Statistics-Based OWASP Top 10 2021 Proposal
The purpose of this work is to make an OWASP Top 10 2021 predictions calculated by understandable metrics, make everyone able to reproduce the results, and present to an entire community for feedback.
Join the DZone community and get the full member experience.
Join For FreeEverybody knows the OWASP Top 10 as well as the fact that it gets updated only every other 3-4 years. With the last update published in 2017, it’s no surprise that a new version is coming this year. During my application security career, I saw OWASP Top 10 at least in 2003, 2004, 2007, 2010, 2013, and 2017.
Since the OWASP creation process is not documented well, it seems reasonable to build an open and transparent rating for the same categories based on a large number of security reports.
The purpose of this work is to make an OWASP Top 10 2021 predictions calculated by understandable metrics, make everyone able to reproduce the results, and present to an entire community for feedback. The following work is based on an analysis of 2 million security reports from 144 public sources including CVE bulletins, bug bounty reports, and vendor security bulletins.
Categories Overlap in OWASP Top-10
The first thing that I should mention about OWASP Top 10 is that it’s not a vulnerability classification and not even the classification at any point since categories overlap. I am referring to the security boulevard article and our blog post that describes the interference presented in the following diagram:
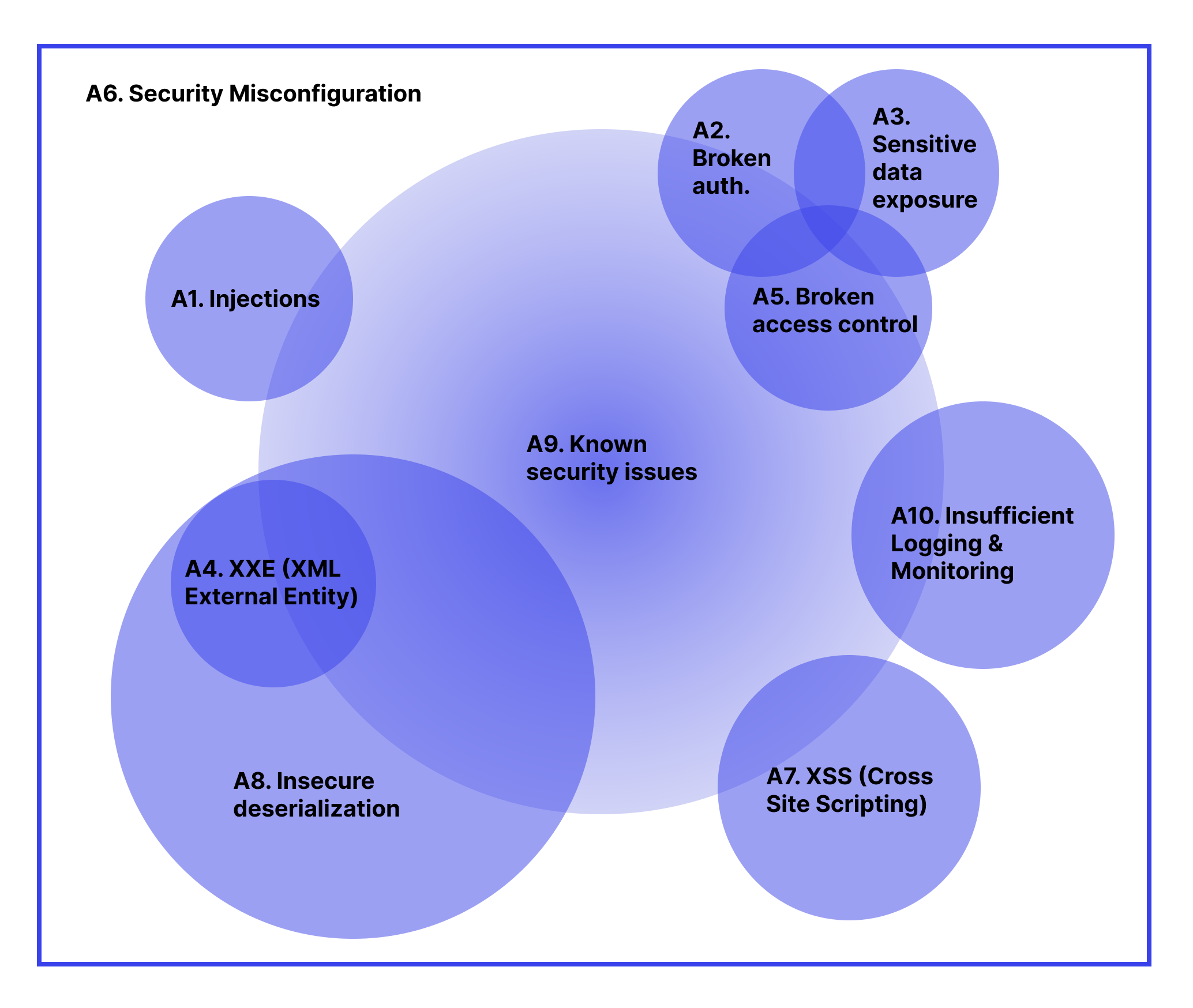
To sum up: OWASP Top 10 IS NOT a vulnerability classification, but rather the list of the risks that have been revealed during the last period of time. That’s why to predict the next OWASP Top 10 2021 list, we have to analyze threats to the targeted web assets for the last four years.
So, here we go.
Methodology
To find the statistical data, we used Vulners.com, which is an aggregated database that includes more than four million bulletins from 144 vendors, including bug bounty programs like HackerOne.
The total amount of bulletins used to build this list is 2,168,521 (search query: “published:[2018-01-01 TO 2020-12-31]”).
To split data by categories, we built vulners search queries for all the ten OWASP categories. Even though the full-text search is not the most accurate solution to classify data, I think I can rely on this particular task. The point is that all the OWASP categories could be found in security bulletins by searching for acronyms and abbreviations like XSS, XXE, SQL, RCE, etc.
The category “Known Vulnerabilities” is out of the full-text search query. The total number of web-related security reports were taken as a total amount of CVE numbers assigned for the last three years.
It’s not a joke, but according to the Vulners statistics, XSS takes 20% of ALL the security bulletins for the last three years. It’s almost 10x more than all the CVEs issued in the last three years. Since many XSS don’t have a CVSS score (meaning zero), an average score for that many of them is still 0.1. That fact, however, doesn’t stop XSS from hitting the Top 3 in a chart, again, because it’s as many of them as each fifth bulletin was found in the last three years.
You can reuse the following queries to validate, modify, or make your own analysis:
| Top 10 2017 to 2021 mapping | Search query |
| A1. Injections | injection OR traversal OR lfi OR “os command” OR SSTI OR RCE OR “remote code” |
| A2. Broken auth | authentication |
| A3. Sensitive data exposure | sensitive AND data |
| MERGE: A8. Insecure Deserialization + A4. XXE | XXE OR deserialize OR deserialization OR “external entities” |
| A5. Broken Access Control | access control |
| A6. Security Misconfiguration | misconfiguration OR misconfigure OR misconfig |
| A7. XSS | XSS |
| NEW: SSRF | SSRF OR “server side request forgery” |
| A9. Known Vulnerabilities | type:cve and (http OR web OR html) |
| A10. Insufficient Logging & Monitoring | logging |
As you can see, my strong opinion is that the OWASP community will add the new category SSRF and merge “A4. XXE – XML External Entity” and “A8. Insecure Deserialization” in the upcoming OWASP Top 10 2021. Here is why.
Proposal 1: Add SSRF as a New Category
As an SSRF inventor and author of the “SSRF bible cheatsheet,” I definitely keep warm feelings about it.
In spite of this, please allow me to mention just the four most powerful facts related to SSRF:
- The SSRF attacks become #3 of the most critical vulnerabilities as of H1 2020 stats.
- Amazon took it seriously and patched in for EC2 metadata services at the end of 2019.
- SSRF caused a lot of high-risk security problems, including the most famous Capital One hack with a WAF bypass, explained in detail by Krebs on Security.
- According to the global stats collected by Vulners, SSRF was mentioned in 912 bulletins last three years, almost the same amount of times as OWASP Top-10 2017 A4 / XXE (1000 results) and 2.5x more often than security misconfiguration (A6 / 481 results).
To sum up, SSRF is a critical issue that causes cloud takeovers, remote code execution, data breaches, and other information security risks. It’s impossible to fix SSRF by input filtration and other data validation mechanisms. Amazon and other cloud providers take it seriously and apply changes to their infrastructures to mitigate these threats. SSRF issues mentioned in almost the same amount of security bulletins as XXE in the last three years. That’s why I’m sure nobody will blame me for adding it to the OWASP Top-10 2021.
Proposal 2: Merge XXE and Insecure Deserialization
XML is the serialization format, according to Wikipedia (https://en.wikipedia.org/wiki/Serialization). The XXE vulnerability, a.k.a. Xml eXternal Entities, is technically a serialization feature that allows the inclusion of local and remote files content into the XML document. Sometimes it causes SSRF, by the way. That’s why it’s absolutely true that XXE is a part of the Insecure Deserialization category anyway, which I mentioned in a bunch of articles related to the OWASP Top 10 2017 weaknesses.
Also, there is no way to claim XXE as the separate category if gathering pretty much everything from SQL injection to Path Traversal and OS commanding a vague group “A1. Injections” which will lead OWASP for years, for sure.
Because of these two facts, plus based on statistical data of the number of security reports in each of the categories, I decided to merge XXE and Insecure Deserialization to a single class.
Proposal 3: Introduce Overall Risk Score
To sort my assumptions of the OWASP Top 10, for each of the categories, I applied an average CVSS score multiplies to the number of reports. In fact, because a lot of the bulletins have 0 CVSS score, the resulting rating should be interpreted as an average CVSS score for the category, but just demonstrates the right proportions between them.
In a few words, to sort OWASP categories, the following formula was applied:
Overall Risk = Avg. CVSS x Amount of Bulletins
Calculating the OWASP Top-10 2021 Rating
As mentioned above, I used an aggregated data from 144 data sources such as security bulletins that Vulners.com indexed. This approach allows to count not only CVE data but all the reports, including bug bounties, exploits, and scanner detects that rely on the real state of information security. If we will count only CVEs, the results will be dramatically different, since the category “Known vulnerabilities” will be technically equal in a count to all the other categories in a sum.
So, here is the fairest way of building OWASP Top 10, look at that!
| #OWASP | Top-10 2021 | Vulners search query | Avg. CVSS | # of bulletins | Overall score |
| A1 | Injections | injection OR traversal OR lfi OR “os command” OR SSTI OR RCE OR “remote code” | 4.83 | 34061 | 164514.63 |
| A2 | Broken Authentication | authentication | 4.08 | 13735 | 56038.8 |
| A3 | Cross-Site Scripting (XSS) | xss | 0.1 | 433353 | 43335.3 |
| A4 | Sensitive Data Exposure | sensitive AND data | 3.55 | 5990 | 21264.5 |
| A5 | Insecure Deserialization | XXE OR deserialize OR deserialization OR “external entities” | 5.33 | 2985 | 15910.05 |
| A6 | Broken Access Control | access control | 0.72 | 16967 | 12216.24 |
| A7 | Insufficient Logging & Monitoring | logging | 3.35 | 2309 | 7735.15 |
| A8 | Server Side Request Forgery (SSRF) | SSRF OR “server side request forgery” | 3.8 | 1139 | 4328.2 |
| A9 | Known Vulnerabilities | type:cve and (http OR web OR html) | 5.38 | 376 | 2022.88 |
| A10 | Security Misconfiguration | misconfiguration OR misconfigure OR misconfig | 2.27 | 480 | 1089.6 |
Results and OWASP Top. 10 2017 Comparison
I’m pretty confident to share the following proposal of OWASP Top 10 for 2021 since it’s based on statistical data available publicly.
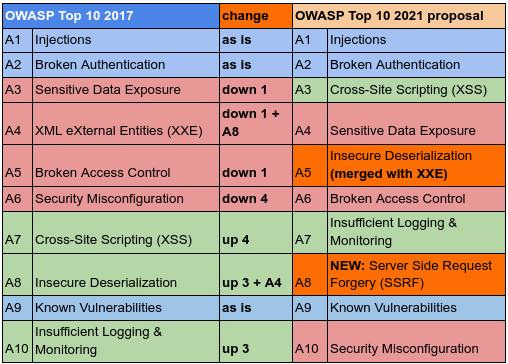 OWASP Top-10 2021 proposal
OWASP Top-10 2021 proposal
I hope these data will be useful for risk assessments, vulnerability management, education purposes, and just interesting reading for application security experts and enthusiasts.
Application security experts could also find interesting distribution these categories by amount of security reports, mean bulletins, bug bounties, exploits, altogether:

Thanks for reading! Ivan, Wallarm.
Special thanks to Vulners.com team for helping with data collection and analysis.
Published at DZone with permission of Ivan Wallarm. See the original article here.
Opinions expressed by DZone contributors are their own.

Comments