The 6 Pillars of Effective Cloud Security
This article covers the basics for a successful cloud security strategy, emphasizing good basic hygiene over complex solutions.
Join the DZone community and get the full member experience.
Join For FreeCloud security is a top priority for several organizations right now; no doubt about that. However, many companies still find themselves grappling in the dark when it comes to implementing effective cloud security controls.
This article addresses challenges businesses might have when deploying cybersecurity for the cloud by focusing on the six most important pillars for successful strategizing and implementation.
1. Zero-Trust Security
Cybersecurity was much easier when systems and data existed in one central location and could be easily monitored from a single point. Today that is not the case. Many organizations can’t even tell the exact number of devices that can access their systems, talkless of understanding how users handle and share data.
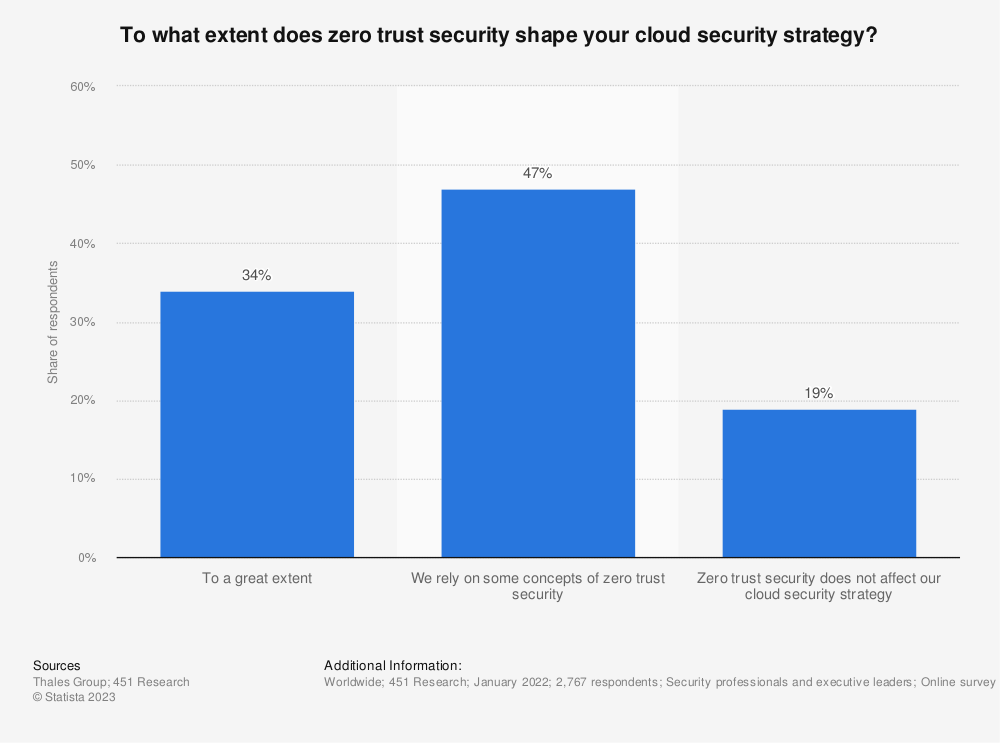
Whereas centralized cybersecurity tools were sufficient sometime ago, today, companies have no option but to use various technologies to track their digital assets wherever they are. But this also complicates things, making data protection increasingly near impossible, especially when it is stored on the cloud.
These factors have necessitated the rise of the zero-trust security framework as a better model to handle the dynamism of cloud environments. With zero-trust security, organizations default to vigilance at all points, maintaining visibility over all data, assets, and risks while assuming that every device and user is potentially malicious.
2. Principle of Least Privilege
One of the key elements of zero-trust security is adopting the principle of least privilege. Most users have access to more than what they need to get their work done at any given time. The principle of least privilege fixes this by balancing usability and security.
That means every user gets access to the exact resources – no more – that they need to perform any given task. And after the completion of the task, the privilege is revoked. This sounds like a lot of work for administrators that are in charge of assigning privileges.
However, the principle is supposed to work with an automated system and with the ultimate aim of minimizing the attack surface by eliminating extraneous access points. If an employee does not need a particular resource, then they should not have access to it; otherwise, an attacker can easily exploit that vulnerability.

3. Privileged Access Management
The Verizon Data Breach Investigations Report for 2022 indicated that half of all cyberattacks target privileged credentials. And the logic is coherent; if you were an attacker looking for the most beneficial loophole, it only makes sense to target privileged users: administrators, managers, emergency contacts, etc.
Before purchasing a privileged access management solution, though, businesses must ensure, first, that only a minimum number of users have access to administrative functions. This is where the principle of least privilege comes in. Permissions should be assigned according to roles.
That said, it’s still important to invest in a PAM solution that automatically enforces your policies concerning usage access. And it is more important that your PAM solution not only focuses on people but also on processes, devices, and technologies.
So, for instance, an effective PAM solution would be able to create, provision, and deprovision accounts automatically, and it would also be able to secure remote access and monitor third-party access to data. This also applies to IoT devices, which are increasingly a worrying leeway for attacks.
4. Cloud Security Monitoring
Real-time monitoring is another non-negotiable when it comes to cloud security. Already, major regulations such as PCI DSS and HIPAA mandate monitoring. So, if your business falls under that legislation, you have limited choice. However, not every company implements cloud security monitoring effectively.
Most cloud service providers have native cloud security monitoring features within their offerings, but many organizations are better served by adding a third-party solution that is more robust into their cloud framework.
Cloud Access Security Broker (CASB) solutions are important because they do not just exist to aggregate security data from multiple sources. With analytics and machine learning, they can also automatically detect anomalies in system behavior and send time-sensitive alerts to human agents to trigger immediate incident response.
Specifically, this is how Security Information and Event Management (SIEM) software works. They aggregate data from various tools, including anti-malware applications, firewalls, intrusion detection systems, etc., and then use the collected insight to proactively enhance threat response.
5. Endpoint Security
Regardless of whatever side you stand on the matter of remote work, it is here to stay, even if in hybrid models; everyone saw this coming; they just weren’t sure when it would come. And that uncertainty is part of why, 3 years after COVID, many organizations are still grappling with the reality of distributed endpoints.

Even among companies that recognize the need for enhanced endpoint security, endpoints are almost always treated as potential victims that can serve as vectors for attacks. However, we need to start paying attention to the fact that endpoints are also potential attackers.
The question then becomes: how do we prepare for either scenario? If all devices on a network are trusted, what happens if one device is made to go rogue and start attacking others or even the main system? What are the protocols for removing and isolating a compromised device? These are important questions for any organization that wants to take cloud security seriously.
There are also questions regarding how data is shared and managed on employee-owned devices in dispersed settings. In essence, it’s important to establish responsibility protocols for the security of each endpoint device. Without such definitions, you leave your systems defenseless with no one taking responsibility.
6. Incident Response
Incident response has always been a thing in cybersecurity. But its role has evolved over the past years as organizations moved towards cloud computing, particularly hybrid cloud models. So, responding to cybersecurity incidents has had to adapt to new challenges with data volume and sophistication of attacks.
One mistake that is obvious but which, apparently, many organizations still make is not changing the default configurations from their cloud vendors. It makes for a very smooth leeway for attacks from malicious actors. For instance, not reviewing the default configurations may mean that certain events are not captured in the log just because.
Perhaps where the roles of human agents are most apparent in data security in incident response. IT teams must be able to adapt to the dynamic nature of cloud security in order to meet the intense demands that the threat of attacks places upon us.
Conclusion
In addition to the six pillars discussed in this article, there are a number of other cloud security best practices that organizations should follow. Sometimes, all an organization needs is to practice basic cyber hygiene before deploying resources into acquiring complicated solutions.
Opinions expressed by DZone contributors are their own.

Comments