How to Handle the CSRF Token in JMeter
When we do load testing using JMeter without handling the CSRF token, you get a certain error. Learn how to handle the CSRF token in JMeter.
Join the DZone community and get the full member experience.
Join For FreeWhat is CSRF? CSRF stands for Cross-Site Request Forgery. Generally, when we log into a website, it always asks for authentication. From a security point-of-view, developers mostly time pass the CSRF token with a login parameter. But our focus is on how to handle this CSRF token in JMeter.
When we do load testing using JMeter without handling the CSRF token, we get this type of error:
CSRF and JMeter
For handling the CSRF token, we have to use the following parameters in JMeter:
HTTP cookie manager.
HTTP header manager.
Request paramter.
Extract CSRF Token Using JMeter Post Processors
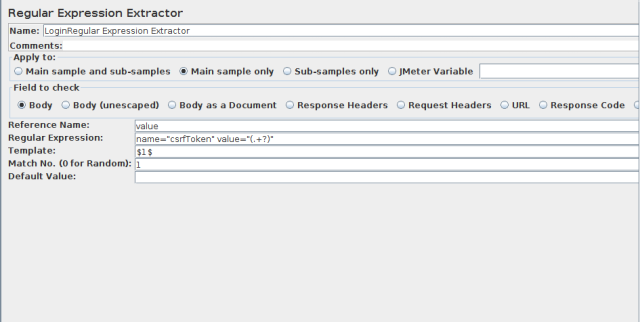
For extracting CSRF, we have to add post processors in the test plan. Then, we have to add a regular expression extractor.

The regular expression extractor handles this CSRF token and its value each time this value is changed. In the regular expression extractor, we have to define certain fields:
Reference name: value
Regular expression: name="csrfToken" value="(.+?)"
Template: $1$
Match no: 1
We just pass this JMeter variable in the request parameter:

Now, we execute the script and see the result:

This is how you can deal with CSRF protection in your Apache JMeter test script.
Opinions expressed by DZone contributors are their own.

Comments