STRIDE Threat Model
Threat Modeling, or Architectural Risk Analysis, helps to reduce risk. The STRIDE Threat Model categorizes threats to help further identify and solve problems.
Join the DZone community and get the full member experience.
Join For FreeWhen designing your system analyze the threats from the perspective or point of view of an attacker. Threat Modeling, also called Architectural Risk Analysis, is a security control to identify and reduce risk. The STRIDE Threat Model helps place threats into categories so that questions can be formulated from the attackers point of view.
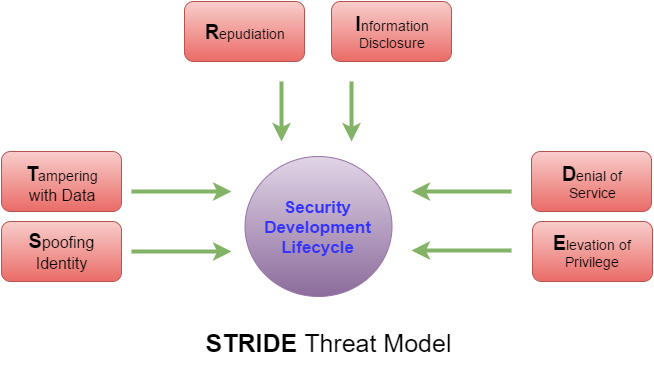
- Spoofing identity. An example of identity spoofing is illegally accessing and then using another user's authentication information, such as username and password. Example: Phishing attack to fool the user into sending credentials to the fake site.
- Tampering with data. Data tampering involves the malicious modification of data. Examples include unauthorized changes made to persistent data, such as that held in a database, and the alteration of data as it flows between two computers over an open network, such as the Internet. Example: Integrity of a message compromised to change parameters or values.
- Repudiation. Repudiation threats are associated with users who deny performing an action without other parties having any way to prove otherwise—for example, a user performs an illegal operation in a system that lacks the ability to trace the prohibited operations. Nonrepudiation refers to the ability of a system to counter repudiation threats. For example, a user who purchases an item might have to sign for the item upon receipt. The vendor can then use the signed receipt as evidence that the user did receive the package. Example: Illegitimately claming a transaction was not completed.
- Information disclosure. Information disclosure threats involve the exposure of information to individuals who are not supposed to have access to it—for example, the ability of users to read a file that they were not granted access to, or the ability of an intruder to read data in transit between two computers. Example: Unencrypted message sniffed off the network.
- Denial of service. Denial of service (DoS) attacks deny service to valid users—for example, by making a Web server temporarily unavailable or unusable. You must protect against certain types of DoS threats simply to improve system availability and reliability. Example: System Flooded by request until the web server fails.
- Elevation of privilege. In this type of threat, an unprivileged user gains privileged access and thereby has sufficient access to compromise or destroy the entire system. Elevation of privilege threats include those situations in which an attacker has effectively penetrated all system defenses and become part of the trusted system itself, a dangerous situation indeed. Example: Attacker changes group membership.
OWASP (Open Web Application Security Project) has more on Threat Risk Modeling at https://www.owasp.org/index.php/Threat_Risk_Modeling.
Stride (software)
Opinions expressed by DZone contributors are their own.

Comments