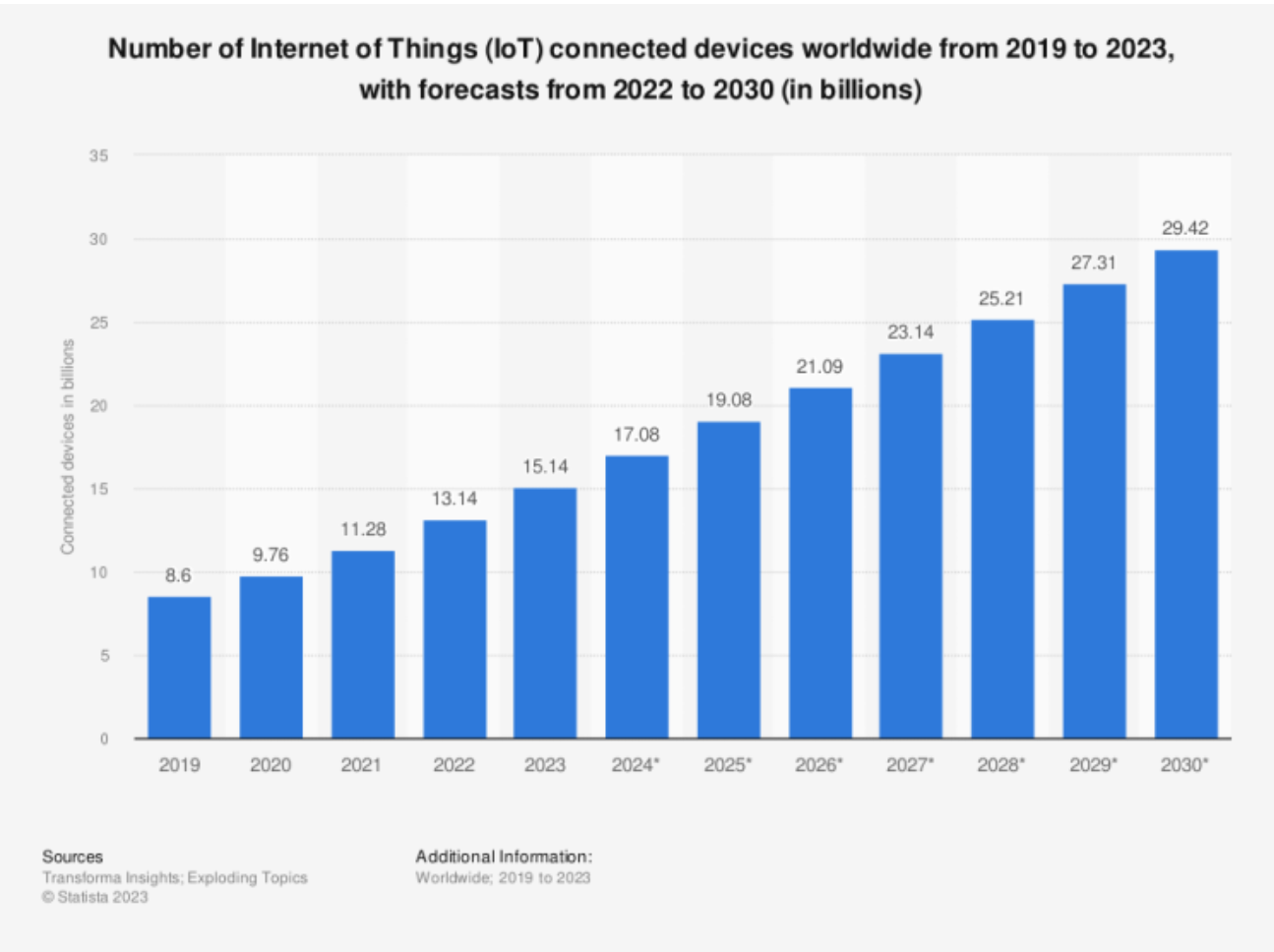
This is why SIEM (System Information and Event Management) systems have become particularly popular today, even if many organizations are yet to adopt them. SIEM platforms enable you to collect and integrate data from a variety of sources and cross-analyze them at once for suspicious activity.
And with the introduction of Data Detection Response solutions, which are an AI-enabled advancement over traditional Data Loss Prevention solutions, businesses should have no objection to adopting real-time monitoring in their cybersecurity framework.
2. Behavioral Analytics
The rise of insider threats, zero-day vulnerabilities, advanced persistent threats (APTs), and other kinds of sophisticated attacks underscore the importance of analyzing and understanding user behavior within an organization’s digital ecosystem. They also prove the need for adaptive, data-driven security.
Behavioral analytics, as a potent tool for data preservation, leverages AI algorithms and machine learning to automatically detect signs of malicious intent from unusual actions. In this age, if data is king, then context is key, and an organization’s vigilant approach must rely on dynamic situational factors rather than static rules in order to effectively protect data from breaches and leaks.
3. Cloud-First Data Security
The world has gone cloud-first, and our data preservation and protection techniques must fully embrace this shift. Unfortunately, many organizations still adopt traditional approaches to cloud-native storage technology.
Firstly, it’s important to precisely define the shared responsibility model for cloud resources. This leaves no aspect of data security up to chance. And client organizations must also be certain that vendors are adopting the highest security practices. After all, vendors can be a major third-party risk.
Particularly, implementing robust identity and access management protocols is crucial – following least privilege principles that limit access to privileged users for only the duration of time that the data is needed.
4. Data Lineage Analysis
For the most part, this is a vastly unexplored area in data preservation and data protection. Many folks are familiar with data lifecycle management, but data lineage analysis offers a different approach. In the latter, you still are tracing the transformations of data throughout its lifecycle; however, the focus is on previous data flow.
It is not enough that you can access data here and now; you must also be able to map how it has moved through an organization’s systems and processes: users who have accessed it, devices it has passed through, downloads and uploads, etc. Tracing the path of data ensures heightened data integrity, but not that alone; it is also a valuable resource for compliance and audit purposes.
If you suspect that a piece of data is corrupt but can’t definitively tell how or when it was corrupted, a data lineage analysis is important in order to prevent (further) damage to your organization’s systems and uphold the reliability of the information.
5. Encryption
Encryption cannot go out of vogue as a data security strategy. It remains a guaranteed approach to ensure that even if data falls into the wrong hands, it’s going to be useless since it can only be deciphered by authorized users. Various industry regulations and compliance standards mandate the use of encryption anyway.
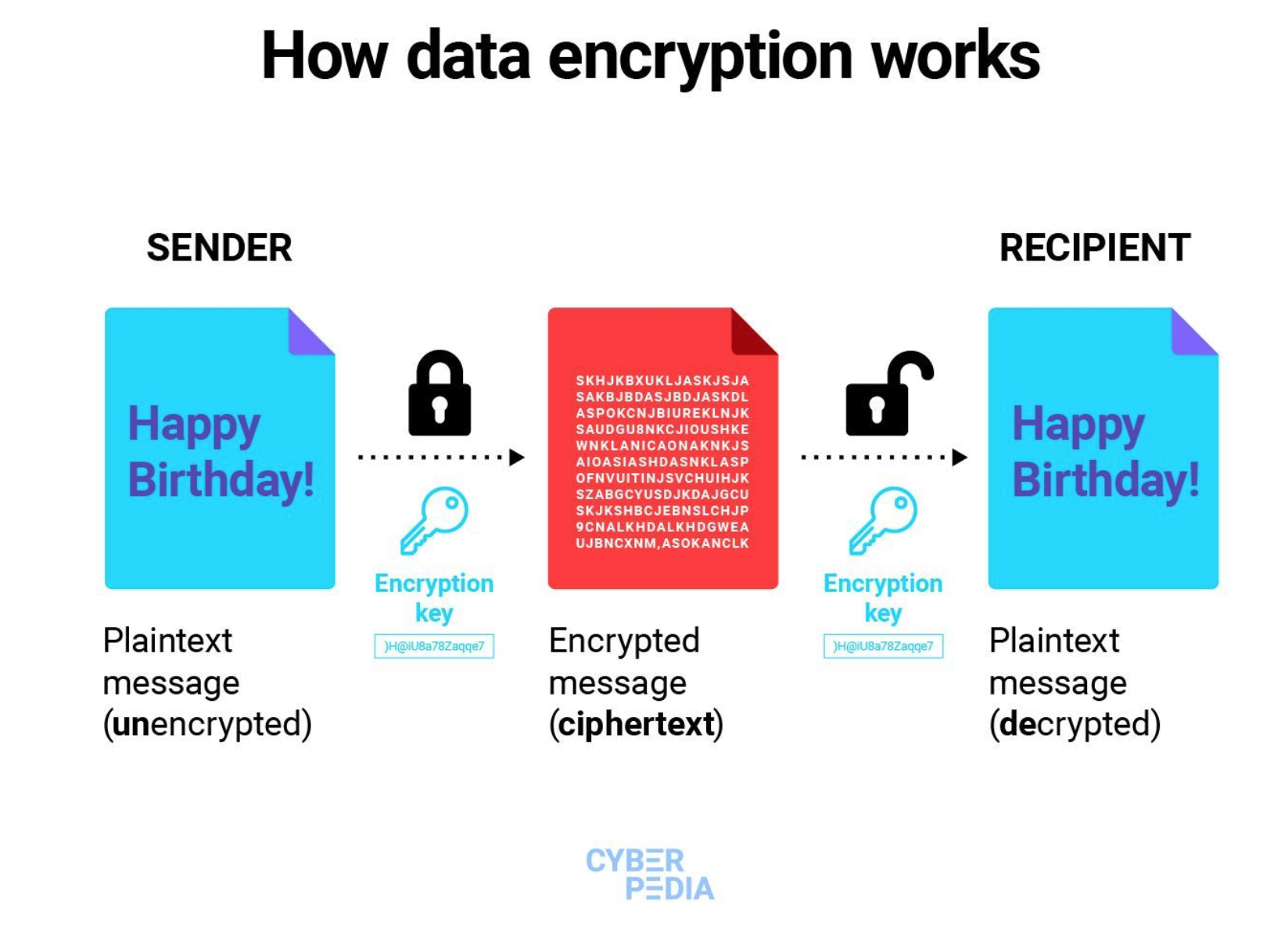
However, it is important to know that encryption does not answer all. It can safeguard data at rest and in transit, but it can’t protect data in use, which is a very critical point of vulnerability. More so, poorly implemented encryption can lead to performance issues or hinder user workflows.
6. Risk Management
A major aspect of data preservation is constantly evaluating your risk posture as an organization. This is even more important as cybersecurity threats keep evolving and getting more sophisticated. For instance, malicious actors now recruit AI algorithms to launch deadlier attacks. And the spate of zero-day attacks keeps climbing.
To anticipate and address threats, you must be able to proactively assess the internal and external factors that could cause security incidents. But this is not a one-time process, as some might imagine. It is an ongoing endeavor that must keep adapting to the evolving landscape. What we knew about cybersecurity five years ago would certainly not work today.
7. Data Governance
Finally, organizations must provide holistic data governance to handle all processes throughout the data life cycle. It is easy to default to external compliance requirements and not see the need for internal controls.
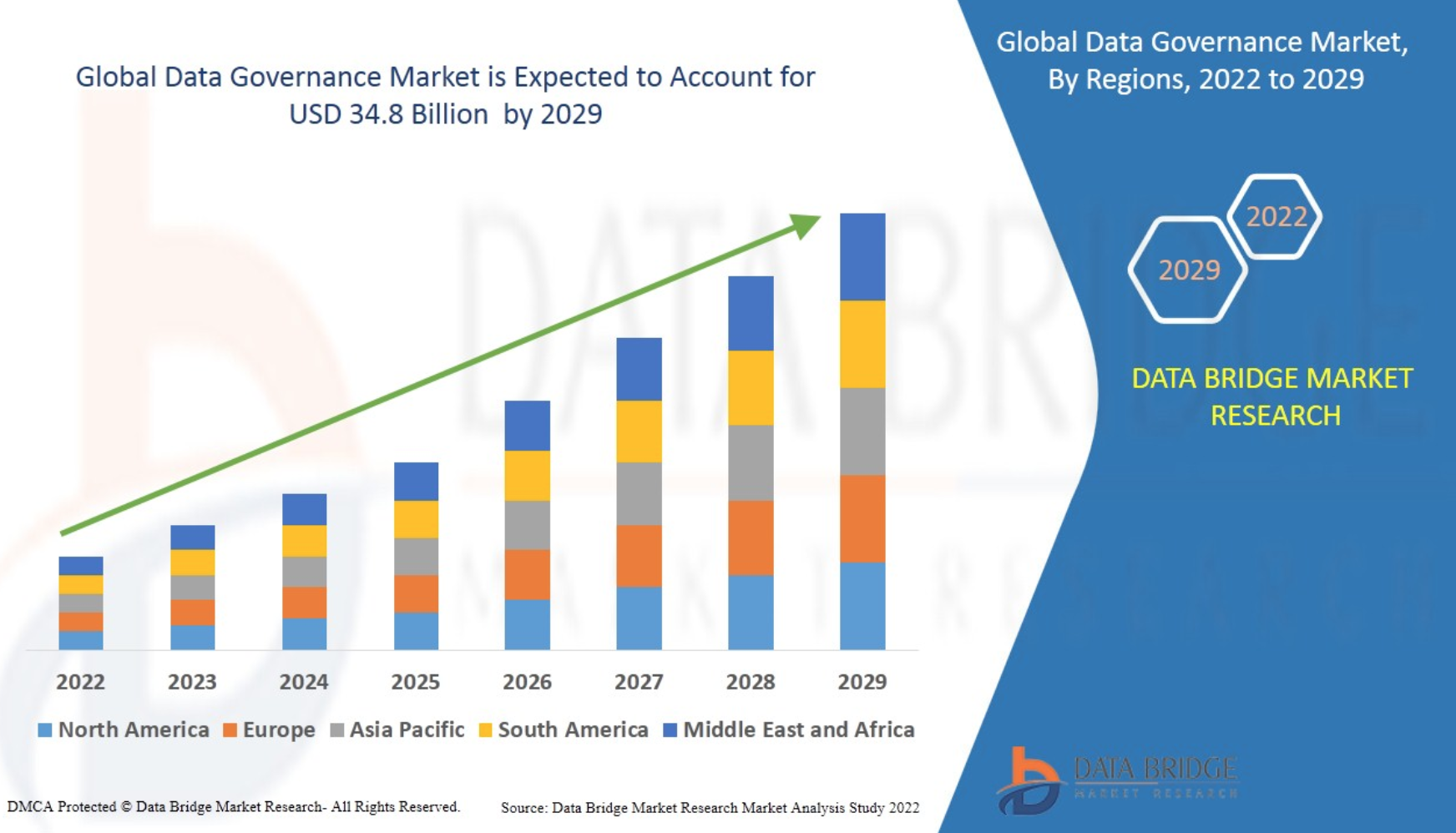
Yet, without internal documents guiding access controls, employee training, legal protection, cybersecurity culture, incident reporting, and sundry issues, an organization might not find its feet as far as data security is concerned. The goal must be to foster a culture of data preservation throughout the organization and enable all employees to take responsibility for security, not just the IT team.
Conclusion
All these factors woven together form a robust tapestry against ever-increasing cyber threats. After all, our strategies for data preservation must advance as technology too. Above all, though, it is critical to maintain a proactive mindset and ensure that nothing happens outside your organization’s line of vision.
Opinions expressed by DZone contributors are their own.

Comments