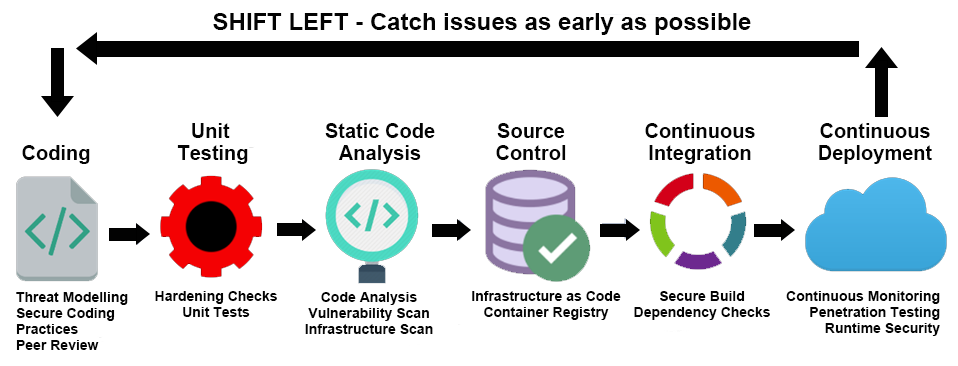
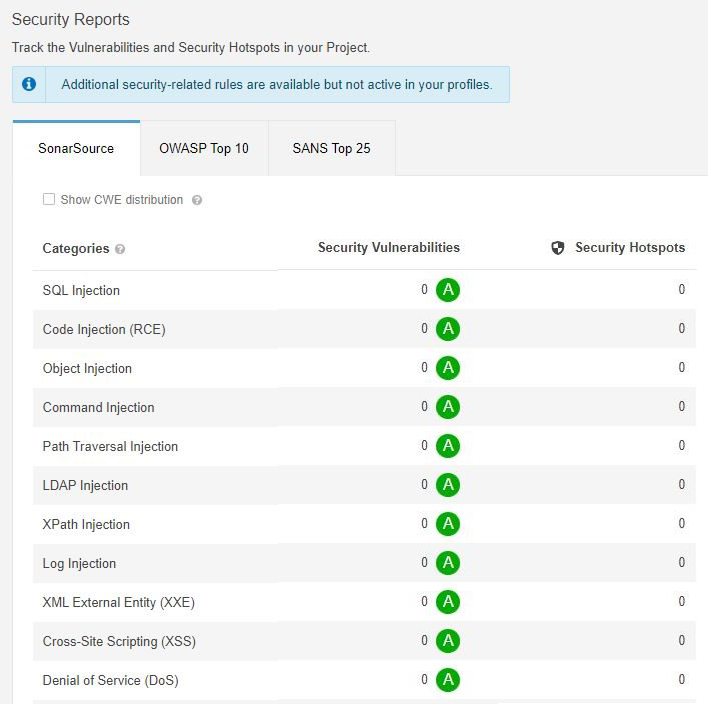
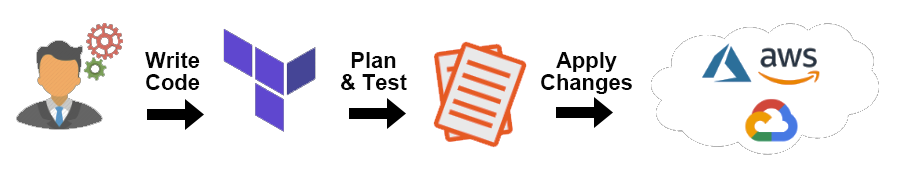
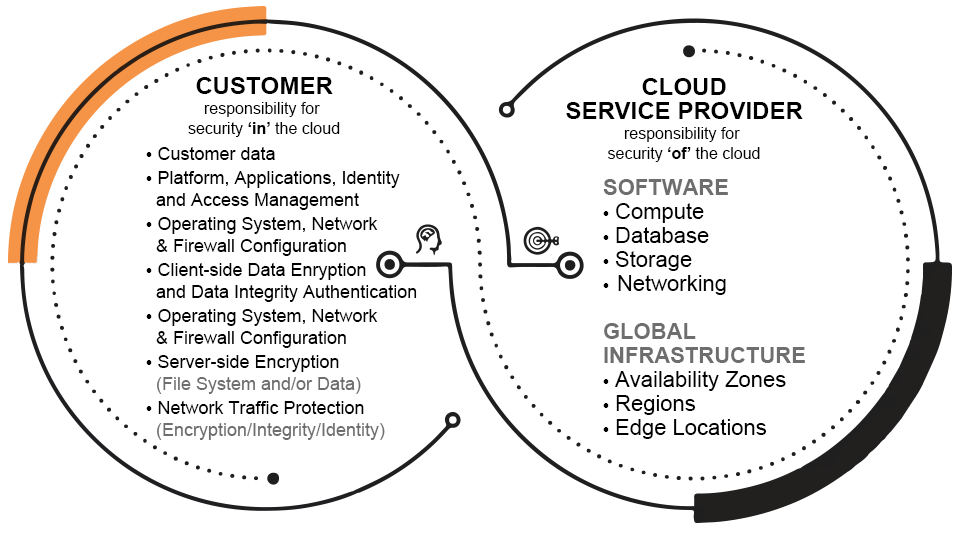
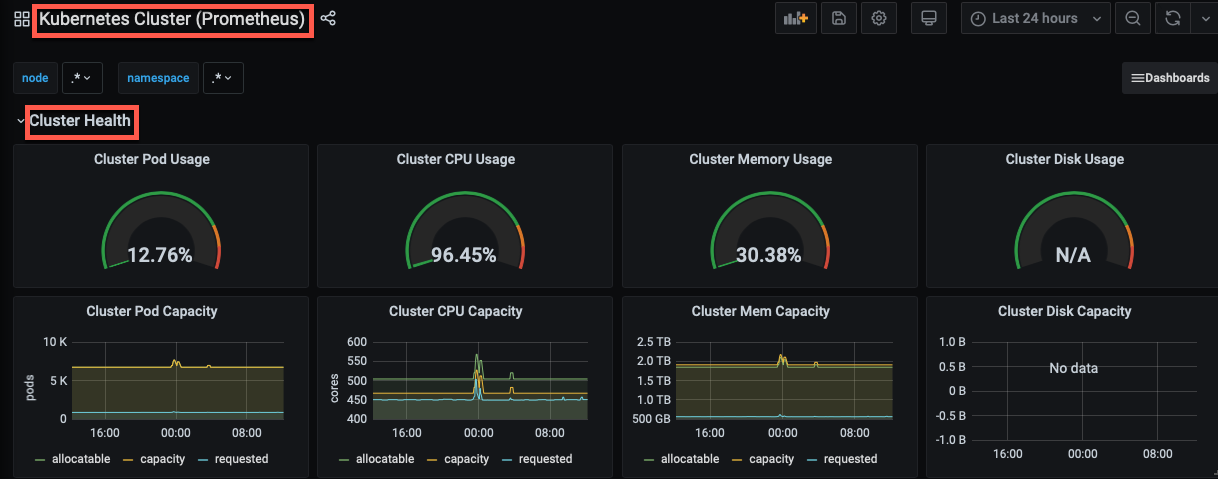
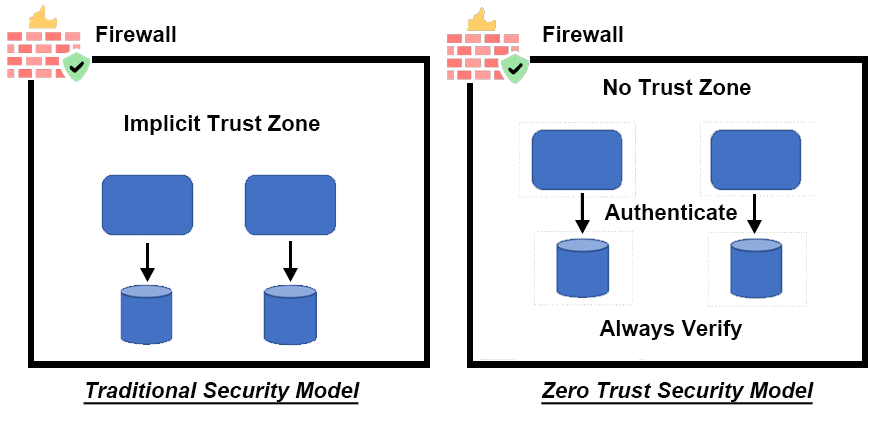
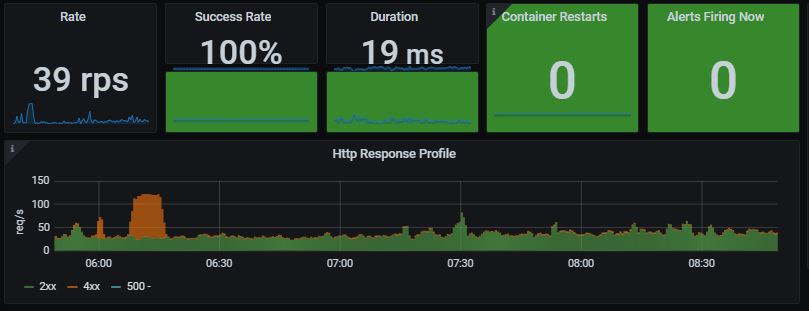
As enterprises increasingly adopt cloud technologies, it's crucial to design a secure cloud architecture. If you don't adhere to cloud security guidelines, organizations can expose themselves to cybersecurity threats, resulting in an unwanted impact on cloud infrastructures and workloads. First, let us look at the most common cloud security challenges facing nearly every organization.
Attack Surface Management
The attack surface is dynamic and continuously changing. As organizations grow, the number of deployed cloud resources increases. Modern infrastructure spins up resources based on demand. As a result, it's challenging to have complete visibility into your cloud resources and other digital assets. The distributed workforce also creates challenges with securing devices across the globe.
Inventory of all the internet-facing resources is required; otherwise, organizations will miss scanning resources for vulnerabilities. Gaps in your monitoring strategy can result in the external exploitation of resources. You can't secure resources that you're not aware of. There are high chances that attacks happen on unmanaged or untracked resources. During cyberattacks, hackers primarily target the cloud assets that are exposed to the internet.
Ransomware Attacks
Ransomware is a malware attack that can prevent or limit users from using their systems until a ransom fee gets paid. In other cases, files in your system are locked or encrypted, making them unusable. Ransomware attacks have increased in recent years: The malware target can either be an individual or an enterprise. There are two types of ransomware attacks that exploit weaknesses in the security posture:
- Crypto ransomware encrypts files on a computer so that the user cannot access the files.
- Locker ransomware locks victims out of the computer so that they cannot use it.
Malicious software gets injected into the system via a phishing attack — e.g., when you get tricked into clicking a link in an email, opening an email attachment, or visiting a malicious site. Infected files are then installed in the target machine, consequently taking control of the resources.
Distributed Denial of Service Attacks
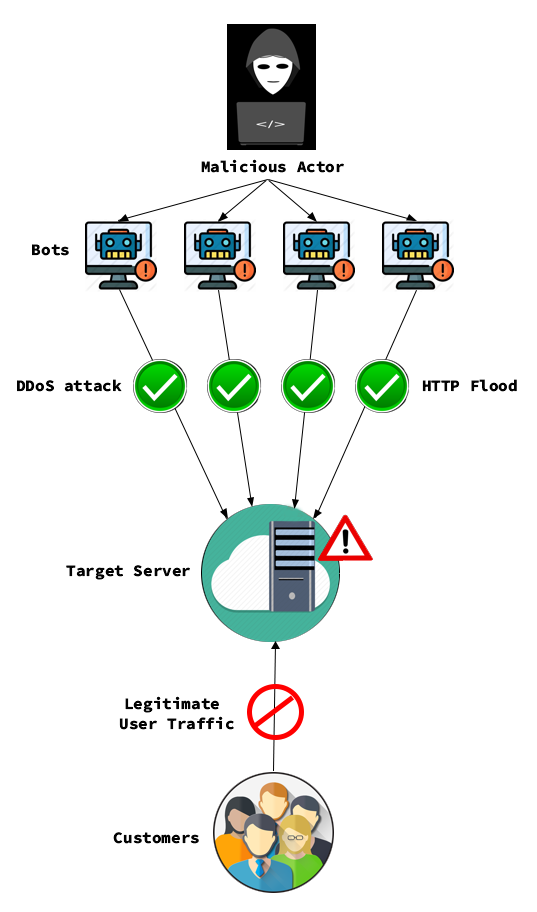
A DDoS attack is one of the most widespread cyber threats where a large amount of traffic from multiple sources is sent to a service, thus overwhelming the target and negatively impacting behavior. This malicious traffic originates from a single IP address or IP range that consumes all the resources; the legitimate users cannot access the service or see degraded service performance.
DDoS attacks can have various impacts: unhappy customers, revenue loss for the business, damage to an organization's reputation, and loss of productivity. DDoS attacks can be classified into infrastructure layer attacks (SYN floods and UDP reflection attacks) and application layer attacks (HTTP floods and DNS query floods).
Figure 1: DDoS attack in action
Data Breaches
Data breaches are one of the top cybersecurity threats as enterprises are rapidly moving to the cloud. Data breaches have impacted organizations of all sizes for many reasons — lack of visibility, gaps in resource monitoring, sensitive information not stored securely, etc. Data leaks are primarily due to:
- Compromised passwords
- Stolen devices
- Non-compliant resources
- Misconfigurations
- Lack of proper security measures and training
In addition, bad actors can get unauthorized access to critical data via weak or stolen user credentials, unpatched components, and human error. In such scenarios, there is a risk of data being modified and incurring data loss that might be irreversible.
Supply Chain Attacks
A supply chain attack is a cyberattack targeting a trusted third-party vendor who offers services or software vital to the supply chain. In some cases, cloud-native applications are more susceptible to supply chain threats. For example, anyone can contribute to the development of open-source software solutions. Using this access, hackers can program vulnerabilities into open-source solutions, making it easy to introduce a threat to companies that use the software.
In addition, cloud environments are interconnected, so bad actors try to take advantage of the weakest component in the chain. During such attacks, a ripple effect is created that impacts a broader audience and eventually reaches the victim, who is not the initial target.
Crypto-Mining Attacks
Cybercriminals are stealing system resources and using this to illegally profit from digital currency mining. They do this by installing a crypto-mining tool on victims' machines and using resources on those systems. As a result, attackers can use the computing power of others without their knowledge or permission, causing a slowdown in device performance. There are two types of crypto-mining attacks:
- Browser-based crypto-mining injects JavaScript into a website and performs mining activities while a user views the page.
- Malware-based crypto-mining takes over your entire computer and uses the computer CPU to mine coins on your system at a much higher level.
Phishing Attacks
Phishing is a type of social engineering attack where the attacker sends fraudulent email communications that appear to be from a trustworthy source, luring the target to respond to the email. It often results in stealing sensitive data (credit card information, passwords, access to sensitive files, etc.) or installing malware on the victim's machine. Attackers use this information to steal money, gain confidential data, or access the company's network.
The rise of phishing attacks is a risk to enterprises and has continuously evolved to adopt new techniques. Subtypes of a phishing attack are vishing (voice-call phishing) and smishing (SMS phishing).
Malware Attacks
A malware attack is a typical cyberattack where malicious software gets installed on someone's machine without their knowledge. Malware uses various attack vectors that disrupt the standard functionality of the services for cybercriminals to gain unauthorized access to systems and networks. A large number of breaches occur in enterprises with the help of malware. Cloud assets get exposed to the internet and, hence, can assist in spreading malware. Malware takes different forms and attacks in varied ways:
- Viruses
- Trojans
- Adware
- Spyware
- Ransomware